With the rising adoption of cloud-based technologies, there is a critical need for cloud security solutions that can effectively address evolving security challenges.
While Trend Micro cloud security is a feature-rich and robust cloud app security tool, other alternative solutions in the market provide varying features and capabilities.
Hence, it is essential for you, as an IT manager, to explore Trend Micro alternatives and then make an informed decision on securing your cloud environments.
Trend Micro offers a wide range of solutions for organizations of all sizes. One of their flagship products is the Trend Micro Cloud App Security solution. This solution is designed to help organizations secure their cloud-based emails and collaboration services, such as Microsoft Office 365, Google Workspace, and Dropbox.
Trend Micro Cloud Security: An Overview
Trend Micro's cloud app security solution provides advanced threat protection, data loss prevention, and compliance capabilities to help businesses address cloud security challenges. Its core mission revolves around fortifying the security of cloud applications by seamlessly integrating with them, all achieved without the complexities of intricate network configurations or the need for rerouting traffic.
Trend Micro introduces an innovative approach ensuring organizations can fully leverage their cloud applications' potential without compromising safety. Its cloud security delivers platform-centric protection, comprehensive risk management, and multi-cloud detection and response capability.
Despite being a comprehensive cloud security solution, Trend Micro Cloud Security has limitations, making it unsuitable for certain IT teams.
Drawbacks of Trend Micro Cloud Security
Here are some limitations, which may prompt you to explore Trend Micro competitors:
- Limited Customization: As an IT manager, you may find that the customization offered by Trend Micro Cloud Security is insufficient to meet your organization's specific needs. For example, you may require more precise control over security policies, which may not be feasible with the solution's current capabilities.
- Complexity: The solution can be complex to deploy and manage for your team, particularly if you manage small organizations with limited IT resources. The learning curve for admins and users may also be steep.
- Pricing: The solution can be expensive, especially for small and medium-sized organizations. The pricing model may not be flexible enough to accommodate your organizational needs with varying sizes and budgets.
- Customer Support: While Trend Micro offers average customer support, you may prefer a cloud security solution with more localized and responsive support for your team.Considering these limitations, you may prefer to explore Trend Micro alternatives and cloud security solutions that better align with your specific needs and budget. But before we discuss the tools, let us briefly introduce us (Zluri) here:
Zluri- An Ultimate Solution for SaaS Security
Zluri is a comprehensive platform that includes various features and capabilities to help you manage and secure your organization's entire SaaS landscape with ease. Our advanced discovery methods allow you to quickly identify and track all SaaS applications being used within your organization.
We prioritize SaaS discovery by utilizing five advanced discovery methods to ensure 100% coverage of all SaaS apps. It helps in SaaS security by providing visibility and control over all the SaaS applications used in an organization, even those not approved by the IT department. This helps to identify Shadow IT, which can be a significant security risk.
Once all the SaaS applications are identified, Zluri's discovery engine can assess the security posture of each application. This includes identifying security vulnerabilities, misconfigurations, and other potential risks.
With our platform, you can track events and statistics, data shared, and perform compliance and security checks for your SaaS applications. We use secure encryption algorithms to ensure the security of your sensitive data and provide a detailed log of all security-related activities for audit purposes.

Further, it helps you stay secure and compliant with various standards, including ISO 27001, SOC 2, GDPR, and more. Our platform assists you in achieving SaaS compliance and prepares you for audits.
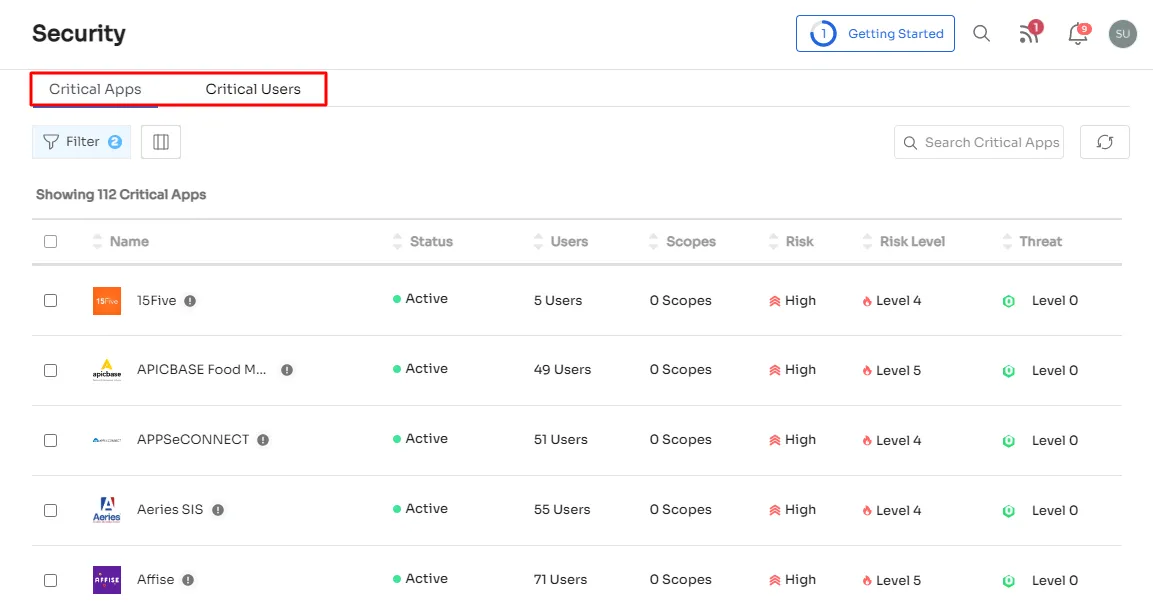
Zluri goes above and beyond by providing a view of critical apps with high threat levels and risk scores, alerting you to avoid using apps that can compromise data confidentiality and increase the risk of cyber attacks.
With our risk-related metrics, such as threat levels and risk scores, you can assess the risks associated with SaaS apps and take appropriate action.
Our risk-scoring system takes these 4 factors into account:
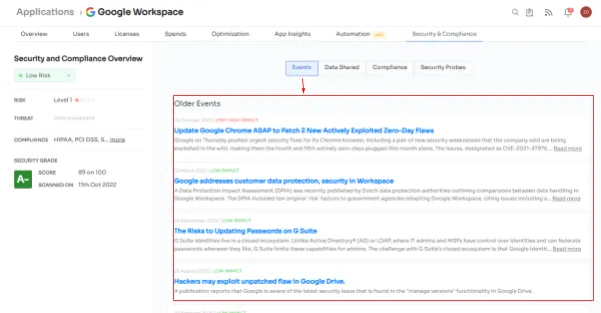
- Events: If there are any events related to any particular SaaS app on the internet, Zluri keeps a close eye on it. It monitors recent security breaches related to SaaS applications and adjusts the risk score of that app accordingly if any such incidents are detected.
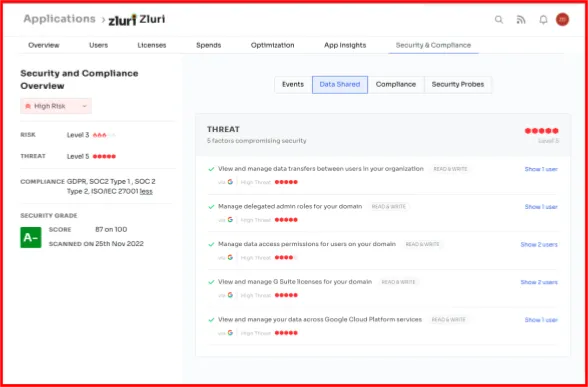
- Data shared: The level of risk associated with a particular scope is determined by the sensitivity of the scopes they have access to. For example, if an application has access to a scope that enables it to delete all your Google Drive files, it is considered a high-risk scope. On the other hand, if an application has access to a scope that only allows it to access a user's email address, it is considered a low-risk scope. Zluri uses this information to determine the risk score of the application.
- Compliance: When it comes to security, compliance is an important factor to consider. Applications that comply with various regulations are generally viewed as more secure. For example, if an application like Slack complies with many major global regulations, it is considered more secure than applications with fewer compliance certifications.

- Security Probes: Zluri gathers security data by conducting technical scans from external sources such as ssllabs, Immuniweb, and imirhil. The tool then computes a weighted average of the security grades obtained and presents the results on its dashboard, with a rating ranging from A (highly secure) to F (low security).
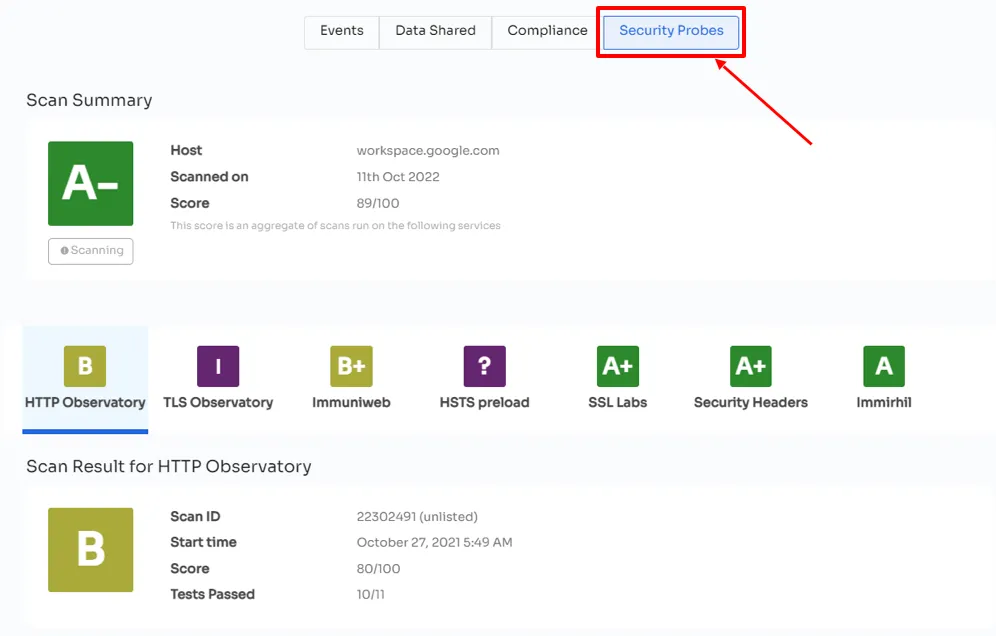
- Zluri rates the security level of your organizational SaaS apps on a scale of 1 to 5, considering the abovementioned factors. Applications with a rating of 1 or 2 are considered low-risk, while those with a rating of 3 are of medium risk. Applications with a rating of 4 or 5 are considered to be of severe risk. This helps you identify which of your critical apps pose a high threat level and have a high risk score.Thus, Zluri is the ideal solution for analyzing and enhancing your SaaS infrastructure's security. It enables you to take the necessary precautions to secure your organization’s SaaS apps and protect its sensitive data.

- Would you like to explore further? book your demo today!
List of 9 Trend Micro Alternatives
Here we will be discussing 9 of the best Trend Micro alternatives to help you choose the best solution for your organization's security needs:
1. Zscaler
Zscaler provides a robust cloud security solution with its Cloud Access Security Broker (CASB) offering. This solution combines traditional CASB features with advanced security capabilities, such as behavior analysis and machine learning, for your IT teams.
Zscaler’s CASB also employs advanced encryption technologies to secure sensitive data both in transit and at rest. Additionally, it utilizes behavior analysis and machine learning to identify and prevent cyber threats like phishing attacks, malware, and data exfiltration. This comprehensive approach to cloud security makes Zscaler an excellent choice for IT teams looking to enhance their organization's data protection capabilities.
Pros
- With Zscaler, you can take advantage of its reporting feature to gain valuable insights into your organization's web and application usage, providing you with greater visibility and helping you to identify any potential security threats
- The tool is user-friendly and requires no specialized skills or training, enabling you to establish policies and rules to safeguard your cloud applications quickly
Cons
- If you are managing a small or mid-sized organization with limited budgets, the solution can be costly, which may make it a less appealing option for you
Customer Rating
- G2: 4.7/5
2. Citrix's secure access
Citrix's Secure Access tool is purpose-built to safeguard cloud-based applications and data against security threats. It acts as a secure connection between users and the SaaS apps utilized within an organization, effectively protecting sensitive data from unauthorized access.
Furthermore, Citrix's secure access offers advanced threat detection capabilities, allowing IT teams to quickly identify and mitigate potential security threats before they can cause harm to the organization. With Citrix's secure access, IT teams can have confidence that cutting-edge security measures protect their organization's cloud-based resources.
Pros
- Citrix's secure access feature enables your employees to securely access company resources remotely, from any location and device, facilitating collaboration and enhancing productivity
- Due to the platform's easy integration with other tools, you can efficiently manage the security of all your organization's cloud applications
Cons
- Your team may encounter difficulties in setting up and configuring the solution, which can be time-consuming and require specialized knowledge, creating a barrier for smaller organizations with limited resources
- Additionally, you may experience delays in accessing critical applications or files due to occasional system slowness, resulting in decreased efficiency and possible downtime
Customer Rating
- G2: 4.2/5
3. Fortinet's Cybersecurity Services
Fortinet, one of the notable Trend Micro alternatives, is a cybersecurity provider with various products, including firewalls, security analytics, and centralized management. Their FortiGuard Cloud Access Security Broker (CASB) stands out for its increased visibility and control over cloud applications and services.
It enables monitoring and regulation of cloud access across all endpoints, ensuring the protection of sensitive data and regulatory compliance. Moreover, FortiGuard CASB provides real-time threat protection using advanced threat intelligence and machine learning to proactively detect and mitigate potential threats within cloud environments.
Pros
- You will have access to real-time threat insights, which will keep you and your team informed about potential cyber threats
- The solution also provides a deep level of security against various phishing sites, safeguarding your organization from DDoS attacks
Cons
- You may encounter challenges in efficiently managing security as the solution lacks visibility in tracking attacks.
- Moreover, some of its features may be complex to use, requiring your team to invest more time in practicing or receiving professional training
Customer Rating
- G2: 4.7/5
4. Oracle's Cloud Access Security
Oracle's Cloud Access Security, a Trend Micro competitor is a robust tool that gives you complete visibility and control over your cloud environment. It presents a centralized view of all cloud services used in your organization, including popular applications like Office 365, Salesforce, and Dropbox and custom-built cloud applications. This enables you to quickly detect potential security risks and take action to address them.
In addition, Oracle's CASB provides advanced threat detection capabilities that allow you to promptly identify and respond to various security threats, whether internal or external, such as malware, phishing attacks, and unauthorized data access. With Oracle's CASB, you can rest assured that your cloud-based resources are protected by advanced security measures.
Pros
- The solution's ability to automatically respond to threats can help you safeguard your organization's cloud files more effectively
- If you're looking for cost-effective measures to protect your organization's data, this solution can be a great option, as it offers an affordable way to secure your cloud applications
Cons
- You may find that the tool has a steep learning curve, and additional training from experts may be required, which can take up valuable time
- Furthermore, you may find it challenging to manage 3rd party apps efficiently with Zscaler, as it lacks a more straightforward approach to handling them
Customer Rating
- G2: 4.6/5
5. Symantec's CloudSOC
Symantec's CloudSOC, a well known Trend Micro competitor, is an enterprise-grade Cloud Access Security solution and a notable Trend Micro alternative that offers complete visibility and control over an organization's cloud applications and services. It safeguards sensitive data, monitors cloud usage, and enforces security policies throughout the organization's cloud environments.
With CloudSOC CASB, you can gain in-depth visibility into cloud usage throughout the organization. This visibility lets you detect potential security risks and proactively prevent data loss or theft. Moreover, CloudSOC CASB offers real-time alerts and notifications, empowering you to respond quickly to security incidents and prevent data breaches.
Pros
- With this tool, you have access to strong reporting capabilities, giving you the power to gain insights into your organization's cloud apps and manage their security more efficiently
- You can define security policies based on users, groups, and devices, allowing you to create and enforce security policies that align with your organization's security requirements with this solution
Cons
- At times, it may not offer comprehensive on-demand scanning, which can lead to inefficiencies in securing your entire IT infrastructure
- Due to the complicated pricing structure, which varies depending on the number of users, cloud applications, and level of support required, it can be challenging for you to accurately budget for the solution
Customer Rating
- G2: 4.2/5
6. Cisco Cloudlock
Cisco Cloudlock, one of the best Trend Micro alternatives, is an advanced cloud security platform that streamlines security operations for cloud applications and data, reducing risks and preventing data breaches. With Cloudlock, security teams can manage access permissions, monitor data usage, and prevent unauthorized data exposure from a single dashboard.
In addition, Cloudlock provides granular controls for data sharing management, allowing IT managers to set policies that govern which data can be shared and with whom. This feature ensures that sensitive data remains secure and minimizes risks associated with data sharing.
Pros
- Cloudlock simplifies the investigation of security issues that arise when an alert is triggered, making it easy for you to resolve the issue and secure your organization's IT environment
- The emails sent to users are concise and provide only necessary information, enabling your team to quickly identify the issue and address it
Cons
- Cisco Cloudlock has a higher price tag than other premium cloud security solutions. If you are managing organizations with a limited budget, it may not be an appropriate option for you.
- Implementing Cisco Cloudlock's advanced capabilities may require you and your team to dedicate additional time and resources for training and implementation, as it has a steeper learning curve
Customer Rating
- Capterra: 4.5/5
7. Forcepoint's Cloud security
Forcepoint's Cloud security solution offers real-time visibility and control over cloud applications to detect and prevent security threats and data breaches. It includes advanced DLP capabilities to identify and prevent data breaches by detecting sensitive data and applying policies to prevent unauthorized access.
The solution also allows for granular control over cloud application usage, enabling users to set policies that govern access permissions and prevent unauthorized data sharing. Additionally, Forcepoint's CASB offers powerful threat detection capabilities, using advanced analytics and machine learning to identify anomalous activity and mitigate threats in real-time.
Pros
- You can easily deploy and manage the solution and, hence, quickly start securing your organization's IT infrastructure and manage it from a single console
- By providing insights into cloud usage and security risks, the solution can help you make informed decisions and improve your organization's security posture
Cons
- At first, the licensing process of the solution can be challenging, which may consume your time that could be otherwise utilized for focusing on other important tasks
- Your ability to detect issues may be limited with this tool, as the solution lacks sufficient security capabilities for CASB integration and Google Cloud integration
Customer Rating
- G2: 4.5/5
8. Netskope's CASB
Netskope's Cloud security, a Trend Micro competitor, is a powerful tool for organizations of all sizes looking to secure their cloud-based operations and safeguard sensitive data. Netskope's CASB solution also provides real-time alerts and notifications, allowing IT managers to respond quickly to security incidents and prevent data breaches.
With Netskope's CASB, IT teams can gain comprehensive visibility and control over their cloud environment, ensuring the data remains secure and compliant with industry regulations. In addition, it offers granular controls for managing data sharing, enabling IT managers to set policies that govern which data can be shared and with whom. This helps you maintain control of sensitive data and mitigate risks associated with data sharing.
Pros
- With Netskope, you can benefit from a comprehensive cloud security platform offering a single glass pane. This will make it easy for you to monitor, manage, and secure cloud applications across your entire organization
Cons
- You may face difficulties with agent deployment using IDP as the tool lacks a centralized agent deployment tool built-in
- You may find the tool limiting in terms of restricting access to a certain group of users, as it offers limited options for doing so
Customer Rating
- G2: 4.4/5
9. Akamai's cybersecurity
Akamai, one of the notable Trend Micro alternatives, offers a range of security solutions designed to address different security needs for IT teams. With these solutions, IT teams can safeguard their organization's networks and data and gain peace of mind in an ever-evolving threat landscape.
One of Akamai's key security solutions is the web application firewall, which protects against common attacks like SQL injection and cross-site scripting. This solution can be tailored to meet the specific requirements of different industries and integrates with existing security tools seamlessly.
Furthermore, Akamai provides additional services, including DDoS protection, threat intelligence, and secure content delivery. With Akamai's security solutions, your IT teams can effectively manage their security needs and reduce the risk of cyber attacks.
Pros
- Akamai's security solution ensures that your website and applications remain accessible to your employees by protecting them against distributed denial of service (DDoS) attacks
- By generating traffic reports, the solution enables you to identify and block unwanted IPs in your organization's network
Cons
- You may find the solution expensive, as it consists of hidden charges, which could be challenging for organizations with limited budgets.
- Configuring the tool is not easy, and you will need to invest more time and effort to do so
Customer Rating
- G2: 4/5







.png)

.svg)














