IT compliance audits play a critical role in safeguarding system integrity and security. They're proactive measures ensuring an organization's IT practices meet regulatory standards, industry best practices, and internal policies. These audits confirm compliance and pinpoint vulnerabilities, potential risks, and areas needing improvement within the IT infrastructure.
In a rapidly changing regulatory environment, maintaining a robust IT infrastructure is paramount to the success of any organization. For this reason, an IT compliance audit is required. Compliance audit is not just a box to check; it's a shield that protects your organization from legal repercussions and financial penalties.
By conducting regular audits, you demonstrate due diligence, mitigate non-compliance risk, strengthen your security policies, and showcase your commitment to best practices. Let's know more about this.
What is an IT Compliance Audit?
An IT compliance audit independently assesses an organization's cybersecurity tools, practices, and policies. This evaluation ensures adherence to specific requirements, compliance regulations, and laws established by certification bodies or organizations setting the standards.
The primary objective is to verify that an organization's IT practices align with established frameworks, effectively safeguard sensitive data, and mitigate risks. These audits are especially critical in industries prioritizing data privacy and confidentiality.
Organizations typically engage with relevant IT compliance auditing bodies to initiate an audit, pay for the audit, and furnish the necessary information for evaluation. Moreover, most compliance certifications have expiration dates, necessitating periodic reevaluation to reaffirm an organization's adherence to compliance protocols.
For instance, a financial institution handling significant amounts of sensitive customer data regularly undergoes IT compliance audits. These audits assess facets like data encryption, access controls, and disaster recovery plans. The institution ensures compliance with data protection laws by conducting these audits, thereby fortifying customer trust and meeting legal obligations.
Internal Audit vs. External Audit
Understanding the distinctions between internal and external audits is crucial, especially within the realm of IT compliance auditing:
Internal Audit:
- Conducted by an organization's internal team, typically led by an internal audit department.
- Primarily evaluates and enhances internal processes, controls, and risk management strategies.
- For instance, in IT, internal audits might involve reviewing network security protocols, assessing the efficacy of user access controls, and ensuring adherence to internal IT policies.
- Aims to improve operational efficiency and mitigate risks by establishing robust internal controls.
External Audit:
- Conducted by independent third-party auditors hired from outside the organization.
- Focuses on providing an unbiased assessment of the company's adherence to external standards, regulations, and industry best practices.
- External auditors might assess the organization's compliance with cybersecurity frameworks and data protection laws in IT compliance.
- Offers an external perspective and validates compliance status to stakeholders, clients, and regulatory bodies, providing credibility and assurance.
The internal audit concentrates on optimizing internal processes and controls, while the external audit ensures adherence to external standards and regulatory requirements, providing an independent validation of compliance to external entities. Both audits are essential components of a comprehensive compliance strategy.
Types of Internal Audit
Internal audits encompass various types, each with its distinct focus and objectives:
1. Operational Audits:
- Aim to assess and enhance the efficiency of day-to-day processes within an organization.
- Examples include evaluating software development processes, IT service delivery mechanisms, and incident management procedures.
- Identify areas for improvement to streamline IT operations and boost overall effectiveness.
2. Compliance Audits:
- Target adherence to industry regulations, legal standards, and internal policies.
- Ensures that IT practices align with relevant standards, minimizing non-compliance risk and potential legal issues.
- Helps navigate the complex web of compliance requirements and ensures alignment with necessary standards.
3. Information Systems Audits:
- Specifically, scrutinize the organization's IT infrastructure.
- Assess the security of data, information systems' effectiveness, and cybersecurity measures' resilience.
- Identify vulnerabilities and ensure the security of sensitive data and IT systems.
4. Financial Audits:
- While typically associated with accounting, they also hold significance in the IT context.
- Involves scrutinizing budget allocations, project costs, and IT investment returns.
- Offers insights into the financial health of the IT department, enabling informed decision-making based on audit findings.
Each type of internal audit plays a crucial role in evaluating and improving different aspects of an organization's operations, ensuring efficiency, compliance, security, and financial health across the IT landscape.
Reasons Why You Need to Perform An IT Compliance Audit

The several reasons for which you need to perform IT audit compliance are mentioned below.
- Customers need a clean sheet
Your customers care about their data and want the vendors to follow the standards or protocols to secure their information.
So, passing a compliance audit is assuring that your company is compliant and taking all the measures to prevent data breaches.
A report from an independent auditing body assures customers that their personal information and data are secure and safe in your company. It gives them the freedom to share data without worrying about any breaches.

- It is mandatory to follow your industry-specific laws and compliance regulations
If your organization is collecting personal information, following the local norms regarding consumer data is essential.
For example, GDPR has a specific view on what constitutes personal data, so the companies need the same level of protection about an individual's IP address or cookie data as they do for name, address, and phone numbers.

- You will have a competitive advantage
Plenty of vendors are in the market, and for your clients to select you over them, you need to provide surety that they don't provide. According to a cybersecurity report by CISCO, 53% of respondents strongly agree with regularly improving security practices.
Even if you are a startup with just a couple of employees, doing an IT compliance audit can give you a competitive edge and make you the first choice among similar startups that haven't done an audit yet.
- You can get attested by your auditors
For example, suppose you are carrying out an audit from a public accounting firm registered with the Public Company Accounting Oversight Board (PCAOB) in the USA. In that case, your customers can be assured that your auditor will conduct the strictest of auditing process and standards.
If you have any publicly held customers, this audit carried over by a PCAOB CPA firm can give their auditors the assurance they need while relying on your audit report.

- Stay protected from cyber attacks
Billions of records have been compromised in cyber attacks. Since all companies collect data in some form today, they can be targets for attackers. A compliance audit helps you and your customers from data breaches.
While conducting an audit, you can learn more about cybersecurity norms, IT compliance, and what it means to your organization.
While preparing for an audit, you understand and establish the controls more accurately and prepare your organization for future audits.
5 Major IT Compliance Regulatory Frameworks

Even though you may be new to audits, it's important to have wide knowledge about the existing regulatory compliance and what it means.
Here is a list of the most common types of IT compliance audits you may need for your organization.
1. HIPAA (Health Insurance Portability and Accountability Act of 1996)
The Health Insurance Portability and Accountability Act was passed in 1996 to protect sensitive patient health information from being disclosed without the patient's consent or knowledge.
HIPAA covers the following businesses:
- Health insurers
- Healthcare cleaning services
- Any healthcare provider who stores health information
If you fall into any of these business types, you must ensure the data is secured and managed correctly. Health data should be physically and technically secured with administrative safeguards.
If there is a breach, you can be fined millions of dollars depending on the negligence. A HIPAA audit can also assure patients that their information is secure and confidential.
2. PCI-DSS (Payment Card Industry Data Security Standard)
PCI compliance is a set of regulations that ensure that all companies that accept, process, store, or transmit credit card data maintain a secure environment to protect it.
Before 2006, there was no clear industry standard for credit card companies, which was a problem for companies that deal with big data because they had to follow different standards.
The DSS component of this audit is a set of regulations to which anyone who has to follow PCI compliance is subject.
In 2006, Visa, MasterCard, Discover, JCB International, and American Express (AMEX) came up with the PCI Security Standards Council (PCI SSS) to help regulate the credit card industry and establish clear operating guidelines for how consumer credit card information should be handled.
These standards apply to any organization working towards processing payment cards or creating the infrastructure to process payments.
To ensure your organization remains compliant, you must:
- Evaluate your business processes to identify any security gaps that could lead to a data breach.
- Do not store any sensitive information about your customers.
If your company is found non-compliant with these rules, you could receive a monthly fine of up to $100,000.
3. SOC 2 (Systems and Organizational Controls)
SOC 2 is a compliance audit defined by the and is an accepted standard of current technology companies. Its main focus is being able to store customer data, and it applies to service providers who use the cloud. These companies are required to be SOC 2 compliant due to their strict policies and procedures.
To get SOC 2 compliance, most companies spend six months to a year doing things like assessing their policies and procedures and implementing new security controls. Its first and foremost priorities are security, confidentiality, privacy, availability, and data integrity.
There are two SOC 2 audits. SOC 2 Type I checks that vendor's systems are properly designed, and SOC 2 Type II checks for the effectiveness of vendors' operating systems. These typically last for six months the first time around.
4. ISO (International Organization of Standardization)
The ISO compliance audit is part of the ISO/IEC 27K Series and is an information security compliance standard. This standard helps companies manage and develop high protection for their critical data, such as employee or third-party data, financial information, and intellectual property.
Both the SOC 2 and the ISO 27001 certifications are risk management processes that involve people, processes, and technology. The certification requires an independent auditor to assess the company's security controls and ensure the risks are appropriately mitigated.
ISO works to promote standards that align with the business practices of over 160 countries. This helps to resolve any disagreement between businesses in the same industry.
One thing to remember about ISO is there's a difference between being compliant and being certified. You can choose to be compliant without going through an audit, but if you want certification, you'll need to go through a long process.
In order to meet ISO standards, you'll need to do a longer external audit by a third party. This is voluntary, but if you get certified, there are benefits regarding customer trust and satisfaction.
5. GDPR (General Data Protection Regulation)
The EU's GDPR is one of the most comprehensive government-imposed data privacy frameworks implemented to date. It went into effect in May 2018 and is meant to protect the data privacy of EU citizens. However, this regulation doesn't just apply to European companies; it's for anyone who processes European citizens' data.
Today, GDPR auditing is mainly self-driven and follows a four-step process:
Planning: This plan will be systematic and methodical. It will follow the law's requirements to outline all key processes and improvements.
- Gap analysis: Locate any gaps in your company's processes
- Remedy gaps: Prioritise and rank the three key areas based on their associated risk level.
- Test new processes: After the remediation is complete, assess the efficiency of new processes that were put into place.
Like HIPAA violations, a GDPR violation can come with a hefty fine. If you're in breach of these regulations, companies can be fined 4% of their global revenue or 20 million euros, whichever is the higher figure. In addition, the data subjects have the right to seek compensation for damages.
If your company deals with the processing of EU citizen's data, whether that's in the context of an identifiable citizen or resident, a company that gives or processes data to EU citizens or residents, or a company that operates in the EU, then it's likely going to need to be GDPR compliant.
How to Pass Compliance Audit Process?
The compliance audit checklist to pass the process is mentioned below.
Compile IT regulations: First, you need to figure out which standards you must comply with. Pay close attention to the obligatory and the non-obligatory regulations, as both of them can benefit your company.
Getting an ISO 27001 implementation is not mandatory, but there is a growing demand among customers for this certification every year.
Appoint Data Protection Officer: You should appoint a data protection officer who will monitor all the protection measures you have implemented in your organization, studies what are the security requirements you need, and is responsible for implementing them. The GDPR and PCI DSS require organizations to appoint employees to maintain compliance.
Carryover risk assessment: A risk assessment systematically examines and analyzes potential dangers, threats, or risks. The potential consequences and the likelihood that they will concern you are assessed. During a risk assessment, it's important to identify:
- Cybersecurity risks and threats to your organization
- Assets that are important to your organization that are subjected to compliance
- The current level of protection and strength & weaknesses your systems have
A risk assessment helps you map the state of your cybersecurity and puts a number on the risks, allowing you to analyze how they may harm your organization. Thus, it should be repeated periodically.
The results from a risk assessment will be useful for planning security improvements as well as for designing new policies and strategies.
Conduct an internal self-audit regularly: A self-audit is an assessment of the security of your implemented controls. It won't tell you how good your security is, but it will show any gaps in compliance. A self-audit is also useful for preparing your employees for an actual IT audit.
Use an official IT compliance audit checklist and guidelines to conduct a self-audit and make it look more like a real audit.
One large downside to self-audits is the high cost, both in terms of money and time. However, the cost of discovering gaps in cybersecurity during an audit is even higher: failing the audit and starting over.
Implement the lacking controls: As a result of our self-audit, you found the policies, practices, and technical controls we need to implement to pass out IT audits. Now, it's time to take action and implement them.
Most regulations, standards, and laws require you to implement tools such as identity management, access control, user activity monitoring, and breach notification.
Implement an IT audit trail: A complete IT audit trail means you have a full record of all the activities involving sensitive data, your databases, or any other part of your infrastructure. Then, when it is time to do a compliance and security audit, the IT auditor will be able to examine how your employees handle these sensitive resources, which is an essential component of any compliance and security audit.
Logging an audit trail can generate a lot of data, but this is useful for security monitoring and incident investigation. The generated logs identify any security incidents and identify the threat source.
Ensure you have a user activity monitoring system in place that records all user actions and stores them in a secure system. Monitoring records are helpful during forensic investigation activities.
Create a long-term compliance strategy: A compliance audit is a process that ensures your organization stays compliant. That's why creating a compliance strategy is essential — a set of internal policies and procedures that will help you stay on the right side of the law.
It is important to make a plan that considers the workflow of all the different departments affected by this. For this reason, you should work closely with the leaders of each department to hear their input and suggestions.
Once your compliance strategy is complete, assigning people responsible for its implementation is important. Sometimes, this work is managed by a data protection officer or chief security information officer.
Automate all the compliance-related information: To achieve compliance, some tasks must be done manually: reviewing policies and investigating security incidents. Automating the process can reduce compliance overhead, save time for audit preparation, and minimize the risk of errors.
Automation benefits large organizations that must pass several IT compliance audits annually.
Raise awareness about compliance among employees: When an audit is required, it often means employees have to change the way they work. This can be difficult, but they must understand their responsibilities and practices.
To help employees understand their role in the audit process, you can:
- Explain how data leaks and failed audits can impact your organization
- Share news on security breaches in your industry
- Conduct cybersecurity training
- Communicate the importance of new security controls
- Describe the outcome of non-compliance.
Your objective here is to undertake a cybersecurity audit and create an awareness of the importance of this.
Zluri Makes You Audit Ready
The task of granting special access privileges to employees has become more accessible. However, the complexity of managing and controlling these privileges has grown, posing significant security risks and compliance challenges.
Enter Zluri's access management solution that offers user access review capability. This transforms how you handle access, providing a robust platform for streamlining IT audits, ensuring compliance, and effectively controlling user access.
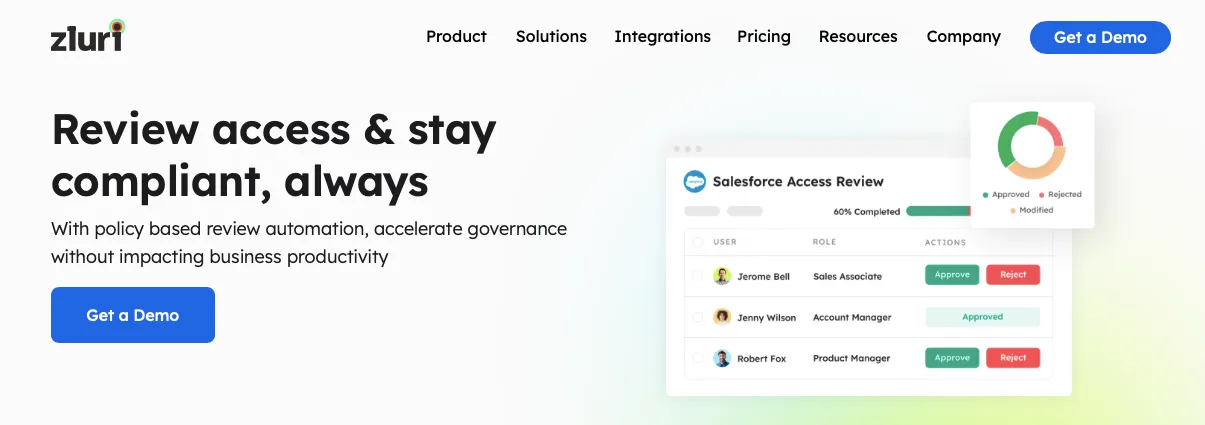
Comprehensive Visibility into SaaS Landscape
Zluri employs nine discovery methods and integrates with over 300 applications, offering 100% visibility into your SaaS landscape. This comprehensive view lets your IT team identify all SaaS applications through a centralized platform, ensuring complete visibility into your organization's SaaS ecosystem.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Unified Access for Enhanced Security
Zluri's unified access solution simplifies the complex task of monitoring user access across different systems and applications. This feature enhances your organization's security, boosts operational efficiency, and ensures compliance with regulations.
- Access Directory: Zluri provides centralized control over access permissions, offering a clear and comprehensive view of who has access to specific resources and applications. This visibility is vital for maintaining a secure environment and adhering to financial standards.
- Access Privileges: Zluri makes defining and monitoring access privileges easy based on user roles, departments, and other relevant information. This level of control ensures that each user has access only to the resources necessary for their specific tasks, reducing the risk of data breaches and maintaining compliance.
- Activity & Alerts: Zluri offers real-time insights into user activity, allowing you to monitor user behavior and identify potential security threats. The proactive alerting system notifies you of any unusual activities or security breaches, empowering you to take swift action and maintain compliance.
Automated Reviews for Effortless Compliance
Zluri's automated access review capabilities are crucial in enhancing your access control system and ensuring compliance with regulatory requirements.
- Access Rules: Zluri's access insights form the basis for creating precise access rules, allowing you to establish strict access controls for sensitive financial information. This ensures compliance with financial standards and reduces the risk of data breaches.
- Scheduled Certification: Zluri streamlines the certification process by allowing you to schedule certifications in advance. This proactive approach ensures that employees' access aligns with the organization's policies and regulatory requirements, keeping access permissions up-to-date and compliant.
- Auto-remediation: Zluri introduces auto-remediation capabilities, actively responding to access violations. This feature automatically triggers corrective actions for immediate resolution in the event of unauthorized access or security breaches, enhancing your organization's security and maintaining compliance with industry standards.
FAQs
What is a compliance audit?
A compliance audit is an impartial assessment designed to verify an organization's adherence to external legal requirements, regulations, statutes, or internal protocols, including corporate bylaws, controls, and established policies and procedures.
What is a compliance audit example?
Consider a compliance audit scenario involving a national bank. In this case, the audit would focus on evaluating the bank's adherence to industry benchmarks related to privacy, financial transactions, and other crucial areas in accordance with governmental regulations.
What is audit compliance testing?
Compliance testing involves auditing to ensure alignment with policies, rules, or regulations. Within the auditing realm, compliance testing is the method employed to assess controls pertaining to regulatory risk. It is frequently the initial testing phase when evaluating the overall control environment.
What is the audit compliance procedure?
Compliance procedures encompass a set of carefully orchestrated activities to accomplish a defined objective. The primary purpose of these procedures is to guarantee the organization's alignment with pertinent laws, regulations, and standards. By providing a more explicit and structured approach to implementation, these procedures effectively support and enable the execution of policies.
What are the advantages of compliance audits?
Optimizing organizational efficiency within the business landscape. Safeguarding stakeholder trust. Adhering to additional regulations, including environmental and consumer safety laws. Upholding standardized operating procedures across the entire organization.







.png)

.svg)














