SailPoint is a leader in the identity governance and administration (IGA) space. It has more than half of the Fortune 500 companies as its customers. However, its enterprise-focused approach, high costs, and implementation complexity make it a poor fit for many organizations.
We've compiled a comprehensive list of 14 SailPoint alternatives for both mid-market companies and large enterprises. This guide helps you find the right IGA solution based on your specific needs, budget, and technical environment rather than market popularity alone.
Let's examine SailPoint's key limitations before exploring the alternatives.
Drawbacks of SailPoint
- Highly Expensive for Mid-Sized Organizations
- Multiple Cost Factors: High licensing fees, plus setup cost, customization, and long-term maintenance.
- Bundled Offerings: You can't buy modules (e.g., access reviews) separately. You often end up paying for features you don't need.
- Resource-Heavy Implementation: Deployment can take years. Most organizations require developers or consultants to configure it properly.
- Complexity Demands Constant Training & Specialized Resources
- Ongoing Upkeep: Roles, policies, and integrations need frequent updates, often requiring specialist skills.
- Training Overload: Business users and system admins need continual training to manage certification campaigns and other daily tasks.
- Integration Challenges
- Lack of Out-of-the-Box (OOTB) Integrations: Even with pre-built connectors, extensive customization is usually required. This often demands scripts, troubleshooting, or professional services.
- API Limitations & Vendor Support: Integrations with platforms like Okta or legacy apps can hit rate limits or can be buggy. You have to rely on documentation and third-party vendors for troubleshooting.
Considering these drawbacks, you might want to explore other IGA solutions. Below is a quick overview of the two main categories of IGA vendors, followed by recommended alternatives.
Categorizing IGA Solutions: Mid-Market vs. Large Enterprise
IGA vendors generally fall into two main groups, depending on the complexity of your environment, team size, and budget.
Zluri: A No-Code, Easy-to-Deploy Alternative to SailPoint
Zluri is a full-suite IGA platform that simplifies access reviews and automates lifecycle management without the complexity of SailPoint. Designed specifically for mid-market organizations, we deliver faster deployment, easier management, and better value. All without requiring specialized technical expertise or expensive consultants.
Here's why switching to Zluri makes sense for your team:
- Save costs with transparent, predictable pricing. SailPoint's pricing often includes hidden costs for add-ons, complex licensing, and third-party consulting. We offer clear, predictable pricing based on the number of identities managed. No extra charges for essential features.
- Get faster results with out-of-the-box integrations. We have 300+ pre-built integrations that instantly connect to your SaaS apps. This gives you complete access visibility right away, without building custom connectors or dealing with lengthy setup cycles.
- Skip the complexity and deploy without deep technical expertise. Unlike SailPoint, which often requires specialized admins and third-party consultants, our no-code platform and intuitive workflows let your IT team deploy and manage it independently. This reduces implementation time and costs significantly.
- Automate access reviews with rich contextual insights. We automatically pull contextual insights directly from your apps, surfacing inactive accounts, overprovisioned users, and risky permissions. Reviews become faster, more accurate, and easier to manage.
Now, we will discuss these differences in detail.
Budget-Friendly Pricing Built for Mid-Sized Organizations (Zluri Delivers Full Identity Governance at a Fraction of SailPoint's Cost)
Identity governance shouldn't come with excessive costs, long implementation timelines, or rigid pricing bundles. Yet many organizations using SailPoint find themselves locked into costly, full-suite licenses even when they only need specific modules.
SailPoint customers have reported pricing that can be extremely high. Often starting at a few hundred thousand dollars and reaching millions when factoring in licensing, add-ons, and ongoing maintenance fees.
We deliver full-fledged identity governance at a fraction of the cost. No hidden fees. No expensive consultants.
Flexible, Module-Based Pricing (Choose Only the Modules You Need Without Paying for Unused Features)
Unlike SailPoint's rigid, bundled packages, we let you choose the modules that align with your compliance and security needs. You're not paying for unused features.
For example, if you only need user access reviews to meet compliance standards like SOC 2, HIPAA, or ISO 27001, you can start with just that module. No need to commit to an entire suite of features you won't use.
No Consulting Fees Required (Your In-House Team Can Deploy Zluri Without Expensive External Consultants)
SailPoint often requires external consultants for setup, policy configuration, and ongoing maintenance. This significantly increases the total cost of ownership (TCO). We take a simpler approach:
- No-code deployment means your in-house IT team handles setup themselves
- Intuitive, pre-configured workflows reduce the need for custom development
- Built-in support from our team eliminates expensive third-party consulting fees
Faster Time-to-Value (Go Live in Days or Weeks Instead of Months with SailPoint)
With SailPoint, lengthy implementation cycles can delay compliance readiness and increase operational overhead. Organizations often spend months or longer just configuring and deploying the platform.
We offer rapid deployment through our out-of-the-box integrations with 300+ apps and minimal setup requirements. You can go live in days or weeks, not months. This allows you to automate identity and access governance without waiting on lengthy rollouts.
Transparent, All-Inclusive Pricing (All Users Are Covered Without Hidden Per-User Fees for Contractors or Vendors)
Many IGA platforms, including SailPoint, charge separate per-user licensing fees for contractors, vendors, or temporary workers. This leads to unexpected costs as your organization scales.
We provide transparent pricing that covers all users, internal and external, without additional or hidden charges. You get complete visibility into costs. No surprises.
Skip the Complex Setup Process (Integration Takes Minutes, Not Months, with Zluri's Pre-Built Connectors)
Integration shouldn't be a drawn-out process that demands heavy development work, constant troubleshooting, and reliance on external consultants. Yet with SailPoint, many organizations find themselves spending months on integrations, scripting custom connectors, and managing API limitations.
For example, connecting a new application that isn't natively supported often requires writing custom scripts. Without in-house expertise, this means relying on external consultants just to keep things running smoothly. More costs. More complexity.
We make integration simpler from day one. No coding or external experts required.
300+ Pre-Built Integrations (Connect Your Entire SaaS Stack in Just a Few Clicks with 300+ Out-of-the-Box Integrations)
We offer 300+ direct, ready-to-use connectors for popular SaaS apps. Integration becomes seamless. Instead of scripting custom connectors or dealing with API limitations, you can integrate your SaaS stack in just a few clicks.
Your team can connect applications independently, without waiting on consultants or developers. These out-of-the-box integrations save weeks of manual effort. You can start automating governance faster.
SDK for Custom Applications (Our SDK Lets You Build Custom Connectors with Guidance from Our Support Team)
If you need to integrate apps that aren't in our pre-built catalog, you're still covered. We provide a built-in SDK that lets your team create custom connectors easily.
Even if your IT team needs guidance, our in-house support team is available to assist. This eliminates the need for costly third-party consultants.
Multi-Instance Support from a Single Platform (Manage Multiple App Instances from One Platform Without Extra Licensing Costs)
Managing multiple instances of the same app (e.g., across different regions or departments) with SailPoint often requires additional licensing or complex setups.
With our platform, you can integrate and manage all instances from a single interface. No need for extra licenses or complicated configurations. This maintains consistent governance across your entire tech stack without additional costs or admin overhead.
Authoritative Data Source Selection (Choose Your Most Reliable Data Source to Drive Accurate Governance Decisions)
We allow you to select the authoritative data source, enabling you to act on identity data with confidence.
For example, you can choose user designation to come from your HRMS instead of an identity provider (like Google Workspace or Entra ID). This ensures the most accurate and up-to-date information drives your governance decisions.
Get Direct Value from Day One (Your Team Can Start Managing Access from Day One Without Training or Certifications)
With SailPoint, even routine tasks like access requests and certifications often come with a steep learning curve. The interface requires navigating multiple steps, using technical jargon, and following rigid workflows.
Even after becoming familiar with the platform, routine tasks can feel exhausting. Too many manual steps slow you down.
If your team changes frequently or lacks deep identity governance expertise, this complexity creates unnecessary overhead. To manage SailPoint effectively, organizations often need to:
- Take multiple training courses and certifications just to get familiar with the platform
- Hire or train specialists who understand APIs and scripting for tasks like rule management and custom attribute updates
- Spend hours troubleshooting or searching for community resources to perform routine tasks
Even one reviewer on G2 stated:
There is a ton of training needed to fully understand and utilize the product to its full potential. All the training offered to use the product is free, but you need to pay for more training to gain a better understanding.
We eliminate this complexity.
Graphical, User-Friendly Interface (No Coding Required) - Visual Workflows Let You Automate Access Controls Without Writing Any Code
Instead of dealing with complex scripts or command-line configurations, we offer a graphical, no-code dashboard. Role assignments, access reviews, and policy management are simplified into visual workflows.
You can easily create, modify, and automate access controls without writing a single line of code. This reduces admin overhead and makes governance simpler for your entire IT team.
No Continuous Training Required - Even Non-Technical Users Can Navigate and Manage Access Effortlessly
Our intuitive interface allows your team to start using it immediately. No lengthy training sessions required. You won't need certifications or specialized expertise.
Even non-technical users can navigate and manage access effortlessly. This saves time and reduces dependence on external support.
In short, with Zluri, you get the identity governance capabilities you need without unnecessary expenses, lengthy deployments, or complex pricing structures. You can scale at your own pace while maintaining effective governance and a budget-friendly approach.
Why IT Teams at Mid-Market Companies Choose Zluri (All Essential IGA Capabilities in One Unified Platform)
Zluri Works Best for Cloud-First Organizations with Modern SaaS Applications
Zluri is purpose-built for mid-market organizations with cloud-first, SaaS-heavy environments. Our platform excels when the majority of your applications are modern SaaS tools.
While we can handle a handful of custom or on-premise apps through our SDK, if your organization heavily relies on custom in-house built applications or runs predominantly on-premise infrastructure, Zluri may not be the optimal choice.
For organizations with extensive legacy systems or complex on-premise deployments, we discuss enterprise-grade alternatives later in this guide that are specifically built for hybrid and on-premise environments.
Other Mid-Market Alternatives to SailPoint
Below, we've listed additional SailPoint alternatives specifically designed for mid-market organizations (with 10,000 or fewer identities).
1. AccessOwl

Best For: Mid-market companies with SaaS-heavy environments needing affordable automation
Like SailPoint, AccessOwl automates user provisioning and access reviews with customizable approval workflows. What sets it apart is its use of private APIs and RPA to automate provisioning for applications lacking native automation support. This makes it ideal for non-standard SaaS tools.
It features real-time data syncing, Slack-based notifications during reviews, and custom approval policies to prevent rubber-stamping. Pricing starts at $4.50-6/user/month, though essential add-ons like provisioning ($2.50) and spend management ($3.50) increase the total cost.
2. RadiantOne Identity Data Platform
Best For: Enterprises with complex identity environments needing AI-driven insights
While RadiantOne handles comprehensive identity governance like SailPoint, it distinguishes itself through its AIDA AI assistant that automatically identifies risky accounts and suggests specific remediation actions directly in a chat interface.
The AI analyzes existing access patterns to recommend role-based access combinations. It automatically sends corrective actions to your ITSM system post-review. The platform works across hybrid environments but lacks real-time synchronization (updates take significant time) and carries a steep price of $798,000 annually.
3. Clarity Security
Best For: Mid-market organizations prioritizing risk-based access reviews in cloud environments
Clarity Security provides access review campaigns similar to SailPoint but focuses on risk-based prioritization through configurable thresholds that automatically flag high-risk items for immediate review.
It surfaces contextual details like nested access, risk scores, and SoD conflicts. Uses SQL queries for internal apps. Offers SDKs for siloed systems. The platform is ideal for SaaS-heavy environments with pre-built templates for various review types.
4. Oleria IGA
Best For: Small to mid-sized companies with cloud-first environments needing granular visibility
Oleria offers identity governance workflows like SailPoint but emphasizes resource-level granularity, tracking permissions down to individual files. It detects dormant accounts, externally shared files, and unused permissions.
Its automated workflows can disable stale accounts in seconds. It maintains centralized logs for audit-ready documentation. The platform is designed for cloud and SaaS environments.
5. Zilla Security (Acquired by CyberArk)
Best For: Mid-market organizations seeking AI-driven role management in SaaS environments
Much like SailPoint, Zilla handles role mining and access requests, but it stands out through AI-driven profile creation that analyzes user attributes to suggest access profiles automatically routed for approval.
It includes a self-service portal, ServiceNow integration, and a Policy Engine that checks requests against company policies in real-time. Integration with legacy systems requires extensive manual configuration, limiting its effectiveness in hybrid environments.
6. Veza
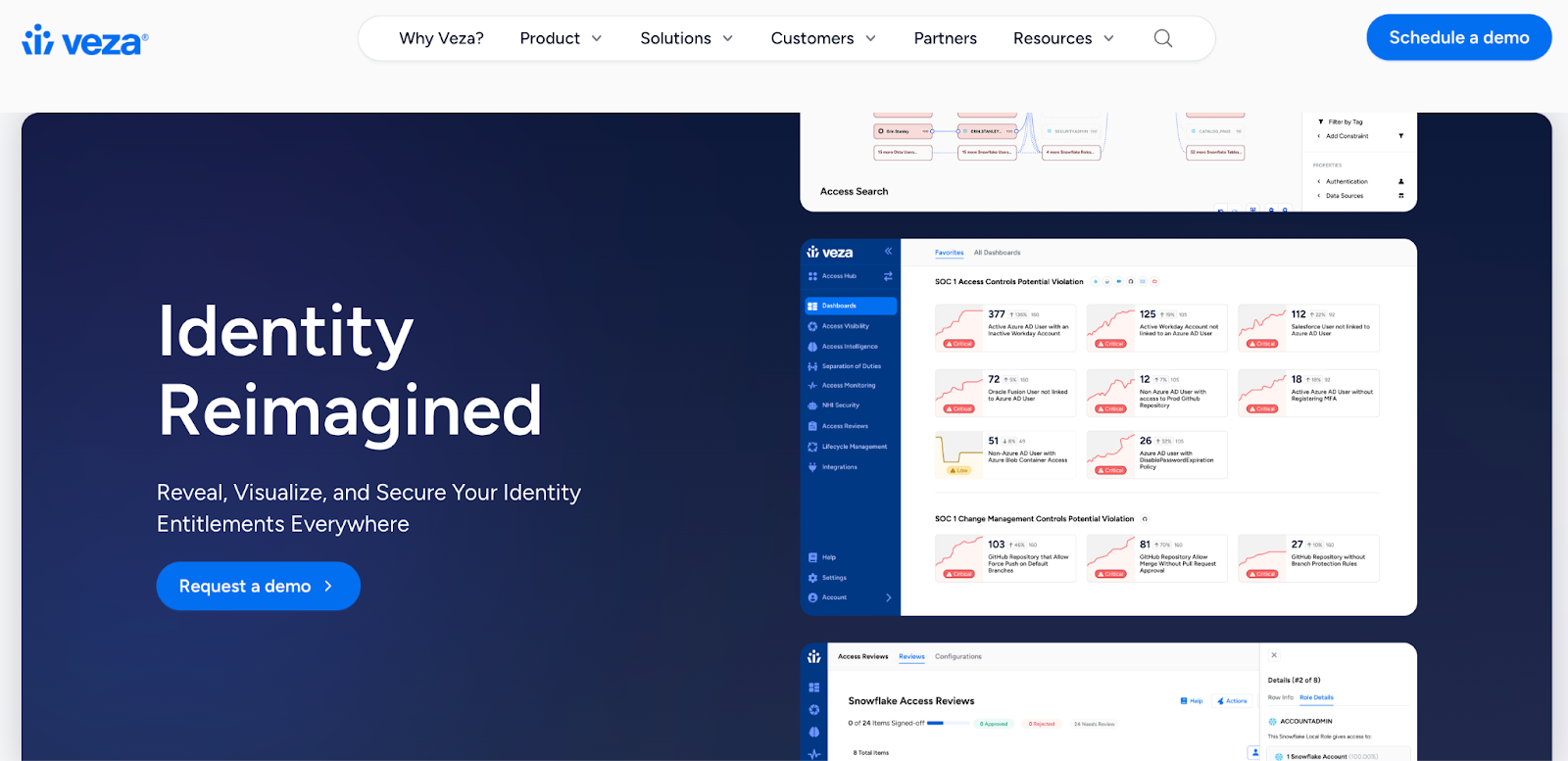
Best For: Mid-sized organizations needing rapid deployment with strict security requirements
Veza delivers access review campaigns like SailPoint but differentiates itself with ultra-fast deployment connecting to existing systems in minutes without agents or installers.
It emphasizes strict security practices. Penetration testing. Complete tenant isolation. Policy-based attribute mapping. Best suited for cloud and SaaS environments, though it requires technical expertise to operate and doesn't auto-remediate rejected access.
7. ConductorOne
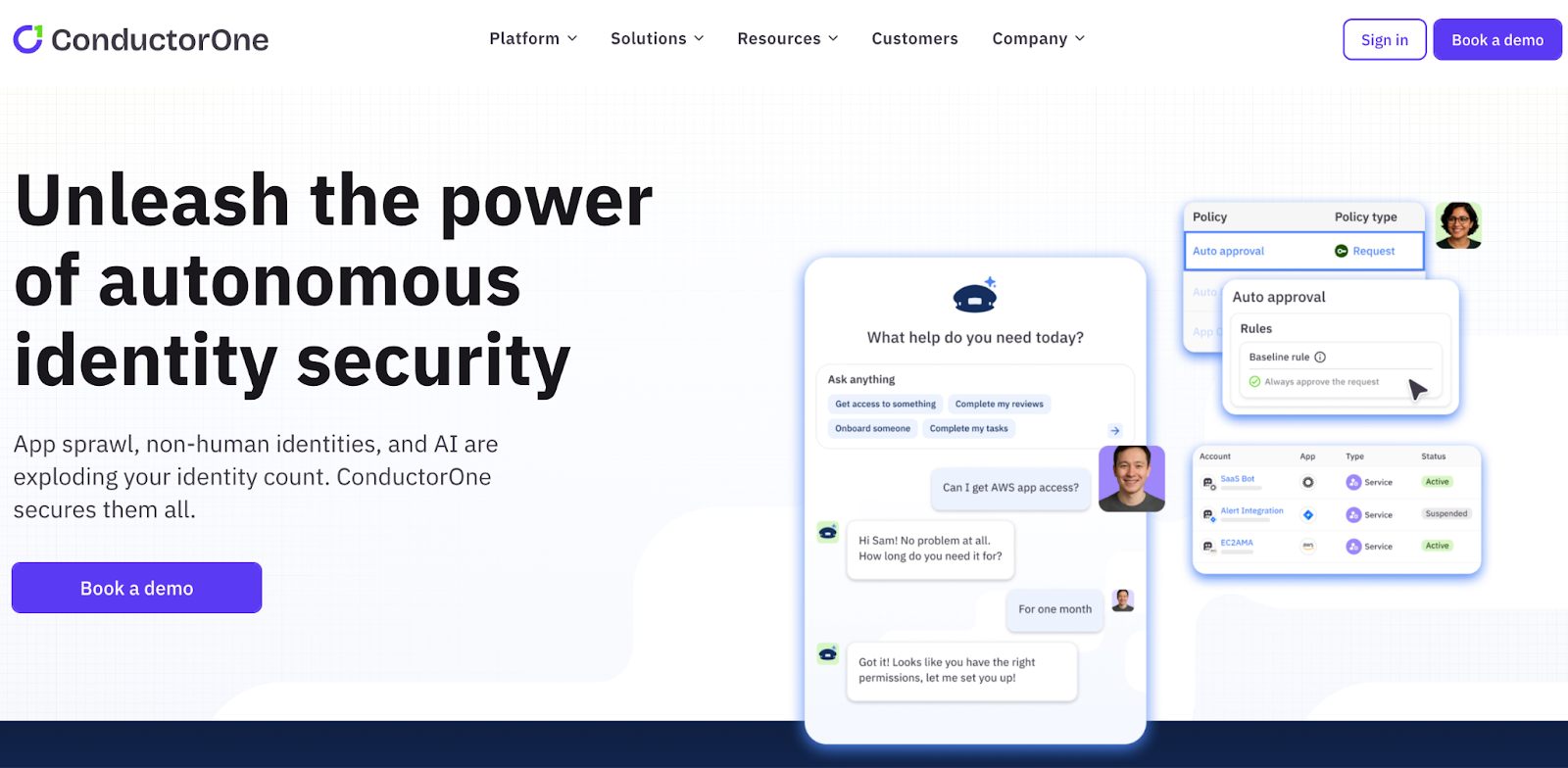
Best For: Tech-savvy mid-market teams managing cloud-native environments
ConductorOne provides off-the-shelf integrations similar to SailPoint but specializes in converting standing access into time-bound temporary permissions to minimize attack surfaces.
It offers real-time automation, multi-step conditional approvals, and emergency break-glass policies. Designed for cloud and SaaS environments, it's not suitable for non-technical users as it requires CLI and Terraform expertise, adding training costs.
SailPoint Alternatives Built for Large Enterprises
Below we've listed SailPoint alternatives that specifically cater to large enterprises (10,000+ identities).
8. Microsoft Entra ID Governance

Best For: Large enterprises deeply integrated with Microsoft ecosystem (hybrid environments)
Microsoft Entra ID automates lifecycle workflows like SailPoint but excels through seamless native integration within the Microsoft ecosystem with Active Directory synchronization and the My Access self-service portal.
It supports configurable 3-stage access reviews and automatic assignment policies. Designed for hybrid environments (Azure, on-prem AD, Microsoft 365). Pricing starts at $6/user/month, though core IGA features require the Entra Suite at $11/user/month with annual commitment.
9. Saviynt

Best For: Large enterprises with complex hybrid environments needing frequent access reviews
Saviynt offers enterprise-scale certification like SailPoint but differentiates through micro-certifications: short, frequent reviews triggered by role changes to reduce review fatigue.
It analyzes 40+ HR attributes to recommend access. Generates trust scores based on risk signals and SoD conflicts. Designed for hybrid environments (cloud, on-prem, custom apps). Costs approximately $120,000 annually versus SailPoint's $240,000, though add-ons increase costs.
10. Omada Identity Cloud

Best For: Large enterprises managing both human and machine identities in hybrid environments
While Omada handles enterprise-scale deployments like SailPoint, it stands out with machine learning-driven role mining for both workforce and non-human identities.
Its ML algorithms analyze access patterns to recommend optimal permissions for new joiners. Its Compliance Workbench surfaces policy violations with an AI assistant (Javi) for request management. Built for hybrid environments (on-prem, cloud, hybrid). Uses batch processing with 1-4 hour sync delays rather than real-time updates.
11. ManageEngine ADManager Plus

Best For: Enterprises heavily invested in Active Directory (hybrid environments)
ManageEngine automates lifecycle workflows like SailPoint but specializes in hybrid Active Directory environments with NTFS permission management.
It uses LDAP queries and Microsoft API calls for data collection. Performs automatic domain discovery. Presents identity data in a centralized dashboard. Priced affordably at $595-795/year, it's significantly cheaper than SailPoint, though it suffers from slow upgrades, performance issues, and high RAM consumption requiring frequent restarts.
12. PingIdentity Governance
Best For: Large enterprises with complex identity needs across hybrid environments
PingIdentity provides enterprise IGA like SailPoint but focuses on AI-powered auto-evaluation of access requests, automatically approving low-risk requests while routing critical ones for multi-step approvals.
It enforces SoD policies that proactively block toxic access combinations. Handles both human and machine identities. Designed for hybrid environments. Lacks built-in support for single-page applications requiring extensive manual configuration and experiences occasional device unpairing issues.
13. Oracle Identity Governance
Best For: Large enterprises seeking self-service capabilities in hybrid environments (most affordable enterprise option)
Oracle automates workflows like SailPoint but emphasizes self-service capabilities for both users and IT teams with an access catalog suggesting role-based access and user-enabled app onboarding via REST APIs.
It performs automated role mining. Harvests user data from connected systems for consistent provisioning. Built for hybrid environments (on-prem, cloud). At $3/user/month for up to 10,000 users, it's the most affordable enterprise option, though report data duplication across categories complicates analysis.
Finding the Right IGA Solution for Your Organization
SailPoint has long dominated the identity governance space, but it's not the only option. As we've explored in this guide, 14 compelling alternatives exist, each designed to address specific organizational needs, budgets, and technical environments.
The key is understanding your requirements. Mid-market organizations with cloud-first, SaaS-heavy environments will find solutions like Zluri, AccessOwl, and Clarity Security deliver faster deployment, simpler management, and transparent pricing.
These platforms eliminate the complexity and cost barriers that make SailPoint prohibitive for smaller teams.
Large enterprises managing hybrid environments with thousands of identities have equally strong options. Microsoft Entra ID offers seamless integration for Microsoft-centric organizations.
Saviynt provides enterprise-scale capabilities at half the cost of SailPoint. Oracle Identity Governance delivers comprehensive features at just $3 per user per month.
Making Your Decision
Start by assessing three critical factors:
- Your environment. Are you primarily SaaS-based, on-premise, or hybrid? Choose a solution built for your infrastructure reality.
- Your team's capabilities. Do you have technical IAM specialists, or do you need a no-code platform that business users can manage? Match the solution to your team's skills.
- Your budget and timeline. Can you invest 6-12 months in implementation, or do you need to go live in weeks? Factor in total cost of ownership, including consulting fees and hidden add-ons.
Take the Next Step
Don't settle for a solution because it's the market leader. The right IGA platform should simplify your operations, not complicate them. It should fit your budget, not strain it. It should empower your team, not require you to hire specialists.
Review the alternatives we've outlined. Shortlist 2-3 solutions that match your environment and organizational size. Request demos focusing on your specific use cases. Most importantly, ask about true implementation timelines, all-in pricing, and what support looks like after deployment.
Identity governance is too critical to get wrong. With the alternatives now available, you can find a solution that delivers enterprise-grade security and compliance without SailPoint's complexity and cost.
The right IGA platform is out there. Choose wisely.







.png)

.svg)














