Your company announced it's pursuing SOC 2 certification.
The auditor's first question: "Show me evidence of access reviews for the past 12 months."
You open your folders. You have:
- Spreadsheets from Q1 and Q3 (Q2 is missing)
- Email threads where managers said "looks good"
- A few Jira tickets marked "In Progress" from six months ago
- No formal signed attestations
- No proof that violations were actually remediated
The auditor takes notes. You can see this isn't going well.
This scenario plays out at organizations that run manual access reviews—they do the work, spend the time, involve the people, but when the audit happens, they can't prove it.
Proof matters. Because auditors aren't just checking that you tried. They're checking that your access reviews actually made you more secure.
When security researchers examine breach data, they find patterns. A former employee still had access months after leaving. A contractor from last year's project never got deprovisioned. An intern somehow accumulated admin rights to production systems.
These aren't sophisticated attacks. They're basic access hygiene failures—exactly what access reviews are supposed to prevent.
Access reviews prevent these audit nightmares when done right. Here's why they're fundamental to security and compliance.
What access reviews actually do
Access reviews are systematic processes where you validate that every person's (whether employees, consultants, contractors, or partners) access to every application is appropriate for their current role and employment status.
Not once during onboarding. Not just when something goes wrong. Regularly—typically quarterly or semi-annually—you verify that access still makes sense.
The review asks simple questions: Does this person still work here? Did their role change? Do they still need admin access? Should this contractor who finished their project 3 months ago still have credentials?
Without systematic reviews, you're operating on assumptions: "We probably deprovisioned that person," "Access was probably appropriate when granted," "Managers probably know what their team needs."
Access reviews replace assumptions with evidence.
Reason 1: Security—preventing breaches from the inside
Insider access shows up in breach after breach
External attackers get headlines. But when investigators trace how breaches actually happened, insider access—whether malicious or just forgotten—shows up repeatedly.
And "insider" doesn't just mean current employees.
It includes former employees who still have credentials, contractors whose projects ended months ago, employees who changed roles but kept old permissions, and third-party vendors with persistent access. Each represents a potential breach vector that remains invisible until something goes wrong.
A contractor still has admin access—6 months after the project ended
A contractor starts a 6-month Salesforce integration project in January.
Week 1: IT provisions admin access. The project completes in June.
The contractor moves on to their next client. Access doesn't get revoked because nobody remembered to add this app to the offboarding checklist, the Jira ticket got closed as "complete" without verification, the contractor used their personal email (not the client's domain), and nobody thought to check after the project ended.
December: That contractor—now working for a competitor—still has admin access to your customer database, pipeline data, and pricing models.
Without systematic quarterly reviews, this access stays active indefinitely. You'll discover it during a breach investigation—after the damage is done.
Organizations without effective reviews face higher breach rates
We asked organizations to trace their security breaches backward—not forward from policy, but backward from incident to root cause. What did investigators actually find?
The pattern repeated: over-permissioned accounts that should have been caught, ex-employees with credentials that should have been revoked, third-party vendors who'd finished contracts months ago.
Organizations that don't conduct regular access reviews report that these three categories—over-permissive access, ex-employee access, and third-party access—account for the majority of breaches they investigate.
Organizations with systematic quarterly reviews cut these breach rates significantly. The difference? Reviews catch these issues before they're exploited.
Access reviews catch these issues—when done systematically
Regular access reviews identify:
- employment status changes (active → terminated),
- role changes (sales → marketing, no longer needs Salesforce admin),
- time-based access (contractor projects that ended), and
- privilege creep (accumulated permissions over years).
The key word here is "systematically." One-off reviews after an incident don't prevent breaches. Quarterly or semi-annual reviews that cover all users and all applications do.
Reason 2: Compliance—meeting regulatory requirements
"Who specifically certified this access as appropriate?"
You're in the SOC 2 audit. The auditor asks: "Show me who certified that John Smith should have admin access to your production database on September 15."
You search your files. You find an email where his manager said "team access looks fine," a spreadsheet with checkmarks (no names, no dates), and a Slack thread discussing whether he needs that access (no conclusion documented).
The auditor asks: "Who specifically certified this access as appropriate?"
You don't have an answer. Because nobody did. Not formally. Not in a way you can prove.
Frameworks require proof, not just reviews
Every major compliance framework mandates regular access reviews:
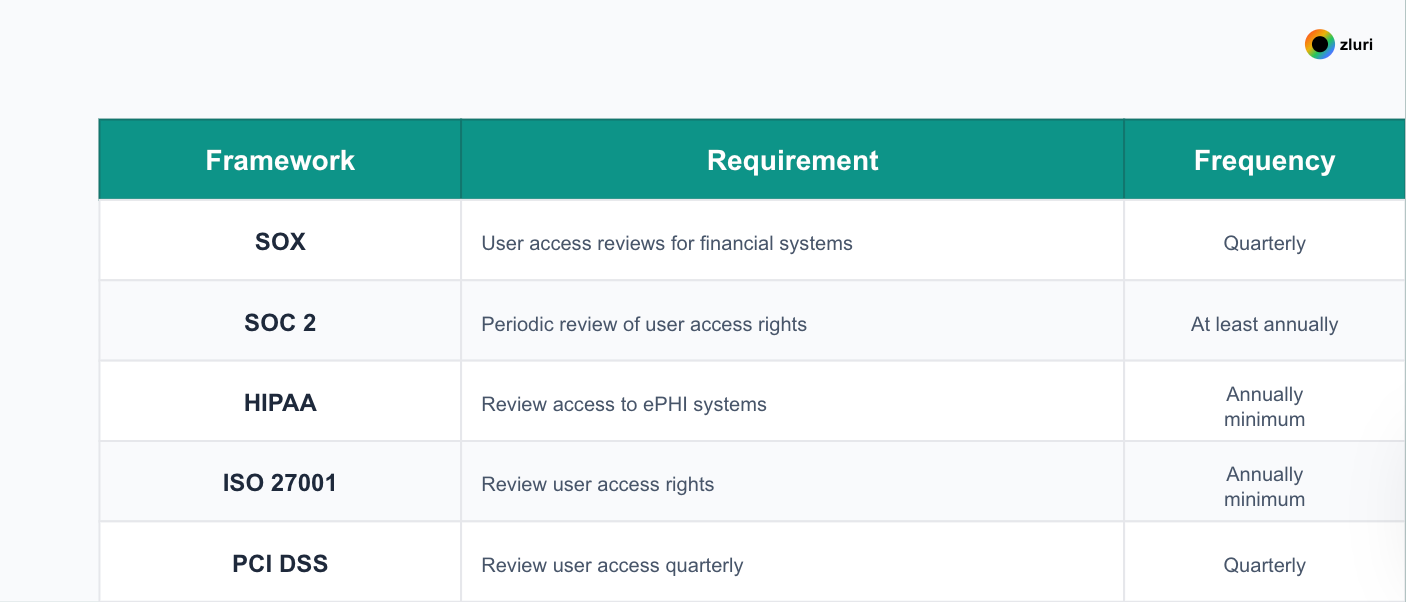
But frameworks don't just require reviews. They require proof. Here's what auditors actually check:
- evidence reviews happened on schedule (not just "we meant to do it"),
- formal signed attestations (not just "someone looked at it"),
- proof violations were remediated (not just "we created a ticket"), and
- complete audit trails showing WHO reviewed, WHAT they decided, WHEN remediation occurred.
We surveyed 215 compliance and security leaders about whether they believe airtight access review processes are required to comply with regulations. Nearly all agreed—91% said access reviews are critical for compliance.
Without systematic reviews and documentation, you can't demonstrate compliance. You can't show auditors that access was appropriate, that you checked it regularly, and that you fixed violations when you found them.
Failed audits mean lost deals, regulatory fines, and executive liability
SOC 2 failed audit = Lost enterprise deals. Most B2B customers require SOC 2 before they'll even evaluate your solution.
HIPAA violations = $100-$50,000 per violation, up to $1.5M annually. Plus reputation damage in a trust-critical industry.
SOX violations (publicly traded) = SEC enforcement actions, stock price impact, personal liability for executives.
PCI DSS non-compliance = Fines up to $100,000/month plus loss of payment processing capability.
These aren't theoretical consequences. They happen to organizations that think they had access under control but can't prove it when auditors asked.
Reason 3: Cost optimization—eliminating wasted licenses
Your CFO asks why SaaS costs jumped 40%
Your CFO asks why SaaS costs increased 40% last year. You investigate. You discover 87 users with Zoom licenses who haven't logged in once (waste from day 1), 134 users who haven't accessed Salesforce in 90+ days (dormant), 23 former employees still showing as "active" in various apps (billing continued for months), and 31 contractors who finished projects but still have licenses.
For a 1,000-employee company, assume 200 SaaS applications, conservative 5 unused licenses per app, and average cost $50/user/month.
Waste calculation: 1,000 unused licenses × $50 = $50,000/month = $600,000/year.
That's not a worst-case scenario. That's typical for organizations without systematic access reviews.
Licenses accumulate every week—but you only notice once a year
License accumulation happens continuously. It doesn't wait for budget reviews.
Week 2: Trial converts to paid without IT approval.
Week 5: Employee onboarded, given access, uses it once, never again.
Week 8: Department buys duplicate tool on corporate card.
Week 11: Contractor project ends, access stays active.
Without quarterly access reviews that include usage data, these licenses accumulate unnoticed. By the time the CFO asks about rising costs, you've already paid for months or years of waste.
Without usage data in your reviews, you're flying blind on costs
Without regular access reviews that include usage data, you can't identify users licensed but never logged in, dormant accounts (90+ days inactive), appropriate license tier (Enterprise when Basic would suffice), or duplicate licenses across multiple instances.
Access reviews combined with usage intelligence turn cost optimization from annual budget panic into systematic savings. Every quarter, reclaim hundreds of unnecessary licenses before they cost you another quarter's billing.
Reason 4: Operational efficiency—stopping the reactive firefighting
Week after week of scrambling for answers
Without systematic access reviews, IT and Security spend enormous time on reactive questions:
Week 1: Former employee's access isn't fully revoked during offboarding. Two weeks later, someone notices they responded to an email from their personal account. IT scrambles to figure out what apps they still have access to. It takes 4 hours.
Week 5: Security alert: "Dormant account suddenly active." Investigation reveals the contractor from 9 months ago still has access. Nobody knew, nobody checked. Another 3 hours identifying what they accessed.
Week 8: Manager asks: "Does Sarah still need Salesforce admin?" IT doesn't know. Manager doesn't know. Sarah doesn't remember why she has it. 2 hours just to answer yes or no.
Week 12: Audit preparation. Compliance asks: "Show me evidence that access to financial systems was appropriate all year." You have scattered emails, partial spreadsheets, and some Jira tickets. You start a 3-week scramble to reconstruct evidence.
Every week: Questions about who has access to what. IT pulling data manually. Security triaging alerts. Compliance worrying about the next audit. This is reactive chaos, not governance.
Organizations without reviews spend weeks reconstructing access data each quarter
We tracked how organizations handle access governance without systematic reviews:
When audits approach, teams rush to pull data manually from 25+ applications. IT reconstructs who had what access when. Security tries to identify current violations retroactively. GRC attempts to piece together evidence from emails, tickets, and spreadsheets.
This reconstruction typically involves 20+ people across IT, Security, and GRC spending weeks gathering information that should have been captured systematically all along.
Access reviews create a single source of truth
With systematic quarterly access reviews, instead of scrambling for answers, you have them ready:
"Can someone check if John still has access to X?" → Dashboard shows exactly who has what across all apps.
"Why is this account active?" → Risk scores flag high-priority access automatically.
"Prove access was appropriate." → "Here's the Q2 certification report with timestamps."
The time saved isn't even the primary benefit. The security posture you gain is.
Reason 5: Risk management—continuous visibility
Without reviews, violations exist for weeks or months before discovery
Without systematic reviews, here's what typically happens:
Week 2: Contractor's project ends, access no longer appropriate—but nobody knows.
Week 5: Employee changes roles, old permissions no longer needed—access remains.
Week 8: Someone's elevated to admin for a one-time migration, should be temporary—becomes permanent.
Week 11: Employee gives notice, leaves the company—some access gets missed in offboarding.
These violations exist for weeks or months before anyone notices. You're not preventing access issues—you're discovering them after they've already created risk.
Access reviews establish systematic validation
Regular access reviews transform access governance from reactive to proactive:
Quarterly reviews provide formal validation that every person's access is appropriate for their current role. Between reviews, you have baseline documentation showing what access should exist. When changes happen (terminations, role changes, project completions), you have a systematic process to catch them in the next review cycle.
Instead of violations accumulating indefinitely, they're identified and remediated within one review cycle—typically 90 days maximum.
Why most organizations struggle with access visibility
Your IDP sees 80 apps. You're actually using 200+.
Your Okta dashboard shows 80 applications. Your access reviews cover all 80. Perfect visibility, right?
Investigation reveals a different reality.
Your engineering team is using GitHub with personal accounts (not SSO), ChatGPT Team (purchased on corporate card), Figma (adopted by design team, never told IT), Notion workspaces (shared via personal emails), and Airtable databases (sales built their own CRM).
These apps have access to source code repositories, customer data exports, product roadmaps and strategy, pipeline data and forecasts, and financial models.
None appear in your access reviews. None go through your IdP/SSO. You're certifying 20-40 apps while 100+ are invisible.
When we asked compliance and security leaders: "What's your biggest access review challenge?" Lack of visibility was among the core reasons. 27% cited "no/limited visibility into who has access to what applications" as one of their primary obstacles.
This is for the known applications only. We are not even talking about the unknown applications yet.
You can't review what you can't see. Your IDP only sees apps accessed via SSO—typically 40-60% of your actual application landscape. The rest? Shadow IT operating completely outside your governance process.
A financial services company discovered half their apps were invisible
One of our clients, a financial services company, investigated their application coverage. They assumed their IDP gave them complete visibility. Investigation revealed that fewer than half their critical applications were behind SSO.
The majority—tools their teams used daily for sensitive customer data—were completely invisible to their access review process. Shadow IT wasn't the exception. It was the norm.
This is why effective access reviews require discovery capabilities beyond just IDP integration. You need to find all applications—SSO-integrated, directly accessed, purchased on corporate cards, adopted by teams—before you can review access to them.
Who needs access reviews?
Every organization. But especially:
1. Mid-market companies (500-5,000 employees)
Large enough to have SaaS sprawl (200+ apps) and compliance requirements. Small enough that manual processes are breaking under the load. Growing fast—access changes weekly, reviews happen quarterly. Pursuing enterprise compliance (SOC 2, ISO 27001) to win larger deals.
2. Financial services & fintech
SOX compliance mandatory (quarterly reviews required). Handling extremely sensitive financial data. Heavy regulatory scrutiny (OCC, FDIC, Fed examiners). High third-party vendor access creates risk.
3. High-growth tech companies
Rapid hiring (onboarding 50+ people per quarter). Developer-heavy orgs adopt tools constantly. Shadow IT is endemic—teams move fast, ask permission later. Pre-IPO compliance preparation with limited security staff.
4. Healthcare & life sciences
HIPAA requirements with serious penalties. Access to ePHI systems must be documented. Contractor-heavy (research, clinical trials, consulting). High audit frequency from regulators.
5. Any organization with:
High contractor and vendor usage, multiple subsidiaries or business units, recent M&A activity (inherited access complexity), existing compliance certifications that need renewal, or audit findings related to access management.
What happens without access reviews?
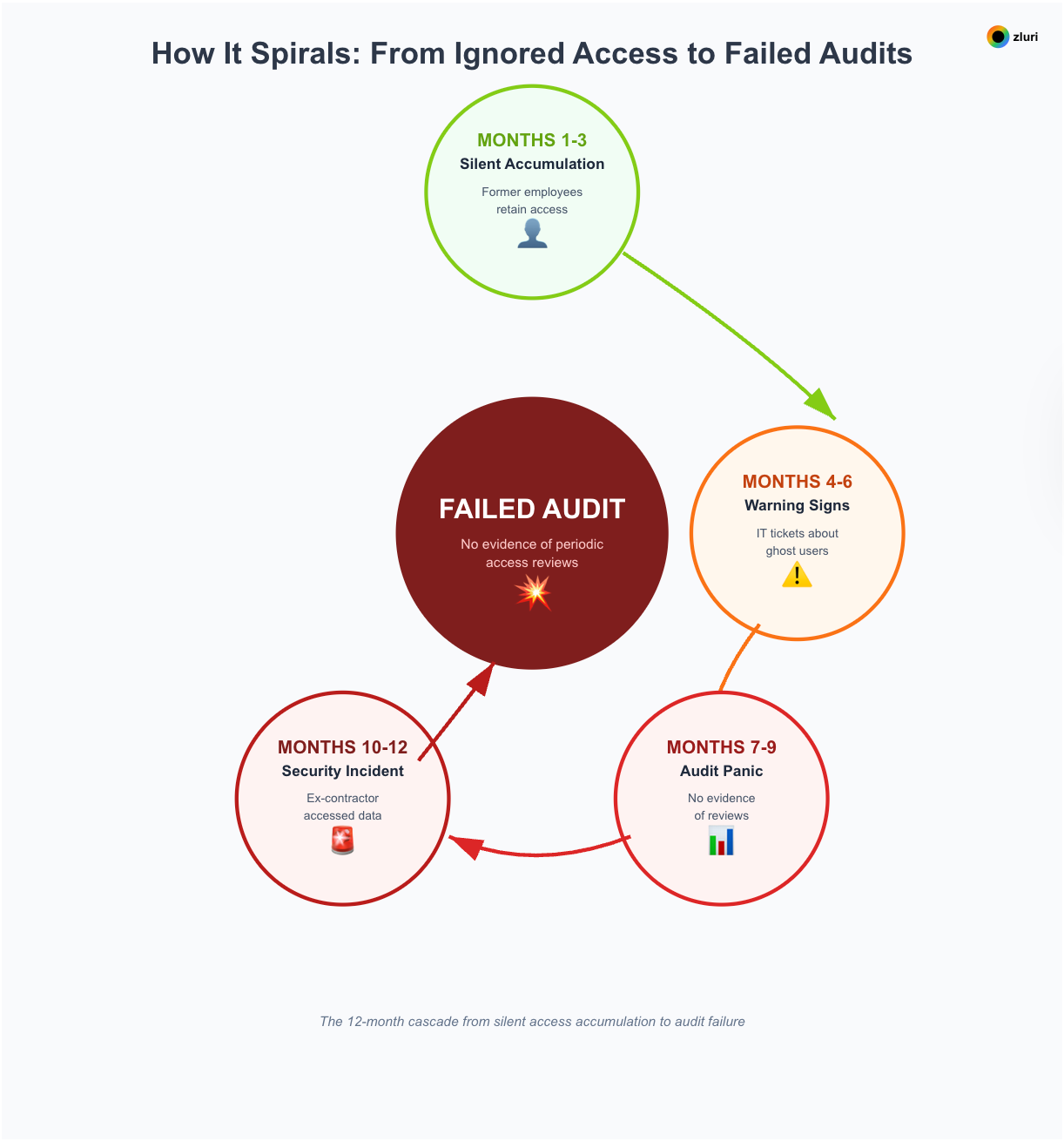
How it spirals: From ignored access to failed audits
Months 1-3: Former employees retain access—nobody notices yet. Contractors finish projects but credentials remain active. Users accumulate permissions from role changes and temporary projects. Nobody knows the extent of the problem because there's no systematic check.
Months 4-6: IT starts getting tickets: "Why does [former employee] still have email?" Security investigates alerts about unusual access from dormant accounts. Managers lose track of what their team can access. CFO notices license costs climbing but can't identify where the waste is coming from.
Months 7-9: Audit preparation reveals gaps: "We don't have evidence of access reviews for the past year." Compliance officer panics. IT scrambles to manually pull access lists from 100+ apps. Data conflicts emerge: Okta says users don't have access, app shows they do. Hours spent reconciling.
Months 10-12: Security incident: Former contractor accessed sensitive customer data 6 months after their project ended. Incident investigation reveals the access was never revoked—no systematic review would have caught it.
The end result is failed compliance audit: No evidence of periodic access reviews for SOX-scope financial systems. "We're working on implementing a process" isn't acceptable to auditors.
SOC 2 certification delayed. Enterprise deals on hold pending certification. Board meeting: "How did this happen?" No good answer.
With systematic reviews, you prevent the spiral
Organizations that conduct regular access reviews systematically:
Security: Ex-employee access caught in next quarterly review (90 days maximum exposure vs. indefinite). Contractors identified when projects end. Violations measured in days or weeks, not months or years.
Compliance: Audit evidence always ready. "Here's the Q2 certification report with complete attestations and remediation proof."
Cost: License waste caught every quarter. Our research shows organizations reclaim an average of $600,000 in annual SaaS spending through systematic reviews.
Operations: Teams spend focused time on quarterly reviews instead of constant reactive firefighting. Questions have answers immediately instead of requiring investigation.
Board confidence: "Here's our access governance framework, the evidence it works, and the metrics showing continuous improvement."
Access reviews are fundamental, not optional
Access reviews aren't optional—they're fundamental to security and compliance.
Organizations without systematic access reviews face:
Higher breach rates from over-permissioned accounts, ex-employee access, and third-party access that should have been revoked
Compliance failures when auditors ask for evidence and you can't produce formal attestations and remediation proof
Wasted spending on hundreds of unused licenses that accumulate because nobody's systematically checking usage
Operational chaos spending weeks scrambling for access information that should be documented systematically
Accumulated risk as violations persist for months or years before discovery
Every day without systematic reviews, you're exposed
Former employees with access to customer data. Contractors with backdoors to production systems. Compliance violations accumulating. License waste compounding. No audit trail when something goes wrong.
That's breach risk, security risk, audit risk, cost risk, and liability risk—all piling up while you assume access is under control.
In our survey, we found that 77% of organizations plan to implement or improve their access review processes within the next year. 43% plan to do it within six months.
Those who act first will reduce breach risk from access-related issues, pass audits with documented evidence, reclaim substantial SaaS spending on unused licenses, and shift from reactive firefighting to systematic governance.
The question isn't whether access reviews are important. They are. The question is whether you'll implement systematic reviews before an audit failure, security breach, or budget crisis forces your hand.
See who has access to what in your environment and prioritize access risks.
[Start Discovery Scan] → Book a Demo to understand your complete access landscape across all applications







.png)

.svg)














