SOC automation tools have become essential, boosting the effectiveness of cybersecurity efforts. This article will explore the top 15 SOC automation tools in detail.
As cyberthreats become more advanced, IT teams are under increasing pressure to keep their organizations secure. The challenge is not just detecting threats but also responding to them quickly and effectively. Managing a Security Operations Center (SOC) manually can be overwhelming, especially when dealing with large volumes of data and potential incidents.
This is where SOC automation tools come into play. By automating repetitive tasks and streamlining threat detection and response, these tools help your team stay ahead of cyberthreats without burning out. But with so many options available, choosing the right SOC automation tool can be difficult.
We have listed down the top 15 SOC automation tools to help you choose the best as per your requirements. But before that, let us discuss the essential features required for an efficient SOC compliance tool.
Key Features To Look For In A SOC Automation Tool
Below are the key features to look at when choosing a suitable SOC automation tool.
- Real-Time Threat Detection: You should look for a SOC automation tool that offers real-time threat detection. This capability allows the tool to continuously monitor network traffic, applications, and endpoints to identify suspicious activities as they happen.
- Automated Incident Response: An effective SOC compliance tool should offer automated incident response. This feature helps streamline the process of responding to security incidents by automating repetitive tasks, such as isolating affected systems, alerting relevant teams, and even initiating countermeasures.
- Threat Intelligence Integration: A SOC automation tool that can pull in data from global threat intelligence feeds will keep your IT team informed about the latest threats, vulnerabilities, and attack patterns. This ensures that your defenses are always up-to-date and capable of countering new and emerging threats.
- Customizable Playbooks: A SOC automation tool with customizable playbooks allows your IT team to tailor responses to the unique needs and policies of your organization. This flexibility ensures that the automated actions taken align with your security strategy and compliance requirements.
- Reporting and Analytics: This feature allows your team to gain insights into security trends, incident frequency, and the effectiveness of your defenses. These reports can help in making informed decisions about future security investments and in demonstrating compliance with regulatory requirements.
15 SOC Automation Tools
Now, let’s discuss the various SOC automation tools. These tools help your IT team enhance security, reduce manual workload, and respond to threats more efficiently.
1. Zluri
One key challenge in maintaining SOC is managing who has access to what within your IT environment. Zluri's access review solution simplifies this process, directly impacting how effectively you can achieve and maintain SOC compliance.
By automating access reviews, Zluri ensures that only authorized users have access to critical systems and data, reducing the risk of security breaches and non-compliance penalties.
Let’s see how.
Ensure Complete Control and Oversight of User Access
Zluri’s access review solution can significantly help you maintain access governance, a critical aspect of SOC compliance. Zluri provides a structured and transparent system to manage who can access sensitive data and systems.
For example, you might set a policy limiting access to certain financial reports to senior finance team members. Zluri automates enforcing these rules, ensuring that only those who meet the criteria can access the necessary resources. This level of precision in access control supports compliance efforts and protects against internal and external threats.
Moreover, to ensure complete control, Zluri allows you to create access certification. This certification will ensure that only authorized personnel gain access to specific information, effectively minimizing the risk of unauthorized access and potential security breaches.
The below image shows that Zluri allows you to create access certification for maintaining access governance.
Continuous User Access Monitoring
Zluri offers deep visibility into user access activities across your organization’s systems and applications. By providing real-time monitoring, Zluri allows you to quickly identify and address any unauthorized access attempts, helping to manage security risks and maintain SOC compliance.
For instance, when an employee is promoted and their role changes, Zluri automatically tracks and updates their access rights to align with their new responsibilities. This ensures that the employee has access only to the tools and data necessary for their current role, adhering to the principle of least privilege—a crucial aspect of SOC guidelines.
Further, this saves time and reduces the risk of unauthorized access, strengthening your organization’s security framework.
Automatically Remediate Access Issues to Manage User Permissions Efficiently
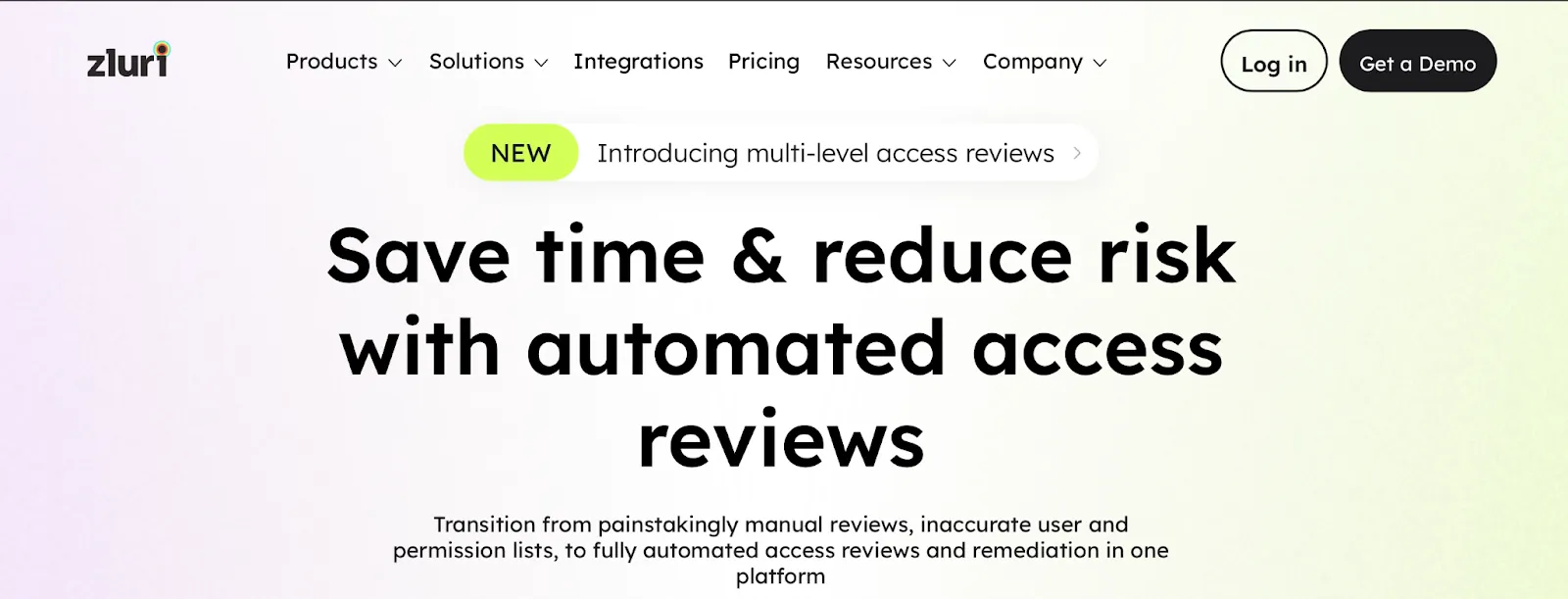
Zluri offers auto-remediation capability for access rights, specifically designed to enhance SOC automation. This functionality allows you to automatically revoke or adjust permissions when unauthorized access is detected, without requiring manual intervention.
This minimizes the risk of access-related incidents and maintains a high level of security and compliance within your organization.
For example, if an employee’s role changes or they leave the organization, Zluri allows you to swiftly adjust or remove their access rights based on predefined policies. This automated response helps prevent potential security breaches and ensures adherence to SOC compliance standards.
The image below shows the Zluri’s auto-remediation capabilities.
Generate In-Depth Reports to Review and Analyze User Access Rights
Zluri makes it easy to stay compliant with SOC requirements by generating detailed reports on access review activities. These reports are essential during audits and assessments.
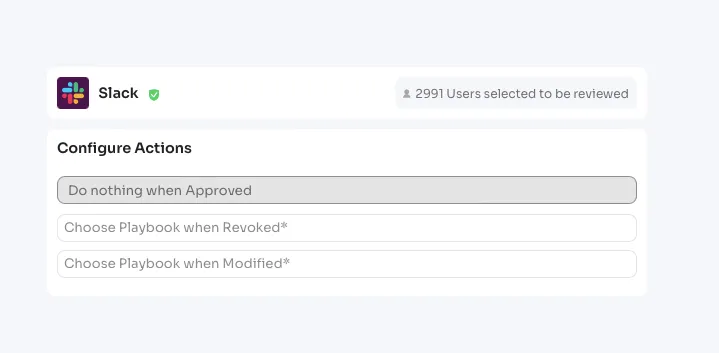
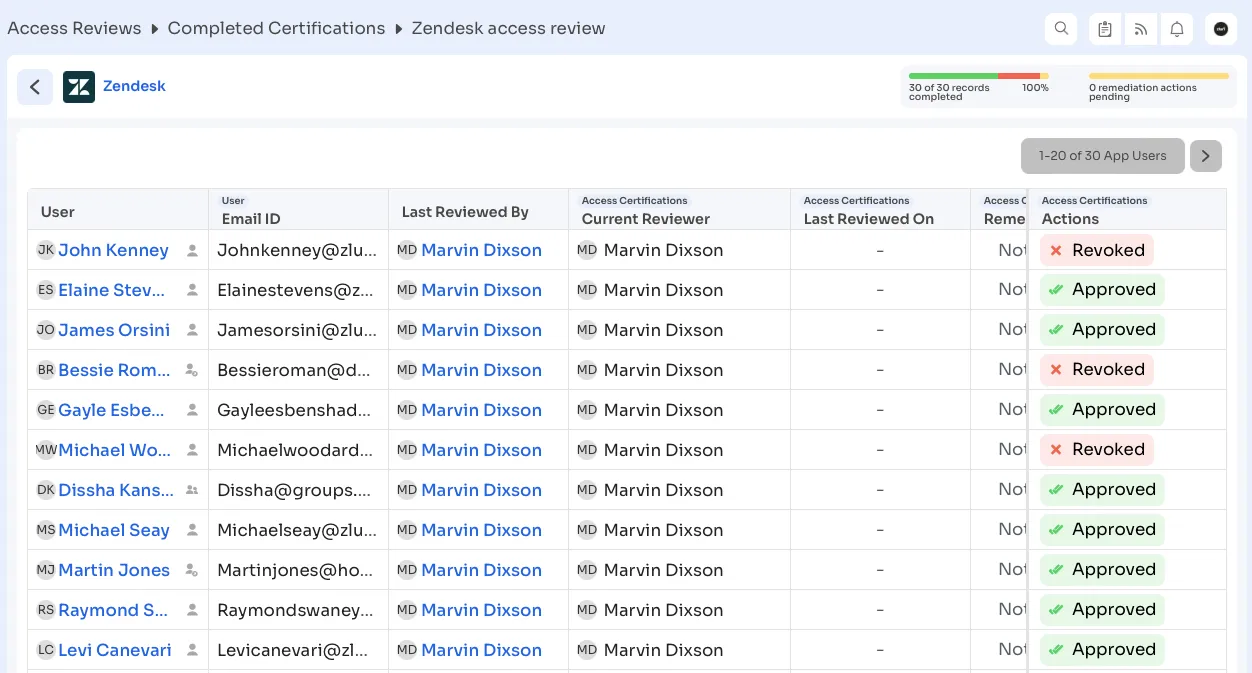
For example, if your company is in the finance sector and deals with sensitive customer data, Zluri’s reports provide a clear picture of who has access to important financial systems. The report shows who has access to which databases, applications, or systems, who approved this access, when it was granted, and what level of access was given.
The below mentioned image shows the reports of access review for Zendesk.
When auditors review your SOC compliance, presenting these detailed reports will show that you take data security seriously and follow the required policies. The reports help auditors verify that access rights are in line with your organization’s rules and regulations .
If you’re curious to know how Zluri’s access review works, Book a Demo today!
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Vanta
Vanta offers a SOC automation tool that simplifies and streamlines the process of achieving and maintaining compliance with SOC2 standards. The tool is designed to reduce the complexity and overhead associated with traditional compliance methods.
Vanta enables you to focus more on strategic initiatives rather than compliance maintenance. This ensures that your organization remains secure and compliant with minimal effort.
Key Features
- Access Reviews: Vanta simplifies the process of managing who has access to your systems. This feature helps you reduce the risk of unauthorized access and ensures that your organization’s security policies are consistently enforced.
- Custom Controls: Every organization has unique security needs, and Vanta allows you to create custom controls tailored to your specific requirements. This feature gives you the flexibility to design and implement security measures that fit your organization’s risk profile and compliance needs.
- System Description: Vanta also provides a comprehensive system description feature that automatically documents your IT infrastructure and security measures. This detailed overview includes information about your systems, architecture, and the controls in place, giving you a clear picture of your security posture.
Customer Rating
- G2: 4.6/5
- Capterra: 4.7/5
3. Drata
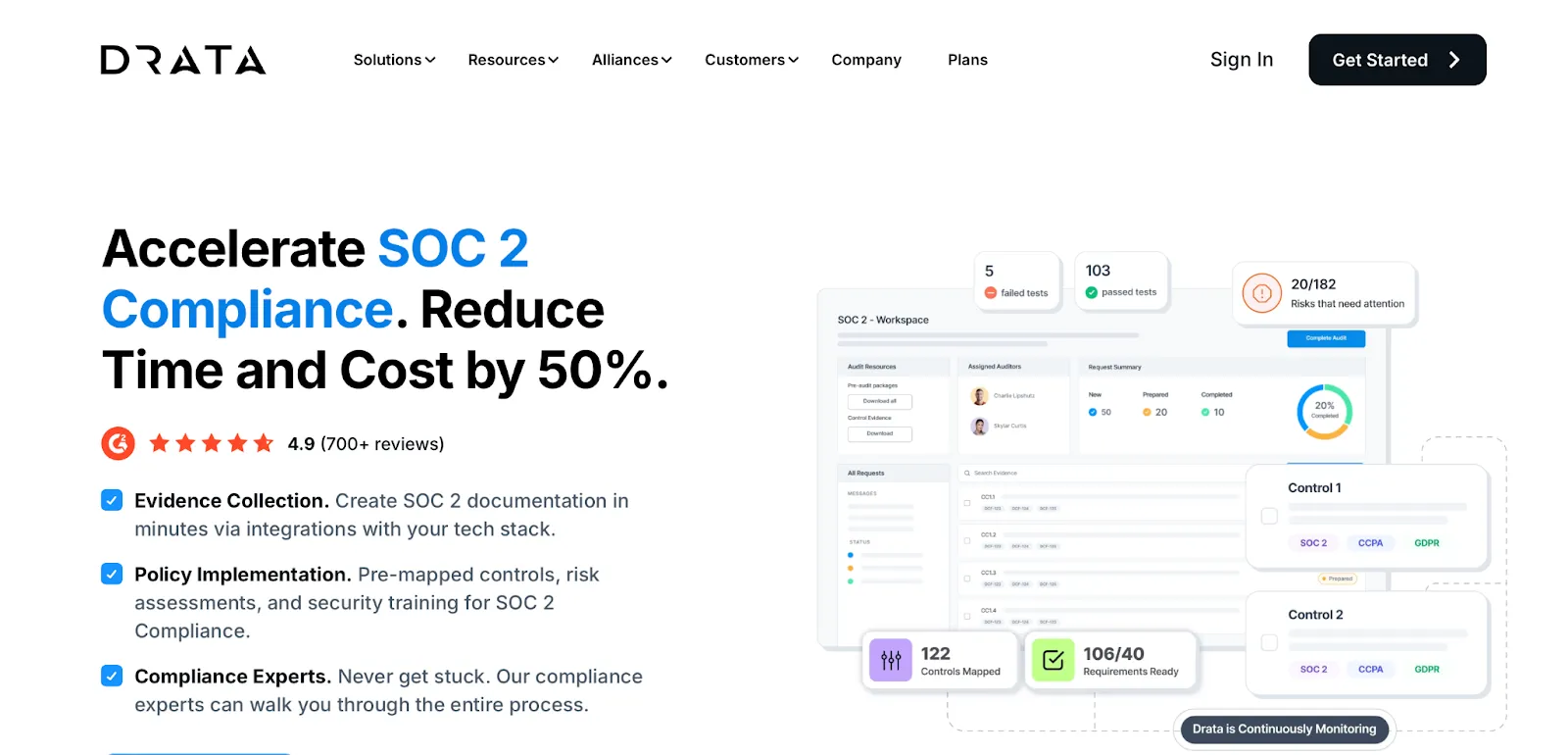
Drata is a security and compliance automation platform that monitors and collects evidence of the vendor's security controls. It helps streamline the compliance frameworks, like SOC, to ensure audit readiness.
The tool offers integrations with your SaaS vendors and brings compliance status in a single platform. It gives you complete visibility into your vendor's compliance status and control across their security program.
Key Features
- Configure Compliance: Drata makes it easy to configure compliance for your organization. This feature ensures that your organization remains compliant with minimal effort, allowing your IT team to focus on other critical security tasks.
- Automated Evidence Collection: One of Drata’s standout features is its ability to automate evidence collection. This includes logs, access records, and other critical data needed for audits. It saves time and reduces the risk of errors, ensuring that your organization is always ready for an audit or assessment without the last-minute scramble.
- Control the Process: With its centralized dashboard, you can monitor and manage all aspects of your SOC automation from a single interface. This feature allows you to track progress, identify gaps, and make adjustments as needed to stay on top of compliance requirements.
Customer Rating
- G2: 4.8/5
- Capterra: 5/5
4. Scrut
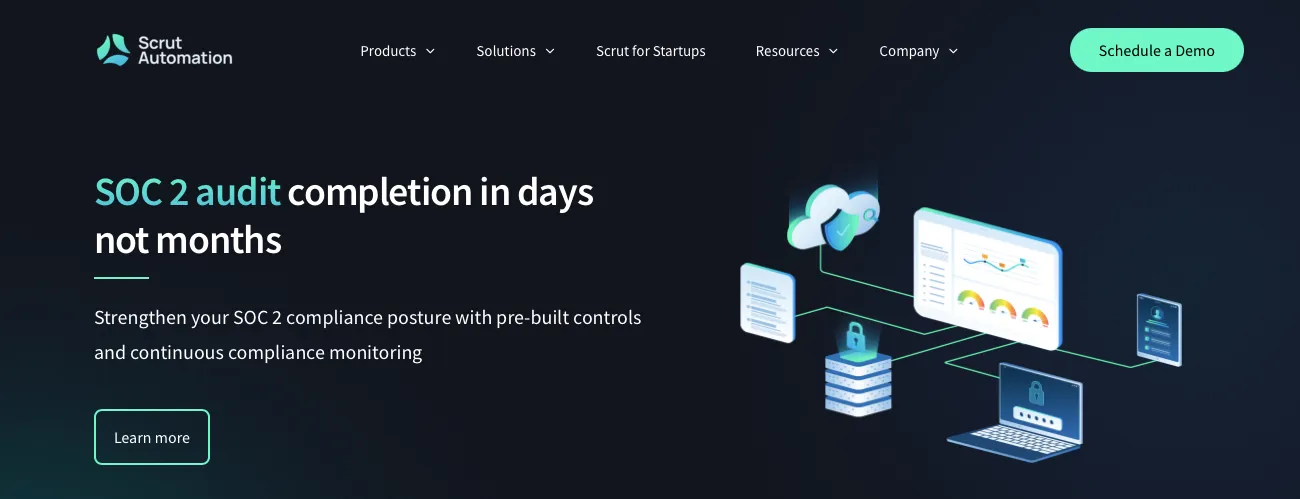
Scrut offers a SOC automation solution that monitors and collects evidence of an organization's security controls. It helps streamline SOC compliance to ensure a smooth audit process on a single platform.
Furthermore, Scrut's reliable tracking capabilities cover employee onboarding checklists, such as background checks, essential documents, and security training. It's a system you can trust to ensure proper offboarding of employees when they leave your organization.
Key Features
- Automate Compliance Workflows: Scrut streamlines your compliance workflows by automating repetitive tasks. This automation ensures that your compliance processes run smoothly and efficiently, allowing your team to focus on more strategic activities.
- Build SOC2 Compliance Policies: The platform helps you develop and implement policies that meet SOC2 standards, tailored to your organization's specific needs. This feature ensures that you have the right policies in place to support your compliance efforts effectively.
- Automate Evidence Collection: Scrut simplifies the evidence collection process by automating it. This automation reduces the time and effort required, making it easier to stay compliant and prepared.
- Continuously Monitor Compliance: With Scrut, compliance is continuously monitored to ensure that your organization remains aligned with SOC standards. The platform provides real-time visibility into your compliance status, allowing you to address any issues promptly and maintain a strong security posture.
- Accelerate Your SOC2 Audit: Scrut speeds up the SOC2 audit process by providing all necessary documentation and evidence in one centralized platform. This preparation accelerates the audit, reduces the stress associated with it, and helps you achieve certification more efficiently.
Customer Rating
- G2: 4.9/5
- Capterra: 5/5
5. Torq HyperSOC
Torq HyperSOC offers a SOC automation tool that simplifies the management of security operations by automating repetitive tasks. This reduces the time spent on manual processes, and accelerates incident response. It ensures that your security team can focus on more strategic activities rather than getting bogged down in routine tasks.
With Torq HyperSOC, you can expect a streamlined SOC experience that enhances both efficiency and effectiveness. Its comprehensive automation features allow for rapid response to security threats, better resource allocation, and a more proactive security posture.
Key Features
- Eliminate Alert Fatigue: Torq HyperSOC helps your SOC team avoid burnout by reducing alert fatigue. It automatically filters out low-priority alerts, ensuring that only the most critical issues reach your analysts. This feature allows your team to focus on real threats, improving their efficiency and reducing the risk of missing important alerts.
- Hyperautomate Case Management: Torq HyperSOC hyperautomates case management, streamlining the entire process from incident creation to resolution. This automation speeds up response times and ensures that each case is handled consistently, freeing up your team to focus on more strategic tasks.
- Augment Analysts with AI: Torq HyperSOC enhances your SOC capabilities by augmenting your analysts with AI-driven insights. The platform uses advanced algorithms to analyze data, identify patterns, and suggest actions, helping your team make more informed decisions.
- Manage & Monitor SOC Responses: With Torq HyperSOC, you can manage and monitor all SOC responses from a centralized platform. This feature provides real-time visibility into ongoing incidents, ensuring that all actions are tracked and documented.
Customer Rating
- G2: 4.7/5
6. SecureFrame
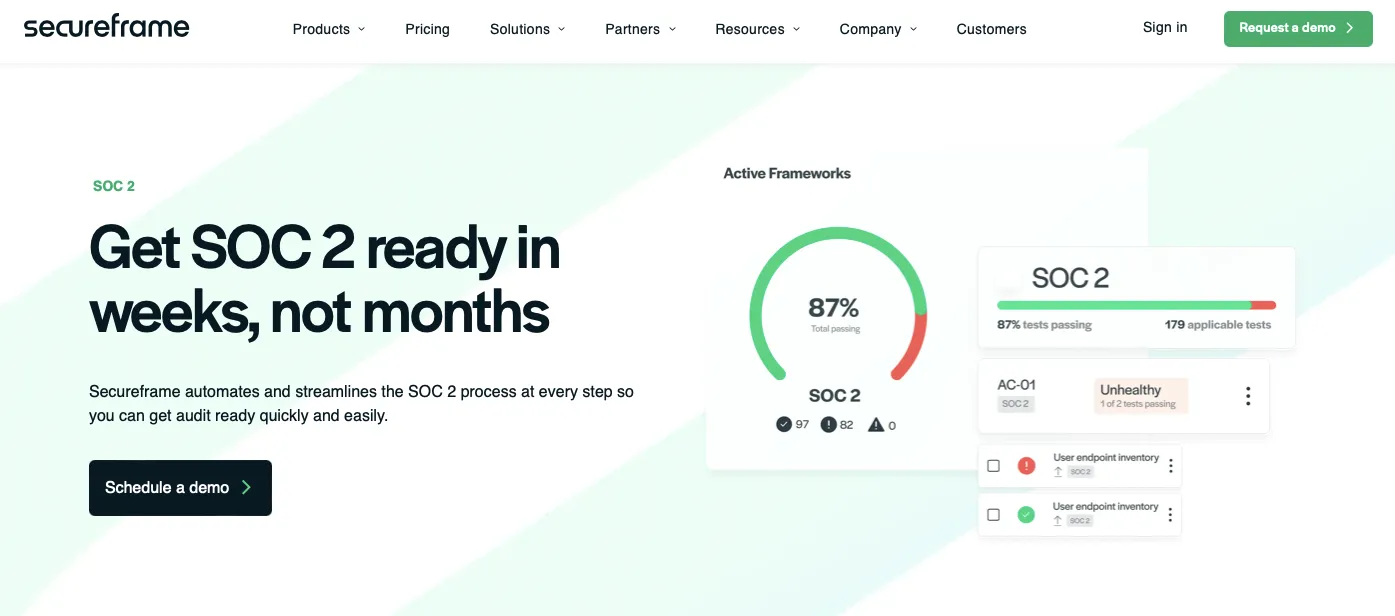
Secureframe helps your organization by automating compliance frameworks like SOC 2. It seamlessly integrates with your existing tools and workflows, minimizing disruption to your operations. Whether using cloud services, collaboration tools, or development platforms, Secureframe has you covered.
Moreover, Secureframe helps you scale your business securely. It streamlines the entire compliance process and controls and workflow that fits your business. It helps you get audit-ready.
Key Features
- Automated Compliance Monitoring: Secureframe takes the hassle out of compliance management by automating the entire process. It continuously monitors your systems and processes to ensure they meet SOC standards, allowing you to stay compliant without manual effort.
- Real-time Compliance Insights: Secureframe offers detailed reports and dashboards that provide a clear overview of your compliance posture, helping you quickly identify and address any areas that need attention.
- Customized Compliance Frameworks: Secureframe allows you to customize compliance frameworks to fit your specific requirements, ensuring you meet SOC standards without unnecessary complexity.
- Simplified Audit Preparation: Secureframe makes audit preparation easier by centralizing all the necessary documentation and evidence. With everything in one place, you can approach audits with confidence and ease.
Customer Rating
- G2: 4.7/5
- Capterra: 5/5
7. Sprinto
Sprinto offers a compliance automation tool for SOC. Sprinto automates compliance monitoring that continuously assesses your systems and processes against SOC compliance standards. Sprinto actively tracks and analyzes your organization's adherence to regulatory requirements, providing real-time insights into your compliance status, from data security to privacy controls.
Key Features
- Customizable Compliance Workflows: Sprinto offers the flexibility to customize compliance workflows to fit your organization's specific needs. Whether you’re mapping controls, assigning tasks, or monitoring progress, Sprinto’s adaptable system allows you to shape the compliance process to align with your business goals.
- Unified Documentation Management: Sprinto brings all your compliance documentation together in one centralized, easily accessible platform. From audit reports to policy documents, you can efficiently manage and organize all SOC compliance materials in a single, user-friendly location.
- Instant Alerts and Notifications: With Sprinto, you can stay ahead of compliance challenges through real-time alerts and notifications. Receive immediate updates on compliance violations, approaching audit deadlines, and regulatory changes, enabling you to address issues promptly before they become major concerns.
Customer Rating
- G2: 4.8/5
8. AuditBoard
AuditBoard offers a SOC automation tool to simplify and streamline compliance management processes. With AuditBoard, you can navigate the complexities of SOC compliance with confidence. Your organization is well-equipped to meet regulatory requirements and safeguard sensitive data effectively.
Key Features
- Simplify Risk Assessments: AuditBoard streamlines the risk assessment process by automating the identification and evaluation of potential threats. This automation makes it easier for your team to prioritize risks based on their severity and impact, ensuring that the most critical issues are addressed first.
- Collect Evidence Efficiently: AuditBoard automates the collection of evidence, ensuring that all necessary documentation is organized and easily accessible. This feature speeds up the audit process and ensures that your SOC team has the right information at their fingertips, improving accuracy and efficiency.
- Drive Collaboration with Stakeholders: AuditBoard enhances collaboration by providing a centralized platform where stakeholders can communicate, share updates, and track progress in real-time. This feature ensures that everyone involved in security operations is on the same page, leading to more coordinated and effective responses.
- Manage Compliance Issues & Reports: AuditBoard automates the management of compliance issues. This helps your team monitor and address any gaps before they become problems. It also simplifies the process of generating reports, ensuring that your organization meets all regulatory requirements without unnecessary hassle.
Customer Rating
- G2: 4.6/5
- Capterra: 4.7/5
9. Swimlane

Swimlane stands out as the SOC automation tool by offering a powerful platform designed to streamline and enhance security operations. With its focus on automated workflows and centralized management, Swimlane enables your team to handle security incidents more efficiently. It integrates seamlessly with existing tools and systems, providing a unified interface for managing and responding to security threats.
Swimlane’s platform allows your team to create customized workflows, automate repetitive processes, and gain deeper insights into security operations. This results in a more efficient SOC that can adapt quickly to emerging threats, ultimately enhancing the overall security posture of the organization.
Key Features
- Automate Security Operations: Swimlane’s automated security operations reduces manual work, allowing your security team to focus on more critical issues.
- Automate Critical SOC Processes: Swimlane enables the automation of critical Security Operations Center (SOC) processes. This includes everything from threat detection to incident response. It also helps maintain consistency and accuracy in your security operations.
- Secure Employee Offboarding: Swimlane automates the offboarding process, ensuring that access to systems and data is promptly revoked when an employee leaves. This automation reduces the risk of insider threats and ensures that no loose ends are left when someone exits the company.
- Fraud Investigation & Response: Swimlane’s automation capabilities extend to fraud investigation and response. This helps protect your organization from financial losses and reputational damage.
- Anti-Cheat Investigation: For organizations dealing with online platforms or gaming, Swimlane offers automation for anti-cheat investigations. It quickly identifies and responds to cheating activities, maintaining a fair and secure environment for users. This feature is crucial for maintaining trust and integrity in your services.
Customer Rating
- G2: 4.6/5
10. HyperProof
Hyperproof offers the ultimate solution for SOC compliance automation. With Hyperproof, you can streamline your compliance efforts, saving time and easily ensuring adherence to SOC requirements. The tool centralizes everything you need in one intuitive interface.
Key Features
- SOC 2 Program Template: Hyperproof simplifies your SOC 2 compliance journey with its ready-to-use SOC 2 program template. This template is designed to align with industry standards, helping you quickly set up a compliant security framework.
- Automate Evidence Collection: The platform automatically gathers and organizes evidence from your systems, saving your team significant time and reducing the risk of human error. This automation ensures that your SOC team is always prepared for audits, with all necessary documentation readily available and up-to-date.
- Easily Assign Tasks to Collaborators: The platform allows you to delegate responsibilities quickly and track progress in real-time. This feature ensures that everyone involved in your SOC operations is aligned and working efficiently towards maintaining compliance and security.
Customer Rating
- G2: 4.6/5
- Capterra: 4.8/5
11. Tugboat

Tugboat is your trusted partner in SOC compliance automation. Tugboat is designed to simplify the daunting task of achieving and maintaining SOC compliance. This empowers your team to focus on strategic initiatives while Tugboat handles the heavy lifting of compliance management.
Tugboat integrates with your existing IT infrastructure and tools, maximizing efficiency and minimizing disruption. Whether you're using cloud services, on-premises solutions, or a hybrid environment, Tugboat adapts to your workflow for a frictionless experience.
Key Features
- Automated Compliance Checks: Tugboat simplifies compliance by automating checks across your systems and infrastructure. It continuously scans for any deviations from SOC requirements, eliminating the need for manual audits.
- Real-time Monitoring: Tugboat's real-time monitoring keeps you ahead of potential compliance issues. It provides instant alerts and notifications if any violations occur, allowing your team to respond quickly and prevent risks from escalating.
- Customizable Reporting: Whether you need in-depth analytics or concise summaries, Tugboat delivers the insights you need in the format that best suits your organization. This flexibility helps you make informed decisions based on clear, actionable data.
- Comprehensive Documentation: Tugboat centralizes all your SOC compliance documentation in one easy-to-access platform. From policies and procedures to audit trails and evidence collection, Tugboat keeps everything organized and up-to-date. This makes it simple to manage and retrieve the documentation you need for audits or reviews.
12. RadiantSecurity
RadiantSecurity provides an AI SOC analyst platform designed to streamline and enhance security operations. Its advanced automation capabilities and seamless integrations with existing tools enable SOC teams to manage security incidents more effectively.
RadiantSecurity's platform centralizes and automates key tasks, improving response times and reducing the manual workload on security professionals.
Key Features
- Automated Detection & Investigation: The platform uses advanced algorithms to quickly identify potential security incidents and initiates an investigation without manual intervention. This automation speeds up the threat response process, ensuring that issues are detected and addressed before they can escalate.
- Rapid Containment & Remediation: RadiantSecurity automates these processes, allowing your SOC team to quickly isolate affected systems and implement fixes. This minimizes the impact of security incidents, reducing downtime and preventing further damage to your organization.
- Escalations & Approvals: When critical incidents occur, the platform ensures that the right team members are alerted and that necessary approvals are obtained swiftly. This feature accelerates response times, ensuring that serious threats are dealt with promptly and effectively.
- Communication Workflows: The platform facilitates seamless collaboration among your SOC team, ensuring that everyone stays informed and aligned throughout the incident response process. This leads to more coordinated and efficient handling of security events.
13. DuploCloud
DuploCloud offers a comprehensive solution for SOC compliance automation. DuploCloud streamlines the compliance process, offering a robust platform designed to automate and simplify SOC compliance management, allowing you to confidently focus on core business operations.
Seamlessly integrate DuploCloud with your existing IT infrastructure and third-party tools. The platform supports a wide range of integrations, allowing you to leverage existing investments and maximize the efficiency of your SOC compliance efforts.
Key Features
- Standard-Compliant Controls: DuploCloud ensures your organization meets industry standards by providing out-of-the-box, standard-compliant controls. These controls are designed to align with major compliance frameworks like SOC 2, making it easier to implement and maintain security measures.
- Continuous SOC 2 Compliance Monitoring: The platform automatically tracks and evaluates your systems against SOC 2 requirements, alerting you to any deviations in real time. This proactive approach ensures that your organization remains compliant without the need for manual checks.
- Streamlined Audits: The platform automatically gathers and organizes the necessary documentation and evidence required for SOC 2 audits, reducing the workload on your team. This feature not only saves time but also increases the accuracy and completeness of your audit preparations, ensuring a smoother and more efficient audit process.
Customer Rating
- G2: 4.7/5
14. Thoropass
Thoropass offers acomprehensive solution for SOC automation that streamlines and automates the compliance process for SOC. This helps your team to focus on what matters most: keeping your systems secure and your organization running smoothly.
Key Features
- Policy Templates: Thoropass simplifies the process of setting up and maintaining security policies with its extensive library of policy templates. These pre-built templates are designed to align with industry standards, making it easier to implement and enforce security policies across the organization.
- Auditor-Approved Custom Controls: Customizing security controls to fit your organization’s unique needs is crucial, and Thoropass makes this process seamless with its auditor-approved custom controls. These controls are designed to meet the highest compliance standards, giving you the flexibility to tailor your security framework while still satisfying audit requirements.
- Continuous Monitoring: The platform continuously monitors your systems and processes, providing real-time insights into potential threats and vulnerabilities. This continuous vigilance enables your SOC team to respond swiftly to incidents, reducing the risk of breaches and minimizing downtime.
Customer Rating
- G2: 4.7/5
- Capterra: 5/5
15. CrowdStrike
CrowdStrike’s Next-Gen SIEM offers advanced AI-native SOC automation capabilities. The platform streamlines threat detection and response. This empowers you to automate routine tasks, reduce alert fatigue, and focus on higher-priority issues, ensuring your organization stays one step ahead of potential threats.
Key Features
- Find and Stop Attacks Fast: Using advanced AI and machine learning, CrowdStrike identifies suspicious activities in real-time, allowing your security team to act immediately. This swift response reduces the risk of a security breach and minimizes potential damage to your organization.
- Eliminate Blind Spots: Blind spots in your security landscape can leave your organization vulnerable to attacks. CrowdStrike eliminates these blind spots by providing complete visibility into your entire network.
- Log All Your Data: CrowdStrike automatically logs all relevant security data, giving you a detailed record of all activities within your network. These logs are crucial for investigating incidents, understanding attack patterns, and complying with regulatory requirements. With all your data securely logged, your organization is better prepared to respond to any security threat.
Customer Rating
- G2: 4.7/5
Choosing the Right SOC Automation Tool
Selecting the right SOC automation tool is essential for optimizing security operations and defending your organization against evolving threats. The top 16 SOC automation tools we've discussed offer various features designed to enhance efficiency, improve incident response times, and provide comprehensive threat management.
As you evaluate these tools, focus on how well they integrate with your existing systems, their ease of use, and their specific capabilities. Each tool has its strengths, so choosing the best fit for your team will depend on your unique requirements and challenges.
Moreover, invest in the right tool timely. It will help you stay ahead of potential threats and maintain a robust security posture.
Frequently Asked Questions (FAQs)
What is SOC automation?
SOC automation streamlines the monitoring and handling of phishing emails, saving valuable time and resources. For instance, automating the detection and response to phishing attempts in Gmail can ensure that malicious emails are identified and addressed promptly without overwhelming your team.
What are SOC tools?
Security Operations Centers (SOCs) act as the first line of defense, constantly monitoring, detecting, and addressing security incidents to protect an organization's digital assets. Advanced SOC tools are central to their effectiveness and crucial for efficient threat detection, rapid incident response, and proactive security measures.
What are the technologies in SOC?
Key technologies in a SOC include SIEM, IDS, IPS, Next Generation Firewalls, EDRs, SOAR, and Threat Intelligence. Each technology has its unique features and functions, but when combined, they provide comprehensive protection against a wide range of digital threats.
What are the three types of SOC?
SOC 1, SOC 2, and SOC 3 serve distinct purposes. SOC 1 is centered on financial reporting controls, SOC 2 covers a broader spectrum of data management practices related to security, availability, processing integrity, confidentiality, and privacy, while SOC 3 offers a summary of the SOC 2 report, designed for a general audience.
What are the best tools for automated security testing?
Some of the best tools for automated security testing includes:
- Zed attack proxy
- BeFF (Browser Exploitation Framework)
- Synk
- Wapiti
What are the key tools for SOC?
- Splunk
- LogRhythm
- SOAR
- Trend Micro
- ArcSight









.svg)














