As an IT manager, you recognize the critical importance of securing your organization's digital assets. One Identity is a tool that has gained popularity for its role in establishing an identity-centered security strategy.
However, despite its popularity, One Identity does have certain limitations. Thus, exploring One Identity alternatives becomes imperative, seeking solutions with enhanced features and increased flexibility.
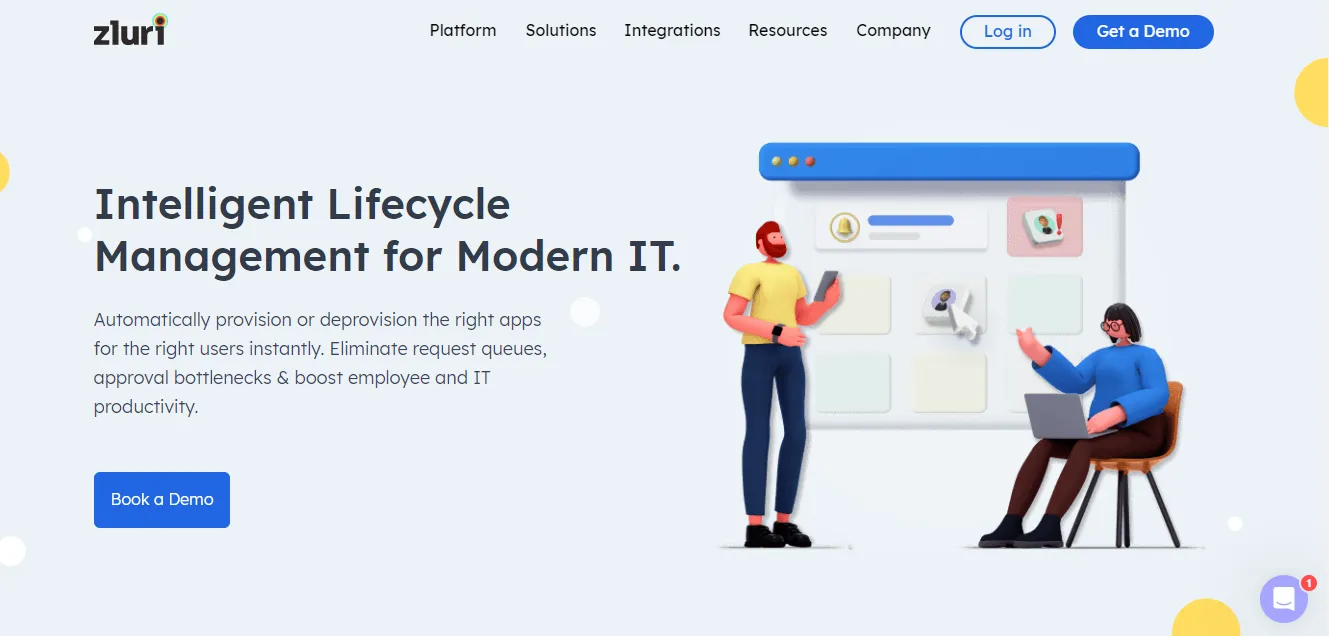
Identity & access management software offers a complete solution to regulate and fortify user identities and access privileges to your organization's critical assets. It plays a crucial role in ensuring that the right individuals have the right access to the right systems and data. One Identity stands out by providing cloud-first identity management services, encompassing AD account lifecycle management, identity governance and administration, and privileged access management.
Despite its myriad features, One Identity is not without its drawbacks. As a result, you might be exploring the best One Identity alternatives.
This blog post delves into prominent One Identity competitors, highlighting their unique features, pros, cons, and overall merits. Armed with this information, you'll be well-equipped to make an informed decision.
Before exploring alternatives, let's explore more about the One Identity and its challenges, prompting the search for suitable alternatives to One Identity.
One Identity - An Identity Management Platform
One Identity offers a unified identity security solution, empowering organizations to enhance cybersecurity and safeguard critical applications and data. As a key component of Quest Software, One Identity contributes to developing an identity-centered security strategy within organizations.
With One Identity, you can customize access levels based on your team's requirements, ranging from full credentials to Zero Trust and least-privileged models. This empowers you to create a tailored and robust security framework aligned with your organization's needs.
Utilizing One Identity PAM enhances security by mitigating risks related to privileged access, offering granular control over user permissions. The solution facilitates the monitoring of privileged activities and the detection of suspicious behavior and provides valuable insights for analysis and compliance requirements.
Nevertheless, the implementation of this solution presents complexities. In the subsequent discussion, we will explore alternative solutions to One Identity. Before delving into these alternatives, let's delve deeper into the intricacies of One Identity.
Key Drawbacks Of One Identity Platform
While One Identity offers a robust identity management solution, it does come with some potential drawbacks and, due to which you might need One Identity alternatives:
- Cost Barrier: One of the significant challenges associated with adopting One Identity management is its relatively high price point. The cost factor poses a considerable hurdle, making the buy-in for One Identity management challenging for organizations. This pricing consideration may require careful evaluation and budget planning to ensure the investment meets the organization's financial constraints and expectations.
- Limited Reporting Capabilities: Limited Reporting Capabilities: One Identity may fall short for those who prioritize robust reporting functionalities. While it effectively manages Identity and access, the tool lacks the comprehensive features to generate in-depth analytical reports. This limitation restricts the depth of insights available to organizations, potentially impacting their ability to derive meaningful conclusions from the data.
- Complex User Interface: The tool's interface presents a formidable challenge, introducing a layer of complexity to access management operations. Navigating through intricate interfaces can hinder your team's efficiency, leading to a suboptimal user experience. The time spent grappling with the complex interface is valuable time that could be otherwise allocated to more critical tasks, potentially affecting overall productivity.
- Implementation Complexity and Learning Curve: Based on some user reviews, one notable drawback of One Identity management lies in its complexity, demanding a substantial investment of time for both implementation and learning. While the platform boasts compatibility with various tools, its intricate nature necessitates the assistance of a professional. The extended learning curve and implementation complexity can pose challenges for organizations seeking a seamless integration process and swift adaptation by their teams.
Now that you know the drawbacks, let's now delve into essential factors to consider when evaluating your next set of One Identity alternatives.
Key Considerations For Selecting One Identity Alternatives
Choosing suitable One Identity alternatives or identity security solutions is critical for any organization. As you explore alternatives to One Identity, a thoughtful evaluation based on specific criteria becomes imperative. The following key considerations are instrumental in guiding your decision-making process.
- Functional Fit: Assess whether the alternative aligns with your organization's specific identity security needs and operational requirements. Ensure it offers the necessary features and capabilities to effectively replace or complement One Identity.
- Scalability: Evaluate the scalability of the alternative solution, considering your organization's growth trajectory. A scalable alternative should accommodate expanding user bases and evolving security demands without compromising performance.
- Integration Capabilities: Check the compatibility of the alternative with your existing IT infrastructure. Seamless integration with other tools and systems is crucial for maintaining a cohesive and interconnected security environment.
- User-Friendly Interface: Consider the alternative's ease of use and user interface. An intuitive and user-friendly solution can contribute to smoother adoption and reduced learning curves for your team.
- Cost Considerations: Analyze the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance expenses. Ensure the alternative provides value for your investment and aligns with your budget constraints.
- Security Features: Prioritize security features that are critical for your organization. Evaluate the alternative's ability to provide robust protection against evolving cyber threats, including features such as multi-factor authentication, threat detection, and encryption.
- Vendor Reputation and Support: Research the reputation of the alternative tool's vendor in the industry. Consider factors such as customer reviews, support services, and the vendor's commitment to addressing security vulnerabilities promptly.
- Compliance: Ensure the alternative software complies with relevant regulatory requirements and industry standards. This is essential for maintaining the integrity of your organization's data and avoiding legal and compliance issues.
Each aspect is crucial in enhancing your identity security framework, from assessing functional fit and scalability to ensuring seamless integration and evaluating security features. By carefully considering these factors, you can make an informed decision when choosing One Identity alternatives to enhance your identity security framework.
The List of Top 11 One Identity Alternatives For IT Teams
Let's explore the top 11 One Identity alternatives, each designed to cater to distinct needs, elevate operational efficiency, and strengthen digital premises environments. These alternatives offer unique features tailored to address specific challenges, providing organizations with diverse choices as they navigate the complexities of identity management.
1. Zluri
Zluri is leading the way in transforming how organizations handle identity governance and access control. The platform provides a modern access management solution, effortlessly overseeing user identities and access policies. Its seamless integration with various single sign-on (SSO) tools enforces robust authentication and authorization controls, all while continuously monitoring user activities for compliance assurance.
This integrated approach establishes a centralized access hub, streamlining the management and monitoring of privileged access. Whether granting or revoking access, the platform ensures a smooth and uncomplicated process. It empowers you to promptly identify suspicious activities, such as unauthorized access, in real-time. In the event of such incidents, immediate actions can be taken to safeguard your invaluable application data.
Furthermore, as per Kuppingercole's report, Zluri goes beyond the basics by providing extra features that allow precise control over who can access what. IT teams can customize each user's rights, ensuring only the right people can access crucial data. This helps prevent unauthorized access and makes everything more secure.
Key Highlights of Zluri's Advanced Features:
- Discovery Engine for SaaS appss’ users and core Access Insights:
Zluri employs a sophisticated Discovery Engine that identifies who has access to resources. It delivers insightful analyses of all SaaS applications and user-associated data using five distinct discovery methods, including single sign-on and identity providers.
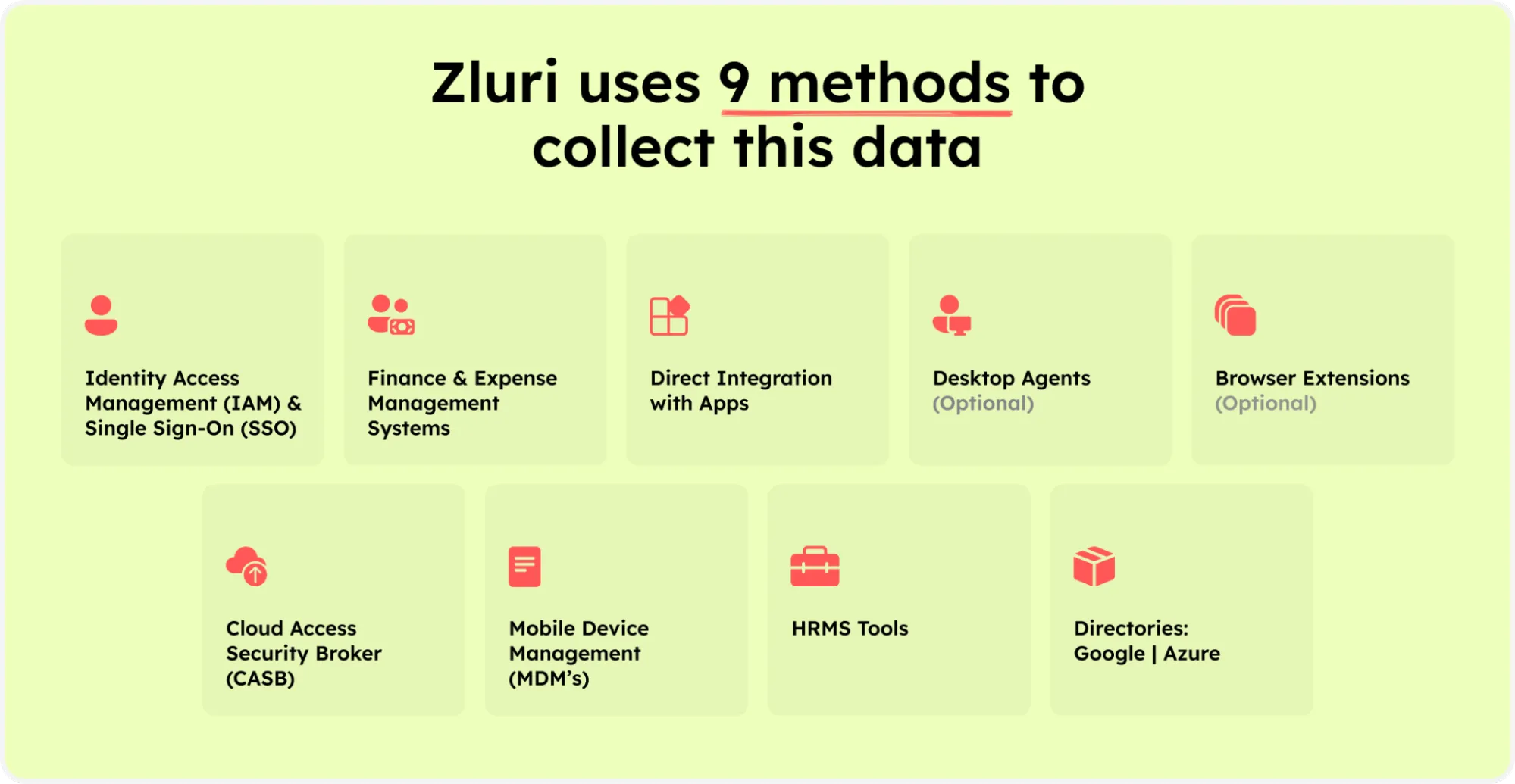
Zluri’s nine discovery methods
This capability reveals application access, active user presence, granted authorizations, and key user classifications, providing immediate and detailed insights into user access permissions.
- Automation Engine for Robust Identity & Access Governance:
Zluri's access governance is strengthened by a robust Automation Engine that oversees access workflows, ensuring accurate authorization assignments and unwavering policy compliance.
Implementing automation rules and triggers enables customized and self-sufficient access and review workflows, optimizing administrative procedures and maximizing IT management potential. This automation-centric approach streamlines access governance, making it efficient and effective.
- User Lifecycle Management with Automation:
Zluri's PAM solution streamlines the entire user lifecycle journey, from onboarding to offboarding, with unified provisioning and de-provisioning capabilities. IT teams can create and customize onboarding and offboarding workflows, ensuring users have the right resources and privileges during their tenure while seamlessly revoking access when needed.
With personalized workflows, reusable playbooks, and smart app suggestions, Zluri optimizes user lifecycle management, enhancing efficiency and security.
- Self-Serve Model for Ad-Hoc Access Requests:
Zluri empowers organizations with a self-serve ad-hoc access request management model called the Employee App Store (EAS). This innovative platform streamlines the handling of ad-hoc requests, enabling IT teams to evaluate and grant temporary access as needed while maintaining overall access control.
The Employee App Store provides a user-friendly interface, allowing employees to conveniently track the status and updates of their requests, fostering transparency and efficiency in the access management process.
- Security & Compliance Maintenance through Access Certifications:
Zluri simplifies access control and reinforces compliance through centralized user access reviews and permissions management. Its access certifications offer a comprehensive audit trail, ensuring clarity on who accesses critical resources.
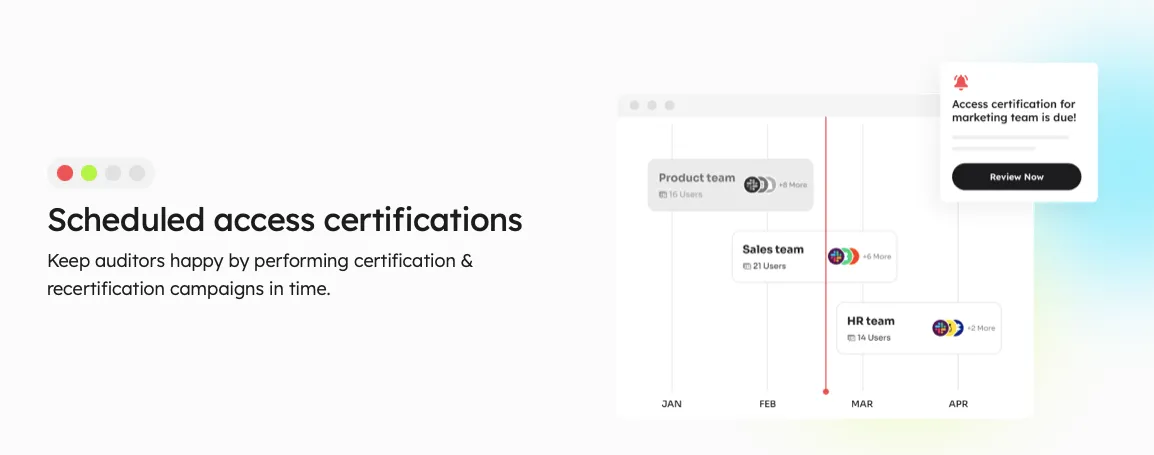
With automated access certifications, intelligent automation, auto-remediation capabilities, and real-time access reviews with anomaly detection, Zluri provides proactive security measures while aligning with industry regulations and standards. The tool's AI-powered compliance insights and industry-standard certificate templates further contribute to robust compliance efforts.
Pros
- Zluri offers a centralized and user-friendly platform for efficiently managing access to diverse applications and resources. This streamlines the administration of access rights, reducing overhead and bolstering security.
- The tool aids organizations in adhering to data protection regulations, bolstering overall security. By ensuring that only authorized individuals access sensitive data and applications, Zluri contributes to compliance and robust security practices.
Cons
- Zluri may not be optimal for smaller organizations with fewer employees. Its features are primarily tailored for large or mid-sized companies, potentially offering more functionalities than needed for smaller-scale operations.
Customer Rating
- G2: 4.9/5
- Capterra: 4.9/5
2. Okta Workforce Identity Cloud
Okta is a web-based identity management service that empowers IT teams to efficiently oversee authorization for various entities, including programs, individuals, and devices. It is one of the leading One Identity alternatives, designed to simplify and centralize user access management, ensuring a secure and seamless authentication process.
The platform includes directory services that act as a centralized repository for user information. This centralized approach enhances the accuracy and consistency of user data, simplifying the management of identities across different applications and services.
Okta workforce identity provides efficient provision and deprovision systems, allowing administrators to seamlessly grant access to new users and revoke access for those who no longer require it. This functionality streamlines the user lifecycle management process, promoting security and compliance.
It boasts built-in reporting systems that provide IT admins with comprehensive insights into user activities, access patterns, and system utilization. This feature enables proactive monitoring and analysis, enhancing security and informed decision-making.
Pros
- One of the notable pros lies in its seamless integration capabilities. It can effortlessly integrate with diverse software, enhancing interoperability and ensuring compatibility with existing IT ecosystems.
- The tool offers the advantage of serving as a viable replacement for other directory services, such as Microsoft Active Directory service. This gives organizations flexibility and the option to transition to a solution that aligns more closely with their specific requirements.
Cons
- A notable drawback is the requirement for users to change their passwords frequently. This can be perceived as a tedious process, potentially leading to user frustration and posing challenges in maintaining a smooth and efficient workflow.
- Another limitation is the dependence on IT support when changing organizational devices. This adds a layer of complexity to device management processes, requiring the involvement of IT personnel for smooth transitions and configurations.
- The tool has certain limitations in terms of identity governance use cases. It lacks functionalities such as access certification and workflows for provisioning, which are essential components for comprehensive identity governance. This limitation may impact organizations seeking a more robust governance framework for managing user identities and access rights.
Customer ratings
- G2: 4.6/ 5
- Capttera: 4.6/5
3. SailPoint Identity Platform
The SailPoint Identity Platform is a comprehensive solution for managing your users' entire lifecycles. It efficiently streamlines processes from onboarding to offboarding and everything in between.
Within this platform, you can seamlessly grant and revoke access, oversee password management, and manage user privileges, all through a centralized interface. Eliminating the need for multiple tools and manual processes conserves valuable time and resources.
SailPoint establishes a robust framework for safeguarding your organization's sensitive data. It ensures that users have only the necessary access, reducing exposure to potential security risks. Furthermore, the platform aids in detecting and mitigating any unusual or suspicious activity, enhancing your company's defense against insider threats.
Pros
- A standout pro is its user-friendly interface, which provides a seamless means to manage access to crucial resources and ensures a smooth user experience throughout its organizational lifecycle.
- SailPoint empowers your team with complete control over the backend code, a potent feature. This capability allows for effortless manipulation of workflows and rules, enabling customization of the tool to meet your organization's specific requirements.
Cons
- One notable drawback is frequent bugs and cache problems associated with SailPoint Identity. These issues can potentially impede system performance, causing disruptions in day-to-day operations.
- Moreover, the installation process for SailPoint Identity can be a significant challenge. Described as complex and challenging to navigate, especially for individuals lacking extensive technical expertise, it can present a barrier to seamless implementation.
Customer rating
- G2: 4.4/5
- Capterra: 4.1/5
4. AuthO
Auth0 stands as one of the best One Identity alternatives, providing a robust identity and access management solution committed to ensuring secure application access for organizations. With a paramount focus on user data privacy and security, Auth0 allows users to concentrate on tasks, ultimately boosting overall productivity.
Auth0 streamlines the authentication process through various features such as unified login, single sign-on, multi-factor authentication, two-factor authentication, and more. These capabilities simplify access management and enhance the security of user interactions with applications, positioning Auth0 as a compelling choice in identity and access management.
Pros
- Auth0 simplifies the tasks of searching, updating, and managing access information for diverse users, streamlining administrative processes, and improving overall efficiency.
- Additionally, Auth0 provides data source connectors that enable seamless connections with both on-premises and IAM cloud providers. This flexibility enhances the integration and management of user data.
Cons
- Users might face difficulties changing their email addresses, potentially resulting in user experience issues and increased support requests.
- Auth0's primary emphasis on cloud-based identity solutions may not align well with organizations heavily dependent on on-premises applications and systems, posing a potential drawback for such entities.
Customer ratings
- G2: 4.3/5
- Capterra: 4.6/5
5. Microsoft Azure AD
Microsoft Azure Active Directory (Azure AD), one of the notable One Identity alternatives, enables seamless access to internal and external resources. Users can effortlessly reach internal apps on the corporate intranet and organization-specific cloud apps. Additionally, it grants access to external resources like Microsoft 365, the Azure portal, and a myriad of other SaaS apps.
Azure AD simplifies the user experience through single sign-on (SSO), eliminating the need for repetitive password entries to access cloud apps. Once authenticated, this integration ensures users can access all relevant apps without repeated logins. The system generates tokens through Azure AD, which are securely stored on employees' devices. Moreover, it supports multi-factor authentication (MFA) for enhanced security when accessing critical company resources.
Pros
- The tool provides secure conditional access, incorporating multiple authentication factors and policy access. This robust security framework enhances protection against unauthorized access and potential threats.
- Users benefit from a seamless experience through features like single sign-on and password-free access. These functionalities contribute to a smoother authentication process, reducing friction for end-users.
- The tool offers a centralized identity management system that seamlessly links all internal or external users to any service or device. This centralization streamlines user access, promoting efficiency and comprehensive control over identity management.
Cons
- The tool's emphasis on manual management over automated processes can make additional tasks burdensome and tedious. The lack of automation may contribute to a less streamlined and more time-consuming workflow.
- In terms of cost-effectiveness, the tool falls short when compared to many other solutions in the market. This could pose a challenge for organizations seeking more budget-friendly alternatives, impacting the overall cost efficiency of adopting the tool.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
6. CyberArk Identity
The CyberArk Workforce Identity platform is an advanced solution and one of the prominent One Identity alternatives streamlines and fortify user access across an organization's diverse application landscape, encompassing cloud-based, mobile, and legacy platforms. It ensures a seamless and highly secure user sign-in and sign-out experience, particularly emphasizing efficacy during user onboarding and offboarding processes. The platform takes into consideration various risk factors to bolster overall security.
Adding an extra layer of security, the CyberArk adaptive multi-factor authentication plays a pivotal role in safeguarding systems. Mandating users to provide diverse authentication methods before accessing applications acts as a robust defense against cyberattacks targeting compromised credentials.
What distinguishes CyberArk as one of the best one-identity alternatives is its robust AI capabilities, introducing personalized authentication experiences for individual users. This innovative feature strengthens security and enhances user convenience and experience by tailoring authentication methods to each user's unique needs and preferences.
Pros
- CyberArk Workforce Identity presents a range of capabilities, encompassing server access management and role-based authentication, rendering it flexible to accommodate diverse organizational needs.
- Users experience the advantages of Single Sign-On (SSO) features, streamlining credential management and elevating user convenience.
Cons
- CyberArk Identity's smartphone permissions, while useful, can prompt privacy concerns, as they may raise potential privacy issues. The limitation of lacking granular permission controls could expose sensitive data.
- The tool's drawback includes a lack of support for SAML response encryption. This deficiency in enhanced encryption measures jeopardizes the security of sensitive data during authentication processes and data exchanges.
Customer ratings
- G2: 4.4/5
- Capterra: 4.2/5
7. Omada Identity

Omada Identity serves as an extensive solution for identity and access management, specifically crafted to overcome prevailing challenges. It enables your team to adeptly handle user identities and roles and access privileges throughout the organization.
Simplifying identity management and access control, Omada Identity liberates your team from the intricacies of user access, allowing them to concentrate on strategic initiatives. The platform streamlines administrative tasks, minimizing the risk of errors through its centralized and user-friendly interface.
Pros
- The platform facilitates seamless and prompt access enablement, streamlining the process of granting and managing user access. This ensures efficient and secure control over access permissions, reducing the risk of unauthorized data breaches.
- Omada Identity stands out for its integration of various tools, enhancing user-friendliness for your team. The consolidated tools and features make monitoring and controlling user access, tracking user activities, and enforcing security protocols convenient.
- Adjusting user permissions and access levels is effortless with Omada Identity. This ease of modification enables the IT department to adapt swiftly to evolving organizational needs without unnecessary complexity or downtime.
Cons
- The initial setup of Omada Identity may be time-consuming and somewhat challenging. This could cause frustration for your team, potentially leading to delays in essential tasks and making it more difficult to meet deadlines.
- While Omada Identity is highly secure and powerful, its functionality has room for improvement. Despite its robust security features, a more modern and user-friendly design could enhance usability. As a result, your team might spend additional time navigating or assisting others, potentially leading to inefficiencies.
Customer rating
- G2: 3.8/5
- Capterra: 4.8/5
8. ManageEngine ADManager Plus
ManageEngine ADManager Plus streamlines user access management, serving as your essential identity and access management tool. It streamlines intricate processes, reinforces security measures, and enhances operational efficiency. Bid farewell to laborious manual tasks and welcome a more seamless and productive IT environment.
This solution empowers you to allocate more time to strategic IT initiatives by minimizing administrative burdens. Additionally, ADManager Plus provides real-time alerts and notifications, enabling proactive management of changes and security events.
Pros
- ADManager Plus by ManageEngine provides a diverse set of tools to enhance your onboarding procedures, optimizing them for greater efficiency and alignment with your organization's specific requirements.
- The software facilitates the extraction of valuable insights by generating comprehensive reports. These reports are crucial in identifying your organization's security risks and compliance issues.
- ADManager Plus stands out with its user-friendly interface and dashboard, emphasizing a design centered around user convenience. This approach ensures swift implementation and management of IT processes, ultimately saving time and effort.
Cons
- A notable drawback of the tool is that specific updates have led to compatibility issues within the Active Directory environment. This situation necessitates considerable time spent on troubleshooting and seeking assistance, introducing delays to the overall IT management process.
- Additionally, a drawback arises from the predominantly manual nature of the upgrade process with ADManager Plus. This manual aspect implies that routine upgrades necessitate a more hands-on approach, demanding additional attention and effort.
Customer rating
- G2: 4.5/5
- Capterra: 4.4/5
9. JumpCloud
JumpCloud's identity management is one of the prominent One Identity alternatives that presents a robust and user-friendly approach to address these challenges, establishing itself as an indispensable tool for your IT team. It simplifies the user onboarding process, enabling a seamless setup for new team members. Utilizing its centralized platform, you can effortlessly provision users, assign roles, and grant access to the necessary resources with just a few clicks.
Similarly, JumpCloud streamlines the offboarding process, providing your team with a quick method to disable accounts and revoke access privileges. This swift action ensures the security of your systems and data, even in the transition of employees.
Moreover, JumpCloud's solution is adaptable to your organization's specific needs. Whether you operate as a small startup or a large enterprise, customization to fit your requirements is easily achievable. The solution's scalability ensures that as your organization grows, you can effortlessly expand without complications, making it a cost-effective choice.
Pros
- One of JumpCloud's standout benefits lies in its seamless control over user access and permissions. This empowers you with a potent tool to oversee and manage access within your organization's systems efficiently.
- JumpCloud facilitates the quick granting of administrative privileges to those who require them. This ensures your team can execute their tasks promptly and without unnecessary delays or complications.
Cons
- A significant downside is that the JumpCloud Agent lacks automatic updates to the latest version and lacks a manual update option. Consequently, your team must actively monitor and manage agent updates, introducing a potential inconvenience and additional workload.
- Additionally, certain aspects of JumpCloud can be somewhat perplexing during the initial setup. This initial confusion may result in a learning curve for your team, especially as they are just starting to work with JumpCloud.
Customer rating
- G2: 4.5/5
- Capterra: 4.7/5
10. Oracle Identity Management

Oracle Identity Management is one of the most advanced One Identity alternatives that govern the entire user lifecycle seamlessly across all enterprise resources, whether within the firewall, outside, or in the Cloud. It delivers scalable solutions encompassing identity governance, access management, and directory services. Operating as a fully integrated solution, it provides a Cloud enterprise platform with multiple tenants, offering core IAM features.
The platform streamlines critical processes, automating the creation, updating, and deleting user accounts, along with password management and the allocation or revocation of permissions across applications hosted in the Cloud or on-premise. The system ensures meticulous access right removal directly from the target platform or application, maintaining a comprehensive record known as closed-loop cleanup.
This robust solution supports diverse access certifications tailored to different user roles, including business managers, role owners, application owners, and entitlement owners, contributing to a versatile and efficient IAM environment. In short, Oracle identity governance enhances security measures, simplifies compliance management, and capitalizes on mobile and social access opportunities.
Pros
- Oracle Identity Management excels in providing robust Service-Oriented Architecture (SOA) workflow capabilities. This allows organizations to streamline and optimize processes, ensuring efficient management of identity-related workflows.
- It offers an extensive range of connectors, facilitating seamless integration into various business platforms. This includes integrating mainframes, AS400, LDAPS, databases, and more. The diverse connector support enhances the platform's versatility, enabling organizations to connect with a wide array of systems.
Cons
- The setup process of Oracle identity governance can be challenging for some users. The complexity involved in the initial configuration may pose difficulties, requiring careful consideration and expertise during implementation.
- While Oracle Identity Management offers a comprehensive set of features, it has a limitation in terms of reporting options within the admin portal. Users may find the reporting capabilities somewhat restricted, impacting their ability to generate in-depth analytical insights directly from the admin interface.
Customer Rating
- G2: 3.7/5
- Capterra: 4.4/5
11. Ping Identity
Ping Identity offers a strong identity and access management platform, enhancing security and streamlining access to networks, APIs, cloud applications, and on-premises software for businesses. The platform proactively detects and addresses suspicious activities with advanced AI technology while ensuring compliance with industry regulations. This versatile tool enables organizations to establish comprehensive access policies, fostering seamless integration, synchronization, and centralized data management from various sources.
Pros
- Ping Identity provides a user-friendly self-service portal featuring a streamlined interface, ensuring effortless registration and authentication requests. This enhances the onboarding process and boosts user productivity by simplifying essential tasks.
- The platform facilitates easy assignment and updating of resource ownership information. This capability enhances control and transparency in resource allocation across the organization, contributing to efficient management practices.
Cons
- The tool exhibits limited adaptability in directly integrating custom attributes, which may present challenges for organizations aiming for personalized customizations. This limitation could hinder the implementation of specific and tailored features.
- While Ping Identity provides robust deployment options, it lags slightly behind certain competitors in offering highly specialized deployment choices. Businesses with specific and advanced deployment requirements might find more suitable alternatives elsewhere, impacting their ability to tailor deployment strategies to precise needs.
Customer ratings
- G2: 4.4/5
- Capterra: 4.8/5
FAQS
1. Why should I consider One Identity alternatives?
While One Identity is a robust solution, organizations may explore alternatives due to factors such as pricing, specific feature requirements, or compatibility with existing infrastructure. This blog delves into various alternatives, providing insights to help you make an informed decision.
2. How do I determine the right alternative for my organization?
The blog outlines key considerations: functional fit, scalability, integration capabilities, user interface, cost, security features, vendor reputation, and compliance. By evaluating these factors, you can identify suitable identity alternatives that align with your organization's unique identity security requirements and operational needs.
3. What are the top features to look for in One Identity alternatives?
The blog highlights features such as scalability, seamless integration, user-friendly interface, cost-effectiveness, robust security features, and compliance. Understanding these features will guide you in selecting an alternative that addresses the drawbacks of One Identity and enhances your identity security framework.
4. How can I ensure a smooth transition to a new identity management solution?
Transitioning to a new solution requires careful planning. The blog suggests factors to consider during the selection process, emphasizing the importance of assessing compatibility, scalability, and ease of integration. Additionally, it provides insights into potential challenges and considerations for a successful implementation.









.svg)














