A structured overview of how to think about relative priorities among Joiner–Mover–Leaver (JML) processes, taking into account the practical realities of compliance, user access reviews (UAR), lifecycle automation, and granular access management. The goal is to help you determine where to start and how to expand your Identity Governance and Administration (IGA) efforts in a pragmatic manner.
1. Identify the Immediate Drivers
- Compliance Requirements
- If your organization faces immediate compliance needs (e.g., audits on the horizon or strict regulatory obligations), a User Access Review (UAR) platform often becomes a top priority.
- If you have no pressing compliance or regulatory deadlines, you may find it challenging to allocate time from stakeholders for UAR.
- Business & Operational Factors
- Rapid Growth: If headcount is increasing rapidly, automating provisioning (especially onboarding) can significantly reduce large amounts of IT overhead.
- High Attrition: If your organization experiences frequent departures, efficiently addressing deprovisioning and revoking access becomes critical from a security perspective.
- Recent Mergers & Acquisitions: These typically trigger both a surge in new hires (through integration) and departures, meaning you need robust offboarding processes to mitigate risk and consistent onboarding to ensure a positive user experience.
- Security vs. Productivity
- Provisioning focus: If users are constantly waiting for essential access to perform their jobs, prioritize automating provisioning (for joiners and movers).
- Deprovisioning focus: If the biggest concern is dormant or leftover accounts that could be exploited, start with automating deprovisioning (Leavers).
2. Start with JML Before Granular Access
Within the JML framework, many organizations see quick wins by automating Leaver and Joiner processes first, because:
- Leaver (Offboarding) Automation
- Quick to implement with the right tools.
- Prevents lingering access for employees who have left the organization.
- Identifies accounts that could be orphaned or pose a security threat.
- Spreadsheet and manual approaches fail when you lack a clear view of which systems the user has access to.
- Side effect - license and cost optimization - SaaS management
- Joiner (Onboarding) Automation
- Define “birthright” or “day-one” access for new hires (e.g., email, HR systems, core collaboration tools).
- Quick to demonstrate ROI because it enhances employee productivity and saves time for IT.
- Commonly includes:
- Enterprise-Wide (IT-Centrally Managed) Apps: Single sign-on environment, email, intranet, etc.
- Department-Level (Line-of-Business) Apps: Systems owned/managed by specific departments.
- Mover (Mid-Lifecycle Changes) Automation
- More complex because you must track changes in role, department, location, or even acquisitions.
- Involves both provisioning of new entitlements and deprovisioning of old entitlements.
- Particularly critical in organizations with frequent internal transfers or reorganizations.
Key takeaway: Automating offboarding first is often simpler, but onboarding quickly follows to maximize operational efficiency and user satisfaction. Then address movers, as they require both provisioning and deprovisioning in a single workflow.
3. Sequence & Strategy for Provisioning
When moving from basic to more advanced provisioning workflows, consider:
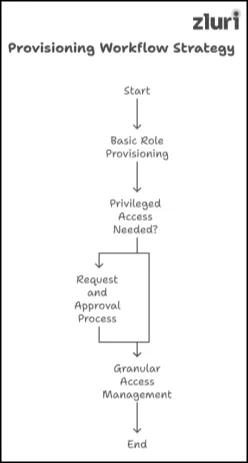
- Basic Role Provisioning (Birthright Access)
- Establish base roles (e.g., “All Employees,” “Contractors,” “Sales Team,” etc.).
- Automate the provisioning of these standard sets of entitlements upon hire.
- Simplifies the bulk of user provisioning without requiring the definition of every possible granular role upfront.
- Privileged or Specialized Access
- Keep it out of the “birthright” flow.
- Use a request and approval process, possibly with multiple levels, for high-risk entitlements or roles.
- Example: Admin rights in critical systems, access to sensitive data in Salesforce, etc.
- Granular Access Management
- After basic roles are stable, expand to non-standard resources with smaller user bases or more complex access models.
- Examples:
- Slack channels or Trello boards.
- Specific project repositories in GitHub.
- Specialized data sets, customized reports, or departmental file shares.
4. Expanding Scope Strategically
Once you have the core JML flows (especially onboarding and offboarding) stable, you can expand your IGA scope by focusing on:
- Apps with Sensitive Data
- Prioritize applications that store highly confidential or regulated information (e.g., customer data, financial records, PII).
- Apps with High User Counts
- Automate provisioning where it will have the biggest impact on efficiency.
- For instance, a globally adopted collaboration tool or a critical enterprise system.
- Targeted Departments / Locations
- If certain departments (e.g., Sales) or regions have high turnover or complex access needs, they are prime candidates for JML automation.
- If you’ve recently done an M&A in a specific subsidiary, focus on that entity first to reduce risk.
- Incremental Resource Coverage
- Gradually fold in new applications as you refine the core processes and gather reliable system/application owners.
- This iterative approach helps you avoid “boiling the ocean” and spreads the load among stakeholders more evenly.
5. Tying It All Together
- Decide Where to Focus First
- If security and lingering accounts are your top concern, start with offboarding.
- If business productivity or rapid onboarding is the main pain point, focus on provisioning first.
- Establish Baseline Roles & Processes
- Automate the “birthright” access every new hire receives.
- Define a clear path for removing that same set of access upon termination.
- Add mover processes to prevent changes in user status from creating orphaned entitlements.
- Introduce UAR or Periodic Reviews
- If compliance is looming or your environment is complex, rolling out UAR ensures that users, owners, and auditors are aware of who has access to what.
- If compliance is not immediate, you can initially gather entitlements, build a robust identity source of truth, and then gradually introduce UAR once stakeholder time is available.
- Scale to Granular Access
- After solidifying your role-based approach, tackle specialized permissions or lesser-used applications.
- Use an access request and approval model for any privileged access, ensuring you track who approved each request and the reasons behind their approval.
Final Thoughts
By prioritizing Leavers first (for quick security wins), then Joiners (to boost productivity and reduce manual work), and finally, handling Movers, you build a strong foundation for your overall Identity Governance strategy. From there, you can tackle more advanced needs, such as granular entitlements, complex departmental tools, and formalized User Access Reviews. This incremental, business-driven approach ensures you not only align with compliance requirements but also deliver visible value to end-users and management.









.svg)














