Every identity activity starts with the same question: Who has access to what?
Your IT team needs to answer it to provision new employees and deprovision departing ones. Your security team needs to answer it to assess risk exposure. Your compliance team needs to answer it to satisfy auditors. And your finance team needs to answer it to optimize SaaS spending.
It's a simple question. Yet, most organizations can't answer it.
They can tell you which applications they've purchased. They can pull user lists from their SSO provider. They can export reports from individual applications.
But ask them:
"Which 47 employees have admin access to systems containing customer data?" or "Who retained access after transferring from engineering to marketing?" or "What applications did the contractor who left last month still have access to?"
And they start guessing.
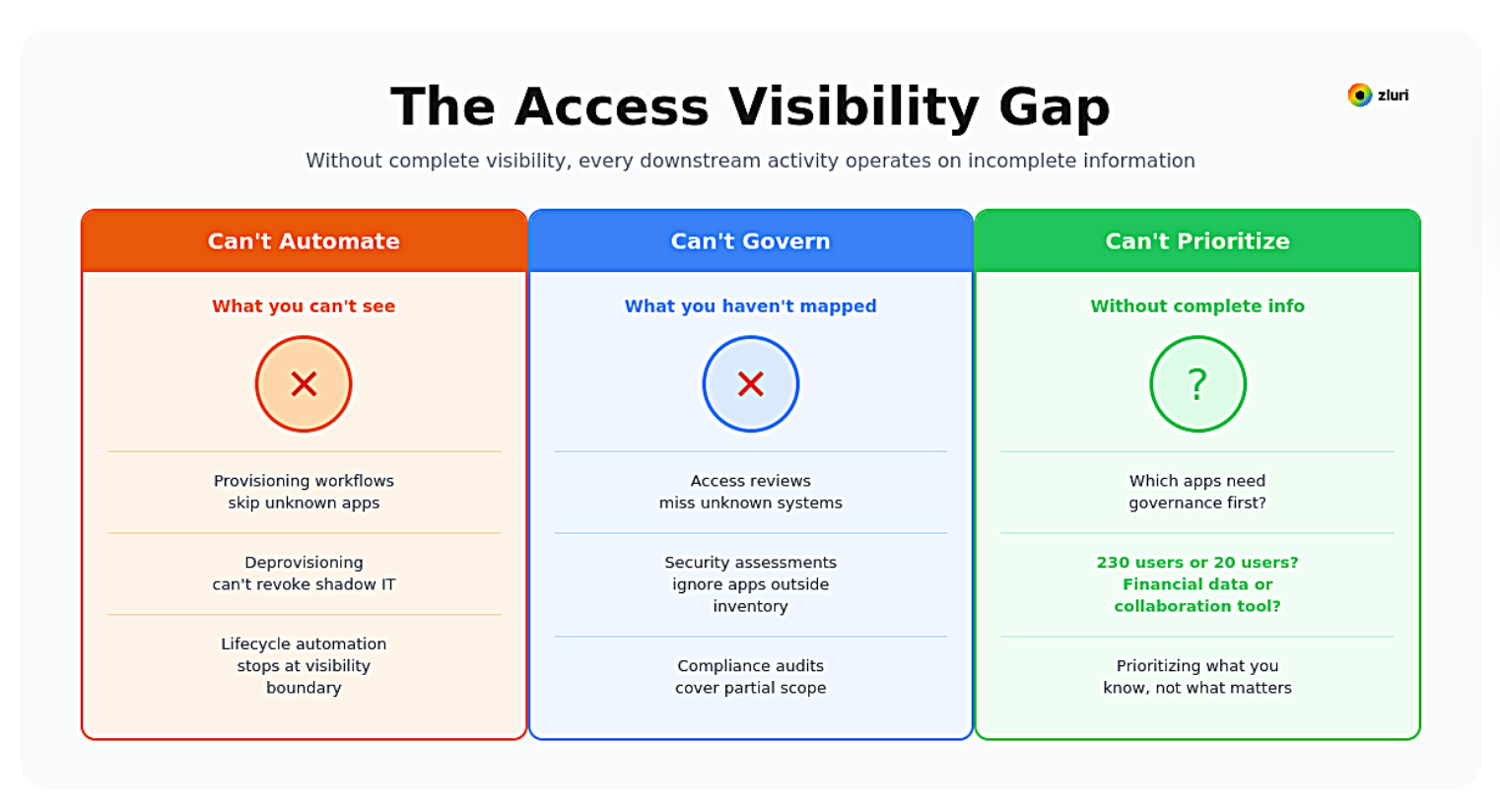
This is the access visibility gap. Without knowing what applications exist, who has access to them, and how that access is being used, every downstream activity—governance and administration alike—operates on incomplete information.
- You can't automate what you can't see. Access provisioning workflows can't include applications you don't know exist. Deprovisioning checklists can't revoke access to shadow IT. Lifecycle automation stops at the boundary of your visibility.
- You can't govern what you haven't mapped. Access reviews validate permissions for known applications while unknown systems accumulate unreviewed access. Security assessments miss applications outside your inventory. Compliance audits cover partial scope and call it comprehensive.
- You can't prioritize without complete information. Which applications need governance first? Without visibility, you're prioritizing based on what you happen to know about, not what actually matters.
However, once you have visibility, the answers become clear: The application with 230 users gets automated before another tool with 20 users. The system with admin access to financial data gets reviewed before the departmental collaboration tool.
Access visibility isn't a feature of identity governance. It's the foundation that identity governance and access management must be built on.
Table of Contents
- The IGA Paradox: Excellent Governance, Incomplete Scope
- Why the Governance-First Model Fails in Modern SaaS Environments
- Why Traditional Discovery Methods Can't Close the Gap
- The Three Visibility Gaps (And Why Manual Methods Fail)
- The Real Consequences of Incomplete Visibility
- What Visibility-First Actually Means
- What You Need for Complete Access Visibility
- Implementation Timeline: 30 Days to Complete Visibility
- Getting Started With Access Visibility
The IGA Paradox: Excellent Governance, Incomplete Scope
Modern identity governance platforms are powerful. They automate provisioning workflows, enforce least privilege policies, conduct scheduled access reviews, and generate compliance reports.
They excel at what they're designed to do—govern access to applications you've identified. But the problem isn't the governance capabilities. The problem is what gets governed.
Most IGA platforms, including modern SaaS-focused ones, operate on a governance-first model. You tell the platform which applications to manage, and it manages them perfectly:
- Access policies are enforced.
- Reviews are automated.
- Deprovisioning happens on schedule.
For those applications in the system, governance is strong.
But this approach assumes you know what applications exist in your environment.
In our work with hundreds of organizations, we've found that assumption is dangerously wrong.
Shadow applications don't just exist alongside managed applications—they outnumber them by massive margins. Small businesses typically have 1.5x more shadow apps than managed apps. Mid-market companies have 2x more. Enterprise organizations have 2.5x more.
Even organizations with dedicated teams, established processes, and resources specifically allocated to visibility are still missing more than half their environment. For midsize organizations without dedicated visibility resources, the gap is significantly worse.
This isn't a minor oversight. You're governing 30-40% of your environment and treating it as comprehensive governance.
Why the Governance-First Model Fails in Modern SaaS Environments
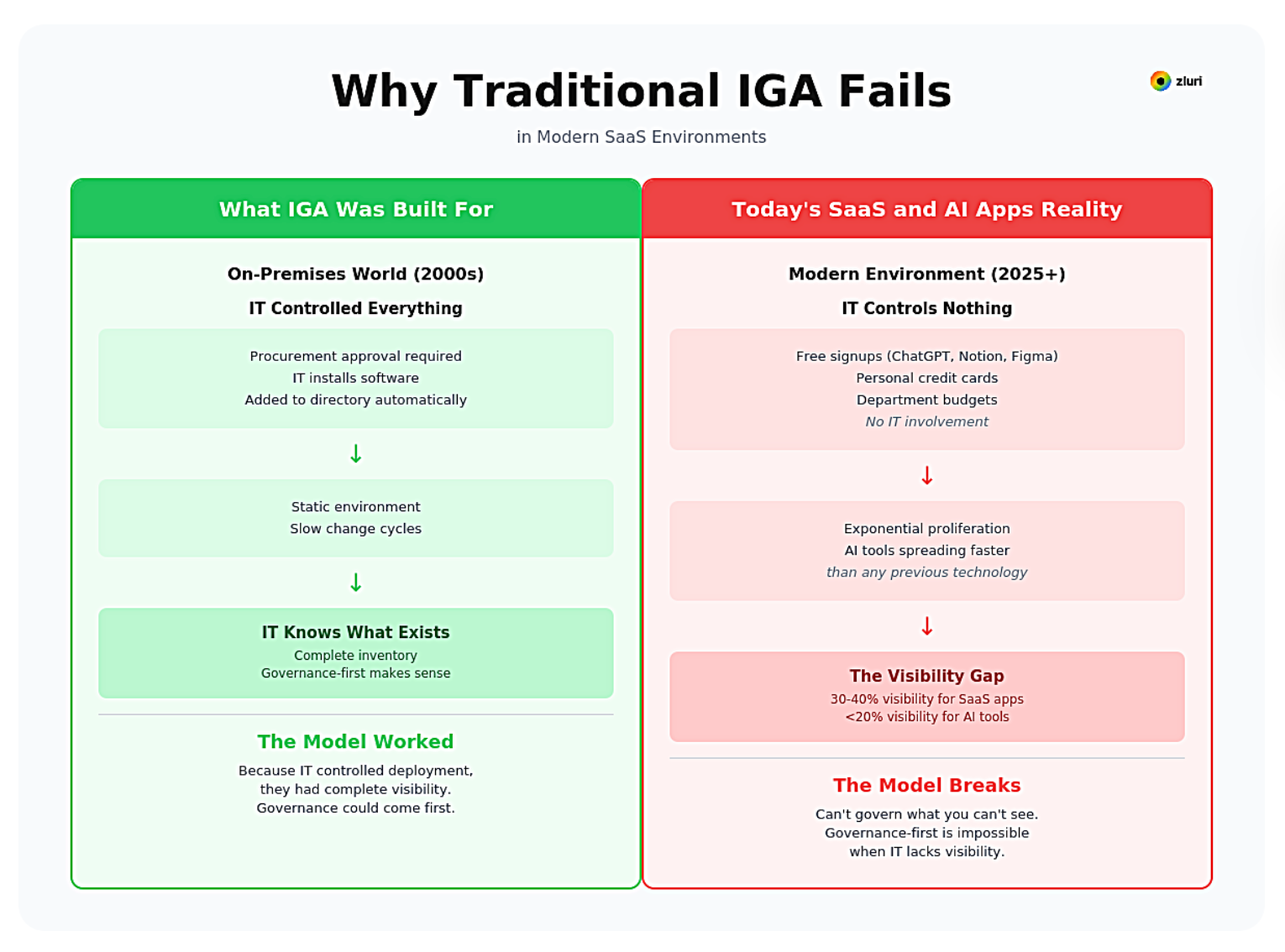
Traditional IGA platforms were designed for a world that no longer exists. They were built for static, on-premises directories where IT controlled software deployment through procurement and installation processes. In that environment, governance-first made sense because IT knew what existed.
Today's SaaS environments are fundamentally different, and we see this pattern across every organization we work with.
Employees adopt applications in minutes through free signups, personal credit cards, or direct department purchases. An engineer discovers a code assistant, a marketer finds a design tool, a sales rep tries a prospecting platform. No procurement approval, no IT involvement, no addition to the IGA inventory.
Departmental autonomy means marketing, sales, engineering, and operations teams often have budget authority to purchase tools directly. By the time IT discovers these applications, they're embedded in workflows with dozens or hundreds of users.
Free tiers bypass all traditional controls. ChatGPT, Notion, Slack, Figma, and thousands of other platforms offer powerful free versions. No corporate card transaction, no expense report, no procurement record. Completely invisible to finance-based discovery.
Application proliferation is exponential. Our research shows the average mid-market company uses over 1,100 total applications. IT knows about roughly 400 of them. The rest exist outside governance entirely.
AI sprawl accelerates the problem exponentially. Employees adopt AI tools faster than any previous technology wave—free-tier assistants, embedded AI features in existing tools, specialized models for code generation, writing, design, and analysis. Our research found IT teams have visibility into less than 20% of AI applications employees use.
These tools often process sensitive data: customer information pasted into prompts, proprietary code shared for debugging, confidential documents uploaded for summarization. The visibility gap for AI is worse than traditional SaaS, and it's growing faster.
Even most modern IGA solutions built for SaaS environments focus primarily on managing access rather than discovering what needs to be managed. They assume you'll feed them an application inventory, then they govern it. But if your inventory represents only 30-40% of reality, your governance covers only that 30-40% of actual risk.
This is the governance-first failure mode. Excellent tools governing an incomplete environment, creating an illusion of comprehensive control while 60-70% of access remains ungoverned and unmanaged.
Why Traditional Discovery Methods Can't Close the Gap
Organizations don't ignore discovery. They use methods that have worked for decades. The problem is these methods were designed for a different environment and can't provide the visibility modern identity governance and access management require.
SSO Integrations (Partial by Design)
Your SSO dashboard shows authentications to applications throughout the day. Your security team uses this data to identify application usage patterns and flag anomalies.
But SSO only captures applications integrated with your identity provider and users who authenticate through SSO.
It's completely blind to direct signups using work emails, personal accounts used for work, applications that don't support enterprise SSO, and applications adopted before SSO integration.
In practice, SSO logs reveal 30-40% of actual application usage. The visibility is real—but treating partial visibility as complete visibility creates dangerous false confidence in governance scope.
Procurement Records (Accurate but Incomplete)
Finance and procurement systems document officially purchased applications with perfect accuracy. But employees don't always follow procurement processes. They expense software on corporate cards under generic categories, seek reimbursement for personal card purchases, or use free tools that generate no financial footprint.
We consistently see procurement data representing a small fraction of applications actually in use. The majority were adopted outside procurement channels entirely.
Manual Surveys (Fundamentally Unreliable)
Some organizations survey employees about application usage. This approach fails because employees don't remember every tool they've signed up for, they underreport applications they think might not be approved, they can't distinguish active from dormant accounts, and they have zero visibility into service accounts.
Even with 100% participation, memory-based reporting cannot produce accurate inventories.
The Core Problem
Each of these methods was designed to solve a different problem in a controlled-deployment environment. None of them were designed for discovery in dynamic SaaS environments where adoption happens independently across hundreds of employees and dozens of departments.
More critically, these methods are reactive. They discover applications after adoption has occurred, sometimes months or years later. By the time finance flags a recurring charge or SSO logs show authentication events, the application already has users, permissions, and company data.
This reactive discovery means governance and administration are always catching up, never comprehensive.
The Three Visibility Gaps (And Why Manual Methods Fail)
The visibility problem exists across three interconnected dimensions. Each has manual workarounds that organizations attempt, and each manual approach fails in predictable ways.
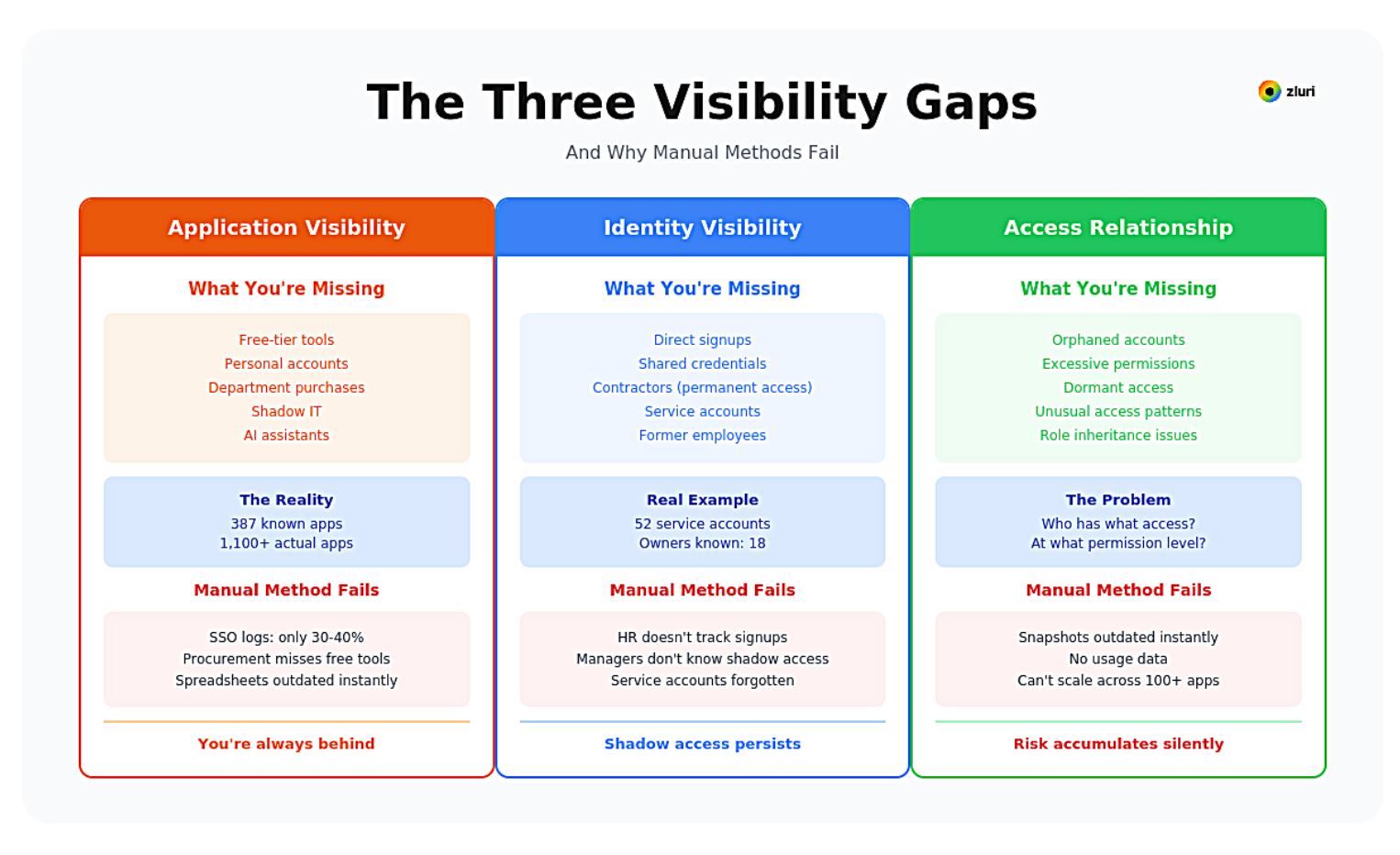
1. Application Visibility Gap
Most organizations only know about applications purchased through procurement, integrated with SSO, and documented in asset inventories. What remains invisible: departmental purchases, individual subscriptions, free-tier tools, personal accounts used for work, applications adopted during remote work, legacy systems never documented.
These aren't fringe tools. Shadow IT concentrates in categories like project management platforms, design software, collaboration tools, AI assistants, and development utilities—core business applications operating outside governance entirely.
The scale of this gap becomes clear during discovery. Your IT team manages 387 applications—that's your governance and automation scope. You deploy comprehensive visibility tools. The results reveal over 1,100 total applications. Your governance and lifecycle automation covered 35% of your actual environment.
Organizations attempt to close this gap manually by compiling lists from SSO logs, procurement records, and expense reports. They survey department heads about tools their teams use. They maintain spreadsheets of known applications.
This manual approach fails because SSO captures only 30-40% of applications. Procurement misses free tools and personal purchases. Surveys rely on incomplete memory. Spreadsheets become outdated the moment they're created. By the time you've compiled everything, new applications have been adopted. You're always behind.
2. Identity Visibility Gap
Most organizations focus on employee identities from HR systems and Active Directory. What remains invisible: employee accounts created by direct signup that bypass SSO entirely, shared credentials among team members that eliminate individual accountability, contractors and vendors with temporary access that becomes permanent, service accounts created for automation that accumulate over time.
Service accounts represent a particularly dangerous blind spot. In one 800-person company, we discovered 52 active service accounts with database access. They could identify owners for 18. The other 34 were created by former employees for forgotten projects—persistent, elevated, completely ungoverned access to production data.
Contractor access creates similar risk. Your organization engages 47 contractors across various projects. Contractor engagements end. Access doesn't. 23 former contractors retain active access to company systems 3-18 months after their engagements ended. Nobody revoked access because the applications weren't in your offboarding workflow.
Organizations attempt to close this gap manually by exporting user lists from HR systems and Active Directory. They ask managers to identify contractors on their teams. They survey application owners about service accounts.
This manual approach fails because HR systems don't track direct signups, personal accounts, or service accounts. Managers don't know about access to their contractors created outside official channels. Application owners don't remember service accounts created by previous team members. Shadow access from role changes—employees who retained permissions after moving teams—never surfaces because nobody thinks to ask.
3. Access Relationship Gap
Discovering applications and identities separately isn't enough. You need to understand the relationships—which identities have access to which applications, at what permission level, and how that access is being used.
Complete access mapping reveals every user's complete access footprint across all applications, permission levels (viewer, editor, admin), access grant dates and sources, last usage timestamps, access paths (direct assignment, group membership, role inheritance). This exposes orphaned accounts, excessive permissions, dormant access, and unusual access patterns that remain invisible otherwise.
Organizations attempt to close this gap manually by exporting user lists from each application individually. They compile everything in master spreadsheets. They cross-reference against HR data. They update quarterly or annually.
This manual approach fails because point-in-time snapshots are outdated immediately. No usage data shows whether access is actually being used. The process can't scale across hundreds of applications—each export takes time, each application has different export formats. There's no automated way to detect changes between review cycles. Orphaned accounts, excessive permissions, and dormant access accumulate silently until the next manual review.
The Unified Problem
Each manual method was designed for controlled-deployment environments where IT knew what existed and controlled who got access. None can provide the continuous, comprehensive visibility modern identity governance and access management require.
By the time you've compiled spreadsheets and validated exports, your environment has changed. New applications adopted. New users provisioned. Contractors ended. Employees changed roles. Your visibility is always historical, never current.
The Real Consequences of Incomplete Visibility
When IGA and access management operate without comprehensive visibility, the consequences aren't theoretical. We see them repeatedly across organizations before they implement visibility-first approaches.
Security Exposure From Invisible Access
A healthcare organization using some autonomous IGA platform showed strong governance—all clinical systems reviewed quarterly, HIPAA controls enforced, access provisioning automated.
During a security assessment, visibility tools revealed 12 collaboration tools clinical staff had adopted for patient care coordination. Three stored protected health information on non-HIPAA-compliant servers. Some of these tools had been in use for 18 months. 73 former employees retained access to patient data through these ungoverned systems.
The IGA platform governed everything IT knew about. It knew about none of these 12 applications. Security exposure accumulated silently while governance dashboards showed green.
Compliance Failures From Incomplete Scope
During a SOC 2 audit, a technology company presented evidence of quarterly access reviews for 67 managed applications. The auditor asked a simple question: "How do you know this is all of them?"
They couldn't answer.
Discovery revealed 143 total applications. The 76 unknown applications included systems processing customer data, storing employee PII, and containing financial records.
Their access reviews covered 47% of their actual environment. The audit delayed SOC 2 certification by three months, costing two major enterprise deals.
Operational Failures From Incomplete Automation
Monday morning. New sales rep starts. IT provisions access to CRM, email, calendar, document storage, communication tools.
By Wednesday, she's still blocked.
Sales rep: "I need access to the prospecting tool the team uses."
IT admin: "What prospecting tool?"
Sales rep: "Apollo. Everyone on the sales team uses it."
IT checks their application inventory. No Apollo. They check SSO. No Apollo integration. They check procurement. No Apollo purchase.
The sales team signed up directly six months ago using a team lead's corporate card. Twelve people have access. IT didn't know it existed.
Your new hire can't be productive because you can't provision access to applications you don't know exist. Your departing employees retain access to those same applications because they don't appear in offboarding workflows.
Offboarding That Wasn't Complete
Your senior engineer submits resignation. IT executes the offboarding workflow—disable AD account, revoke SSO access, remove from email groups, return equipment.
Two weeks later, the engineering manager notices something: The former employee's commits are still appearing in the team's repository. Different account, same code patterns.
You investigate. The engineer had created a personal account for work. Never connected to SSO. Never appeared in your identity provider. Still has push access to production repositories.
You check other departed employees. Seventeen former staff members retain access to applications outside your offboarding workflow—project management tools, design platforms, collaboration systems, code repositories. Applications they signed up for directly, applications their departments purchased, applications that never appeared in IT's visibility.
Your offboarding process is rigorous for applications you know about. It's nonexistent for applications you don't.
Operational Waste From Duplicate Tools
Three departments independently purchased project management tools, spending $43,000 annually combined. None knew the others had solved the same problem. They deployed the Zluri discovery engine 18 months after the first purchase—$64,500 in unnecessary spending that complete visibility from the beginning would have prevented.
What Visibility-First Actually Means
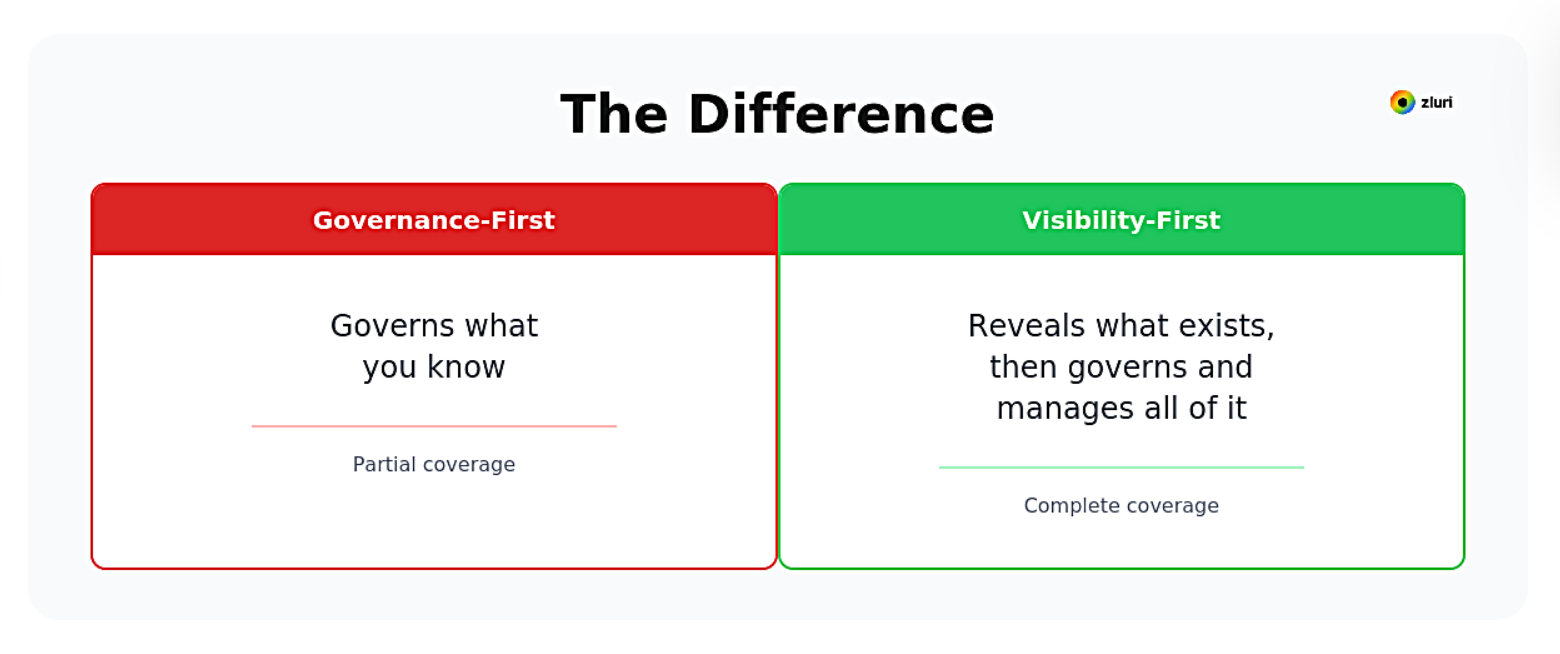
Visibility-first inverts the traditional IGA model. Instead of assuming you know what to govern and manage, it starts with comprehensive, continuous discovery to reveal everything that exists, then applies governance and automation to that complete environment.
We built Zluri specifically around this principle because we saw the governance-first approach failing across every customer we worked with. Here's what visibility-first actually requires:
Continuous, not periodic. Discovery runs constantly, detecting new applications and identities within hours or days of appearance. This prevents the perpetual lag that governance-first creates. Quarterly or annual discovery audits are obsolete before they're completed.
Multi-method, not single-source. No single data source reveals the complete picture. Visibility-first requires combining identity provider data, direct application connections, finance system analysis, endpoint monitoring, browser tracking, and network observation. Each method reveals different applications and identities. Together, they approach completeness.
Automated, not manual. Human processes can't keep pace with SaaS adoption speed. Visibility-first requires automated systems that continuously monitor, cross-reference, and validate without requiring IT intervention. Manual discovery is always outdated.
Visibility before governance and automation. Applications and identities are discovered, cataloged, and assessed before governance policies or automation workflows apply. This ensures both governance and administration cover the actual environment, not an incomplete subset.
The Fundamental Difference
Governance-first approach: IT identifies 67 applications for governance. IGA platform provisions access, conducts reviews, manages lifecycle for those 67 applications. Governance is strong for what's managed. But 76 other applications exist outside governance entirely. Automation workflows don't include them. New hires don't get provisioned. Departing employees don't get deprovisioned.
Visibility-first approach: Discovery reveals 143 total applications before governance or automation begins. Classification determines which require governance and which need lifecycle automation. All 143 enter appropriate workflows based on risk and usage. No application operates outside visibility.
The difference: Governance-first governs what you know. Visibility-first reveals what exists, then governs and manages all of it.
Enabling Prioritization
Once you have complete visibility, prioritization becomes data-driven rather than guesswork.
Risk-based prioritization: The application storing customer PII gets governed before the internal collaboration tool. The system with admin access to financial data gets reviewed before the departmental wiki. You see which applications contain sensitive data and prioritize accordingly.
Usage-based prioritization: The application with 230 users gets automated before the tool with 20 users. You see actual usage patterns and focus automation efforts where they'll have the greatest impact on IT efficiency and employee experience.
Cost-based prioritization: Visibility reveals duplicate tools, underutilized licenses, and consolidation opportunities. You see spending patterns and optimize based on actual data rather than procurement records.
Without visibility, you're prioritizing based on what you happen to know about. With visibility, you're prioritizing based on what actually matters.
What You Need for Complete Access Visibility
Complete access visibility requires solving all three gaps—applications, identities, and access relationships—through a unified approach. Here's what that requires:
Multiple Discovery Methods Working in Parallel
No single source reveals complete visibility. You need multiple discovery methods running continuously:
Identity provider integration for sanctioned applications and employee populations.
SSO platform connection for authentication patterns and federated applications.
Finance system integration for purchased tools and spending patterns.
Browser extensions for web application usage patterns, including free-tier tools and direct signups.
Endpoint agents for desktop applications and locally installed software.
Direct API connections for granular permission data from major SaaS platforms.
HR system integration for employee lifecycle events, contractors, and organizational structure.
Each method reveals different applications and identities. Together, they achieve comprehensive coverage. We use nine discovery methods in Zluri because that's what complete visibility actually demands.
Automated Classification
Raw discovery data isn't actionable. You need automated classification to evaluate each discovered application:
Risk classification: Does it store customer data? Does it process financial information? Does it have admin-level access? Does it contain regulated data?
Usage classification: How many users? How frequently accessed? Which departments?
Cost classification: What's the spending? Are there duplicate tools? Underutilized licenses?
Classification enables prioritization. You see which applications need governance first based on risk, which need automation based on usage, which represent cost optimization opportunities.
Continuous Monitoring
Discovery isn't a one-time project—it's ongoing. Your environment changes constantly as employees adopt new tools, departments purchase solutions, and access patterns shift.
Continuous monitoring detects new applications within hours or days of adoption. It identifies new users and access grants as they occur. It flags changes in usage patterns, permission levels, and risk indicators.
Without continuous monitoring, your visibility degrades immediately after initial discovery. With it, you maintain current, accurate understanding of your environment.
Complete Identity Mapping
Visibility into applications alone isn't enough. You need to map all identities to all applications with complete relationship data:
All identity types: Employees, contractors, vendors, service accounts, shared credentials.
All relationship attributes: Which identities have access to which applications. Permission levels. Access grant dates and sources. Last usage timestamps. Access paths.
This mapping enables complete governance and administration. Access reviews cover actual access footprints. Provisioning includes all relevant applications. Deprovisioning revokes access comprehensively. Risk assessments evaluate actual exposure.
Actionable Insights
Visibility without action is just reporting. You need insights that drive governance and administration:
Prioritized action lists: Which applications need governance first? Which needs automation? Which represents security risk?
Anomaly detection: Orphaned accounts, excessive permissions, dormant access, unusual patterns.
Optimization opportunities: Duplicate tools, underutilized licenses, consolidation candidates.
Lifecycle triggers: Role changes requiring access updates, contract expirations requiring deprovisioning, compliance deadlines requiring reviews.
These insights transform visibility from passive awareness into active governance and management.
Implementation Timeline: 30 Days to Complete Visibility
Traditional visibility projects take 6-12 months—deploying agents, integrating systems, validating data, building dashboards. By the time you achieve visibility, your environment has changed.
We deploy comprehensive visibility in 30 days (one-time setup):
Week 1—Core Integrations: Connect to identity providers, SSO platforms, HR systems, and finance tools. These primary sources identify sanctioned applications and employee populations immediately. Initial discovery runs, revealing your baseline application inventory and identity landscape.
Week 2—Extended Discovery: Deploy browser extensions and optional endpoint agents. Activate direct API integrations with major SaaS platforms. These methods reveal shadow IT, free-tier tools, and direct signups invisible to primary sources. Application count typically increases 3-5x from Week 1 baseline.
Week 3—Identity Mapping: Map all discovered identities to applications. Identify service accounts, external users, shared credentials. Flag orphaned accounts and dormant access. Build complete access relationships showing who has access to what, at what permission level, with what usage patterns.
Week 4—Validation & Baseline: Validate discovery results with application owners. Establish baseline metrics: total applications, total identities, ungoverned access, dormant accounts, duplicate tools, risk exposure. Configure continuous monitoring and alerting for new applications and access changes.
By day 30, you have complete visibility into what exists, who has access, and how that access is being used. Now governance and administration can begin with comprehensive scope.
Getting Started With Access Visibility
Access visibility isn't a feature to add to IGA. It's the foundation IGA must be built on.
Without it, you're not doing identity governance and access management. You're governing and managing the visible portion of your environment and hoping the invisible portion doesn't become your next security incident, compliance failure, or operational bottleneck.
Learn how Zluri achieves complete access visibility → Book a Demo
Frequently Asked Questions
What is access visibility?
Access visibility means understanding the complete access footprint across your environment—what applications exist, what identities have access to them, and how that access is being used. It answers the fundamental question: Who has access to what?
Why is access visibility important for identity governance?
You can't govern what you can't see. Access reviews, compliance reporting, and security assessments can only cover applications and identities you know about. Without complete visibility, governance operates on incomplete information, creating gaps where ungoverned access accumulates risk.
Why is access visibility important for access management?
You can't automate what you can't see. Provisioning workflows can't include applications you don't know exist. Deprovisioning checklists can't revoke access to shadow IT. Lifecycle automation stops at the boundary of your visibility.
What's the difference between governance-first and visibility-first?
Governance-first assumes you know what applications exist and governs that known set. Visibility-first discovers everything that exists before governance begins, ensuring policies and automation apply to your complete environment rather than a partial subset.
Why can't SSO provide complete visibility?
SSO only captures applications integrated with your identity provider and users who authenticate through SSO. It misses direct signups, personal accounts used for work, applications without enterprise SSO support, and free-tier tools. In practice, SSO reveals 30-40% of actual application usage.
What is shadow IT and why does it matter?
Shadow IT refers to applications adopted outside official IT processes—departmental purchases, individual subscriptions, free-tier tools, direct signups. Shadow applications typically outnumber managed applications by 3-7x depending on organization size. They represent significant ungoverned risk.
How long does it take to achieve complete visibility?
Traditional visibility projects take 6-12 months. We deploy comprehensive visibility in 30 days through phased integration of identity providers, finance systems, browser extensions, endpoint agents, and direct API connections.
What does visibility reveal that governance-first misses?
Visibility typically reveals 3-7x more applications than IT manages, including shadow IT, departmental purchases, free-tier tools, and direct signups. It also reveals identity gaps: service accounts, external users with persistent access, orphaned accounts, and employees with dormant or excessive permissions.
How does visibility help with prioritization?
Complete visibility enables data-driven prioritization. You can prioritize governance for applications with customer PII over internal tools. You can prioritize automation for applications with 230 users over those with 20. You can identify cost optimization opportunities based on actual usage patterns.
What about service accounts?
Service accounts represent significant risk because they typically have elevated privileges, long-lived credentials, and no employment status to trigger offboarding. Complete visibility identifies all service accounts and maps them to owners for governance.
How does visibility relate to compliance?
Compliance frameworks require demonstrating you've reviewed access across your environment. Auditors ask "how do you know this is all of them?" Visibility provides that answer—systematic discovery covering all applications and identities, not just the ones IT happened to know about.
Do I need complete visibility before starting governance?
Ideally yes—visibility-first ensures governance covers your complete environment. However, you can run discovery and initial governance in parallel. The key is achieving comprehensive visibility so governance scope expands to cover everything discovered.









.svg)














