How to do access reviews for compliances like SOC 2, ISO 27001, PCI DSS, HIPAA, SOX, and more, with the help of user access review software.
Manual access reviews are very painful for a lot of people. It's messy and time-consuming. It’s an ugly process, and no one wants to touch it.
We have helped hundreds of IT teams automate user access reviews at their companies. In our experience, there are three problems with manual user access review:
- There is no central repository for “who has access to what.” Hence, IT teams rely on spreadsheets and email threads to gather data from disparate systems. Because they often do not own all applications—particularly SaaS tools—IT teams must coordinate with various app owners to pull users and app lists, causing lengthy data collection cycles.
- Reviewing access rights is difficult, even after users and app lists are collected, with no context to guide whether to keep or revoke access.
The reviewers—department heads or local admins—are too busy, and it’s too difficult or time-consuming for them , so it just ends up sitting in their inbox.
As a result, IT teams end up conducting the review, and the problem with IT approving or disapproving users' access to an app is that IT doesn’t really know who actually needs what permissions. Often, IT is forced to guess, leading to potential over-provisioning or under-provisioning.
This is more problematic at companies with different locations, subsidiaries, or business units. It’s really difficult to have one or two people conduct the access review when they do not have boots on the ground.
- Remediation is very difficult and time-consuming. It often doesn’t get done because it’s ‘someone else’s job’ or too complicated to track.
But meeting tight compliance deadlines doesn’t have to be so difficult. In the next section, we’ll discuss the key factors to consider when choosing a User Access Review Software.
Factors to Consider When Choosing a User Access Review Software
Not all user access review tools are the same, and your choice should be guided by your organization's specific needs and the tradeoffs you're willing to make.
- Consider your organization's size (i.e., the number of users you need to manage) because vendors cater to specific customer bases, which are often categorized based on the company employees. Any vendor claiming to be a good fit for all company sizes is a bad choice.
- Evaluate your IT environment—whether most of your systems are on-premises, SaaS, or custom-built applications. This affects your integration requirements. Some vendors focus on on-premises, some on SaaS, and some on cloud or hybrid.
- Additionally, budget constraints play a crucial role; some solutions offer advanced automation and analytics but may come at a premium, while others provide essential functionalities at a lower cost. With user-access review software, more features are not always better—especially for mid-size enterprises (<5000 employees). In our experience helping companies optimize SaaS license costs, many features can remain unused, and companies can do their work with better products or license plans.
Here’s what to prioritize while looking for user access review software:
1. Integration Coverage Across Your Key SaaS Applications
User access review tools rely on integrations to pull data about identities, roles, and access privileges. The broader and deeper its integrations, the easier your reviews become.
When talking to a user access review (UAR) vendor, ask them about:
- Out-of-the-Box Integrations: Check whether the user access review tool supports direct integrations with your most critical apps—especially for IDPs (e.g., Google Workspace, Azure AD), HRMS, CRM, finance systems, and any system storing sensitive data.
Note that while you may have 100s of systems in your company, most compliance frameworks require access reviews only on applications with sensitive data. In our experience, mid-size companies (having 500-5000 employees) usually require access reviews for 10-50 apps.
- Multiple Instances Support: Many organizations have multiple IDP tenants. This is common among companies that have subsidiaries or that have gone through mergers or acquisitions. Also, multiple instances are common in apps like GitHub or Docker in companies operating in multiple locations. Ensure the tool can handle this.
2. Actionable Insights for Faster, More Accurate Reviews
Large, unfocused reviews often cause “rubber-stamping,” where reviewers simply check “Approve All” if they have no context or if the list is too large.
To avoid this, check if the user access review solution provides:
- Risk-Based Insights: The right user access review software provides risk-based contexts on users' accounts—such as orphaned accounts, external users, and elevated privileges—so reviewers can approve or disapprove access based on these insights. Without such insights, reviewing user access rights is no different than reviewing on a spreadsheet. It's still a guessing game.
- Option to Delegate or Reassign the Reviewer: This is an important feature, yet many user access review tools in the market don't have it. This feature allows managers to delegate the reviews to another person. This helps in better collaboration as this is managed at a local level by the reviewer.
Outcome? Faster, more accurate reviews that truly mitigate risk—rather than just checking a compliance box.
3. Flexible Campaign Setup for Streamlined Access Reviews
User access review solutions should adapt to your organization’s workflows, not the other way around. Key capabilities to look for in user access reviews software:
a) Automated and Repetitive Campaigns
This is because almost all compliances require you to do access reviews on a periodic basis. For instance, SOC 2/ISO 27001 requires you to do a quarterly access review.
- Campaign Templates and Scheduling: Instead of re-creating campaigns from scratch each time, look for solutions that let you reuse past campaigns. Furthermore, tools that allow you to schedule UAR campaigns save significant administrative overhead.
b) Reviewer Management
This is often overlooked. Almost all companies make this mistake. We have seen IT teams not thinking ahead on this, and later, things can get stuck when they assign to the wrong reviewer. Because their tool doesn't allow them to delegate or if they are on vacation. The tool should give options like the fallback reviewer, multi-level reviewer, and role-based reviewer.
- Fallback Reviewers: A fallback reviewer should be automatically assigned if the primary reviewer is absent or on vacation.
- Multiple-Level Approvals: Complex organizations may need multi-tier reviews (e.g., immediate manager, then security team).
- Role-Based Reviewers: Avoid hardcoding individuals. Assign reviews dynamically based on roles (e.g., “Team Lead for Marketing” instead of “John Doe”).
c) In-Campaign Remediation Setup
- Remediation Workflow: Ensure corrective actions (like revoking or downgrading access) can be launched within the same campaign process. This keeps everything in one place and creates a complete audit trail. This brings us to our next point.
4. Built-In Remediation to Automate Issue Resolution
It’s not enough to simply identify and mark improper access; you need to act on it. A lot of user access management solutions leave you halfway just helping with the reviewing. A key part of the user access review process that you need to present to auditors is what corrective actions you've taken.
But if you do the remediation manually, this semi-automated process still leaves a lot on your plate. Even conducting AR across 10 apps with 50 users can leave 100s of remediation actions. This is very time-consuming.
- Auto Remediation: Most of the user access review (UAR) tools that claim to fully automate the access review process actually create tickets in your ITSM platform, leaving the burden on IT to remove access manually. Ideally, the UAR solution should be able to revoke access directly in the integrated system.
- Audit-Ready Evidence: For compliance, you must show proof of what was removed or adjusted, not just that you “recommended” it. A solution that automatically implements and logs changes helps you demonstrate a closed-loop process.
5. Long-Term Identity Governance and Administration (IGA) Needs
Usually, access reviews is not the end goal of identity governance. It is the first step towards it. If not immediately, you would eventually want to automate a lot of stuff that helps you ensure the right people have the right level of access to the right tool at the right time.
So, also look for your needs beyond user access review. These features are provided as lifecycle management, granular access management, and self-service access requests. These can be part of the overall IGA product or sold separately by the vendor.
- Lifecycle Management (LCM): Eventually, you’ll want to automate provisioning, de-provisioning, and role management to ensure that the right people have the right level of access at all times.
- Self-Service Access Requests: Many organizations transition to a model where employees can request access, get automated approvals based on policies, and have that access automatically revoked when it’s no longer needed.
- Cost and Scalability: If the vendor’s entire IGA solution is sold as a bundle, you may unlock these extended features without an additional per-feature fee. If they are separate modules, weigh these costs against your roadmap.
Note: Zluri offers all the above capabilities and is best suited for mid-size organizations (500-5000 employees).
To learn more about how Zluri can simplify access reviews and meet your long-term IGA needs, book a demo today.
Top User Access Review Software
Selecting the right user access review software can transform how you manage access reviews. From automating review processes to helping you maintain compliance, these tools reduce manual effort and improve review accuracy.
Below are some of the top user access review tools to help you conduct more effective user access reviews.
1. Zluri
At Zluri, we have a visibility-first approach to identity governance. With our discovery engine, Zluri provides 100% visibility across your entire SaaS environment. This ensures IT teams gain a clear understanding of who has what level of access to which applications.
By consolidating user access data from all connected SaaS tools into a single, centralized platform, Zluri eliminates the need for a time-consuming manual data collection process. This unified approach simplifies access reviews, allowing IT teams to easily identify access anomalies, optimize permissions, and maintain continuous compliance.
What makes Zluri different from other user access review tools in the market?
- Seamless integrations to cover all your SaaS apps
Zluri makes user access reviews faster and more effective with out-of-the-box integrations with 300+ SaaS applications. This enables Zluri to bring all apps, users and access data into one centralized dashboard.
“We thought that we have around 100 SaaS applications… It appears we have more than 300+ apps. Most of them are unknown to IT.” – Shahar Cohen, IT Technician, Assured Allies.
Plus, connecting SaaS applications is easy, even if you're not the owner. Either you can email them or share a connection link with them.
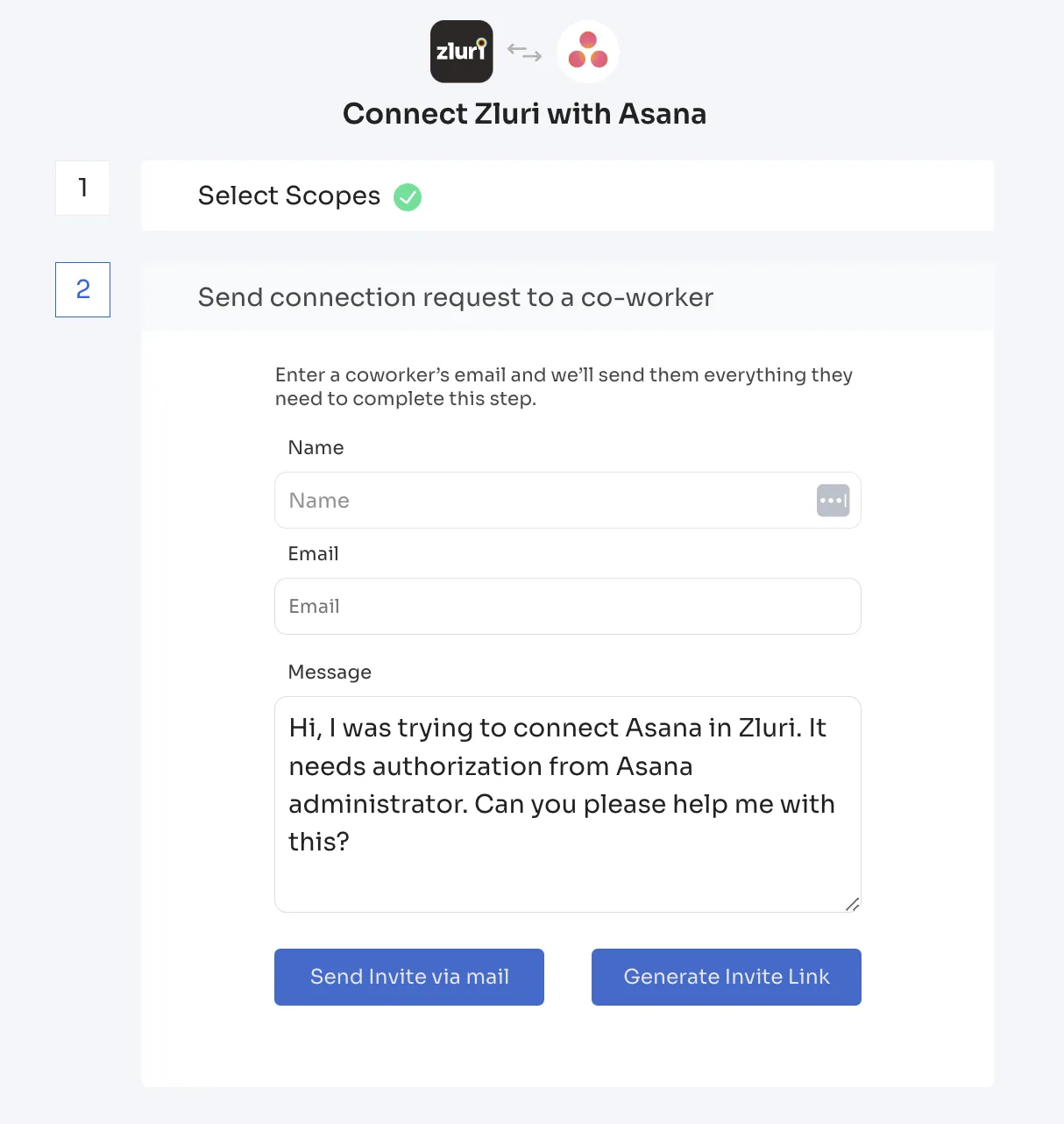
All user types, including third-party users (consultants, partners, vendors, contractors, etc.) and service accounts, are part of the standard access reviews solution. Unlike other UAR tools, we don't charge separately for managing non-employees or machine identities, making up a good fit for mid-size organizations with not-so-deep pockets.
Another big reason many companies chose Zluri is that we can integrate multiple instances of an application (multiple IDP and SSO). You can select an authoritative data source if data exists in different systems.
Another reason companies choose Zluri is that we can connect with apps that don't offer SCIM integration or are not connected to your SSO. Many companies don't connect the app with SSOs like Okta to avoid the SSO tax. However, it becomes an issue during access reviews, as they can't revoke or modify users' access to these apps that are not connected to SSO. From our experience, that's applicable to the majority of the SaaS applications for mid-sized enterprises.
- Auto remediation to resolve access issues
The second biggest differentiator of Zluri is closed-loop remediation. We don't leave you halfway. We truly automate user access reviews by actually revoking the access instead of creating IT tickets for manual corrections. Here's how Zluri stands out:
Unlike tools that merely flag access issues and create tickets for IT teams to resolve manually, Zluri enables direct, real-time remediation. You can do this during the access reviews campaign setup.
You'll have two options:
1.To revoke access, or
2.To modify access
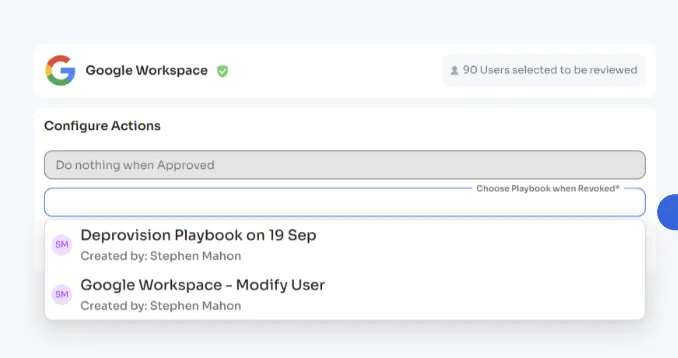
This action helps minimize security risks by swiftly removing unauthorized access.
Another unique capability of Zluri is remediation beyond access revocation, i.e., role & license adjustment. Zluri doesn’t stop at just revoking access—we provide granular control over user roles (e.g., user, analyst, finance, admin) and license management (e.g., basic, standard, pro plans).
IT teams can downgrade or upgrade user roles (such as switching user roles from admin to a regular role or vice versa) and adjust license types (like changing from a pro to a basic plan or vice versa) directly within the platform. This flexibility allows organizations to right-size access permissions and licenses based on actual user requirements, improving security and reducing unnecessary SaaS costs.
Another similar use case is permission management within apps. For example,
- Remove or add users to specific channels in Slack or
- Remove or add users to certain boards in Trello
- Risk-based Recommendations to Prioritize High-Risk Access Decisions
Zluri provides risk-based insights to help reviewers make informed decisions. It flags potential security risks, such as dormant accounts and high-privilege access, by analyzing user roles, activity levels, and permission structures.

- Dormant Access Identification: Dormant accounts—users who no longer access certain applications—can become a security loophole if left unchecked.
Suppose a contractor who no longer works with your company still has access to a tool like Asana. Zluri identifies this dormant access and alerts your team to revoke it, closing the security gap.
- High-Privilege Access Monitoring: Accounts with elevated privileges, like admin rights, can be risky if not managed properly. Zluri highlights these accounts so IT teams can review whether the user really needs that level of access.
For example, if an IT admin with full control over financial systems is only responsible for managing user accounts, Zluri might suggest downgrading their privileges to reduce security exposure.
These insights improve security posture and help maintain compliance with organizational access policies.
- Multi-Level Approval to Ensure Accountable Access Reviews
Zluri streamlines your access review process by enabling configurable multi-level approval workflows. Instead of relying on a single approver, Zluri lets you involve multiple stakeholders—like department heads, security managers, and IT administrators—to ensure access requests are thoroughly vetted at every step.
For example, when an employee requests access to financial data, you can configure the workflow. - a. Initial Reviewer (e.g., Department Manager): Verifies if the access is still needed from a functional standpoint.
- b. Security/IT Teams: Validates alignment with corporate security policies and broader risk considerations.
- c. Executive or Specialized Compliance Approver (Optional): In highly regulated industries, certain entitlements may also require sign-off from compliance officers or executive stakeholders.
With Zluri, you can customize these workflows to match your organization’s requirements, reducing errors, improving accountability, and maintaining compliance—all while saving time and eliminating manual coordination efforts.
This is very helpful for dealing with sensitive data in specific industries, like healthcare and finance, or when doing UAR for critical applications.
Zluri goes beyond simplifying access reviews with features designed to keep your organization audit-ready and compliant. You can generate detailed, audit-ready reports with just a few clicks, offering complete visibility into access decisions and remediation actions.
These reports are supported by comprehensive audit logs that track every activity, providing a clear trail for accountability and simplifying compliance audits.
“Zluri has revolutionized how we manage access reviews. The audit-ready reports have made compliance seamless.” – Sejal Chadha, IT & Security Manager, Pano AI
Besides the features and capabilities we covered throughout this article, Zluri also offers:
- Access Management
- Joiner-mover-leavers workflow automation
- Self serve Access requests
- Time-bound access
- SaaS management
- License optimization
- IT Contract management
- Shadow IT discovery
If managing SaaS discovery and identity governance separately feels overwhelming, Zluri can be your go-to choice, as it provides a single platform for identity governance.
Book a demo to see how Zluri simplifies identity governance in a single platform.
2. SailPoint IdentityIQ

SailPoint IdentityIQ is a comprehensive identity governance solution built for enterprises that need to automate and secure user access across diverse systems. It helps you manage identities at scale by automating access reviews, enforcing governance policies, and streamlining lifecycle events such as onboarding, role changes, and offboarding.
What sets IdentityIQ apart is its ability to leverage AI and machine learning to spot unusual access patterns and make smarter access decisions. By integrating with both on-premises and cloud environments through an extensive connector library, the solution provides centralized visibility into user access across your IT landscape.
Key Features
- Self-Service Access Requests with Automated Approvals: Instead of relying on back-and-forth emails, IdentityIQ provides a self-service portal where users can request access directly. IT teams receive all requests in a single interface, making it easy to track, review, and approve access efficiently—ensuring users get the right access without delays.
- Automated Compliance Management: Staying audit-ready is simpler with automated access certifications. SailPoint IdentityIQ schedules and streamlines periodic access reviews, allowing managers and auditors to regularly verify user access. With flexible scheduling options (quarterly, annually, or based on compliance needs), you can maintain regulatory alignment effortlessly.
3. CyberArk Identity

CyberArk Identity is an identity security solution that helps you efficiently manage user access across cloud, on-premises, and hybrid environments. It simplifies access governance by automating key aspects of user access reviews while enhancing visibility and compliance.
The platform streamlines periodic reviews and empowers IT teams to take control of access privileges and security risks. With actionable insights and seamless integration capabilities, CyberArk Identity ensures that access remains secure and compliant with organizational policies.
Key Features
- Access Discovery for Complete Visibility: Tracking who has access to what can be a challenge, especially in large organizations. CyberArk Identity automatically discovers and maps user access across your IT environment, helping you identify excessive or unnecessary permissions and ensure access aligns with security policies.
- Automated Access Certification Campaigns: Manually reviewing access rights is time-consuming and prone to errors. CyberArk Identity lets you schedule and automate periodic access reviews, ensuring that managers and reviewers can regularly verify and adjust user access—keeping your environment secure and audit-ready.
- Comprehensive Reporting and Analytics: Understanding access trends is crucial for governance and compliance. CyberArk Identity provides detailed reports and analytics, giving you clear insights into access patterns, risks, and anomalies. These reports make it easier to demonstrate compliance and make informed decisions about access governance.
4. Vanta

Vanta helps you stay audit-ready by automating compliance processes, reducing manual effort, and continuously monitoring your security posture. It integrates seamlessly with existing systems, giving you real-time visibility into your compliance status while supporting frameworks like SOC 2, ISO 27001, and HIPAA.
Key Features
- Automated Evidence Collection for Access Reviews: Manually gathering access data for audits can be tedious and error-prone. Vanta automates evidence collection from cloud platforms, identity providers, and other systems, ensuring that your user access documentation is always complete and audit-ready.
- Continuous Monitoring of User Access: Compliance isn’t just a once-a-year task. Vanta continuously tracks user access changes, flagging configuration issues and security risks before they become compliance violations. This helps you maintain a proactive approach to access reviews.
- Audit-Ready Reporting for User Access: You need clear and accurate reporting when it’s time for an audit. Vanta automatically compiles user access review reports, presenting compliance data in a way that auditors can easily assess—saving you time and reducing complexity.
5. Drata

Drata helps you streamline user access reviews by automating repetitive tasks and gathering comprehensive access data across your systems. Its integration capabilities ensure minimal disruption to existing workflows, allowing you to maintain compliance efficiently.
Key Features
- Scheduled Access Reviews: No more chasing manual reminders or tracking review cycles yourself. Drata lets you schedule recurring access reviews, ensuring they happen on time, every time—without manual intervention.
- Reviewer Assignment Made Easy: Getting the right people involved is critical for accurate reviews. With Drata, you can assign specific review tasks to managers and system owners, making it easy for them to approve or revoke access efficiently.
6. OneLogin by One Identity
OneLogin by One Identity lets organizations streamline user access management while ensuring compliance with regulatory requirements. Its automation capabilities reduce manual intervention and help maintain a secure, policy-driven governance environment.
Key Features
- Customizable Access Review Campaigns: Every organization has different compliance requirements. OneLogin allows you to customize access review campaigns, focusing on high-risk roles or systems. This ensures reviewers spend time on critical access decisions rather than blanket evaluations.
- Role-Based Governance: Managing access manually can lead to errors and inconsistent practices. With OneLogin, you can define and enforce user roles, simplifying access assignments and revocation while maintaining control across departments.
- Detailed Compliance Reporting: When audit season arrives, you need clear data. OneLogin provides comprehensive reports with insights into user access actions, approvals, and policy enforcement. This streamlines audit preparation and demonstrates compliance effectively.
7. MidPoint by Evolveum (Open Source)

Keep your identity data accurate and up to date with MidPoint’s advanced synchronization features. With a centralized view, you control who has access to what—and why—ensuring security and compliance. Automate access requests to speed up identity processes and reduce manual effort. As your organization grows, midScale enhancement helps you seamlessly scale identity governance, handling deployments even with tens of millions of identities.
Key Features
- Streamline access with Policy and Role Management: Automate access control with role-based (RBAC) and attribute-based (ABAC) policies, so users get the right permissions based on their roles, departments, or other attributes. With midPoint, you can easily manage roles and access rights across your business while keeping security and compliance in check.
- Gain visibility with Auditing & Reporting: Keep track of who accessed what, when, and why with detailed audit logs and reports. midPoint lets you trace all interactions, generate compliance reports, and review access decisions with built-in feedback mechanisms—so you always stay in control.
- Keep access in check with Access Certification: Regularly review and confirm user access to make sure only the right people have the right permissions. With midPoint, you can automate certification campaigns, simplify approvals, and quickly remove unnecessary access to strengthen security and maintain compliance.
8. OpenIAM (Open Source)
With OpenIAM, you get a flexible, scalable solution that adapts to your organization’s needs— whether you’re reviewing access across SaaS, on-premises, or even non-integrated applications. Instead of juggling between multiple spreadsheets and follow-ups, you can customize workflows, enforce deadlines, and ensure compliance effortlessly. OpenIAM helps you complete reviews up to 85% faster, reducing administrative burden while keeping your environment secure.
Key Features
- Multi-Level Approval Workflows: OpenIAM lets you define approval hierarchies based on risk—whether it’s a quick manager review or a multi-step approval process for high-risk access. This ensures that critical permissions are properly reviewed without unnecessary bottlenecks.
- Delegation for Senior Executives: C-level executives don’t have to get involved in access reviews. OpenIAM allows them to assign trusted delegates who can complete reviews on their behalf, ensuring high-level approvals happen on time while maintaining full accountability.
- Enforced SLAs and Smart Escalations: Missed access reviews can lead to compliance risks. OpenIAM helps you stay on track with automated reminders and escalation paths—if a review is delayed, it’s automatically reassigned or flagged for higher-level intervention. This keeps reviews moving and ensures compliance deadlines are met.
9. Opal Security
Keeping up with user access reviews can be a headache, especially when juggling multiple systems and compliance requirements. Opal automates access reviews, so you don't have to rely on spreadsheets or manual tracking. With real-time visibility and seamless workflows, you can ensure the right people have the right access without the extra workload.
Key Features
- Automate Access Reviews for Compliance: Manually reviewing user access for SOX, SOC 2, ISO 27001, or HITRUST compliance can be tedious and time-consuming. Opal automates the entire process, making it easy for you to verify access without the manual back-and-forth. The platform ensures reviews happen on schedule, so you can stay compliant without unnecessary effort.
- Get Full Visibility Into User Access: Instead of digging through different systems to check who has access to what, Opal gives you a centralized view of all user permissions. You can quickly spot excessive access, enforce the least privilege, and fix security risks before they become problematic.
- Streamline Reviews with Simple Approvals: You won't have to chase down approvals or wait for email responses anymore. With Opal, you can review and approve access requests directly through Slack or a web interface. System owners can set up automated approval rules, security checks, and revocation workflows, making the entire process smoother and more secure.
10. Saviynt
User access reviews can feel like a never-ending task, but Saviynt makes them faster and smarter. With AI-driven automation, you get clear visibility into who has access to what, so you can quickly approve low-risk access and flag anything that needs attention. Instead of spending hours on manual reviews, you can streamline the process, reduce risk, and stay compliant—without the extra workload. Plus, with a cloud-native platform, you can get up and running fast and see results in just weeks.
Key Features
- Centralized Access Reviews in One Place: No more jumping between systems—Saviynt lets you manage all human and machine identities from a single control panel, making reviews easier and more consistent.
- AI That Speeds Up Decision-Making: Why waste time reviewing every request manually? Saviynt’s AI automatically approves low-risk access and flags anything suspicious, cutting review time by 70% so you can focus on what matters.
- Just-in-Time Access for Tighter Security: Instead of letting users keep access they don’t need, Saviynt enables just-in-time access—so permissions are granted only when necessary. That means fewer security risks and stronger Zero Trust enforcement.
11. Omada Identity

Keeping up with user access reviews can be overwhelming, especially when managing entitlements across multiple systems. Omada Identity makes the process seamless by automating access reviews, providing real-time visibility into user permissions, and ensuring that only the right people have the right access. With risk-based insights and built-in compliance controls, you can quickly identify policy violations, remediate excessive access, and stay audit-ready without manual effort.
Key Features
- Risk-Based Access Reviews with Full Visibility: Omada gives you a centralized view of all user entitlements, making identifying and reviewing high-risk access easy. Instead of sifting through spreadsheets, you get automated risk analysis that flags excessive permissions, helping you prioritize reviews based on actual security impact.
- Compliance-Driven Review Processes: With predefined policies and a compliance dashboard, Omada ensures that every access review aligns with regulatory standards like SOX, GDPR, and ISO 27001. The platform tracks and documents reviews and triggers remediation actions when unauthorized access is detected, reducing the risk of non-compliance.
- Automated Review Workflows for Efficiency: Manual access reviews slow down decision-making and increase errors. Omada automates review scheduling, notifications, and approvals, so you can complete reviews faster while ensuring accuracy. Integrated workflows streamline revoking unnecessary access, helping you enforce least privilege without administrative burden.
12. BetterCloud
User access reviews don’t have to be a manual, time-consuming process. With BetterCloud, you can automate access tracking, detect risks, and enforce policies, making it easier to review and adjust user permissions as needed. You also get real-time visibility into roles and access levels, so you can streamline compliance efforts, prevent excessive privileges, and ensure security policies are enforced without constant oversight.
Key Features
- Automated Access Reviews with Compliance Reporting: No more manual audits—BetterCloud tracks permissions across your SaaS applications, helping you quickly identify excessive access. Automated reporting documents review history and policy enforcement, making it simple to prove compliance when needed.
- Role-Based Access Controls and Auto-Revocation: Granular permission controls make managing admin access easier. BetterCloud lets you automate role assignments, enforce access limits, and revoke super admin privileges automatically when users exceed set thresholds, reducing the risk of overprivileged accounts.
- Policy-Driven Access Monitoring: BetterCloud continuously monitors user entitlements, ensuring access policies are followed. If risky access is detected, automated workflows step in to trigger remediation, keeping user permissions secure and compliant.
Take Control of User Access Review with the Right Software
By now, you’ve seen why a user access review software isn’t just a nice-to-have—it’s essential. Whether you’re aiming for compliance or strengthening security, the right tool makes all the difference. Automating UAR reduces manual effort, ensures timely audits, and helps enforce the principle of least privilege without the usual headaches.
Book a demo to see how Zluri automates user access reviews to ensure compliance, enhance productivity and strengthen security.









.svg)














