As an IT manager, selecting the right identity governance and administration (IGA) software is a crucial decision that directly impacts your organization's security, compliance, and efficiency. With numerous options available in the market, it can take time to identify the best fit for your specific requirements.
Work decentralization has become increasingly prevalent in today's modern work environment, presenting new challenges for managing and governing users' access across organizations. Ensuring a robust and secure access management system is paramount for employees working from various locations and utilizing multiple devices.
However, this task can be daunting for IT managers who need to maintain control over access permissions while allowing flexibility and productivity. Implementing an identity governance and administration (IGA) solution emerges as the ideal strategy to address these challenges effectively.
Why IGA is the Solution:
An IGA solution is designed to streamline the user access management process by centralizing identity and access control. This approach gives you a comprehensive view of user identities, roles, and access privileges across the entire organization.
By implementing an IGA solution, you can achieve the following:
- Enhanced Security: IGA ensures that users only have access to the resources they need, reducing the risk of data breaches and unauthorized access.
- Regulatory Compliance: With a centralized IGA system, enforcing compliance with industry regulations and internal policies becomes easier, avoiding potential penalties.
- Increase in Productivity: By streamlining access management processes and providing a seamless user experience, IGA solutions contribute to increased efficiency and productivity.
Therefore, choosing the most suitable IGA tool for your organization requires careful consideration of its capabilities and compatibility with your existing infrastructure. This article will help you explore and understand the questions that you should consider before selecting an IGA tool suitable for your organizational needs.
Questions to Consider When Choosing an IGA Tool
Here are some essential questions to guide your decision-making process while selecting a suitable IGA tool.
1. Does it help you gain complete visibility into your users' access?
One of the key challenges you face is obtaining a comprehensive view of the entire SaaS landscape. Traditionally, you have relied on manual methods like spreadsheets to monitor and track the organization's software usage. However, these manual approaches often fall short of providing the depth of insights required to understand users' access thoroughly.
Additionally, the data obtained through these manual methods may lack accuracy and real-time updates, making it challenging to make informed decisions promptly.
For this reason, having a comprehensive understanding of the apps in your organization empowers you to optimize costs, improve security measures, and enhance overall productivity. It allows you to evaluate user access and permissions critically.
Understanding who has access to what data and applications is crucial for maintaining data security and compliance with industry regulations. Identifying any unauthorized or inappropriate access can help prevent potential data breaches and mitigate security risks, safeguarding sensitive information.
Also, having access to real-time data and insights allows you to identify redundant applications, consolidate licenses, and negotiate better deals with vendors, leading to cost savings.
Thankfully, modern IGA solutions like Zluri help you effortlessly gain complete visibility into your organization’s SaaS landscape.
Zluri makes it simple to analyze data about your SaaS applications and users. It leverages nine methods to discover this information: through MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
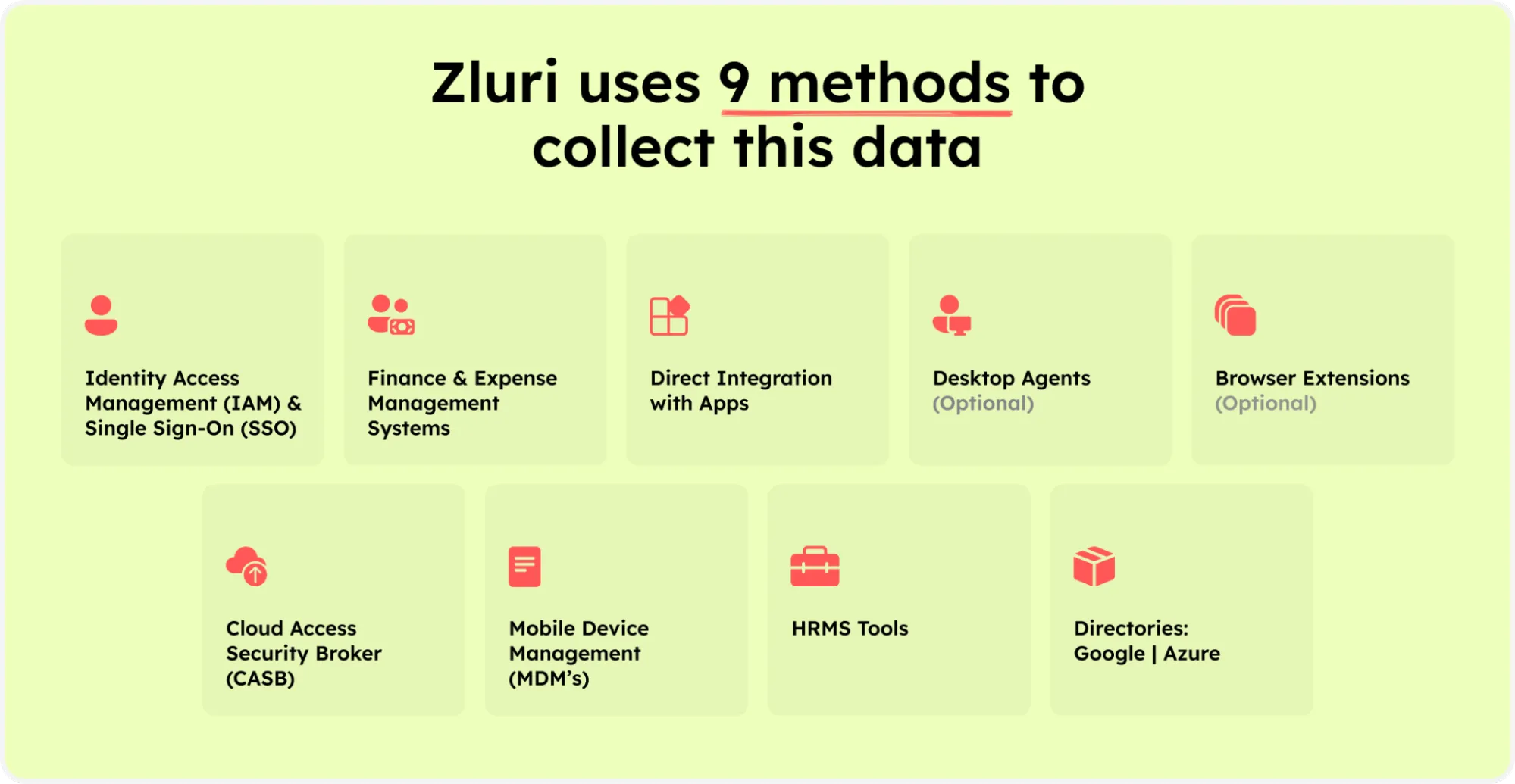
Zluri’s nine discovery methods
In addition to its discovery capabilities, Zluri's platform goes beyond by offering integration with over 300 SaaS applications. It provides real-time data, valuable insights, and AI-powered alerts to keep you informed.
With API-based integrations, Zluri ensures the profound discovery of data across all your SaaS applications, leaving no information hidden. You can trust that Zluri delivers 100% visibility into your SaaS environment.
Moreover, Zluri has the most extensive library, with over 2,40,000 apps. It excels in providing granular-level access data. It dives into the details, giving you a comprehensive understanding of user permissions and access levels within your SaaS ecosystem. This level of granularity ensures that no vital aspect goes unnoticed.
2. Does it streamline and optimize users' access management through automation?
The growing complexity of modern business environments, with numerous applications, systems, and data sources, demands an efficient and automated approach to handle access controls. Manually managing access rights can lead to oversights, leaving potential security vulnerabilities or causing access discrepancies.
Rather than manually processing each access request and provisioning user rights, an automated IGA solution can swiftly handle these tasks. This automation reduces the burden on your IT team, freeing them to focus on more strategic and value-added tasks, ultimately increasing productivity and effectiveness.
Further, by adopting a modern IGA solution, like Zluri, with robust automation, you ensure consistent access controls, minimizing the chances of unauthorized access and data breaches.
Zluri's automation engine effortlessly handles access workflows, ensuring smooth and efficient automation with meticulous reviews while adhering to clear rules and policies.
Zluri's IGA solution simplifies managing user lifecycle while maintaining robust security measures. Onboarding new employees becomes a breeze, granting them easy access to essential applications and resources through automated processes and seamless integration with HR systems.
Your IT teams gain unprecedented efficiency with Zluri, as they can centrally set up user accounts across multiple applications, eliminating errors, reducing administrative burden, and ensuring new employees have the right access from day one.
Even when employees leave the organization, Zluri's automation takes charge. Through automated deprovisioning workflows, it helps your IT teams revoke user access across all applications, minimizing the risk of abandoned accounts and potential security breaches. Zluri empowers your organization with smooth, secure, and hassle-free user access management.
In addition, Zluri offers key unique features that differentiate it from others, ensuring effective access management:
Customizable workflows: With Zluri, you can set up pre-defined workflows tailored to your organization's specific requirements, eliminating the need for manual granting and revoking access permissions. The intuitive interface allows you to customize workflows based on user roles, departments, and seniority levels.
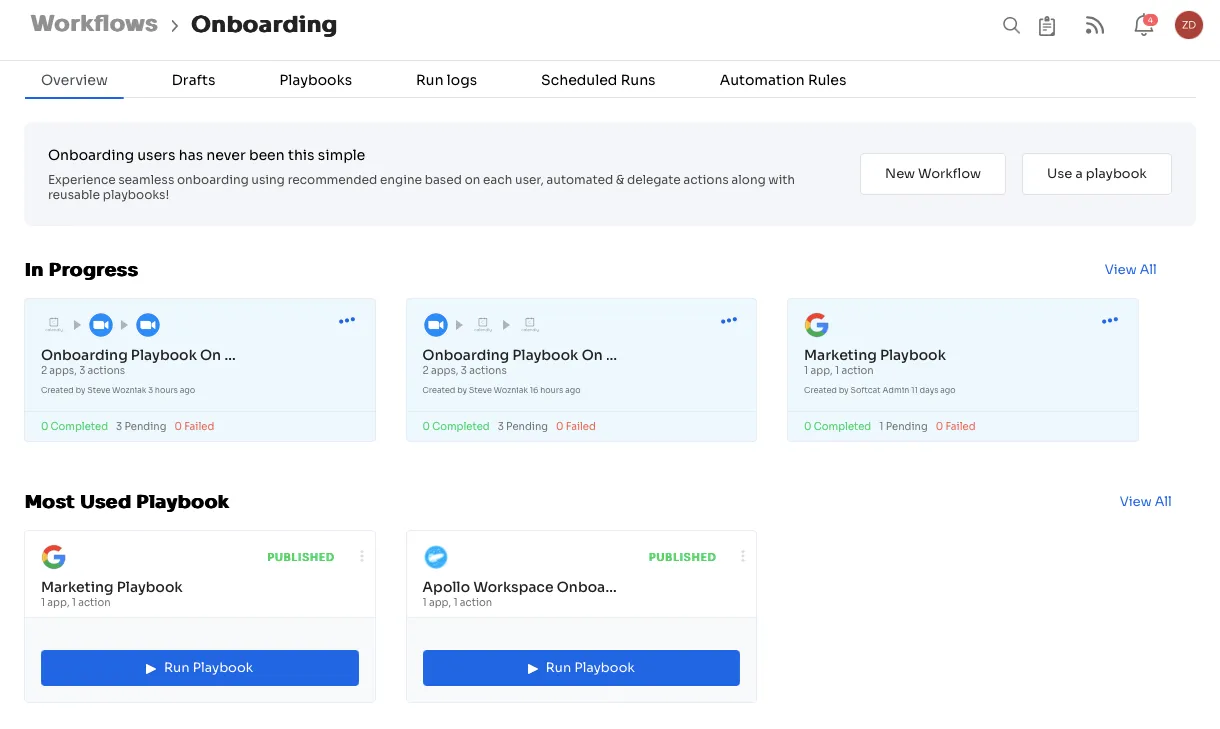
Onboarding

Offboarding
Powerful app recommendations & in-app suggestions: Zluri also provides contextual-based app recommendations based on user profiles, department, seniority level, etc., making it convenient for your team to choose the appropriate apps for provisioning.

Moreover, it offers in-app suggestions to enhance user productivity by recommending required actions for efficient task performance.
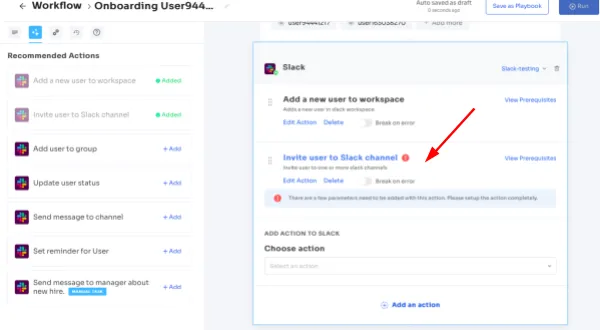
Automation Playbooks: By saving the workflows for both onboarding & offboarding as predefined “playbooks”, Zluri eliminates the need to recreate workflows for each user, further streamlining the process and increasing operational efficiency.
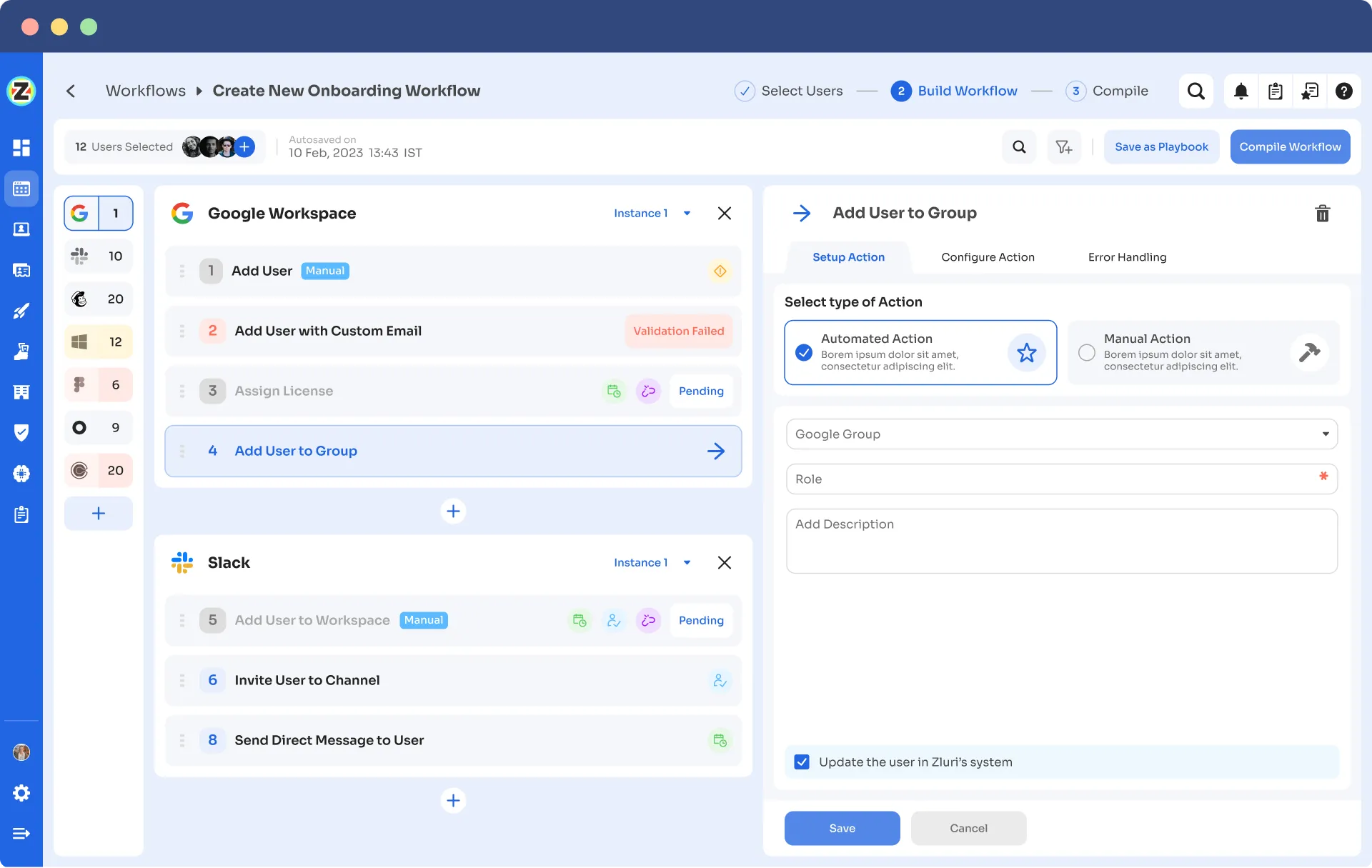
Onboarding Playbooks
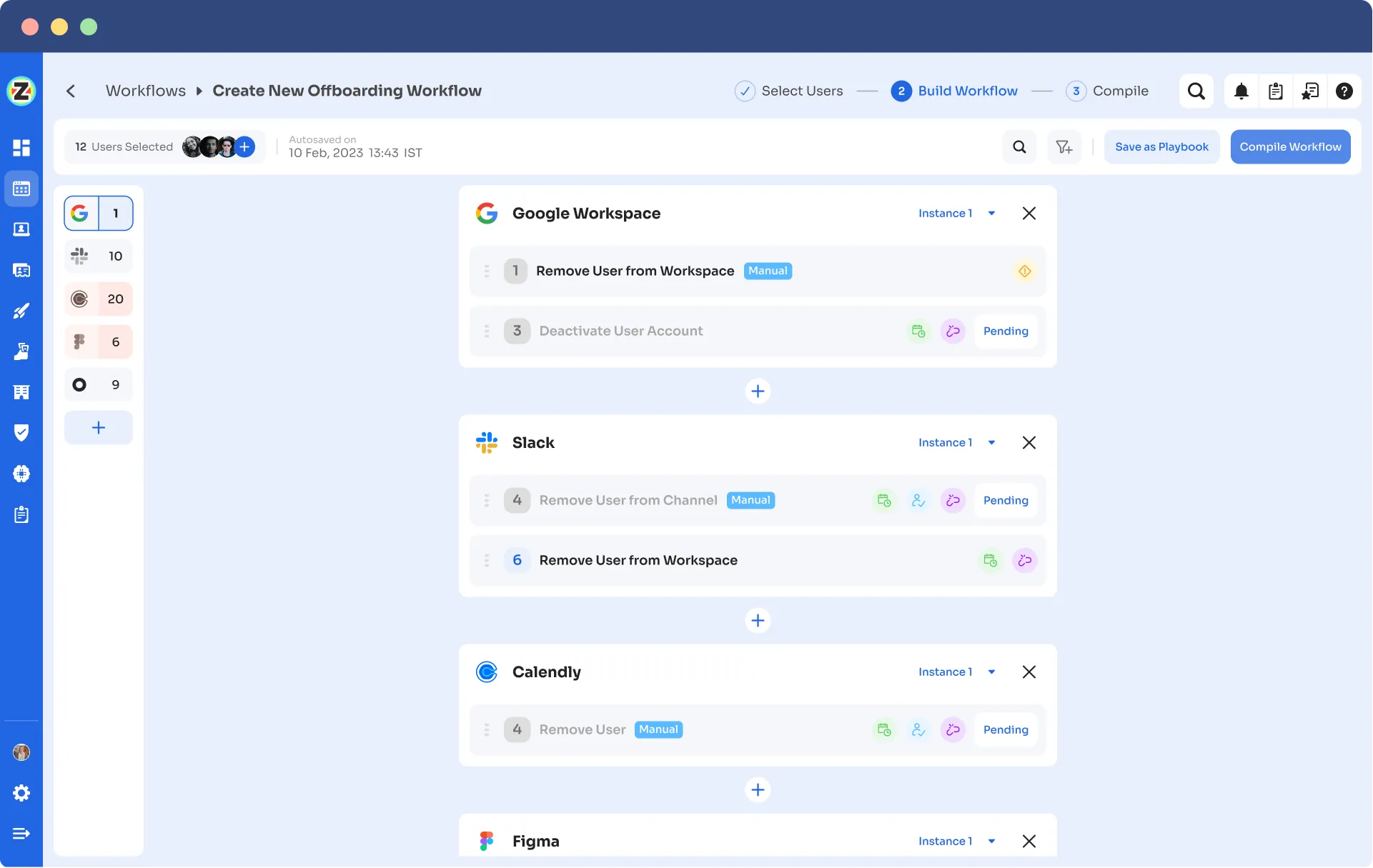
Offboarding Playbooks
Note: These playbooks help your team to ensure security and compliance while provisioning and deprovisioning users’ access even in the future.
3. Does it provide self-service to manage ad-hoc access requests?
One of the most challenging tasks for IT teams is managing ad-hoc access requests. These requests often arise due to midlife cycle changes or transitions within the organization. Dealing with these ad-hoc requests can be a time-consuming and cumbersome process for you.
Without a streamlined system in place, it becomes increasingly difficult to ensure that the right users have the access they need while maintaining security and compliance protocols.
How does Zluri solve this?
Zluri makes it easy for businesses to manage user access during role changes with its self-serve model, called the Employee App Store (EAS). With this powerful feature, your IT team gains control over employees' access to important tools and applications.

Using the EAS, your team or a designated approver can review and approve access requests based on employees' job roles and responsibilities. This ensures that the permissions granted match their specific needs, allowing you to control access and safeguard sensitive information within your organization.
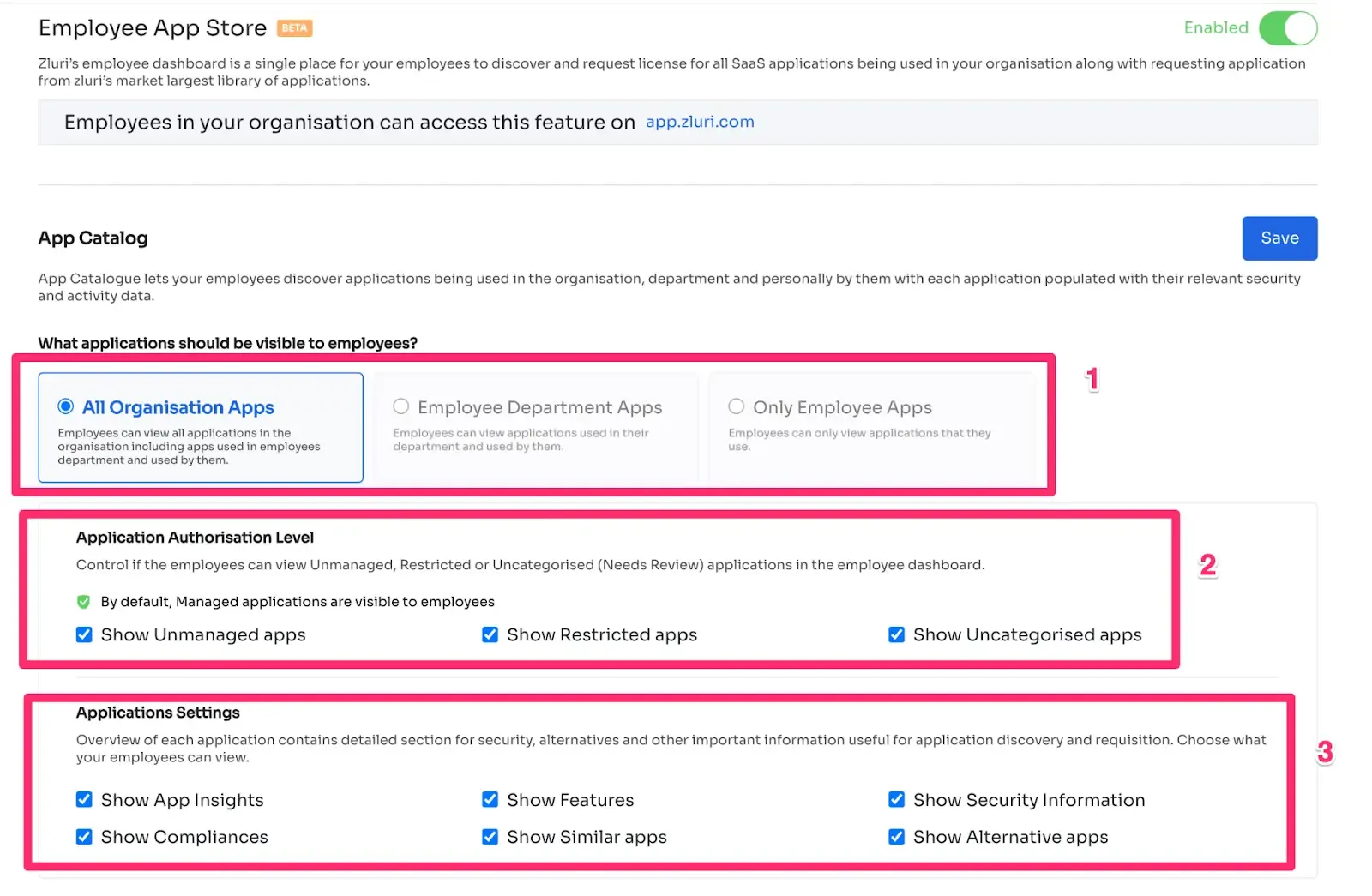
Zluri's transparent approval system consists of three levels: app owners, reporting managers, and IT admins. Higher-level authorities can make decisions that override those made by lower-level admins or managers.
In case an access request is rejected, decision-makers can provide comments explaining the reasons for the rejection. This ensures transparency and clarity throughout the access request process. Approvers also have the flexibility to modify specific requests if needed.
To keep users well-informed, Zluri provides a \"changelog\" feature. This allows users to track updates related to their access requests. For example, they can see if their request was approved or rejected, any license duration or tier changes, and any comments added by an admin. This helps users stay updated and aware of any decisions made regarding their access to applications.
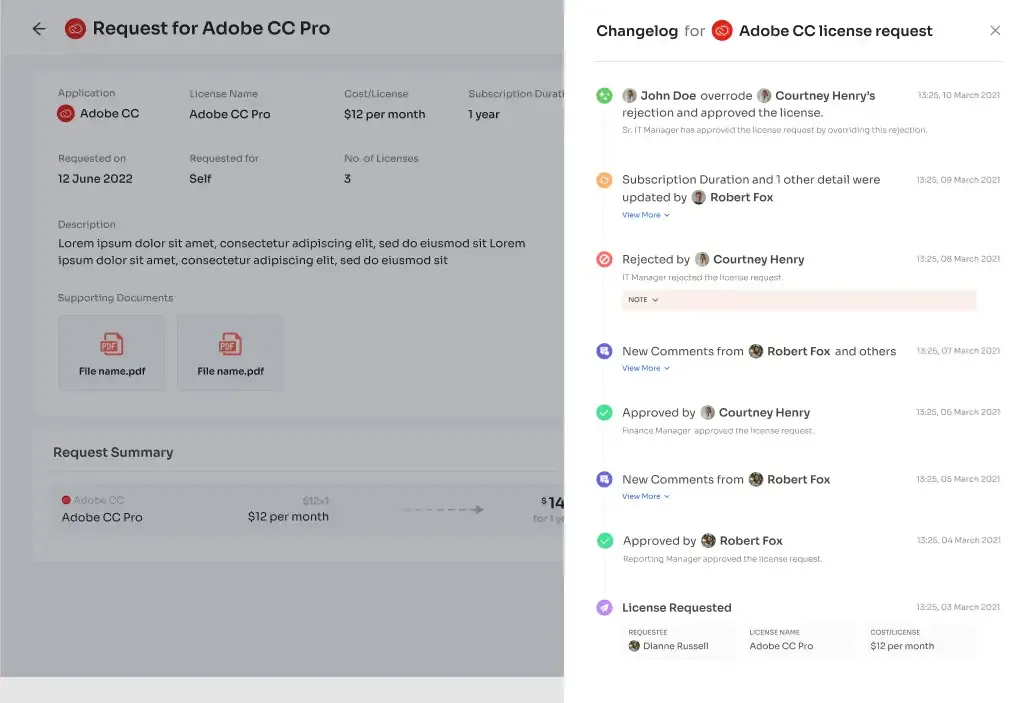
For instance, an employee at your organization requests access to a new project management tool through Zluri's Employee App Store (EAS). The employee’s reporting manager reviews the request, ensures it aligns with the role, and approves it.
Consequently, the EAS updates the changelog for the employee, indicating that the request was approved, and the employee now has access to the project management tool. If, in the future, there's a change in the access, such as a license extension, this information will also be recorded in the changelog, keeping the employee informed about any updates related to the access.
4. Does the tool support automated user access reviews?
Ensuring the security and efficiency of user access within organizations is paramount. For this reason, you need to review and evaluate the users’ access as per your requirements to safeguard sensitive data and prevent unauthorized access.
User access review is a crucial component that allows you to proactively govern user access effectively. It serves as a proactive measure to keep a close eye on the access rights granted to users within the organization. It involves regularly evaluating and verifying the access permissions of each user to various systems, applications, and data.
Traditionally, access reviews were conducted manually, which was time-consuming and prone to human errors. With automation, the IGA solution can automatically trigger periodic access reviews based on predefined schedules or events, reducing the burden on your IT teams and enhancing overall productivity.
Zluri’s IGA solution offers a strong feature for reviewing user access, making it easier for you to manage and evaluate users’ access permissions. This feature helps minimize security risks and gives you better control over user access in your organization.
Let's take a closer look at how it works
- Empower your user’s data with Zluri’s unified access
Zluri simplifies the complex task of managing user access across multiple systems and applications. With Zluri's unified access, your organization can enhance security, streamline operations, and comply with industry regulations.
Unified access provided by Zluri offers the following benefits:
Access Directory: Gain centralized control over your organization's access directory. Easily see who has access to which resources and applications, ensuring a secure environment and preventing unauthorized access. No more struggling with various access lists, permissions, and user roles scattered across different platforms.
For instance, imagine you run a fast-growing tech company with teams spread across different locations. Keeping track of access rights for each employee and department can be overwhelming. Zluri's Access Directory empowers you to effortlessly manage access, giving you peace of mind and ensuring your sensitive data remains protected.
With Zluri, managing user access has never been easier! Say goodbye to access-related headaches and welcome a more efficient, secure, and compliant organization.
Access Privileges: At Zluri, we understand that knowing and managing the access privileges of your users is crucial for effective access control. The platform empowers you to define and monitor user roles, departments, and other relevant information that determines their access privileges. This can include details like job roles, project involvement, or any other contextual data.
With Zluri's granular control, you can ensure that users only have access to the resources necessary for their specific tasks. This minimizes the risk of data breaches and strengthens overall security.
For example, consider a marketing employee responsible for social media management. Using Zluri, you can precisely assign the access they need to perform their job efficiently. They'll have access to all the required social media platforms and marketing tools while being restricted from accessing sensitive areas of your IT infrastructure.
With Zluri, you have the power to manage access privileges effortlessly, promoting a secure and productive work environment for your organization.
Activity & Alerts: With Zluri, you can effortlessly access valuable information about user actions, such as their recent login/logout times for various applications. This visibility allows you to monitor user behavior closely and quickly detect any suspicious activities that might indicate potential security threats.
Additionally, Zluri provides a proactive alerting system that works in real-time. You'll receive instant email alerts whenever unusual activities or possible security breaches occur. This proactive approach empowers you to take swift action, minimizing the impact of security incidents and ensuring the overall safety of your IT environment.
With Zluri's user activity insights and proactive alerts, you can stay ahead of security challenges and safeguard your organization's sensitive data effectively.
- Streamline your access review process with automation
With Zluri, you have the power to effortlessly manage access control and protect your valuable data. The automated reviews feature ensures top-notch security while keeping you compliant with regulations. Zluri’s automated reviews capabilities include:
Access Rules: With Zluri's access insights, you gain a comprehensive understanding of your organization's access landscape. These insights serve as the foundation for creating precise access rules.
Example: Let's say you discover that some employees have access to confidential files they don't need. With Zluri, you can quickly set up rules to limit their permissions and enhance data security.
Scheduled Certification: With Zluri, certification becomes a breeze as you can proactively schedule the process. After gaining valuable insights, take action by setting up certification tasks.
These certifications make sure that employees' access aligns with your organization's policies and regulations. By scheduling certifications, you ensure that access permissions are always up-to-date and compliant.
Auto-remediation: Zluri takes access management to the next level with its incredible auto-remediation capabilities. This powerful feature goes beyond simple reviews and takes immediate action when it detects any unauthorized access or potential security breaches. By automatically triggering corrective actions, Zluri ensures your organization's security is always top-notch and compliant with industry standards.
Example: Let's say a team member in your finance department changes their role within the company. With Zluri, adjusting their access privileges becomes a breeze. You can effortlessly modify their access rights to match their new responsibilities, whether they get promoted or switch roles.
Likewise, if a user has unnecessary access, Zluri can quickly revoke it through auto-remediation, minimizing any potential security risks.
In short, manual access reviews can be time-consuming and labor-intensive, involving coordination between different departments and cross-referencing access permissions. These tasks are prone to errors, which could lead to compliance problems or security vulnerabilities.
But with Zluri's automated reviews, you can say goodbye to these challenges. The intelligent automation streamlines the process, reducing manual efforts by up to 70% and making the review process 10 times faster. Zluri collects, organizes, and analyzes access data, freeing up your IT team to focus on more strategic tasks.
Now, let’s discuss the steps to automate the access review process.
- Step 1: Open Zluri's main interface and go to the \"Access Certification\" module.
- Step 2: Now, to create an access certification, click on \"Create a New Certification.\" Now, assign a suitable certification name and assign a responsive owner.
- Step 3: Under the setup certification, choose how you want to review users' access: either by Application or Users.
For example, if you select to review access by Application, add the application to audit users' access.
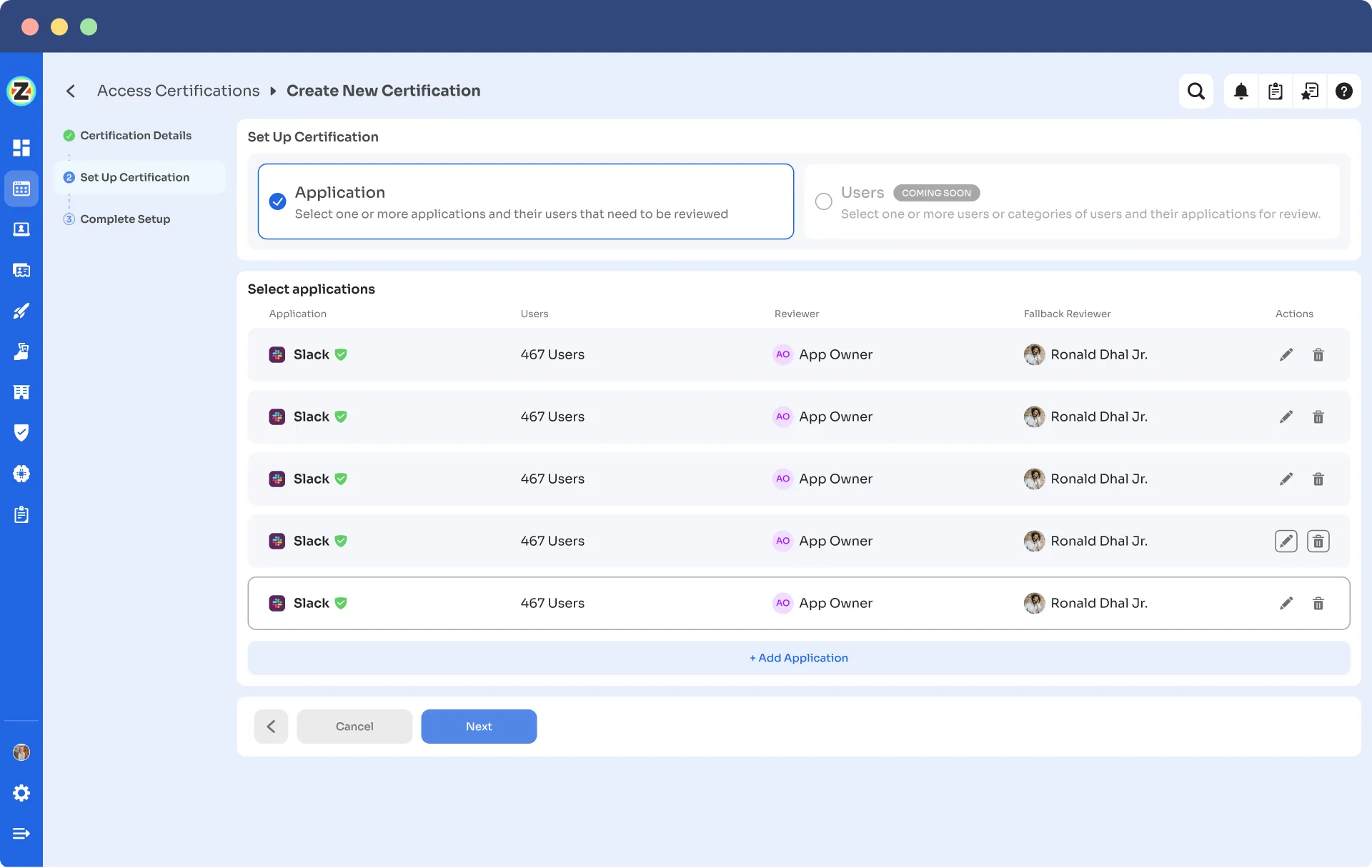
- Step 4: Then choose a primary reviewer and a fallback reviewer from the drop-down menu. Once you are done selecting the reviewers, you can click on Next.
Note: Generally, the primary reviewers are app owners. Also, choose the fallback reviewer carefully whom you think is responsible.
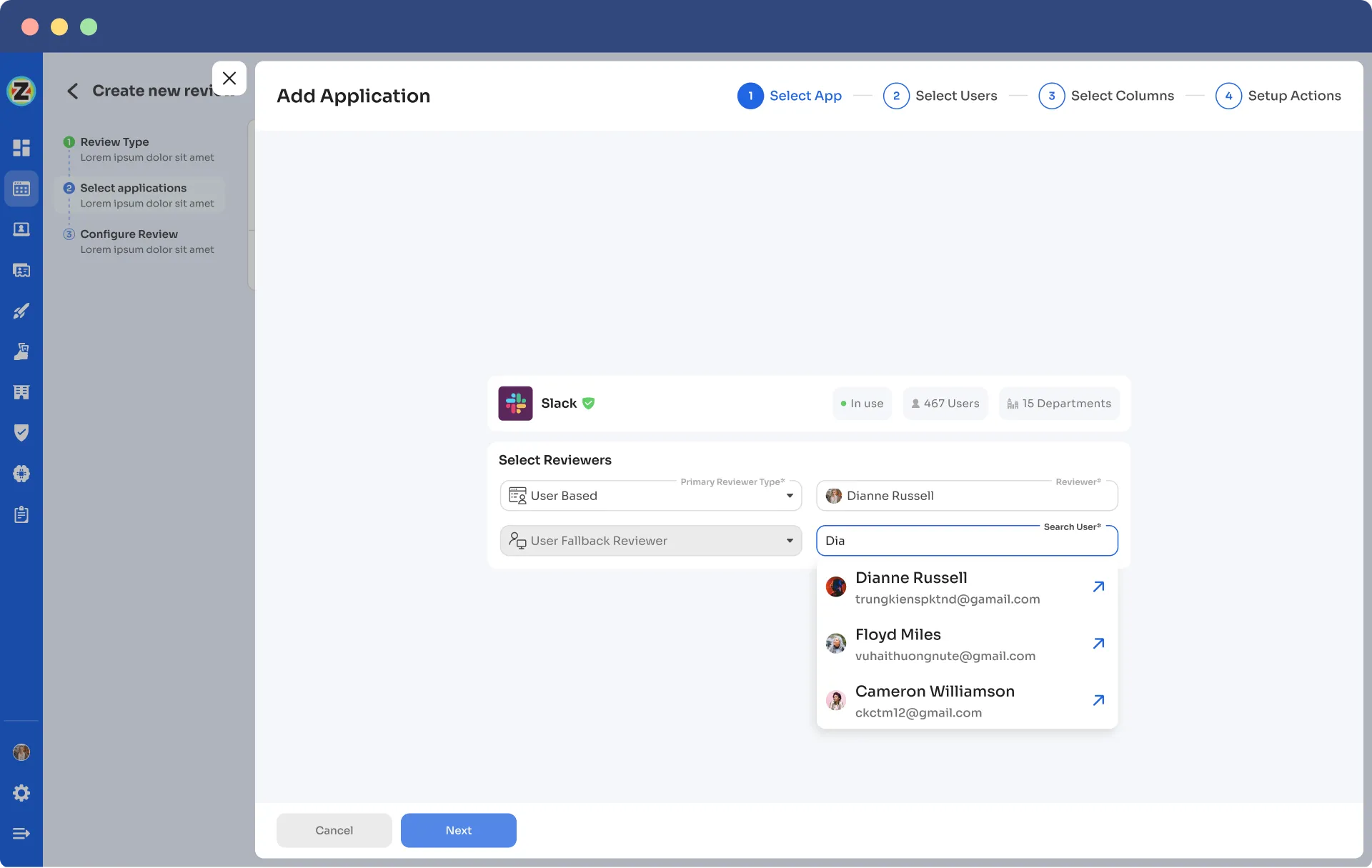
- Step 5: Choose the specific users to include in the certification process. You can also filter the data points such as user department, job title, usage, and more, as per your certification requirements. Then, click on \"Next.\"
Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
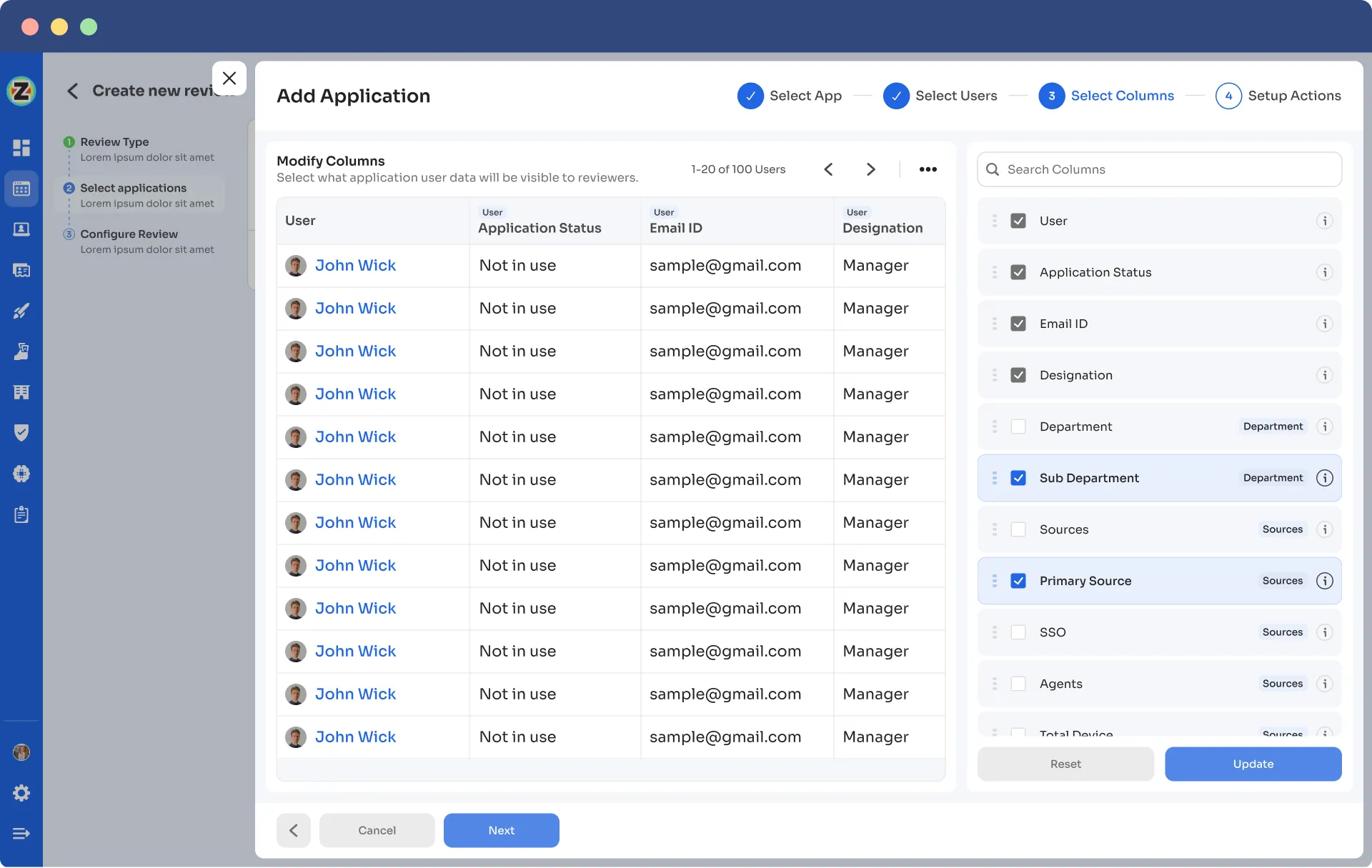
- Step 6: Configure actions based on your needs and choose from the drop-down options.
For example, for rejection action, you can select the respective deprovisioning playbook to revoke the unnecessary access of the users.
Once you set up the action, click “add applications”.
Note: You can add multiple applications for the same certification.
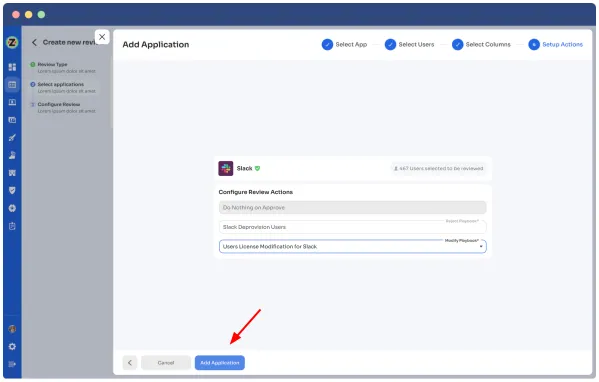
- Step 7: Set the start and end dates for the certification process, depending on the time span you want the review completed.
Note: You can also click on \"Save Template\" to save it for future use.
- Step 8: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and viewing whether the review is still pending, modified, declined, or approved.
5. How robust are the reporting capabilities of the tool?
As an IT manager, one of your key responsibilities is to ensure the security and compliance of your organization's digital assets. This means overseeing users' access to critical systems and data. In this complex task, having comprehensive reports within an IGA tool is of utmost importance.
The reports provide valuable insights into who has access to what systems and data, allowing you to keep a close eye on potential security risks. By understanding the access privileges of each user, you can detect any suspicious activities or unauthorized access attempts promptly.
In addition, comprehensive reports are equally vital for management and auditors. With these reports, they can gain a clear overview of your organization's access policies and identify areas that may need improvement.
The reports offer data-driven evidence to evaluate the effectiveness of access control mechanisms and assess whether they align with your organization's security and compliance objectives. As a result, management and auditors can make informed decisions about access policies, streamline processes, and allocate resources efficiently.
Zluri generates comprehensive audit reports that provide valuable insights into access patterns, vulnerabilities, and compliance status. These reports make it easy to demonstrate compliance to auditors and make informed decisions about access management.

In Zluri’s access certification, once the review is completed and the assigned reviewer approves, rejects, or modifies it, you can simply conclude the review to send the reports through email instantly.
6. Does the tool support your required compliance frameworks?
A reliable IGA tool must support your required compliance frameworks to ensure your organization meets all the necessary regulatory standards and data protection requirements. It will help you maintain compliance with industry-specific regulations, such as GDPR, HIPAA, PCI DSS, SOX, and more, depending on your business's nature.
Moreover, aligning your IGA tool with compliance frameworks helps maintain data integrity and confidentiality. The tool enables you to set up segregation of duties and role-based access controls, ensuring that users are granted appropriate access based on their job responsibilities. This prevents data leakage and minimizes the potential for internal fraud.
Zluri is your trusted partner in navigating the complexities of compliance frameworks. By centralizing and automating the user access review process, the IGA platform empowers you to efficiently stay on top of the organization's compliance requirements. With Zluri, you can ensure that your organization remains compliant, avoids costly penalties, and maintains a strong reputation in the market.

With Zluri by your side, navigating compliance frameworks becomes a breeze, allowing you to confidently focus on your business's success. Schedule your FREE personalized demo.







.png)

.svg)














