Cloud security posture management is vital in empowering IT teams to control their cloud infrastructure and reduce security threats. It achieves this by providing visibility into cloud environments and alerting against compliance risks and misconfigurations. Lacework is a cloud security posture management (CSPM) tool that helps IT teams identify cloud configuration issues and compliance risks.
While Lacework is a capable cloud security platform, it has limitations. Hence, it's crucial to explore other Lacework alternatives to ensure your organization's cloud security requirements are addressed.
Lacework handles cloud security by identifying, analyzing, and reporting any unusual cloud activities or patterns that can risk the organization's cloud security. It tracks down the cloud behavior abnormalities and provides complete information about it, like why specific native attacks or abnormalities happened.
Lacework is a capable cloud security posture management tool; however, if you prefer a user-friendly option with minimal learning requirements, it might not be the best choice.
This article discusses 8 Lacework alternatives you may consider while evaluating cloud security posture management tools. But before that, let’s learn more about Lacework and its drawbacks.
Lacework Cloud Security: An Overview
Lacework's Cloud Security Posture Management empowers organizations by providing comprehensive visibility into their cloud infrastructure. It maintains constant vigilance, tracking all cloud interactions to proactively mitigate risks and ensure compliance with industry standards. It sends instant notifications when configurations fall short of compliance.
Lacework offers the capability to manage multi-cloud environments seamlessly, breaking down silos and eliminating blind spots. It facilitates an agentless approach for a comprehensive cloud account asset inventory. It provides valuable recommendations for addressing non-compliant resources.
Lacework serves as a unified platform encompassing AWS, Google Cloud, Azure, and Kubernetes configurations. Additionally, it offers seamless integrations with tools such as Jira and Slack, to expedite the remediation process.
Drawbacks of Lacework
Let's explore the disadvantages of Lacework in more detail before delving into Lacework alternatives:
- Inability to Operate on Local On-Premises Networks: Lacework's limitation in running on local on-premises networks can be a significant drawback for organizations that require security monitoring and continuous compliance enforcement for both their cloud and on-premises environments. This limitation can lead to a fragmented security approach, making it challenging to maintain consistent security policies across all infrastructure components.
- Limited Operating System Support, Especially for Windows: The insufficient support for various operating systems, particularly Windows, can pose a problem for organizations with diverse IT environments. This limitation may force them to seek alternative solutions or invest additional resources in addressing security gaps, which can be costly and time-consuming.
- Steep Learning Curve Due to Complex User Interface (UI): The complex nature of Lacework's user interface can be a hindrance, especially for newcomers or less experienced users. This steep learning curve may delay effectively implementing and managing security measures, potentially leaving the organization vulnerable during the initial learning phase.
- Delays in Alerting, Potentially Resulting in Missed Actions: The possibility of delays in receiving alerts from Lacework is a critical concern. In cybersecurity, timely responses are essential. Delays in alerting can result in missed opportunities to mitigate security threats, exposing the organization to risks and potential security breaches.
For IT teams evaluating Lacework alternatives, it is crucial to carefully balance these drawbacks against the strengths of competing solutions and to thoroughly evaluate whether the platform aligns with their unique security and operational needs.
Customer Rating
- G2: 4.5/5
- Capterra: 5/5
Before we dive into the Lacework alternatives, let us take a moment to introduce ourselves and highlight how Zluri can contribute to enhancing the security of your SaaS infrastructure.
Elevate Your SaaS App Security & Management with Zluri
Zluri facilitates comprehensive management of your organization's entire suite of SaaS applications. Leveraging our platform, you can swiftly pinpoint, monitor, and oversee the full SaaS stack utilized throughout your organization, thanks to our sophisticated discovery methods.
The platform uses five advanced discovery methods to ensure 100% coverage of all SaaS apps in use. Once identified, Zluri offers a range of security and compliance information solutions to ensure that your organization meets every compliance requirement.

Our platform allows you to access event and statistic tracking capabilities, shared data, and security & compliance assessments tailored for SaaS applications. This approach allows you to work towards achieving compliance objectives while concurrently advancing your security objectives.
- Events: Zluri actively monitors and aggregates news pertaining to your applications during their usage. Our platform collects this information from the web and presents it in the Events Tab. Examples include updates on ransomware, data breaches, patches, or security vulnerabilities.The risk score assigned to each app is based on event analysis. For instance, apps with a greater frequency of events will receive a lower risk score.
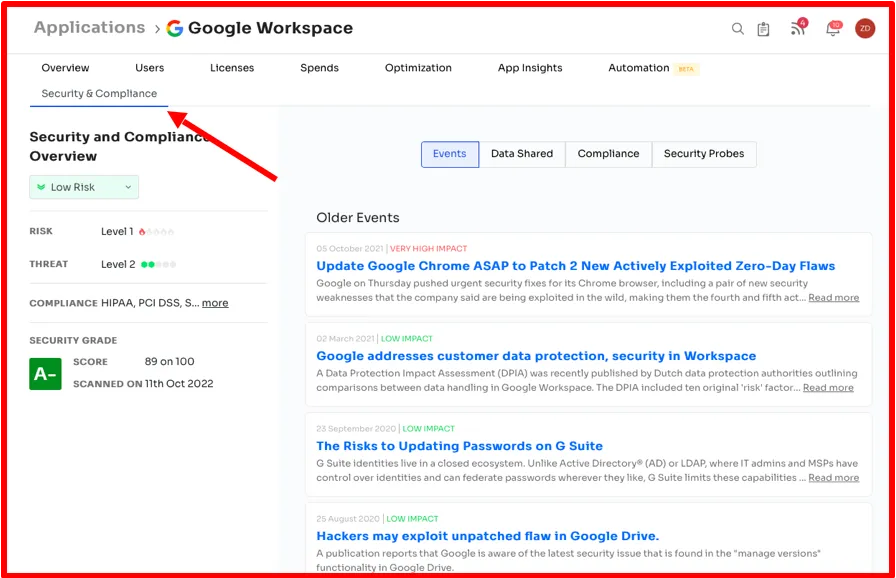
- Data Shared: When you link one app to others, those connected apps gain access to the content within the linked app. This access can take various forms, such as read, write, modify, or delete permissions. The greater the sensitivity of the data accessible to the app, the higher the associated threat level.
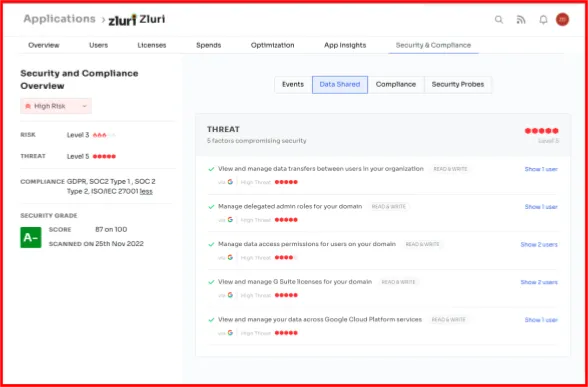
- For instance, if an app can access Google Drive and possesses the capability to modify or delete files within the drive, it is assigned a high threat level.
- Compliance: Zluri provides comprehensive compliance details for each app, indicating the specific compliance frameworks with which the app aligns. The risk score for the app increases with a greater number of compliant frameworks it adheres to.
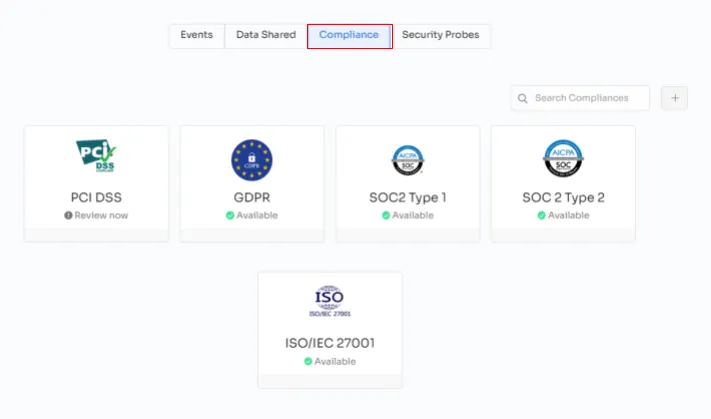
- Security Probes: This feature offers a glimpse into the technical scanning process, which occurs on a monthly basis. However, the scanning frequency can be tailored to suit the organization's specific needs and preferences.
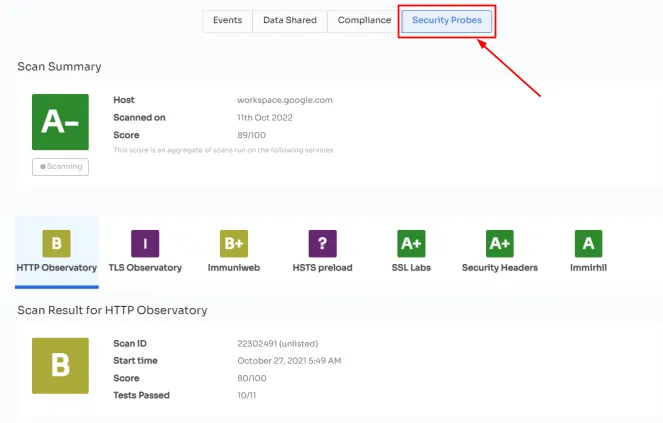
- Additionally, as per Kuppingercole's research and analysis report Zluri employs robust encryption algorithms to safeguard the confidentiality of sensitive data. Our platform offers a comprehensive, auditable log of crucial activities, allowing you to monitor all app security-related actions effectively.All collected data, including metrics on SaaS app usage, is retained indefinitely, unless a specific request for removal is submitted. Zluri stores all data in a secure, encrypted state and maintains backups for a duration of 60 days.
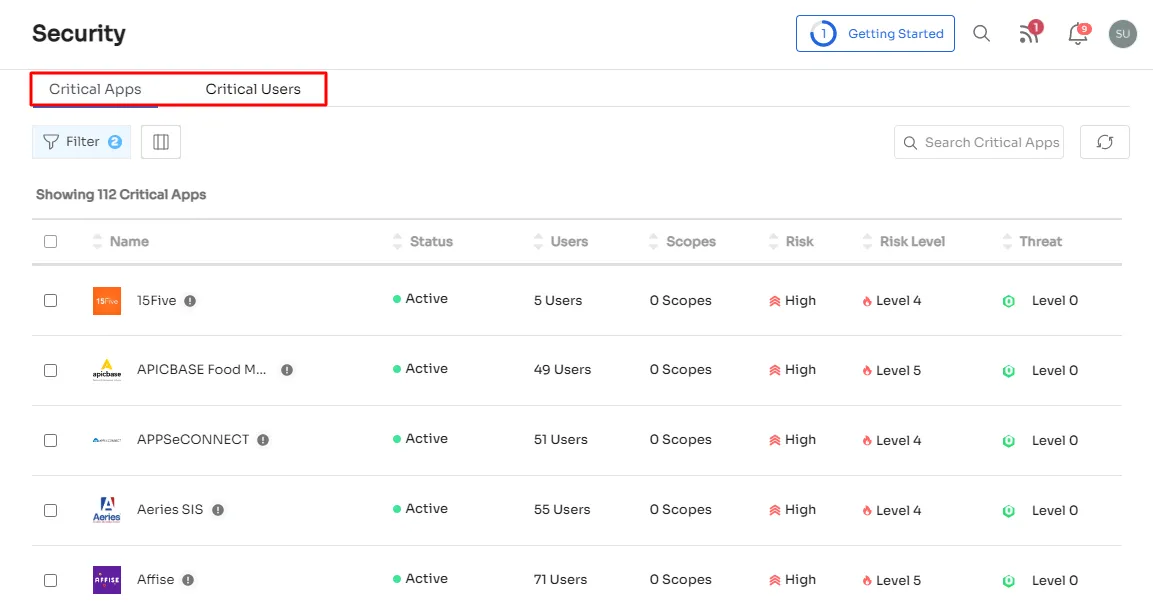
- Furthermore, Zluri provides a clear overview of critical apps with elevated threat levels and risk scores. Our platform issues alerts to users, cautioning against the use of critical apps that could compromise data confidentiality and protect against cyber threats.Beyond its security features, Zluri delivers additional valuable advantages for efficient SaaS app management. Let's delve into these benefits.
- SaaS License Management Made Easy: Zluri simplifies tracking, identifying, and reporting SaaS licenses by automating these tasks. Get a 360-degree view of all licenses, monitor usage, identify redundancies, and enhance security.
- Comprehensive Renewal Control: Stay on top of renewals with Zluri's Renewal Calendar. Receive automatic alerts and prioritize critical renewals to avoid interruptions.
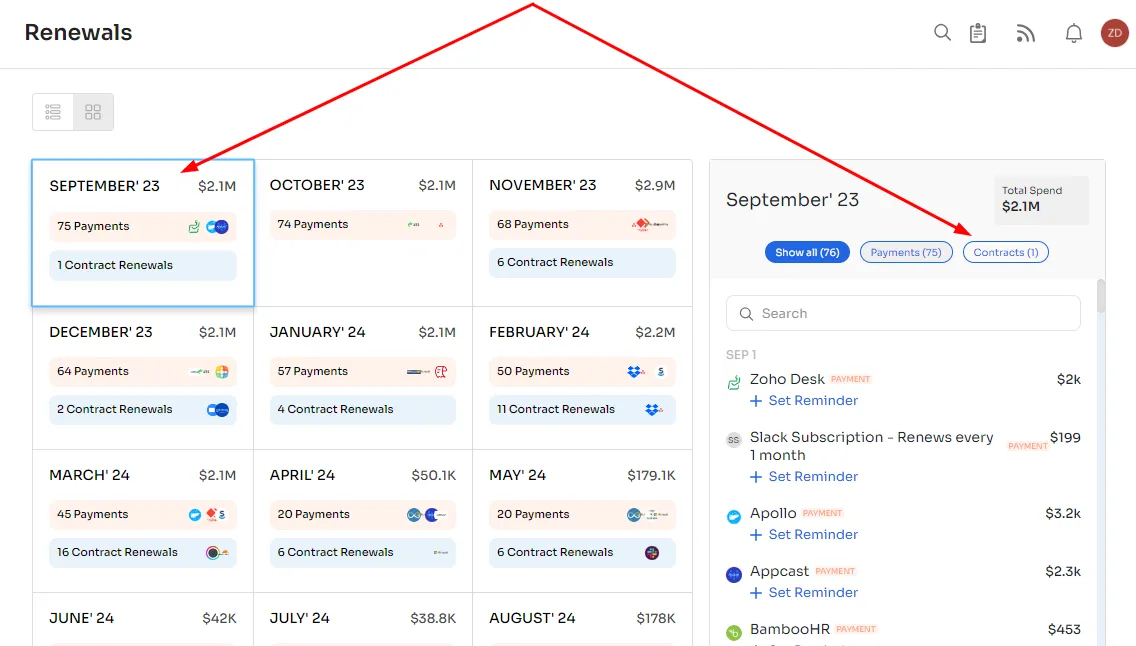
- Cost Savings: Detect and eliminate unnecessary duplicates to save costs. Optimize your SaaS applications and gain insights into usage patterns.
- Vendor Management: Zluri offers complete vendor management, improving visibility and control over your tech stack. Seamlessly integrate with core systems for a comprehensive SaaS system of record.
If you want to enhance your SaaS infrastructure's security, schedule a demo with Zluri!
List Of Top 8 Lacework Alternatives
In this updated list, we present the top 8 Lacework alternatives, each offering its own set of features and advantages to safeguard your cloud infrastructure
1. Threat Stack
Threat Stack is a cloud security monitoring and analytics software that helps IT teams protect their business from cloud risks. It sends alerts of any unusual activities in your cloud-native applications and helps to detect threats and prevent breaches.
Threat Stack helps organizations observe the security and compliance across the entire cloud infrastructure and application stack. It provides built-in and configurable rules to detect and alert security and compliance risks.
Pros
- The system operates consistently in the background, ensuring a continuous real-time data flow. This approach guarantees uninterrupted access to current information, enabling swift decision-making and efficient task management.
- The tool provides exceptional post-sale support, ensuring swift issue resolution and valuable guidance, guaranteeing you receive assistance precisely when required.
Cons
- The learning curve for this software tends to be rather steep, which means it may take users a while to grasp its complexities and nuances fully.
- Implementing updates in the interface can be time-consuming, potentially causing delays in the release of new features or improvements to the user experience.
Customer Rating
- G2: 4.5/5
- Capterra: no reviews
2. Orca Security
Orca Security is a cloud workload protection platform that provides cloud security and compliance for AWS, Azure, and GCP. It protects your cloud assets by detecting threats and sending alerts to the IT teams. It also prioritizes cloud risk based on the severity of affecting the organization and eliminates unnecessary threats, and helps you focus on what is more needed.
Pros
- Orca Security boasts remarkable efficiency by not consuming any additional storage for its routine operations, ensuring that your device's available storage remains unaffected while the software diligently safeguards your security.
- This security solution conducts comprehensive scans across various data sources, offering you a meticulously compiled list of potential threats that demand your immediate attention.
- The precision and reliability of the messages and alerts you receive from Orca Security are notably high, allowing you to trust the information provided and respond promptly to identified threats.
Cons
- The extensive volume of captured and presented data often proves overwhelming and, in many instances, fails to deliver meaningful insights or practical utility, posing a significant challenge in effectively leveraging the information.
- The learning curve associated with this software can be steep, requiring users to invest considerable time and effort to become proficient. This learning curve may hinder the swift adoption and efficient utilization of the software's capabilities.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
3. Qualys Cloud Platform

Qualys Cloud Platform is a cloud security posture management software that reduces cloud risk by detecting threats and sending alerts to IT teams.
It alerts the IT teams if a cloud risk is assessed that might affect the security and compliance of the organization. It gives complete visibility of the cloud assets and can detect any unauthorized or unusual activities.
Pros
- This tool is designed to be user-friendly and straightforward, making it accessible for individuals with varying levels of expertise. Users can quickly grasp its functionality, minimizing the time required for training and onboarding.
- The software provides users with a flexible module selection, allowing them to choose from various modules according to their needs. This adaptability empowers users to customize their software experience to align precisely with their requirements, ultimately maximizing their investment by only paying for the modules they actively use.
Cons
- The support provided by the company is often perceived as unprofessional, with instances of slow response times and prolonged resolution periods when addressing user issues. This lack of prompt and effective support can lead to frustration and downtime for users.
- The cost of licenses for this software is relatively high, which can be a significant drawback for organizations with budget constraints.
Customer Rating
- G2: 4/5
- Capterra: 3.6/5
4. Sysdig Platform
Sysdig is a cloud and container security software. With the help of this platform, IT teams can find and prioritize unusual cloud activities and detect and respond to insider threats. It provides a single platform to manage containers and Kubernetes to cloud services.
Pros
- The customer service is of high quality, ensuring users have a positive experience and can seek assistance or guidance when needed.
- The software excels in providing comprehensive research and detailed reports whenever it detects potential threats, offering users in-depth insights into their security posture.
Cons
- There is a substantial learning curve associated with the software, which may require a significant investment of time and effort to become proficient.
Customer Rating
- G2: 4.5/5
- Capterra: 3/5
5. Armor
Armor is a cloud security tool. It makes cloud security and compliance simple and easy to manage for IT admins. It provides insight into threats and helps organizations respond quickly and effectively.
It helps to detect and eliminate threats to your private cloud, public cloud, SaaS, workplace data, etc. It helps to identify and manage vulnerabilities and misconfigurations across your IT and application environments.
Pros
- Exceptional post-purchase support ensures that customers receive assistance and value even after the sale.
- It offers real-time threat monitoring, intrusion detection, and efficient threat mitigation, enhancing security and responsiveness to potential threats in real-time.
Cons
- Armor experiences frequent update-related issues, which can disrupt the software's performance and user experience.
- It lacks real-time data updates, potentially resulting in outdated information and limiting its ability to provide up-to-the-minute insights and protection.
Customer Rating
- G2: 5/5
6. JupiterOne
JupiterOne is a cloud compliance software. Compliance is complicated, but it tries to simplify the compliance for the organizations. It is used for governing cloud data and visibility and provides an absolute solution for security. In addition, it provides continuous monitoring of cloud environments and controls.
Pros
- It exhibits compatibility with various operating systems, including Windows, macOS, Linux, and more, offering flexibility and adaptability to diverse user environments.
- The software is designed to be user-friendly, ensuring a smooth and intuitive experience for users of varying technical backgrounds.
Cons
- The current performance of the system (suboptimal speed, efficiency, or responsiveness) does not fully meet its expected potential, indicating a need for significant enhancements and optimization.
Customer Rating
- G2: 5/5
- Capterra: 5/5
7. CrowdStrike Falcon
CrowdStrike Falcon is a cloud security posture management tool that helps to prevent cloud breaches. It protects the organization from any unauthorized risks or threats.
It detects, prevents, and responds to threats, ensures compliance, and builds safety in the cloud. It helps to gain visibility across your entire cloud environment, monitor for misconfigurations, enforce security policies and compliances, and stop cloud breaches.
It provides automated discovery, continuous runtime protection, and EDR for cloud workloads and containers and manages threat hunting, enabling you to securely deploy applications in the cloud.
Pros
- This solution offers a high degree of customization, allowing organizations to selectively adopt and tailor features based on their specific needs and objectives. This adaptability ensures that businesses can align the software with their unique requirements, optimizing its functionality for their operations.
- Comprehensive in scope, it provides a holistic approach to managing and securing cloud-based resources, ensuring organizations have a robust tool to address various aspects of their cloud infrastructure, from storage and networking to security and compliance.
Cons
- The results generated by the software are not consistently accurate, which can undermine its reliability and utility in decision-making and analysis.
- The level of customer support falls below expectations, often leading to dissatisfaction among users who encounter issues or require assistance.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
8. Prisma Cloud
Prisma Cloud is a cloud security posture management tool that provides visibility and protection across hosts, containers, and serverless in a single platform. It secures the infrastructure, applications, data, and entitlements across the cloud.
It integrates with any continuous integration and continuous delivery (CI/CD) workflow to secure cloud infrastructure and applications. It helps to monitor posture, detect and respond to threats, and maintain compliance across public clouds.
Prisma Cloud leverages cloud service provider APIs to provide visibility and control over public cloud environments.
Pros
- It offers excellent visibility, especially when integrated with third-party tools and platforms, allowing for a comprehensive view of your systems and data in conjunction with external sources.
- The software provides real-time scanning capabilities and generates detailed reports on vulnerabilities, empowering users to promptly identify and address security issues, ultimately enhancing the overall security posture of the system.
Cons
- Frequent upgrades can create a burden in terms of ongoing maintenance, potentially overwhelming users with the need for continuous updates and adjustments.
- The user interface is intricate and can be challenging to navigate, potentially causing confusion and frustration for users trying to interact with the software.
Customer Rating
- G2: 4.3/5
- Capterra: 4/5









.svg)














