A Cloud Access Security Broker (CASB) sits between your organization's users and cloud service providers, monitoring network traffic to enforce security policies. For this reason, CASB software can be implemented either in the cloud or on-premise. This article will help you explore the top CASB solutions to make an informed decision.
The complexity of managing and protecting data across various cloud applications can lead to significant challenges. Without the right CASB software, your organization may face security breaches, data loss, and compliance violations.
IT teams often struggle with maintaining visibility and control, while procurement teams find it hard to evaluate and select the most effective solution. This can result in wasted resources, frustration, and inefficiency.
To address these pain points, it's crucial to choose a suitable CASB software that aligns with your organization's specific requirements. In order to do so, we will explore the top 15 CASB solutions in 2024.
By understanding the features of each CASB tool, you can make an informed decision, ensuring enhanced security, compliance, and streamlined cloud management.
Key Requirements to Look for in CASB Software
When looking for CASB software, make sure it satisfies the following requirements-
- Offers real-time visibility: Companies with large manpower find it challenging to keep a tab on all the cloud services being used and who is using them. Most cloud service providers do not offer a proper logging or data audit in their normal plan tiers. However, an ideal CASB software provides businesses complete visibility into their cloud app usage. This helps discover any redundancies.
- Optimum data security features: Undoubtedly, this should be a high priority while choosing a CASB solution for your business. All CASB software solutions come with an integrated cloud DLP (Data Loss Prevention Mechanism) system. It uses document fingerprinting, in combination with detecting the user's location and activity, to find any suspected violations.
- Ensure security compliance: While moving on to the cloud, businesses must adhere to all security guidelines. These standards act as a base for secure cloud space, which can lead to data breaches. It addresses various compliance regulations, including HIPAA, GDPR, and regulatory requirements like PCI DSS, ISO 27001, and others.
- Protection against security threats: Many times, third-party companies (or insiders) try to steal data or get access to sensitive information, which can lead to security threats. A robust CASB tool runs regular scans to determine cloud usage patterns. This way, if anyone attempts to steal the cloud’s data, they would get caught. Moving forward, we will discuss the top 15 CASB solutions that you can opt to safeguard your cloud space.
Top Cloud Access Security Broker (CASB) Solutions
1. Netskope
Netskope is titled the number one CASB software consecutively for the fourth year by Gartner. The platform accelerates your digital transformation journey by offering a robust cloud security system that is data-driven, cloud-smart, and fast.
You can manage cloud spaces like Office 365, Box, DropBox, and other available cloud services. It offers multiple risk assessment and discovery features that enhance visibility, prevents threats, and comply with security policies.
Netskope Pros & Cons:
Pros-
- Complete visibility for both sanctioned and unsanctioned apps.
- Its Next-Gen Secure Web Gateway (NSWG) feature offers web security from the cloud, where it protects cloud applications, websites, services, and data from any location.
- Fast and easy to deploy.
Cons-
- The after-sales support can be improved
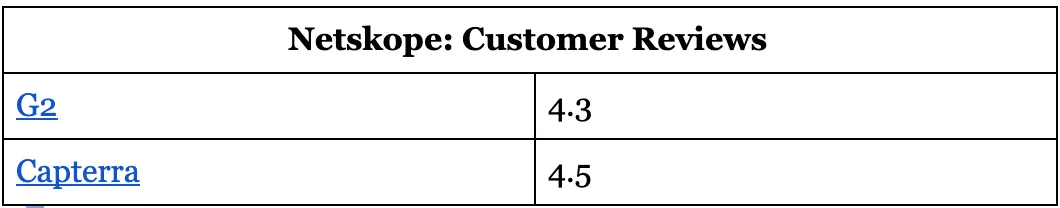
Netskope: Customer Reviews
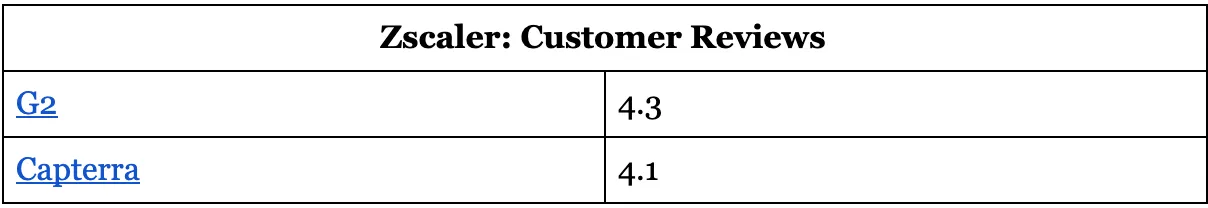
2. McAfee MVISION
McAfee is an open-source, insight-driven, cloud-native platform that protects data and can be used for all Iaas, Saas, PaaS. The platform is best suited to handle enterprise needs that have a high degree of complexity.
McAfee also allows organizations to create and implement policies according to their needs, besides having pre-built policy templates (for PCI DSS, SOX, GLBA, HIPAA, FISMA). The system is driven by over a billion sensors worldwide with high-power analytics to deliver the best intelligence capabilities.
McAfee MVISION Pros & Cons:
Pros
- It is pretty simple to deploy & operate.
- McAfee is constantly evolving and takes customer feedback quite seriously.
Cons
- The user interface needs improvement.
McAfee: Customer Reviews

3. Palo Alto
Palo Alto offers Prisma products to help SaaS enterprises get robust cloud data security. It offers fast, zero-delay evasion-resistance threats (acts within seconds of cloud data analysis). The platform detects new and unknown threats via inline machine learning models across SaaS applications.
Prisma provides a centralized management system that helps users with complete global visibility and control over Palo Alto Network’s various next-generation firewalls.
Palo Alto Pros & Cons:
Pros-
- Easy to deploy
- An excellent user interface
- Continuously evolving to offer more value
Cons-
- The after-sales support can be an issue
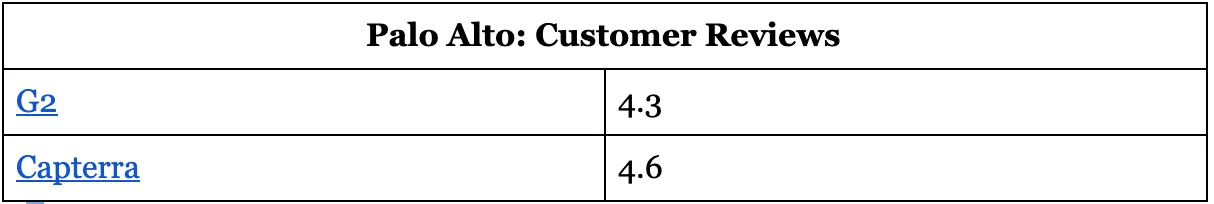
Palo Alto: Customer Reviews
5. Cisco

CISCO Cloudlock is one such comprehensive, cloud-native CASB solution that protects your business on the cloud. The platform uses an advanced machine learning mechanism that identifies suspicious actions outside the listed countries.
With robust Data Loss Prevention (DLP) technology, CISCO Cloudhouse indulges in detecting security threats. It also offers complete app security to identify and block suspicious activity.
Cisco Pros & Cons:-
Pros-
- Ability to handle L2/L3 traffic for all large data center deployment
- Easy-to-integrate with almost all cloud services
Cons-
- You might encounter some bugs.
Cisco: Customer Reviews

6. Proofpoint

Proofpoint is a robust cloud security solution that will help you access cloud services and applications. The platform offers high-level threat protection driven by forensic insight and threat intelligence that mitigates the risk of any cloud threat. You can also enable an advanced threat protection option for access control and browser isolation to safeguard sensitive data.
Proofpoint Pros & Cons:
Pros-
- Compatible with most antivirus software.
- Excellent support
Cons-
- The UI is quite complex
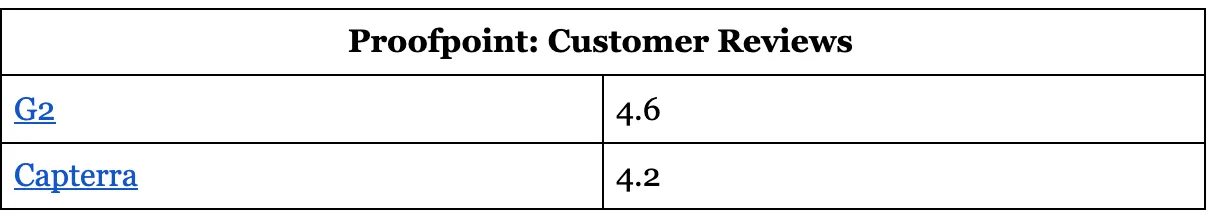
Proofpoint: Customer Reviews
7. Symantec

A complete all-in-one cloud protection platform for Software-as-a-Service (SaaS), Information-as-a-service (IaaS), and Platform-as-a-Service (PaaS). Symantec makes your cloud space adhere to the tiniest Cloud Data Protection guidelines and security spectrum. You can also integrate your existing security stack with Symantec to address evolving cloud needs.
Symantec Pros & Cons:
Pros-
- The product thoroughly detects security threats and informs whenever a suspicious file is found in the system.
- Excellent customer staff
- Easy-to-use interface
Cons-
- Customer support needs improvement
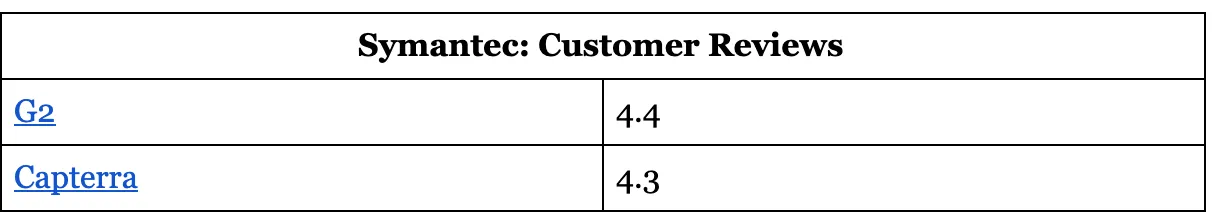
Symantec: Customer Reviews
8. Microsoft
Microsoft’s Defender for Cloud Apps is a dedicated cloud security solution that detects threats, protects all sensitive information, defends any cyberattacks, and comply with all cloud security guidelines. The platform is extremely easy to deploy with provider APIs necessary for complete real-time visibility.
Defender for cloud discovers and analyzes all cloud apps to detect any threats. Plus, the software analyzes both sanctioned and unsanctioned apps to keep your cloud safe.
Microsoft Pros & Cons:
Pros-
- Microsoft supports over 25000+ cloud apps, and the number is continuously growing.
- On-point customer support
- Easy to integrate with other Microsoft products
Cons-
- The inbuilt Azure reports can be more granular
Microsoft: Customer Reviews
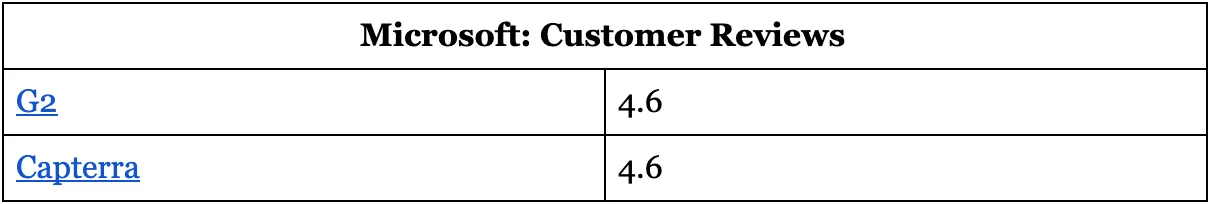
9. Forcepoint

Forcepoint is a leader in cloud security and has served over 14,500+ customers across 150+ countries. The platform guarantees early detection of high-risk behavior, reduction in data policy violations, and high operational savings. In addition, it provides a holistic solution to safeguard any sensitive information and provide complete visibility to your cloud.
Forcepoint Pros & Cons:
Pros-
- Easy to use interface and user dashboard
- The DLP feature allows you to detect high-risk users, unauthorized sharing, and real-time threats.
- It also covers USB and printer leakage
Cons-
- Technical support requires improvement.
Forcepoint: Customer Reviews
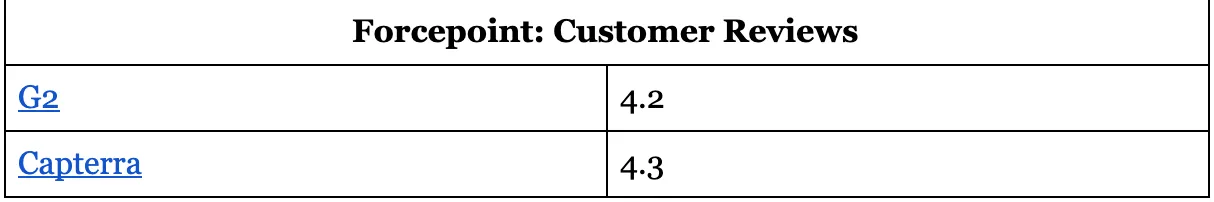
10. Cipher Cloud
Cipher Cloud, now part of Lookout, offers endpoint cloud security to its users. The platform includes advanced DLP (Data Loss Prevention Mechanism) that offers complete data protection and visibility for IaaS and SaaS applications. CipherCloud secures your cloud via Security Posture Management (SSPM) and Cloud Security Posture Management (CSPM).
These solutions conduct a comprehensive automated assessment for both IaaS and SaaS platforms to prevent data loss and ensure complete data compliance for your cloud space.
CipherCloud Pros & Cons:
Pros-
- Outstanding technical support
- Supports both G-suite Office 365
- A flexible and scalable cloud-security solution
Cons-
- The onboarding can be smoother
Cipher Cloud: Customer Reviews
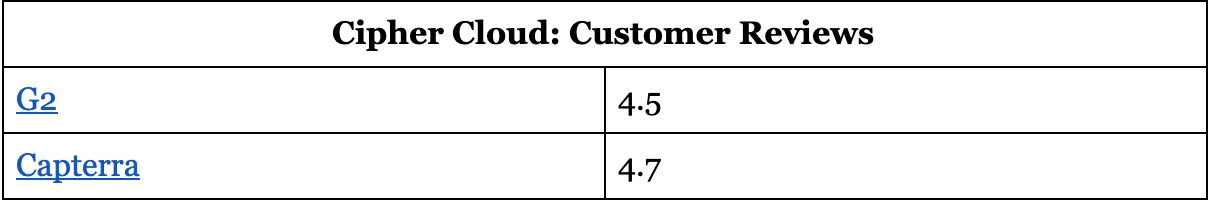
11. Trend Micro

Trend Micro is a comprehensive CASB solution to protect cloud users against advanced security threats and data policy violations. The software supports G-Suite, Office 365, and other file-sharing platforms. They claim to analyze 100TB of threat information to detect any threats.
Trend Micro is a holistic cloud security solution for all consumers, small businesses, and enterprises. It also has 240 pre-built data compliance templates to manage user policies.
Trend Micro Pros & Cons
Pros-
- The Trend Micro Apex endpoint solution offers an exceptional threat detection mechanism and easily integrates into the user's dashboard.
- Excellent customer support
- Ease of connectivity with other platforms
Cons-
- Product documentation can be better
Trend Micro: Customer Reviews
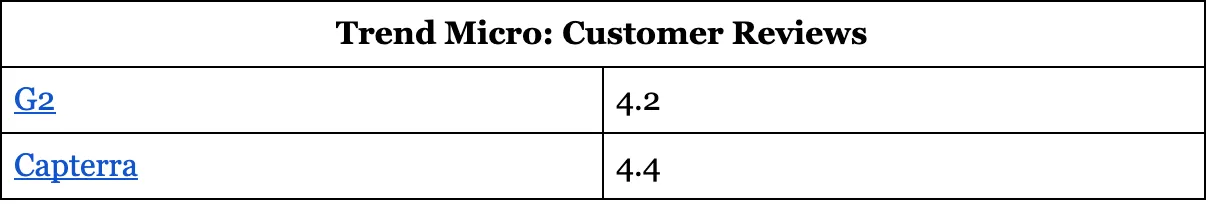
12. Zscaler
Zscaler is a go-to solution for any business looking to build a secure cloud presence. It offers an excellent zero-trust architecture built to reduce all cloud risk by detecting security gaps and minimizing any future attacks. The platform also ensures proper configurations and compliance with all data policies.
Zscaler Pros & Cons:
Pros-
- Highly consistent performance with automated features
- Easy to navigate and understand
- On-point technical support
Cons-
- Does not notify if the application a user is still connected to the application
Zscaler: Customer Reviews
13. Censornet
Censornet is one such dedicated solution that offers users complete visibility, data-policy compliance, and safety against advanced threats. The CASB solution meets the needs of every organization with optimum flexibility to deploy and operate. Censornet analyzes all files uploaded on the cloud apps and looks for any suspicious threats. Users will have access to thousands of actions and hundreds of cloud-centric applications.
Censornet Pros & Cons:
Pros-
- Users can integrate web security with cloud security to safeguard both.
- Excellent customer service
- Easy to use platform
Cons-
- Reporting can be improved.
14. Citrix
Citrix is another CASB solution that offers Zero Trust Network Access (ZITNA) to its users to safeguard their cloud platform. The software is designed to detect threats in both sanctioned and unsanctioned apps. From role-based access to identifying suspicious threats from user identity device posture and location, Citrix does it all.
Citrix Pros & Cons:
Pros-
- Easy to deploy
- Responsive UI that makes navigation smooth
Cons-
- We would have encouraged a more customizable dashboard for better reporting.
Citrix: Customer Reviews
15. CloudCodes
CloudCodes offers a holistic solution for enterprises looking to secure their cloud space. It detects threats, complies with data policy, and offers complete data visibility. The platform supports G-suite, Jira, Zoho, Slack, Salesforce, FreshDesk, and more. Its Single Sign-On (SSO) feature saves users from the password hassle and allows them to access their application from anywhere.
CloudCodes Pros & Cons:
Pros-
- Role-based access
- Great for remote working
Cons-
- It lacks direct customer support to entertain immediate concerns.
CloudCodes: Customer Reviews
Why Zluri is Better than CASB for Securing Securing SaaS Stack
Though CASB solutions are a good solution for securing platform as a service (PaaS) and infrastructure as a service (IaaS) platforms, for software as a service (SaaS), Zluri, a SaaS management platform, has advantages over CASBs:
- Remote-first approach: CASBs primarily filter the data through logs (network packets, firewall, secure web gateways, endpoints) via deep packet inspection (DPI). Though this might work in the office environment, where the data can be controlled by flowing through the determined network, this is not enough for today's modern remote world.
- Users can now access applications on the internet without going through a specific network. Furthermore, the logs are never exhaustive in nature. On the other hand, Zluri being connected to the source—the application itself, never misses any data, and the accuracy is high too.
- Integration: Zluri has deep integrations with 300+ applications, including SSO (a few CASB and SIEM integrations including MCAS are under development), along with browser and desktop agents. We ensure to discover all the applications fully—both approved and unapproved (shadow IT) apps used by an employee.
- Multiple sources: To provide 100% coverage, Zluri has multiple sources of information. We prefer to get the data directly from the application, including the usage and access data for each employee across multiple devices and multiple network connections. This is our preferred source of truth.
Another source of data is the point of source; hence we focused a lot on the browser extensions and desktop agents. These are optional f0r the users. Though we can also get the activity and usage data of applications used on the device, we don't send out any data over the network via our desktop agents.
The third option is to get the data via connected systems like SSO, CASB, SWG, finance and expense management systems, etc., which gives us a secondary source of information on the usage and activity to discover the applications.
5. Application coverage: We can discover SaaS apps that keep on expanding at a much faster rate as new apps hit the market. Because of the multi-source approach, we can also help companies discover the internal applications and track the usage and activity.
This number is ten times more than MCAS's catalog, a CASB solution! In addition, with our 300+ deep direct integrations with applications, you get a plethora of information on the number of licenses, type of access being shared, security scopes, insecure connections, billing cycles, important metrics, etc., apart from just the access and usage data.
Zluri is built for the modern world where users can use any device, and we shall get information across each one of them since we do have a lot of agentless sources (with direct integrations on SSO and applications).







.png)

.svg)














