IT managers play a pivotal role in streamlining the offboarding process. They are responsible for safeguarding sensitive data, protecting valuable assets, and ensuring a smooth transition when employees leave the organization.
Therefore, streamlined user offboarding should be a top priority for every organization looking to maintain a strong security posture, build trust among customers and stakeholders, and stay ahead in the competitive landscape.
Implementing a comprehensive user offboarding process is vital for safeguarding sensitive data and upholding organization security standards. The risk of security breaches, unauthorized access, and data exposure can be effectively mitigated by promptly and thoroughly revoking access to company systems and applications when an employee or user departs.
Imagine a departing employee or user retains access to your company's SaaS applications, paving an easy way for potential security breaches and data leaks. By swiftly deactivating user accounts and revoking access privileges during offboarding, you can lock down your digital fortress, minimizing the risk of unauthorized access and data breaches. This proactive approach ensures that sensitive information remains safeguarded and in trusted individuals' hands.
Let’s take a look at a few of the compelling ways to improve this user offboarding process. Implementing these techniques can bolster data security, maintain regulatory compliance, and protect your valuable intellectual property.
Top 4 Ways to Improve User Offboarding Process
Let’s explore the top four ways to improve the user offboarding process, empowering you and teams with effective strategies to ensure a seamless transition when employees leave the organization.
1. Suspension of employee licenses
When an employee leaves the company, their access to various systems, applications, and resources should be promptly revoked to protect sensitive information. By suspending licenses, your IT team eliminates the risk of ex-employees potentially misusing or leaking confidential data, whether intentionally or accidentally.
Insider threats, where former employees exploit their knowledge and access to harm the organization, can pose significant risks. By suspending licenses immediately, your team minimizes the window of opportunity for ex-employees to exploit their privileges and engage in malicious activities such as unauthorized data access, theft, or sabotage.
Further, suspending employee licenses upon offboarding helps ensure compliance by preventing unauthorized access to data and systems.
Promptly disabling employee licenses demonstrates a responsible and proactive approach to data security. Clients, partners, and stakeholders place their trust in your organization's ability to safeguard their information. By preventing unauthorized access by former employees, you maintain that trust and protect your company's reputation.
2. Revoking system access control from SSO
Revoking system access from single sign-on (SSO) is crucial to prevent unauthorized access to critical systems and sensitive information. Promptly disabling SSO access when employees leave the organization proactively protects against data breaches, intellectual property theft, and security threats from unauthorized access.
Over time, inactive user accounts, including those of former employees, accumulate and pose a significant security risk. By revoking SSO access upon an employee's departure, your IT administrator can eliminate these dormant accounts, reducing the attack surface and strengthening overall security.
Revoking SSO access aligns with strict compliance regulations such as HIPAA, GDPR, and PCI DSS. This measure ensures that sensitive data is only accessible to authorized individuals, meeting regulatory requirements.
By revoking SSO access, you can help greatly reduce the likelihood of disgruntled or malicious employees exploiting their previous access privileges. This measure is a crucial safeguard against intellectual property theft, sabotage, and unauthorized modifications to critical systems, effectively mitigating the potential impact of insider threats.
3. Securely transfer employee data when access is revoked
Ensuring the integrity of employee data is paramount. When revoking access to an employee's account, it is crucial to securely transfer their data to prevent any loss, corruption, or unauthorized access. By prioritizing data integrity, vital information remains intact and reliable for future use.
In addition, it is essential to consider specific legal and regulatory requirements related to data protection and privacy, depending on your organization's industry and location.
Neglecting secure data transfer can result in severe consequences, including potential fines, penalties, and damage to your reputation. Adhering to industry best practices and compliance guidelines is necessary to mitigate legal risks effectively.
Employee data often contains sensitive and confidential information, such as personal details, financial records, and intellectual property. Mishandling or exposing this information during the transfer process can lead to severe consequences, ranging from identity theft to corporate espionage. Therefore, safeguarding sensitive data should be a top priority to uphold the trust of your employees and maintain your organization's reputation.
4. Enhancing security measures through comprehensive audits
Conducting security audits after an employee's departure is crucial for your team to maintain a robust cybersecurity posture. These audits involve identifying and addressing access points linked to the offboarded employee, such as email accounts, network privileges, and cloud storage. Reviewing and revoking these access rights can eliminate the risk of unauthorized access and data breaches.
Security audits also help monitor departing employees' activities and potential interactions with critical systems or sensitive data. By scrutinizing their actions, suspicious behavior can be detected, and measures can be taken to mitigate insider threats.
Security audits after an employee's departure provide an opportunity to evaluate the organization's overall security posture. By reviewing access controls, data protection mechanisms, and security protocols, weaknesses or gaps can be identified and addressed, ensuring continuous improvement of the security framework.
Now, you understand the challenges that come with offboarding employees from your organization's IT ecosystem. The process can be time-consuming, prone to errors, and leave your company's sensitive data vulnerable. That's where Zluri comes in.
Zluri offers a cutting-edge SaaS management platform that helps to automate the user offboarding process. With its robust features, Zluri empowers your team to overcome offboarding challenges, reduce repetitive tasks, and enhance overall efficiency.
How Zluri Helps Automate the Employee Offboarding Process
One of the key strengths of Zluri lies in its ability to help you and your team gain complete visibility into your SaaS ecosystem with 100% accuracy. Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.

Zluri’s nine discovery methods
But what sets Zluri apart from other solutions is its comprehensive approach to data protection. When it comes to terminating a user's account, Zluri seamlessly performs a data backup and securely transfers it to a reliable cloud storage solution like AWS. This ensures that your company's valuable information remains safeguarded even after an employee's departure.
With Zluri, you can bid farewell to the hassle of drawn-out offboarding procedures. By efficiently removing departing employees from all the applications they were using, Zluri streamlined the process, saving you time and effort. You will no longer have to manually navigate multiple systems or worry about missing crucial access revocations.
Zluri's direct integration with SaaS apps elevates its automation capabilities to new heights, surpassing other solutions in the market. By automating various IT processes and enhancing app and data security, Zluri proves to be an indispensable tool aiming to optimize your offboarding workflows.
Zluri's user-friendly interface makes navigating the offboarding process easy, saving you time and effort. With recommended actions tailored to each application, you'll receive intelligent suggestions to complete the deprovisioning process seamlessly. This means you can customize your actions according to your specific requirements, ensuring a smooth and hassle-free offboarding experience for your IT team.

Zluri's advanced functionality includes an intelligent backup feature specifically designed to safeguard the data stored in an employee's Google Drive before terminating their licenses. This means that before the offboarding process begins, Zluri automatically creates a secure backup of all the data in the employee's Google Drive, ensuring nothing is lost during the transition.
With Zluri, you can rest assured that no valuable data will be lost or inaccessible, making it easier for the new employee to take over the responsibilities and continue with minimal disruption seamlessly.
While many solutions focus on single sign-on (SSO) or Google Workspace, Zluri takes data security to the next level by ensuring comprehensive app deprovisioning across all applications.
Zluri leverages the power of application programming interfaces (APIs) to establish deep integrations with a wide range of applications. This direct integration allows Zluri to communicate with apps at a granular level, empowering you to successfully deprovision access for ex-employees. With over 300+ different applications already connected, Zluri provides a seamless offboarding experience, regardless of the apps your organization relies on.
Zluri performs a series of actions to ensure proper offboarding every time. Let's see why Zluri is the ideal choice for streamlined offboarding:
- Eliminate access to devices: Zluri takes the first step by removing all authentication from the various devices associated with the user. Whether they were signed in on multiple devices or applications, Zluri ensures that the user's access to those devices is completely eliminated. This prevents unauthorized usage and reinforces the security of your organization's apps.
- Backup of the data: Data backup is a critical aspect of the offboarding process, and Zluri has got you covered. It takes a comprehensive backup of the user's data and securely stores it. This helps prevent any data loss and enhances knowledge transfer within your organization. By preserving the user's data, Zluri ensures the continuity of operations and safeguards your organization's sensitive information.
- Revoke the user's license: Once the data backup is completed, Zluri seamlessly returns to the app and revokes the user's license. This action effectively removes the user's ability to access the application, ensuring that they can no longer utilize any functionalities tied to their account. By revoking the user's license promptly, Zluri helps maintain data security and prevents unauthorized app use.
- Remove SSO: As the final step in the offboarding process, Zluri removes the SSO authorization. This ensures the user can no longer access your organization's SSO system, safeguarding your apps and sensitive data. By removing SSO, Zluri reinforces the security of your IT ecosystem and ensures that the offboarding process is comprehensive and thorough.
Creating a seamless offboarding workflow has never been easier with Zluri. Follow these crisp steps to streamline your offboarding process:
1. Navigate to Zluri's main interface and access the workflow module. Choose the offboarding option from the drop-down list and click on \"New Workflow.\"

2. "Select the user for offboarding," choose the employee(s) you wish to offboard, and click "Continue" once you've made your selection.

3. When you click on an app, Zluri provides a comprehensive overview of the employee's access privileges and presents you with recommended actions specific to that app. Choose from a range of suggested actions and effortlessly execute them across the selected applications.
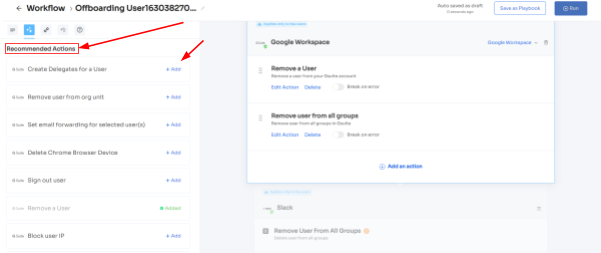
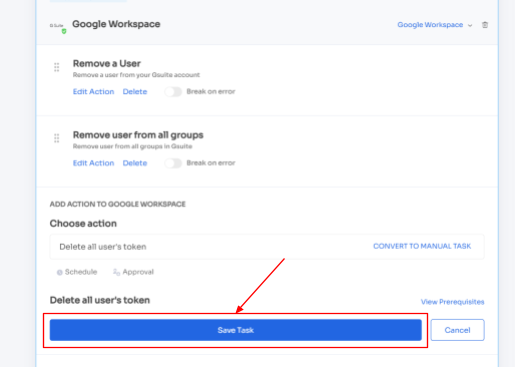
4.To include additional actions, click "Add an Action" Fill in the required details and save the task by clicking "Save Task." Your actions will be saved and ready to be executed.
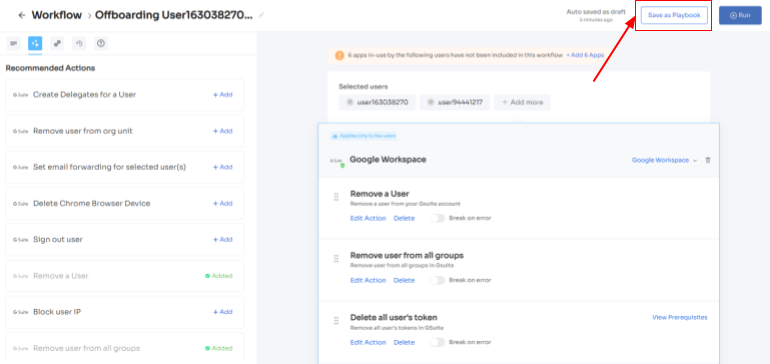
5. Finalize the workflow by saving it as a playbook. Provide a name, click "Save Playbook," and voila! Your offboarding workflow is now set and ready to go.
Take control of your offboarding procedures and optimize your workflow with Zluri. Experience the benefits of a centralized, automated, and secure offboarding process. Start using Zluri today and transform the way your team manages employee departures. Book a demo now.









.svg)














