As an IT manager, you understand the importance of cloud security and the need for a robust CASB solution. Netskope's CASB is a powerful solution that helps you secure your organization’s cloud-based operations and safeguard sensitive data.
Netskope's CASB helps you mitigate the risks associated with cloud-based applications and data by giving you the visibility and control you need to safeguard sensitive information.
However, it has certain drawbacks that restrict you from securing your cloud environment efficiently. For example, the solution initially consumes time to set up and configure, wasting time and delaying the detection of security issues. So, you might want to consider other options from Netskope alternatives.
But before we do that, let's briefly examine Netskope and its limitations, giving you the information you need to make a well-informed decision later on.
Netskope CASB: An Overview
Netskope's Cloud Access Security Broker (CASB) is a cybersecurity solution providing a comprehensive view of cloud services, applications, and user activities. Thus, Netskope CASB helps to keep everything safe and secure in your cloud operations. Accessible from any location and device, this platform operates on a data-centric approach, ensuring a careful balance between robust protection and optimal speed essential for a secure cloud transformation journey.
When it comes to threat protection, Netskope employs a multi-faceted strategy. Leveraging the power of Cloud Access Security Broker (CASB), a secure web gateway, and a sophisticated multi-layer threat detection and remediation system, Netskope provides a shield that comprehensively encompasses cloud and web services. This ensures a robust defense mechanism against various threats and vulnerabilities, making the digital landscape safer and more secure for organizations leveraging this platform.
With Netskope, you can easily manage your cloud platforms, including popular ones like Office 365, Box, and Dropbox. It offers tools to assess risks and discover threats, improving visibility and ensuring compliance with security rules.
Drawbacks of Netskope CASB
Here are a few drawbacks of Netskope’s CASB for your reference:-
- The cost of implementation can be a hurdle, especially for smaller organizations with tight IT budgets, making it challenging for them to justify the expense.
- Its complex learning curve may restrict users from fully harnessing its capabilities, and mastering the entire tool can be time intensive.
- The tool is incompatible with various cloud services that an organization uses, creating gaps in the organization's security coverage and leaving data vulnerable.
Customer ratings
- G2: 4.4/5
- Capterra: 4.8/5
Now, considering alternative solutions is always a good idea to ensure you get the best possible security for your organization's needs. This post will discuss a list of suitable Netskope alternatives for your organization.
But before discussing the tools, let's take a moment to introduce who we are and what solutions we provide at Zluri for you.
Zluri - An Ultimate Solution for Managing Your SaaS Landscape
Zluri assists you in identifying, tracking, and managing the complete SaaS landscape of your organization. For this, it uses five advanced discovery methods to ensure 100% discovery of all SaaS apps within your organization. Once identified, Zluri provides a range of security and compliance information to ensure you meet every compliance requirement.
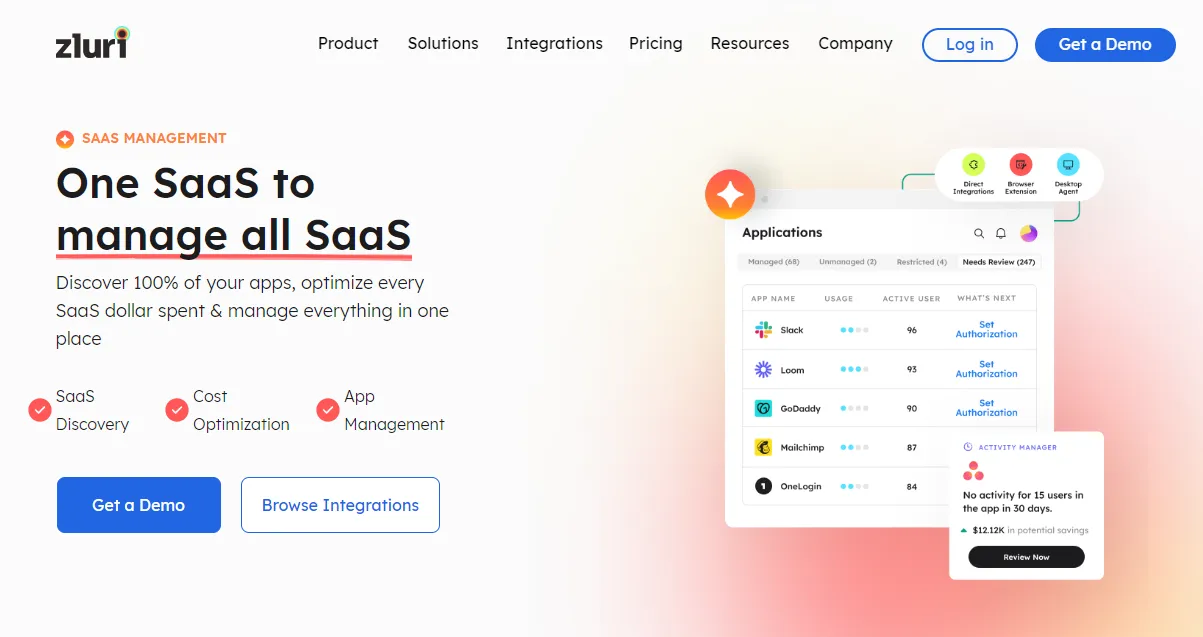
It provides all the information related to events, shared data, and compliance and security probes for SaaS applications. This way, you can work towards achieving compliance while simultaneously meeting your security goals.
Zluri keeps you up-to-date with any events related to your apps while they are in use. We actively curate this information from various online sources and present it in a centralized location - Events. This includes critical updates, security vulnerabilities, data breaches, and other relevant news that may impact your SaaS applications.

Connecting apps with each other can grant varying degrees of access to the data of the connected app, ranging from read-only to write, modify, and delete access. The threat level increases with the sensitivity of the data accessed by an app.
For instance, an app with access to Google Drive and the ability to modify or delete files would be considered a high threat.
Also, Zluri provides comprehensive compliance information for each app, highlighting which compliance frameworks they adhere to. This allows you to easily assess the compliance status of your SaaS applications and ensure that they meet your organization's regulatory requirements.

Moreover, Zluri's risk scoring system considers the number of compliance frameworks an app adheres to. The higher the number of frameworks, the higher the app's risk score will be, indicating a lower risk of non-compliance and better overall compliance posture.
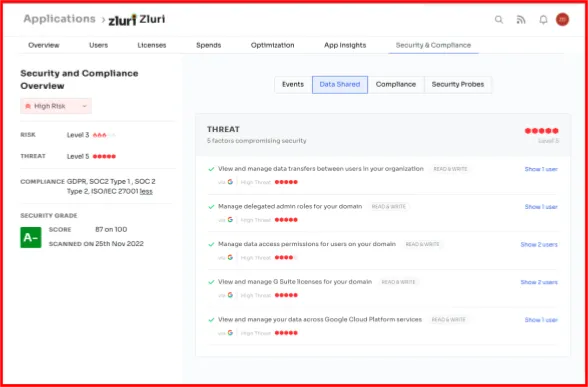
Finally, security probes give you a view of the technical scanning. The scanning is done every month. But this is customized as per the requirement of your organization.
Zluri prioritizes the security of your sensitive data by utilizing secure encryption algorithms. Thus, you can stay assured that all your data remains secure. It also provides you with a comprehensive and auditable log of key activities, enabling you to keep track of all app security-related activities.
All data collected, such as SaaS-app usage metrics, is retained indefinitely unless a removal request is made. Zluri stores all data in an encrypted state, backing it up for 60 days to ensure it's always available when needed.
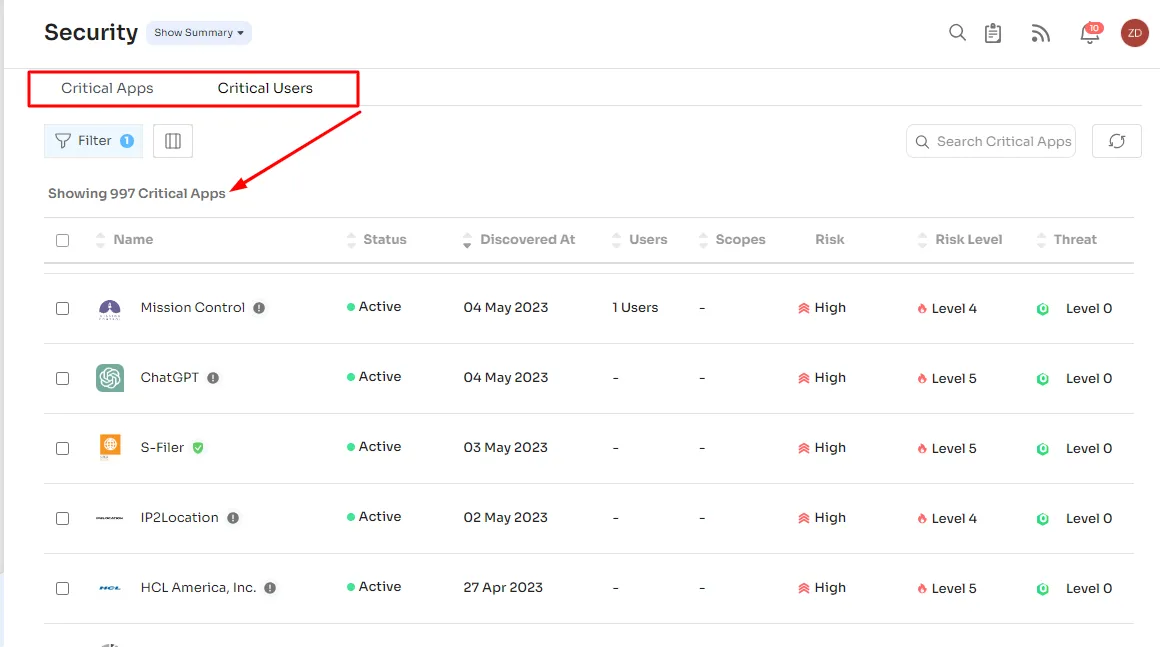
Moreover, Zluri goes the extra mile by providing you with a view of critical apps with high threat levels and risk scores. It also alerts you not to use critical apps that can impact data confidentiality and prevent data from cyber-attacks, so you can take the necessary precautions to keep your organization secured.
Besides its robust security capabilities, Zluri provides other essential advantages that enable you to manage your SaaS applications efficiently.
Key Benefits Of Zluri
Let us discuss some other key benefits of using Zluri.
- SaaS License Optimization: Zluri streamlines the process of tracking, identifying, and reporting SaaS licenses for your organization. By automating these tasks, you can easily access a comprehensive view of all your SaaS licenses in one place, providing complete visibility into your SaaS stack.
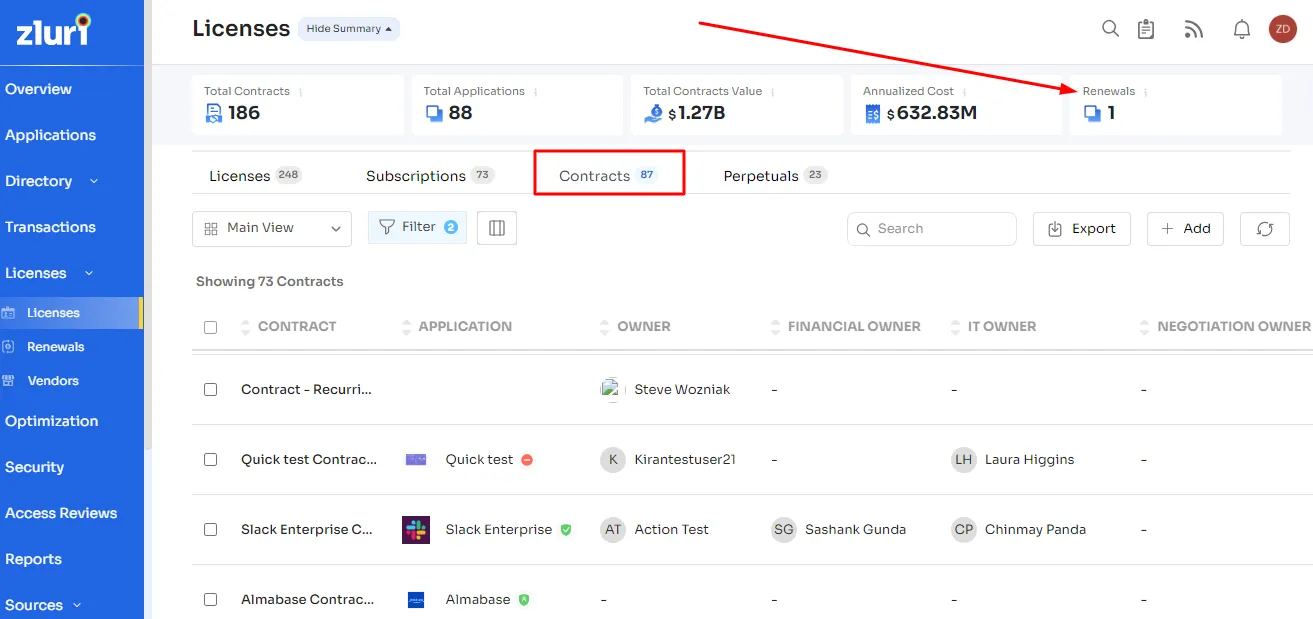
- This allows you to monitor SaaS usage by employees and identify redundant or duplicate apps, helping you save costs and protect your organization from security breaches arising from non-compliant or unlicensed SaaS usage.Moreover, Zluri enables you to right-size your SaaS licenses to suitable tiers by tracking their usage, business requirements, and more. This feature helps you optimize costs and make better-informed decisions when it comes to managing your SaaS licenses.
- Renewal Management: No more last-minute scrambling or missed renewals - Zluri’s renewal calendar provides a comprehensive view of all your subscription renewals, enabling you to plan ahead and ensure a smooth renewal process. Whether you have a large or small renewal coming up, a renewal calendar helps you prioritize your preparations and stay organized.
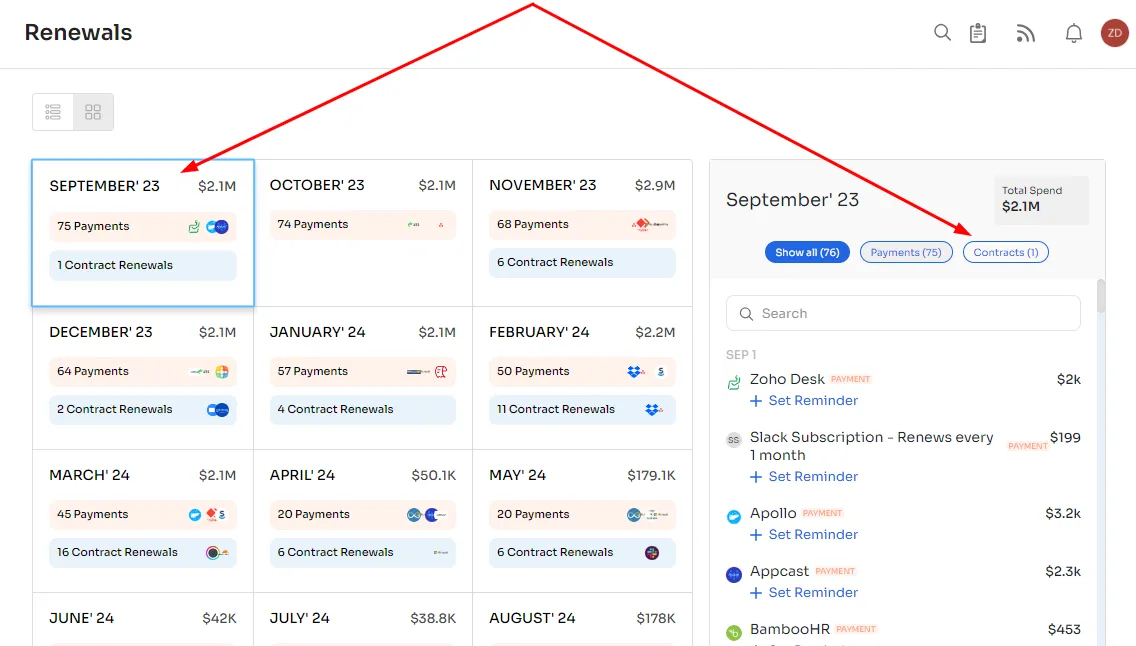
- Moreover, Zluri sends automatic alerts on renewal updates, making it easy for you to stay on top of your SaaS license renewals. You can also manually set notifications at your convenience, prioritizing the most critical renewals to ensure uninterrupted service.
- Usage Monitoring: Zluri allows your IT teams to track the usage of SaaS applications across their organization efficiently. By leveraging usage data, your team can quickly identify underutilized software applications and optimize your organization’s SaaS stack for better efficiency and cost savings.Without a robust solution like Zluri, manually tracking app usage can result in errors and make detecting duplicate or redundant apps challenging. However, with Zluri, you can effortlessly track SaaS usage, gaining valuable insights into your SaaS apps and identifying any unnecessary duplicates that can be eliminated to save costs.For instance, if you're working in an organization that tracks app usage manually, you know how time-consuming and error-prone it can be. But with Zluri, you can automate this process and easily detect any underutilized or duplicate apps, allowing you to optimize your SaaS stack and save money. With Zluri, your IT team can easily manage your organization's SaaS applications.
- Cost Optimization: Zluri helps you reduce SaaS spend by identifying unused licenses, comparing prices across different vendors, and providing insights to negotiate better contracts.
- Vendor Management: Zluri is equipped with an automated vendor management system that provides you with all the essential features required to manage your entire SaaS stack effectively. With Zluri, you can gain better visibility and control over the constantly evolving tech stack.What sets Zluri apart is its ability to maintain a SaaS system of record by seamlessly integrating with your core business systems. This ensures that all the data related to your SaaS vendors are accurately recorded and easily accessible. Zluri streamlines your vendor lifecycle management with predefined workflows, allowing you to focus on your core business operations.
List of 10 Netskope Alternatives
Let us explore the various alternatives to Netskope’s CASB.
1. Forcepoint’s CASB
Forcepoint's CASB solution is designed to provide you with real-time visibility and control over cloud applications, enabling you to quickly detect and prevent security threats and data breaches.
The solution also boasts advanced DLP capabilities, allowing you to identify and prevent data breaches by detecting sensitive data and applying policies to prevent unauthorized access.
With Forcepoint's CASB, you gain granular control over cloud application usage, enabling you to set policies that govern access permissions and prevent unauthorized data sharing.
Also, the solution provides powerful threat detection capabilities, leveraging advanced analytics and machine learning to identify anomalous activity and mitigate threats in real-time.
Pros
- The solution’s functionalities are easy to implement, allowing you to quickly learn and start securing your organization’s IT infrastructure and manage it from a single console
- It gives you the flexibility to configure your systems with email notifications, enabling you to monitor and troubleshoot the issue quickly
Cons
- When it comes to CASB integration and google cloud integration, the solution does not offer sufficient security capabilities, limiting your ability to detect issues entirely
- The solution’s licensing can be a challenge for you, leading to time consumption that could be used to focus on other important tasks
Customer ratings
- G2: 4.5/5
2. Cisco Cloudlock
Cisco Cloudlock is a cutting-edge cloud security platform that delivers real-time visibility and control over cloud applications, spanning SaaS, PaaS, and IaaS. Cloudlock empowers you with valuable insights into how data is accessed and shared, enabling you to rapidly detect and respond to security threats.
Cloudlock is a centralized platform streamlining security management across all cloud applications and data, helping your IT admin reduce risk and prevent data breaches. By leveraging Cloudlock, your security teams can effectively manage access permissions, monitor data usage, and prevent unauthorized data exposure from a single glass pane.
Furthermore, Cloudlock provides granular controls for managing data sharing, enabling you to set policies that govern which data can be shared and with whom. This helps you control organizations' sensitive data and mitigate risks associated with data sharing.
Pros
- With Cloudlock, it is easy to deploy and integrate with your existing system, making it convenient for your team to monitor, identify, and resolve security issues
- The solution provides all the alerts related to security issues like threats or cyberattacks, allowing you to identify the problem and resolve it quickly
Cons
- Cisco isn't a better option if you have a tight budget for a cloud security solution. That's because it is a premium solution that comes with a higher price tag
- The solution’s interface is complex to navigate, requiring you to dedicate additional time and resources to training and implementation
Customer ratings
- Capterra: 4.5/5
3. Fortinet’s Cybersecurity Services
Fortinet is a provider of cybersecurity solutions catering to organizations of all sizes. Their comprehensive suite of products includes FortiGate firewalls, FortiAnalyzer for security analytics, and FortiManager for centralized management.
One of Fortinet's standout products is the FortiGuard cloud access security broker (CASB). This solution gives you increased visibility and control over cloud applications and services used within your organization.
With FortiGuard CASB, you can monitor and regulate access to cloud applications and services across all endpoints, including mobile devices and remote workers. This ensures that sensitive data is protected from unauthorized access and ensures that regulatory compliance is maintained.
In addition, FortiGuard CASB provides real-time threat protection, malware protection, and other security risks that can occur within cloud environments. By leveraging advanced threat intelligence and machine learning, you can proactively detect and mitigate potential threats to your organization's data.
Pros
- It gives you real-time threat insights, providing you with up-to-date information about potential cyber threats
Cons
- It lacks visibility in tracking the attacks, making it difficult for your team to manage the security efficiently
- Some of its features are complex to use, resulting in investing more time in practice or getting trained by experts
Customer ratings
- G2: 4.7/5
4. Zscaler’s Data Protection
Zscaler is a cloud security solution, and its Cloud Access Security Broker (CASB) solution stands out for its robust data protection capabilities. The platform combines traditional CASB functionalities with advanced security features like machine learning and behavior analysis.
With Zscaler CASB, you gain comprehensive visibility into cloud usage, enabling your IT admin to monitor user activity, identify threats, and enforce policies across multiple cloud services. The system automatically classifies sensitive data and applies policies based on sensitivity, ensuring only authorized personnel can access it.
Moreover, Zscaler CASB also harnesses the power of machine learning and behavior analysis to identify and thwart cyber threats such as malware, phishing attacks, and data exfiltration.
Pros
- It is easy to use and understand the functionalities, allowing you to quickly learn and start using the tool to protect your cloud applications efficiently
- The tool gives you the flexibility to customize your organization’s security policies and procedures to your requirements, ensuring that your organization’s data is secure
Cons
- If you have a limited budget for a CASB solution, then this solution is not a suitable one as it is expensive compared to other CASB tools
- The tool has a steep learning curve, requiring you to dedicate more time and resources in training your team
Customer ratings
- G2: 4.7/5
5. Akamai’s Security Solutions
Akamai's security solutions include various products and services that address different security needs. It helps you to safeguard your organization's data and networks and provide peace of mind in an ever-changing threat landscape.
It provides a web application firewall that protects against common attacks like SQL injection and cross-site scripting. This can be customized to suit the needs of different industries, such as healthcare or financial services, and can integrate with existing security tools.
Another important solution is Akamai's Bot Manager, which helps you detect and mitigate bot traffic. Bots can be used for various purposes, from scraping data to launching DDoS attacks, and can be difficult to detect. Bot Manager uses machine learning and behavioral analysis to identify and block malicious bots while allowing legitimate traffic to pass through.
In addition, Akamai offers services like DDoS protection, threat intelligence, and secure content delivery. It enables you to take a proactive approach to security rather than waiting for an attack to happen.
Pros
- Akamai's security solution protects against distributed denial of service (DDoS) attacks, ensuring that your website and applications remain accessible to the employees
- The solution is capable of generating traffic reports, enabling you to block the unwanted IPs in your organization’s network
Cons
- It is expensive and consists of hidden charges, making it difficult for you to procure it if your organization has limited budgets
Customer ratings
- G2: 4/5
6. F5’s Network Security Solution
F5 is a provider of network security solutions for businesses of all sizes. Their solutions are designed to protect networks from a wide range of threats, including malware, phishing, and DDoS attacks.
F5's network security solutions provide real-time visibility and control over network traffic, helping you monitor your organization’s network for potential threats and prevent them before they can cause any damage. It also offers advanced threat protection capabilities, which can help you detect and respond to emerging threats more quickly and effectively.
Further, F5's network security solutions offer advanced access control features, which can help you ensure that only authorized users are able to access their networks. This can help prevent data breaches and other security incidents and can also help your organization comply with industry regulations and standards.
Pros
- It provides real-time visibility into network traffic, enabling you to detect the issues and block any unauthorized access in real-time
- It is easy to configure and manage security policies across the entire network, simplifying the management process and reducing the likelihood of configuration errors
Cons
- The tool is expensive compared to other CASB tools, creating a barrier to adopting it for some organizations, especially the smaller ones
- It has a steep learning curve associated with deploying and managing F5's network security solution, requiring you to invest time and resources into training your team to use the product effectively
Customer ratings
- G2: 3.9/5
7. Symantec’s CloudSOC CASB
Symantec's CloudSOC CASB (Cloud Access Security Broker) is an enterprise-class security solution that provides comprehensive visibility and control over an organization's cloud applications and services.
It helps protect sensitive data, monitor cloud usage, and enforce security policies across the organization's cloud environments.
The solution provides you with deep visibility into cloud usage across your organization. This visibility helps you to identify potential security risks and take proactive steps to prevent data loss or theft.
CloudSOC CASB provides real-time alerts and notifications, allowing you to respond to security incidents and prevent data breaches quickly.
Pros
- The tools provide you with strong reporting capabilities, empowering you to get insights into the cloud apps and manage their security efficiently
- It enables you to define security policies based on users, groups, and devices, allowing you to create and enforce security policies that align with your organization's security requirements.
Cons
- The pricing structure is complex as it varies depending on the number of users, the number of cloud applications, and the level of support required, making it difficult for you to estimate the budget required to procure the solution accurately
- Sometimes it lacks complete on-demand scanning, resulting in inefficiencies in securing your organization’s entire IT infrastructure
Customer ratings
- G2: 4.2/5
8. Citrix’s Secure Access
Citrix's secure access tool is specifically designed to safeguard cloud-based applications and data against security threats. Acting as a bridge between users and the SaaS apps used within an organization provides a secure connection that protects sensitive data from unauthorized access.
A standout feature of Citrix's Secure Access is its real-time visibility and control over cloud application usage. With Citrix, you can monitor all cloud-based activity and enforce security policies to prevent sensitive data from being exposed to unauthorized users. This level of visibility and control ensures that company data is always protected.
In addition to its robust security features, the solution provides advanced threat detection capabilities. This allows you to quickly identify and mitigate potential security threats before they can cause harm to the organization.
With Citrix's Secure Access, you can rest assured that cutting-edge security measures protect your organization’s cloud-based resources.
Pros
- The tool provides easy integration with other tools, making it efficient to manage the security of the complete cloud apps in your organization
- With Citrix's secure access, you can provide your employees with secure remote access to company resources from anywhere and on any device. This allows them to work efficiently and collaboratively, improving productivity
Cons
- The solution can be difficult to set up and configure, which can be time-consuming and require expert training.
- Sometimes the system is slow, and as a result, users may experience delays in accessing critical applications or files, leading to decreased efficiency and potential downtime
Customer ratings
- G2: 4.2/5
- Capterra: 4.1/5
9. LookOut
Lookout Cloud Access Security Broker (CASB) is a powerful CASB solution designed to enhance cloud application security and mitigate the risk of data breaches. This advanced CASB offers comprehensive visibility into cloud applications and proactively safeguards against both external and internal threats. With Lookout CASB, organizations gain full insight into user interactions, endpoints, cloud applications, and their data, enabling real-time threat detection and response capabilities.
Pros:
- This CASB solution excels in automating assessments for all cloud applications and infrastructure, ensuring that configurations are consistently maintained at a high security level. This automation streamlines security management and reduces the risk of misconfiguration.
- It offers a high degree of customization, allowing users to tailor the CASB to meet their specific security requirements. This adaptability ensures that organizations can align the CASB with their unique security needs and preferences.
- It also offers advanced search capabilities, enabling users to efficiently locate and access the information they need. This feature enhances usability and simplifies the management of cloud security.
Cons
- The extensive range of features provided by this CASB may result in an overwhelming user interface. Users may find it challenging to navigate and utilize the platform effectively due to the abundance of options and functionalities.
- The documentation provided for end-users can be complex and challenging to comprehend.
Customer Rating
- G2- 4.2/5
- Capterra- 4.7/5
10. Iboss CASB
The iboss Cloud Access Security Broker (CASB) is a robust solution that equips organizations with the essential tools to establish fine-grained security controls and gain unparalleled visibility into their cloud applications. With iboss CASB, users can confidently access cloud applications without exposure to potential threats. This comprehensive platform offers a range of features, including the ability to scrutinize data at rest within various cloud services.
Moreover, it provides detailed insights into cloud application usage patterns and categorizes users based on their respective risk levels. In essence, iboss CASB empowers organizations to embrace the cloud with enhanced security and a clear understanding of their cloud environment.
Pros
- This CASB solution excels in preventing data loss by proactively identifying and mitigating risks associated with shadow IT. By offering robust protection against unauthorized data transfers and access, it helps organizations maintain control over their sensitive information.
- Users benefit from exceptional customer support services, ensuring a smooth and trouble-free experience with the CASB. The availability of responsive and knowledgeable support teams enhances user satisfaction and problem resolution.
Cons
- Despite its overall efficiency, the system faces occasional application performance challenges. You may experience intermittent slowdowns in application responsiveness, which can be a drawback in situations where optimal speed and performance are crucial.
- A notable concern with this solution is its cost. The investment required for implementation and utilization is relatively high, making it less accessible for smaller organizations or those with budgetary constraints.
Customer Rating
- G2- 3.2/5
- Capterra- 5/5









.svg)














