Vendor risk assessment is important to ensure the security and compliance of the vendors you’re engaging with. But the question arises: How to do it? To make the assessment effective, it is necessary to have a proper vendor risk assessment process. This article covers the 6 key steps of the vendor risk assessment process to perform it efficiently.
As an IT manager, you might struggle to assess vendor risks accurately. Vendors often lack a structured approach, which might lead to inconsistent evaluation of vendor risks. This can leave gaps in security and increase the chance of hidden vulnerabilities. Moreover, relying on ad hoc assessments will add more uncertainty as your number of vendors increases.
The solution? A structured vendor risk assessment process. You can evaluate each vendor thoroughly by establishing a clear, step-by-step approach. This will help you identify risks early, ensure compliance, and make smart decisions.
This post will explore the various steps of a vendor risk assessment process.
Steps Involved in an Effective Vendor Risk Assessment Process
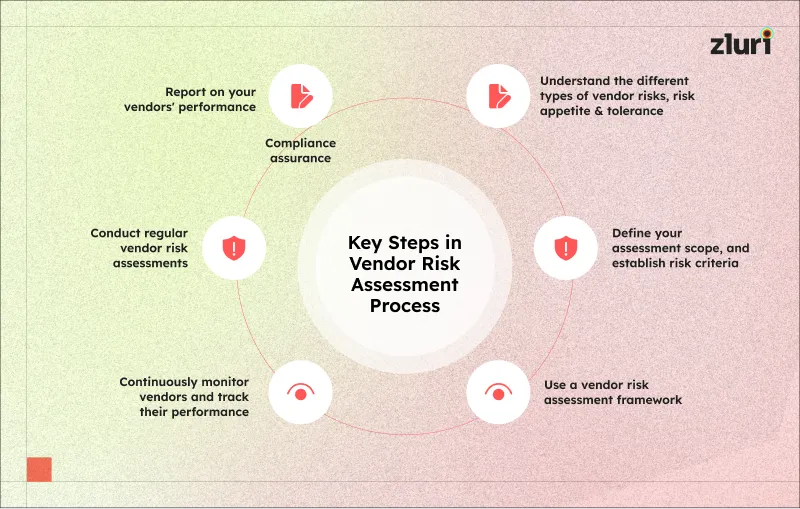
Let’s discuss the steps of vendor risk assessment process in detail.
1. Understand the different vendor risks, risk appetite & tolerance
This step of the vendor risk assessment process is important, as it helps your team identify potential risks. It also helps your team set boundaries around what level of risk your organization can handle. Without this knowledge, your team could engage with vendors who could bring risks to your organization, impacting your business continuity and compliance.
To perform this step of your vendor risk assessment process, your team must first categorize different vendor risks. These include:
- Operational Risk: This risk type of vendor often fails to meet agreed-upon standards or services.
- Financial Risk: This risk is associated with a vendor's financial stability or potential insolvency.
- Compliance Risk: The risk type of a vendor fails to comply with industry or regulatory requirements.
- Cybersecurity Risk: This is a risk of data breaches, cyberattacks, or vulnerabilities through vendor systems.
- Reputational Risk: This type includes the risk of damaging your organization's reputation if a vendor acts unethically or irresponsibly.
Once you are aware of these risk types, the next step is to establish the organization's risk appetite and tolerance.
- Risk appetite refers to the level of risk your organization is willing to accept to achieve its goals.
For example, your organization might have a lower risk appetite when it comes to storing sensitive financial data in the cloud. In this case, factors like the vendor's security protocols, compliance certifications, and history of data breaches become critical. This makes your organization more selective about cloud storage options for financial information.
- Risk tolerance, on the other hand, defines the maximum level of risk your organization can handle before it impacts your overall operations.
For instance, if a data security breach could lead to major issues, your organization's risk tolerance may be low in this area. This means any security vulnerabilities need to be addressed immediately to avoid impacting your operations.
By clearly defining them, your team can create a risk threshold to help you decide on each vendor. It will also keep your organization compliant and protect your organization's reputation by preventing partnerships with high-risk vendors.
2. Define your assessment scope & establish risk criteria
Once you understand the types of risks in detail, this step helps you set clear objectives for your vendor risk assessment and ensure that your team focuses on the most critical areas. Without a defined scope, assessments can become broad, which might lead to missed risks. By setting a scope, your team can assess vendors more effectively and make informed decisions.
To perform this step in the vendor risk assessment process, identify which areas of a vendor's operations and security practices will be assessed. This includes deciding whether to evaluate financial stability, data security, regulatory compliance, or other areas directly impacting your organization.
For instance, your team might prioritize cybersecurity and data protection practices if a vendor has access to sensitive data. By defining this scope, you can avoid assessing irrelevant aspects, saving both time and resources.
Next, establish risk criteria to measure each vendor's level of risk. Risk criteria can include factors like the vendor's history of security breaches, compliance with regulations, or financial health. For each criterion, define what level of risk is acceptable, moderate, or critical. Then, your team can give a score or rating based on these levels, such as using a scale from 1 to 5.
For example, a vendor with no history of breaches might be given a score of 1. On the contrary, the vendor with recent breaches would be given a score of 4 or 5. This scoring system helps you standardize assessments and make comparisons between vendors more easily.
This step of the vendor risk assessment process helps your team prioritize vendor assessments by focusing on higher-risk vendors that might need deeper evaluation or mitigation strategies. It also ensures that your organization partners with vendors who meet your specific security posture and operational standards, reducing potential risks to your organization.
3. Use a vendor risk assessment framework
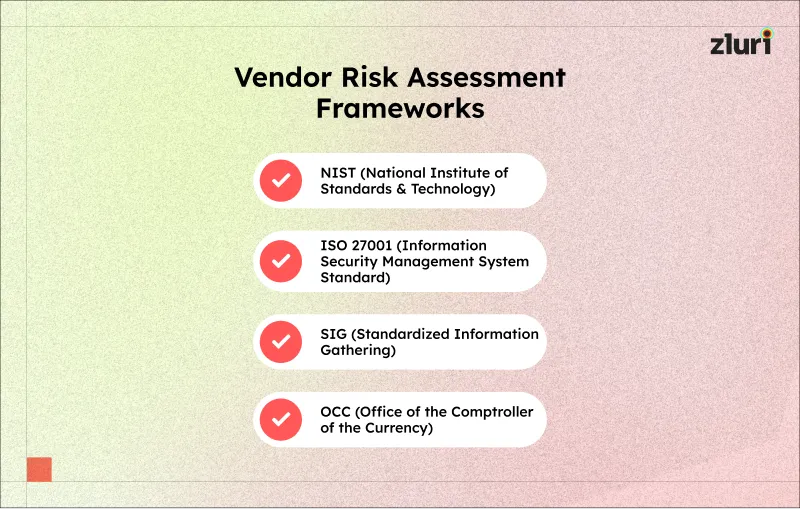
Assessments can become complex without a set framework, making it difficult to identify and compare risks across different vendors. Having a framework in place helps streamline the vendor risk assessment process. This will ensure a thorough evaluation of vendors, keeping your organization secure.
To use a vendor risk assessment framework, your team needs to first select a framework that aligns with your organization’s needs and risk priorities. Several popular frameworks can guide this process, such as:
- NIST (National Institute of Standards and Technology): This NIST framework provides guidelines for managing information security risks and is widely used for IT security evaluations.
- ISO 27001: This is an international standard focused on information security management. This is an ideal framework for assessing vendors' data security practices.
- SIG (Standardized Information Gathering): Developed by Shared Assessments, this framework provides a set of standardized questions to evaluate a vendor's security, privacy, and risk practices.
- OCC (Office of the Comptroller of the Currency): This framework focuses on vendor management for financial institutions. It can be useful for evaluating your vendors if they're handling sensitive financial data.
Once you choose a framework while performing the vendor risk assessment process, your team can customize it to align with your specific assessment needs. For example, if data security is your priority, you might focus on questions and requirements related to data handling and protection. The framework will guide your team in collecting and analyzing vendor responses, focusing on areas where vendors might pose higher risks.
Moreover, it enables consistency across your assessments, making it easier to compare the vendors and identify potential red flags. A framework-based assessment also helps you ensure that each vendor meets your organization's security posture and compliance standards.
4. Continuously monitor vendors and track their performance
The core of the vendor risk assessment process is continuous monitoring of vendors and tracking their performance. Vendor risks are continuously evolving. This might impact your organization's security, compliance, or operational efficiency.
For example, a vendor at low risk at the start might experience issues over time, currently making it a high-risk vendor. Therefore, it is important to continuously monitor the vendors. This will help your team to quickly detect and address any changes that might introduce new risks.
To perform this step of the vendor risk assessment process, your team should implement regular check-ins and assessments to evaluate vendor performance. Also, there are several effective strategies for your ongoing vendor monitoring.
- Regular Audits: You can schedule regular audits to verify that your vendors meet compliance and security standards. This helps you ensure that vendors align with your organization's risk criteria.
- Performance Reviews: Your team can conduct performance reviews at set intervals, such as quarterly or annually, to discuss the vendor achievements and areas for improvement.
- KPIs: Key performance indicators (KPIs) can be used to review vendors' performance. You can set KPIs and track them over time to evaluate how well vendors meet performance and security benchmarks. This allows your team to easily spot any downward trends.
- Surveys and Questionnaires: Your team can send surveys or questionnaires to the vendors. This will help them gather updated information on vendor practices, compliance, and recent risk-related changes.
These strategies allow your team to stay proactive, addressing any vendor issues before they become significant risks. Moreover, this creates accountability, as your vendors will know they are closely monitored.
5. Conduct regular vendor risk assessments

Regular vendor risk assessments are important for managing your vendor relationships effectively. To conduct this step of the vendor risk assessment process, begin by setting a clear structure for how you will conduct them. This includes defining what areas of risk are most relevant, such as data security, compliance with regulations, or operational performance.
In order to conduct regular vendor risk assessments, you can use different methodologies. This will create a thorough view of each vendor’s risk level. Below mentioned are a few key methodologies to consider:
- Self-Assessments: In self-assessments, vendors will provide details about their own security, compliance, and risk controls. This can be an easy way to gather initial data, though it may require a follow-up for verification.
- Third-Party Audits: This methodology involves hiring an external firm to evaluate the vendor's practices and identify risks. This is a more reliable approach, providing an objective view of the vendor’s risk level.
- Vendor Scorecards: Scorecards use a range of metrics to score vendors on factors like performance, compliance, and incident history. They provide a consistent way to measure and compare vendors over time.
- Vendor Risk Assessment Questionnaires: Questionnaires are useful for collecting specific information from vendors about their policies and controls. This helps gather consistent data, especially if sent out regularly for updates.
Each method allows your team to create a complete view of your vendor risk from multiple perspectives. Moreover, regular assessments give your team ongoing insights. This further enables you to take quick action if your vendor’s risk profile changes.
6. Report on your vendor's performance
Reporting on vendor performance is the final step in the vendor risk assessment process. This step will give you a documented view of each vendor’s performance and risk status. A detailed report helps your stakeholders understand any existing risks and what actions need to be taken.
Your team should compile data from all assessments, audits, and monitoring efforts to perform this step of the vendor risk assessment process. This data should be organized into a report highlighting key aspects of the vendor’s performance. The report should include the following:
- Performance Metrics: These metrics show how well the vendor meets agreed-upon service levels. They may cover uptime, response time, and support quality.
- Compliance Status: Documenting compliance status helps show whether the vendor meets regulatory and industry standards, which are vital for reducing legal and operational risks.
- Vulnerabilities Identified: List any security or process vulnerabilities found during assessments. Knowing these helps you understand where potential risks lie.
- Current Level of Risk: Based on the findings, summarize the vendor’s overall risk level. This rating could range from low to high, helping decision-makers prioritize actions.
- Vendor Criticality: This indicates how critical the vendor is to your operations. This helps prioritize high-risk vendors that are essential to business functions.
- Risk Mitigation Actions: Here, you should include recommended steps to reduce identified risks. This might involve strengthening security protocols, increasing monitoring, or setting stricter compliance requirements.
Note: The report should be shared with all your relevant stakeholders, including IT, compliance, and procurement teams.
Moreover, the report in your vendor risk assessment process ensures that all your stakeholders have a clear view of your vendor’s risk level and performance. It also allows your team to track improvements or new risks over time, making it easier to make future vendor decisions.
Assess & Manage your Vendor Risks Efficiently with Automation
Once you’re aware of the steps of a vendor risk assessment process, manually tracking all the vendor details and performing the process can be time-consuming. Therefore, automation will help your team handle vendor risks better and keep your organization compliant.
To automate the process, you need to use a suitable tool. However, numerous tools are available in the market. One such tool is Zluri. It offers a SaaS management platform that helps you centralize all your vendors and their details in one single location. These details include information about the vendors' contracts, spend, cost, status, and more.
These centralized vendor details help you avoid juggling multiple spreadsheets and save you time. Now, the question arises - how does this information help you identify vendor risks?
Zluri’s SMP allows you to gain visibility into the compliance and security insights of various apps discovered in your organization. This information helps you determine the threat levels, risk, and risk scores associated with each app.
Based on these risk and threat levels, you can compare the different apps offered by the vendor. This will help you make an informed decision on whether to retain or eliminate the vendor. It will also help you associate with secure vendors, enhancing your organization’s security posture.
Book a demo today if you want to learn more details about how it can help!
Frequently Asked Questions (FAQs)
1. How do you create a vendor risk management program?
Below mentioned are the steps for creating a vendor or third-party risk management program:
- Document Your Vendor Risk Management Policies
- Set Vendor Selection Standards
- Conduct Vendor Due Diligence
- Regularly Audit Your Vendors
- Define Clear Reporting Expectations
- Map Your Supply Chain Attack Surface
- Prioritize High-Risk Vendors
2. What is a third-party risk assessment?
A third-party risk assessment evaluates the risks that come with a company’s relationships with third-party vendors, suppliers, and service providers across the supply chain. This assessment helps you identify and manage potential threats from external partners.
3. What is a cybersecurity policy?
A cybersecurity policy outlines clear guidelines for how employees should handle digital security, covering actions like encrypting email attachments and limiting social media use. Such policies are essential because they help protect against costly cyberattacks and data breaches.
4. What is a vendor risk assessment report?
VRA reports are designed to spotlight vendor risks for key decision-makers, usually within procurement, security, or IT teams. These reports support informed procurement decisions, help establish internal controls, and guide effective vendor risk management (VRM) strategies.
5. What is the vendor categorization?
Vendor categorization is a systematic process of classifying vendors/suppliers based on specific criteria, such as the nature of the products/services, risk, and their importance to your business.







.svg)














