It's Monday morning. Your calendar reminder pops up: "Q1 Access Review - Start Today."
Your stomach drops. Not again.
You know what's coming.
- Two weeks of logging into 30 different applications.
- Exporting user lists.
- Copy-pasting into spreadsheets that never quite line up.
- Chasing down managers who don't respond.
- Answering the same 50 questions from people who don't understand what they're reviewing.
- Manually revoking access one user at a time while trying to do your actual job.
- Scrambling to compile evidence when the auditor asks for proof.
And at the end of all this effort—this massive, exhausting, soul-draining effort—someone will still find something you missed.
The auditor will write a finding. Your boss will ask why you didn't catch it. Security will say you're not doing enough. And the cycle will repeat next quarter.
It feels like punishment. Like you're being set up to fail, then blamed for failing.
Here's the thing: You're right. It IS punishment. Not because anyone is intentionally punishing you, but because the entire access review system is designed in a way that makes IT the scapegoat for an impossible task.
You're not failing at access reviews. Access reviews are failing you.
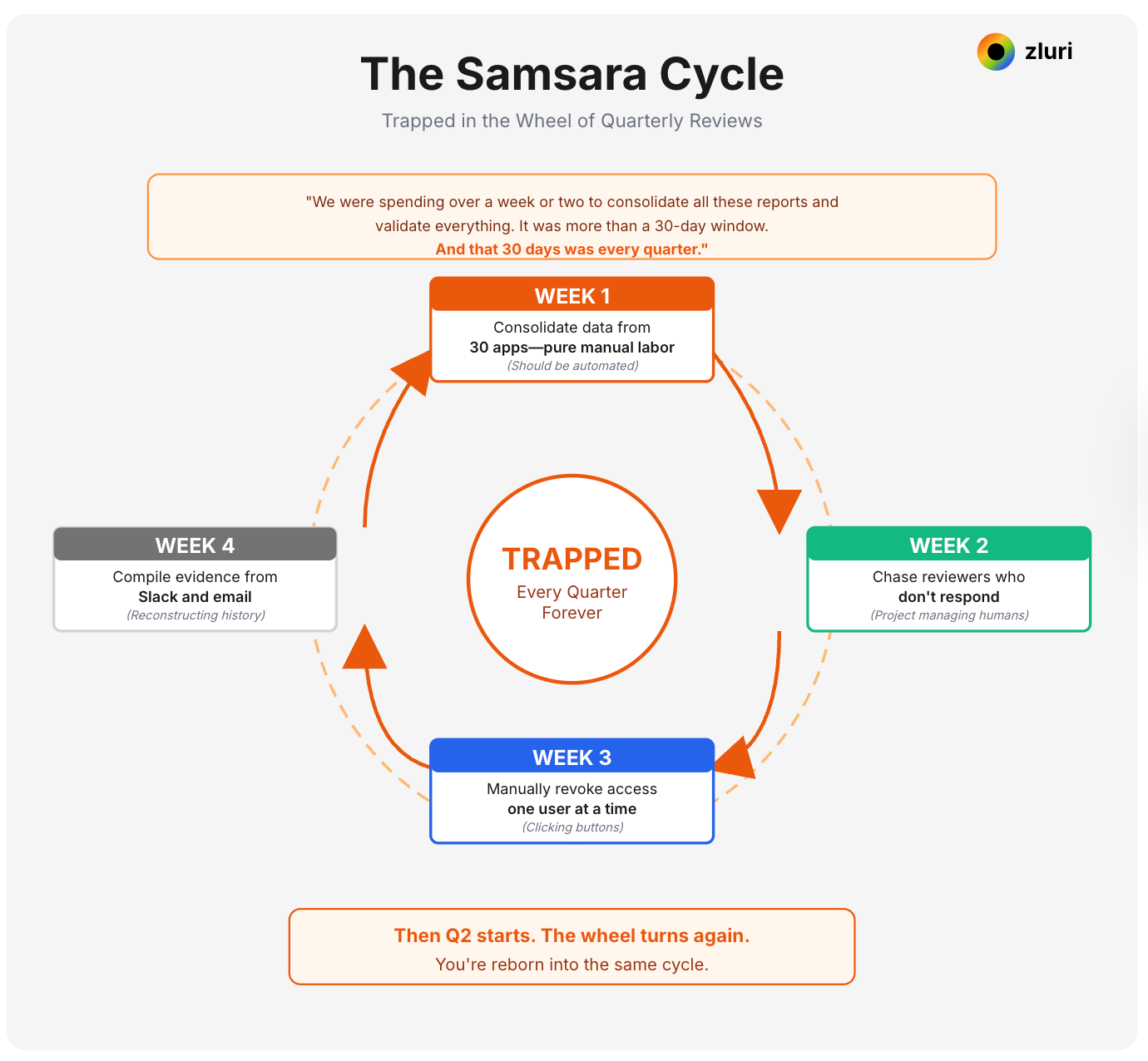
The Samsara Cycle: Trapped in the Wheel of Quarterly Reviews
Samsara is the endless cycle of birth, death, and rebirth—trapped in the wheel, repeating the same patterns until you achieve fundamental change and break free. That's access reviews.
One of our recent customers in financial services described their previous process before using Zluri: "We were spending over a week or two to consolidate all these reports and validate everything. It was more than a 30-day window. And that 30 days was every quarter."
Every quarter. Forever. Trapped in the wheel.
Week 1 of the cycle: You consolidate data from 30 applications. This is pure manual labor—log in, export, copy, paste, reconcile. You're not making strategic security decisions. You're doing data entry that should be automated.
Week 2: You chase reviewers who don't respond. You answer questions from people who don't understand what they're reviewing. You're project managing humans through a process they hate as much as you do.
Week 3: You manually revoke access one user at a time across 30 applications. You're clicking buttons that should be automated. Production IT work—provisioning new employees, fixing broken systems, supporting the business—waits.
Week 4: You compile evidence for the audit. You're reconstructing what happened from Slack messages and email threads because nothing captured it automatically.
Then Q2 starts. The wheel turns again. You're reborn into the same cycle.
The cruel part: You're working incredibly hard. You're spending entire weeks on this. You're doing exactly what compliance and security policy requires. And yet:
- Nothing gets easier
- The workload grows (more apps, more users, more complexity)
- You're always behind
- Someone always finds something you missed
- You're blamed for the gaps
One of our recent customers in life sciences research described their previous process before using Zluri: "It was manual, slow, error prone."
In short, you're set up to fail, then blamed for failing.
You're Being Asked to Do Something Impossible (Then Blamed When It's Incomplete)
Your CEO asks a simple question: "Who in the company has admin access to our financial systems?"
It's not a simple question. To answer it, you'd need to:
- Log into NetSuite, QuickBooks, Bill.com, Expensify, Stripe, the bank portal, the payroll system, and at least five other systems
- Navigate to user management (different path in every application)
- Export current state
- Cross-reference against HR data to see who these people actually are
- Check if any of these are contractors whose contracts ended
- Verify if anyone was granted temporary admin that was never revoked
- Repeat this for every "financial system" (which systems count as financial?)
And even after all that work, you'd only know the current state. Not any historical state. Not "who had access three months ago during the audit period."
The ask seems reasonable. The execution is impossible.
One of our recent customers in healthcare described their previous challenge before using Zluri: "We didn't know if someone had been given admin permissions or user permissions. If a user had admin access for a certain period, we would forget to remove it later."
This isn't negligence. This isn't IT being lazy or careless. This is the natural consequence of asking humans to manually track thousands of access decisions across hundreds of applications with zero automated visibility.
Of course you forget. Of course you miss things. Of course you can't answer "who has what access" instantly. You're not a database. You're a human being.
But when the auditor finds the contractor who still has access six months after their contract ended? When they find Sarah's forgotten admin access from the project 18 months ago? When they find the segregation of duties violation nobody caught?
You get blamed. Not the system. You.
The Reviewer Problem: You're Accountable for Decisions You Don't Control
You send the Engineering manager a list: 47 AWS users to review. They have three columns to work with: Name, Email, Role.
The manager looks at roles like "IAM:PassRole" and "EC2:FullAccess" and has no idea what they mean. They don't know which permissions are required for the job. They don't know if the contractor who left is still on the list. They don't know if Emily should still have access after her transfer.
So they do one of three things:
- Approve everything (don't want to break production)
- Revoke everything that looks weird (might break production)
- Ignore the request until you chase them down
None of these options produce good security outcomes.
One of our recent customers in life sciences research identified the problem in their previous process before using Zluri: "Reviewers lacked context. They needed clear signals like privileged roles, last activity, and cost."
But here's the painful part: When the review misses something, when the rubber-stamping creates a security gap, when the auditor finds an issue—you're held accountable.
Not the reviewer who approved without looking. Not the system that gave them insufficient information to make good decisions. You.
You're responsible for the quality of decisions made by people who:
- Don't have the information they need
- Don't have the time to investigate thoroughly
- Don't fully understand what they're approving
- Aren't held accountable when they make mistakes
You own the outcome but don't control the process.
The Audit Trail Nightmare: Prove You Did Something You Can Barely Remember
Your auditor asks: "Show me evidence that you reviewed John's Salesforce access in Q2, including who approved it, when, and the business justification."
Your heart sinks. You know you did this. You remember discussions. There was definitely a Slack thread. Or was it an email? Or Jira? Or that spreadsheet someone updated?
You search. You find fragments: A Slack message that says "Looks good ✓" (but from whom? approving what exactly?). An email thread discussing something related (but was this Q2 or Q3?). A Jira ticket that might be relevant (but it's not clear if this was the final approval).
Two hours later, you've compiled something. You hope it's enough.
One of our recent customers in technology described their previous situation before using Zluri: "Our audit evidence was scattered across Jira, Slack, and Okta. We needed all historical information to support access decisions."
Here's why this is so demoralizing: You did the work. You spent weeks running the review. You got manager approval. You revoked access. You did everything the policy requires.
But because the evidence was never captured systematically, because it's scattered across five different tools, because nobody designed the process to generate proof—you can't prove you did what you did.
The auditor writes a finding. Not because you didn't do the review. But because you can't prove you did it.
You're being held to a standard of proof that the system wasn't designed to generate.
The Remediation Gap: The Work Is Never Done
Your Q1 review finished. Managers identified 200 users who need access revoked across 30 applications. You think: "Great, we found the issues. Now we'll fix them."
Then reality hits.
You have to log into 30 different applications. Navigate to user management in each one (different path every time). Find each user (search by email? by name? by ID?). Click through the deactivation workflow (2 clicks here, 5 clicks there). Confirm. Document. Move to the next one.
200 revocations. One at a time. Manually.
A customer in healthcare told us: "When we have audits, we have to remove users from the software manually. Going to each tool, downloading the Excel file, checking whether they are present, and then we have to remove them."
Week 1: You remove 50 users. Good progress.
Week 2: You remove 30 more. Slowing down because production issues came up.
Week 3: You remove 15 more. Taking longer than expected.
Week 4: You still have 105 users to remove.
Week 5: The Q2 review launches.
You never finished remediating Q1. Now Q2 identified 180 more. Your backlog is 285 users. You're falling further behind every quarter.
A prospect in financial services described what they are looking for: "We want to find out visibility and then the fixing, addressing it. We are also looking to take the automated approach for remediating."
The irony is that you found the security issues. You identified exactly who needs access revoked. You did the hard investigative work. And then you get stuck in weeks of mind-numbing manual clicking because remediation isn't connected to the review.
The security value was in the discovery and decision. The remediation should be automated. Instead, you're doing the most tedious, error-prone, soul-crushing part manually. And when it's not finished on time? You're blamed for the delay.
The Impossible Coverage Problem: You're Judged on Applications You Can't Access
You implemented an access review tool. It connects to SSO and automates reviews for 20 applications. Amazing! You cut review time from 6 weeks to 15 days for those apps.
But you still have 50 applications that aren't behind SSO. Legacy systems. Vendor-managed tools. Contractor-built apps. Industry-specific platforms.
One customer in healthcare said: "32 of 60 applications are not behind a proper SSO. These 50% are critical apps that require more attention, and we need manual intervention."
50% of your applications. The most critical ones. Still manual. Still spreadsheets. Still 2 weeks of work every quarter.
You have two parallel systems now:
- Automated (20 apps): Click button, done in 15 days
- Manual (50 apps): Log in, export, spreadsheet, email, chase, revoke—6 weeks of work
Here's the punishment: Your compliance policy says "quarterly access reviews for all applications." Not "for applications behind SSO." All critical applications.
You're being judged on complete coverage. But complete coverage is technically impossible for 70% of your stack. Those apps will never integrate. The vendors offer SSO, but it requires an enterprise plan which is 4 times the cost of a standard plan (also called SSO tax.) The legacy systems can't be modified. The business won't sunset them.
You're being held to a standard that's technically impossible to achieve. And when coverage is incomplete? When the auditor picks one of the 50 apps you can't automate and asks for evidence? You're blamed.
The Fallback Failure: You're Responsible for Other People's Availability
You launched the Q1 access review. You assigned the Sales VP as primary reviewer for Salesforce. The deadline is Friday. It's Wednesday. No response.
You check Slack. They're on vacation. For two weeks.
You assigned a fallback reviewer. But the fallback was never notified. They don't know they're the backup. They don't know there's a review pending. They don't have context.
You frantically message them: "Can you review 73 Salesforce users by Friday?"
Reply: "What? I didn't know I was assigned this. I don't have access. What am I reviewing?"
It's Wednesday. The deadline is Friday. You're starting over.
One of our customers in banking described this exact scenario in their previous system: "We need to manually reach out to the fallback reviewer and tell them, 'You're a fallback reviewer, please take action.' The certification owner has to inform the fallback reviewer."
The system failure: The primary reviewer is responsible for completing the review. But the system didn't notify the fallback reviewer. Didn't give them context. Didn't escalate automatically when the primary didn't respond. Didn't give them time to be mentally prepared.
And of course, the fallback reviewer was just sitting around waiting for this urgent assignment. They had no other projects, no other deadlines, no other responsibilities. They were eagerly hoping someone would drop 73 users to review into their lap with 48 hours notice.
They'll obviously drop everything they're working on—the product launch, the security incident, the executive presentation—to review Salesforce access they didn't know they were responsible for.
You have to manually monitor every reviewer. Track who's responding. Figure out who's on vacation. Manually escalate to fallbacks. Provide context. Chase people down.
You're doing project management work that should be automated. And when the review is late because the fallback wasn't notified? You're blamed for missing the deadline.
The Notification Nightmare: You're Answering the Same 50 Questions Every Quarter
You send 20 managers an email: "Please complete your Q1 access review by March 15."
Within an hour, 20 replies:
- "What am I reviewing?"
- "Where's the link?"
- "I'm on vacation that week."
- "Can someone else do this?"
- "What does this mean?"
- "How long will this take?"
- "Why am I getting this?"
- "Is this urgent?"
You spend the next week answering the same questions from 20 different people. Questions you answered last quarter. And the quarter before. And the quarter before that.
One of our customers in banking told us about their previous autonomous IGA solution: "It was very generic—the notifications didn't tell reviewers what they were supposed to review or what they needed to do. Reviewers had no context, so they just ignored the emails. We had to manually follow up with people on Slack even after the platform had sent notifications."
The punishment: The system sends a generic notification. The notification lacks context. Reviewers don't understand what they're supposed to do. They ask you. You explain. Individually. Repeatedly. Every single quarter.
You're compensating for bad system design with manual communication. And when reviews are delayed because reviewers didn't understand the instructions? You're blamed for poor communication.
The Compliance Pressure: You're Cramming for an Exam That Never Ends
Your ISO 27001 audit is in two weeks. The auditor will ask for evidence of quarterly access reviews.
You did them. Sort of. You have: A spreadsheet from Q1 (maybe Q2?). Some Slack messages. Email threads. Jira tickets for some requests. A partially completed Q3 spreadsheet. Q4... you might have skipped Q4 because of the incident.
You spend the weekend compiling "evidence." Searching Slack. Digging through email. Reconstructing timelines. Taking screenshots. Building a presentation.
You pass. Barely. The auditor writes: "Access review process needs improvement. Documentation is inconsistent."
You promise to fix it. You don't. Because you're too busy doing the next review.
A prospect we are talking to recently told us: "After the ISO 27001 certification last year—they now need something more reliable and efficient. Auditors may randomly pick one to see what it looks like."
The pattern repeats:
3 months before audit: Should start planning 2 months before audit: Really should start 1 month before audit: Launch reviews NOW 2 weeks before audit: Panic, scrambling Weekend before audit: Working late compiling evidence Day of audit: Hoping it's enough
You're not doing continuous governance. You're cramming for an exam. Every quarter. Forever.
And when the auditor finds gaps? When documentation is incomplete? When you can't produce evidence for something you definitely did but didn't capture? You're blamed for the control failure.
You're Set Up to Fail (The Frustrating Reality)
Let's be clear about what's happening here:
You're being asked to:
- Manually discover access across 50+ applications every quarter
- Make good decisions with incomplete information
- Get busy managers to review things they don't understand
- Execute hundreds of remediation actions manually
- Prove you did all of this with evidence scattered across five tools
- Do all this while handling your actual IT responsibilities
- Complete everything within rigid compliance timelines
- Achieve perfect coverage even for applications that can't integrate
And when this impossible task is incomplete, imperfect, or late, you're blamed.
Not the system that's designed to require superhuman effort. Not the approach that makes comprehensive coverage technically impossible. Not the process that provides insufficient information for good decisions.
You.
This is why it feels like punishment. Because you're being held accountable for outcomes you can't control, using tools that aren't designed to succeed, with expectations that aren't realistic.
What Actually Needs to Fix (And It's Not You)
The problem isn't that you need to work harder. You're already working incredibly hard.
The problem isn't that you need better spreadsheets or more detailed procedures. Documentation doesn't fix systemic design flaws.
The problem isn't that reviewers need better training. Training doesn't solve the lack of information.
The problem is the entire access review approach is designed wrong.
What needs to change:
Stop reconstructing access state every quarter. You shouldn't spend 2 weeks consolidating data. You should have continuous visibility into who has what access, automatically, all the time. The 30-day "consolidation" phase shouldn't exist.
Stop asking reviewers to guess. Reviewers shouldn't make decisions based on names and role titles with no context. They should see: last login date, privileged access indicators, what changed since last review, whether this person transferred departments, clear role definitions. Give them the information they need to make good decisions.
Stop treating reviews and remediation as separate phases. When a manager clicks "revoke," that action should either execute automatically via API or create a tracked task with clear ownership. The gap between "decision made" and "access removed" should be minutes, not weeks.
Stop scattering evidence across Slack, email, and Jira. Every review, every decision, every action, every approval should be automatically logged in one system with timestamps and context. When the auditor asks for proof, you should export a report, not spend 2 hours reconstructing history.
Stop making IT manually manage escalation. When a primary reviewer doesn't respond for 3 days (assuming the campaign timeline is 1 week,) the fallback should be notified automatically. With context. With access. Without IT having to monitor and manually intervene.
Stop sending generic notifications. Reviewers should receive clear, specific instructions: "You're reviewing 23 users in Salesforce. Here's why you're assigned. Here's what to look for. Here's the deadline. Click here to start." Not "Please complete your access review."
Stop maintaining two parallel systems. One workflow should handle both SSO-integrated apps (automated) and non-SSO apps (manual tasks with tracking). Same process, same audit trail, different execution paths.
Stop cramming for audits. Compliance should be an always-ready state. The audit report should be a button click, not a weekend project.
Here's what this means in practice:
If you have continuous access visibility, the 2-week consolidation phase disappears. If reviewers have decision-ready information, rubber-stamping decreases and review quality improves. If remediation is linked to reviews, the weeks-long manual cleanup phase disappears. If evidence is captured automatically, the weekend-before-audit scramble disappears.
The 30-day quarterly cycle becomes 3-5 days. Not because you're working faster. Because you're not doing work that shouldn't exist.
How to Explain This to Leadership
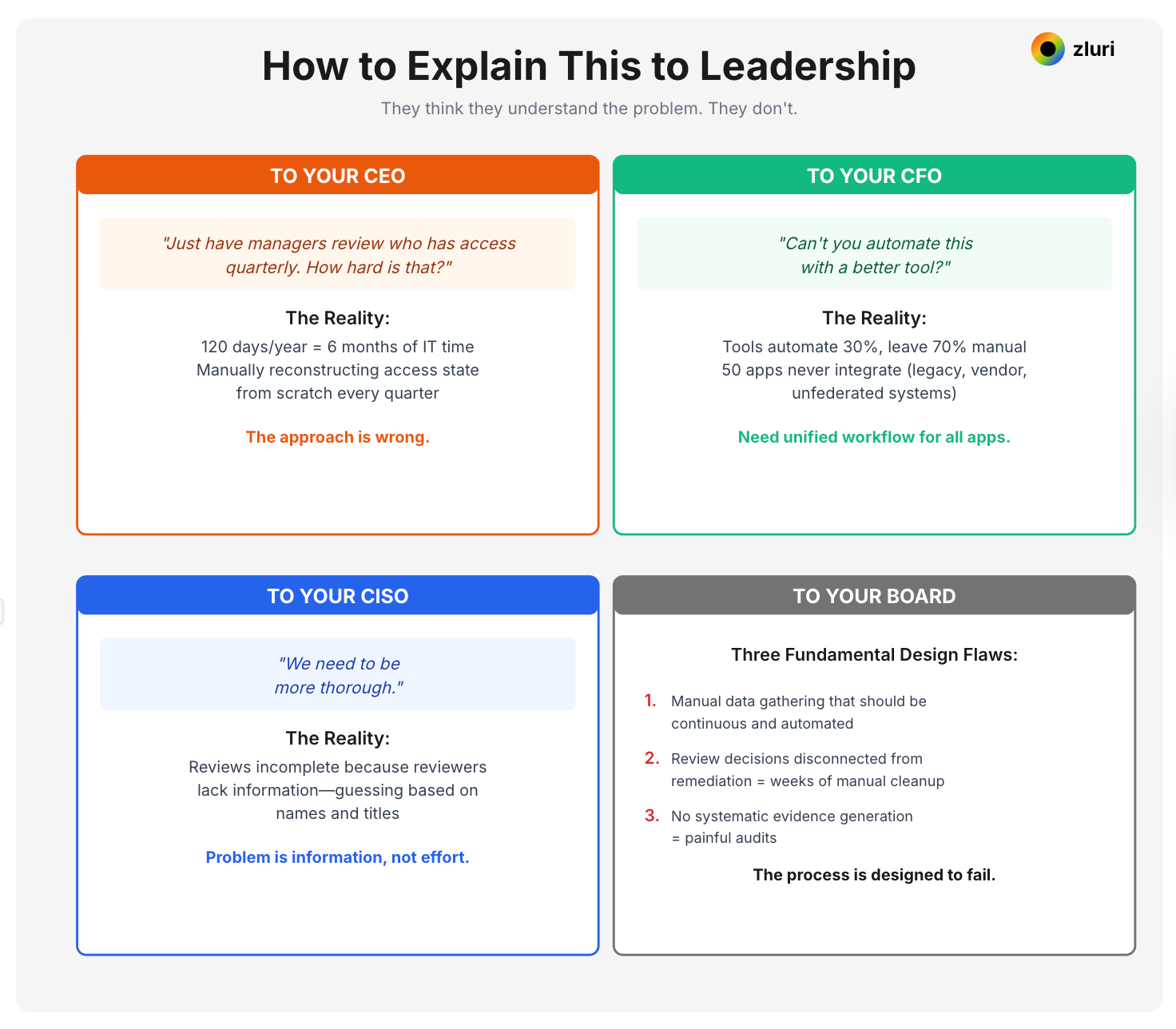
Your CEO thinks access reviews are simple: "Just have managers review who has access quarterly. How hard is that?"
Your CFO thinks it's an efficiency problem: "Can't you automate this with a better tool?"
Your CISO thinks it's a rigor problem: "We need to be more thorough."
They're all wrong. And they're wrong because they don't understand the systemic design problems that make this impossible.
Here's how to explain it:
To your CEO: "We're spending 120 days per year—6 months of IT time—on access reviews. Not because we're slow, but because the approach requires manually reconstructing our access state from scratch every quarter, then manually executing hundreds of revocations one by one. It's like asking someone to manually count every item in inventory every month instead of using an inventory system. The approach is wrong."
To your CFO: "Tools that automate 30% of the work still leave 70% manual. We have 50 applications that will never integrate with —legacy systems, vendor-managed tools, unfederated apps. We need an approach that handles both automated and manual apps in one unified workflow. Otherwise, we're paying for automation but still doing 2 weeks of manual work every quarter."
To your CISO: "The reviews are incomplete not because we're not thorough, but because reviewers don't have the information they need to make good decisions. They're guessing based on names and role titles. When we give them activity data, risk indicators, and change context, review quality improves dramatically. The problem is information, not effort."
To your Board: "Our access review process has three fundamental design flaws: First, it requires manual data gathering that should be continuous and automated. Second, it disconnects review decisions from remediation actions, creating weeks of manual cleanup. Third, it doesn't generate evidence systematically, making audits painful. We're not failing to execute the process. The process is designed to fail."
The Work You're Not Doing
You're spending 120 days per year on access reviews. That's half a product you could build. A security architecture you could redesign. A system you could transform.
For a company with 500 employees and 50 applications, that's 120 days × $150/hour fully loaded IT cost = $144,000 per year spent on access reviews.
What could you build with $144,000?
Instead, you're manually clicking "revoke" 200 times across 30 applications. Compiling evidence from Slack messages. Explaining the same thing to 20 managers who don't understand what they're reviewing. Watching the wheel turn again.
The punishment isn't the work. It's what you're not building while you're trapped in samsara.
Next Monday, your calendar reminder will pop up: "Q2 Access Review - Start Today."
Your stomach will drop.
Unless you stop turning the wheel.






.png)


.svg)














