Proper user provisioning is critical for organizations to ensure that employees have access to systems and applications they need to do their jobs effectively while protecting sensitive data.
However, many organizations make mistakes when it comes to user provisioning, which can lead to serious consequences.
Imagine this scenario: you're an IT admin responsible for setting up new employees at a large company. But when new employees sit at their computer, you realize they don't have access to SaaS applications they will need to handle their daily responsibilities.
They cannot receive daily updates as they don't have access to the productivity tracker SaaS application. This causes a delay in their work and can be a frustrating experience for a new employee.
This is where user provisioning can help.
It is all about ensuring that the right people have access to the right resources at the right time. But when IT teams make mistakes in this process, it can lead to risks like data breaches, productivity, or even legal issues.
An example of this is that access is not being revoked on time when it's no longer needed. Granting employees access to systems and applications that they don't need increases the risk of unintentional or intentional access to sensitive information, which can lead to security breaches.
This is why IT teams must balance two critical objectives of user provisioning. First, they must provide users with access to the systems and applications necessary to perform their job duties efficiently. Second, they must prevent unauthorized access to sensitive information.
While balancing these two tasks, IT teams can make several mistakes in the user provisioning process that can impact the organization's security posture and operational efficiency.
Let's explore these:
Top User Provisioning Mistakes to Avoid
Here are some of the top user provisioning mistakes to avoid:
1. Lack of automation
As companies grow, managing user access can become an increasingly complex and daunting task. This is especially true when relying on manual provisioning processes, which are labor-intensive and prone to errors.
Manual user provisioning increases the risk of human error, leading to inconsistencies and potential security vulnerabilities. This risks the company's valuable assets and can impact the bottom line through lost productivity and resources.
Moreover, manual provisioning can be a bottleneck, slowing down the onboarding process for new employees, contractors, and partners.
Fortunately, the automated provisioning process can streamline user provisioning, from account creation to access management. By leveraging automation, IT admins can significantly reduce the likelihood of errors, enhance consistency, and improve overall security posture.
Automated provisioning can also provide a more efficient and scalable approach to managing user access. With automation, IT teams can quickly provision, deprovision, and modify user access across various systems and applications, all from a centralized location.
This means that IT teams can focus on higher-value tasks, such as enhancing security measures and driving innovation, rather than spending time on manual administrative tasks. Not just that, by adopting automated provisioning, companies can future-proof their identity and access management processes, ensure compliance, and gain a competitive advantage.
Read more on the topic: top user provisioning tools.
2. Over-provisioning or under-provisioning
As businesses continue to adopt digital transformation initiatives, managing user privileges becomes increasingly crucial to safeguard sensitive data and ensure optimal productivity.
However, a common mistake numerous IT admins make is granting excessive or inadequate user privileges, which can have significant repercussions.
Over-provisioning user privileges, or granting access beyond the required level, can expose an organization to potential data breaches and other security incidents. For example, this can occur when employees have access to sensitive information that they do not require to perform their job functions or when user accounts are left open and vulnerable to external attacks.
In addition, over-provisioning can result in compliance issues, as certain regulations require businesses to limit access to specific data based on the user's role or the need to know.
On the other hand, under-provisioning user privileges, or limiting access more than necessary, can negatively impact productivity and create frustration for users. In addition, when employees cannot access the tools and information needed to perform their job functions, they may resort to inefficient workarounds or seek shadow apps that can further compromise data security.
To strike the right balance, IT teams should implement a comprehensive identity and access management (IAM) strategy. These strategies can help IT admin enforce access policies and automate user provisioning and deprovisioning processes, reducing the risk of human error.
In addition to IAM, IT professionals should also consider implementing other security measures, such as multi-factor authentication, encryption, and employee training programs. They can mitigate risks, increase productivity, and maintain regulatory compliance by taking a holistic approach to security and balancing user access with data protection.
3. Insufficient authentication in place
User provisioning can work only if a company has a strong authentication system.
As businesses continue to digitize their operations and store more data electronically, ensuring strong authentication measures is more important than ever.
Weak passwords, outdated authentication protocols, and inadequate access controls can all result in unauthorized access, data breaches, and other security incidents.
It's critical to recognize the importance of strong authentication and authorization practices and take steps to protect your organization's data. One of the most effective ways to improve authentication and authorization is through multi-factor authentication (MFA).
- MFA adds an additional layer of security beyond a password, requiring users to provide multiple verification forms before granting access. This could be a fingerprint or facial recognition scan in addition to a password, making it much more difficult for unauthorized individuals to gain access.
- In addition to MFA, implementing access control policies can help to manage user privileges and reduce the risk of security incidents. Access control policies involve assigning specific levels of access based on a user's role and then monitoring and enforcing these policies to ensure that only authorized users have access to sensitive data.
- Regular security awareness training for users is another crucial aspect of authentication and authorization. Educating employees on best practices for password management, phishing attacks, and other security threats IT department can help reduce the likelihood of human error and improve overall security posture.
- It's also important to stay up-to-date with the latest authentication and authorization protocols to ensure that your organization uses the most secure methods. As technology evolves, new threats and vulnerabilities may emerge, making it critical to stay vigilant and proactive in implementing security measures.
By taking a comprehensive approach to authentication and authorization, IT teams can reduce the risk of security incidents and protect sensitive data. Implementing MFA, access control policies, and security awareness training are all critical steps in improving authentication and authorization practices and safeguarding your organization against potential threats.
4. Lack of review & audit
IT professionals today face a constantly evolving threat landscape, making it imperative to maintain a proactive approach to cybersecurity. Yet, one common mistake that many organizations make is failing to conduct regular reviews and audits of user access privileges.
With regular reviews, organizations may notice changes in user roles and responsibilities, leading to consistency and security vulnerabilities. This can result in the improper assignment of user privileges, leading to data breaches and other security incidents.
User access privileges are critical to maintaining the security and compliance of an organization's data. Failing to review these privileges can result in compliance issues, as certain regulations require businesses to limit access to specific data based on the user's role or need to know.
Regular auditing of user access privileges can help to identify and remediate vulnerabilities promptly, reducing the risk of security incidents. In addition, by regularly reviewing user access privileges, IT teams can ensure that only authorized users can access sensitive data, reducing the likelihood of data breaches and other security incidents.
Furthermore, regular audits can help identify unused or dormant accounts that hackers can exploit to gain unauthorized access to sensitive data. To boil it down, regular reviews and audits of user access privileges are critical to maintaining a secure and compliant environment.
5. Lack of role-based access control (RBAC)
Managing user access privileges is critical to ensuring security and efficiency in IT operations. However, IT professionals struggle with managing user access effectively, leading to inconsistent and inefficient access management that can put the company at risk.
One way to address this issue is by adopting a role-based access control (RBAC) system.
For example- A technology firm might use RBAC to control access to its intellectual property among its employees, partners, and vendors.
The company might grant access to certain software codes and development resources based on employees' roles within the company, such as software engineers or project managers. Partners or vendors may also be granted access to specific resources based on their contractual obligations and job functions, such as marketing or sales personnel.
If the company fails to adopt RBAC, it could lead to unauthorized access to critical information, such as trade secrets or confidential client data, which could result in loss of revenue, damage to reputation, or legal issues.\"
RBAC is a method of access control that assigns user access based on roles and responsibilities, ensuring that users have the necessary access to perform their job functions while minimizing the risk of unauthorized access.
By adopting an RBAC system, IT admins can streamline the management of user access privileges and reduce the risk of data breaches and other security incidents.
The benefits of RBAC extend beyond security. By assigning access based on roles, RBAC can also improve efficiency by reducing the time and resources required for manual access management. This can help improve employee productivity and reduce the likelihood of errors that can occur with manual access management.
RBAC is also critical for compliance with regulations that require organizations to limit access to sensitive data based on roles and responsibilities. By adopting RBAC, admins can ensure they meet these requirements and reduce the risk of non-compliance penalties.
Wondering what might help avoid the above mishaps?
A cloud-based ULM software like Zluri can help IT teams avoid user provisioning mishaps by providing a more efficient and effective way to manage user identities, access permissions, and roles across multiple IT systems and platforms.
How Zluri Helps Avoid User Provisioning Mishaps
Zluri is a cloud-based lifecycle management solution that offers a streamlined onboarding process. It allows IT professionals to create workflows that automate the onboarding process, enabling them to quickly provision access to necessary software, systems, and training materials.
One of the key benefits of Zluri is its flexibility. IT admins can easily add multiple users and various apps to a workflow and customize actions that need to be taken for each user or app. In addition, these workflows can be executed immediately or saved as a playbook for future use and can be modified or removed per the organization's changing needs.

This feature helps create custom workflows for different roles and departments, ensuring new hires can access the necessary applications and tools to perform their duties.

Another helpful feature of Zluri is its contextual app recommendation and in-app suggestion functionality.
Zluri's app recommendations feature sets it apart from other providers by enabling IT admins to provide application access to employees before they even join the organization, based on their department and role. This results in increased productivity and an improved overall onboarding experience.

Additionally, Zluri's in-app suggestion feature makes it easy for IT admins to add new hires to relevant communication channels or groups, such as Slack, while simultaneously granting access to these tools. These features not only streamline the onboarding process but also help reduce the workload of IT admins.
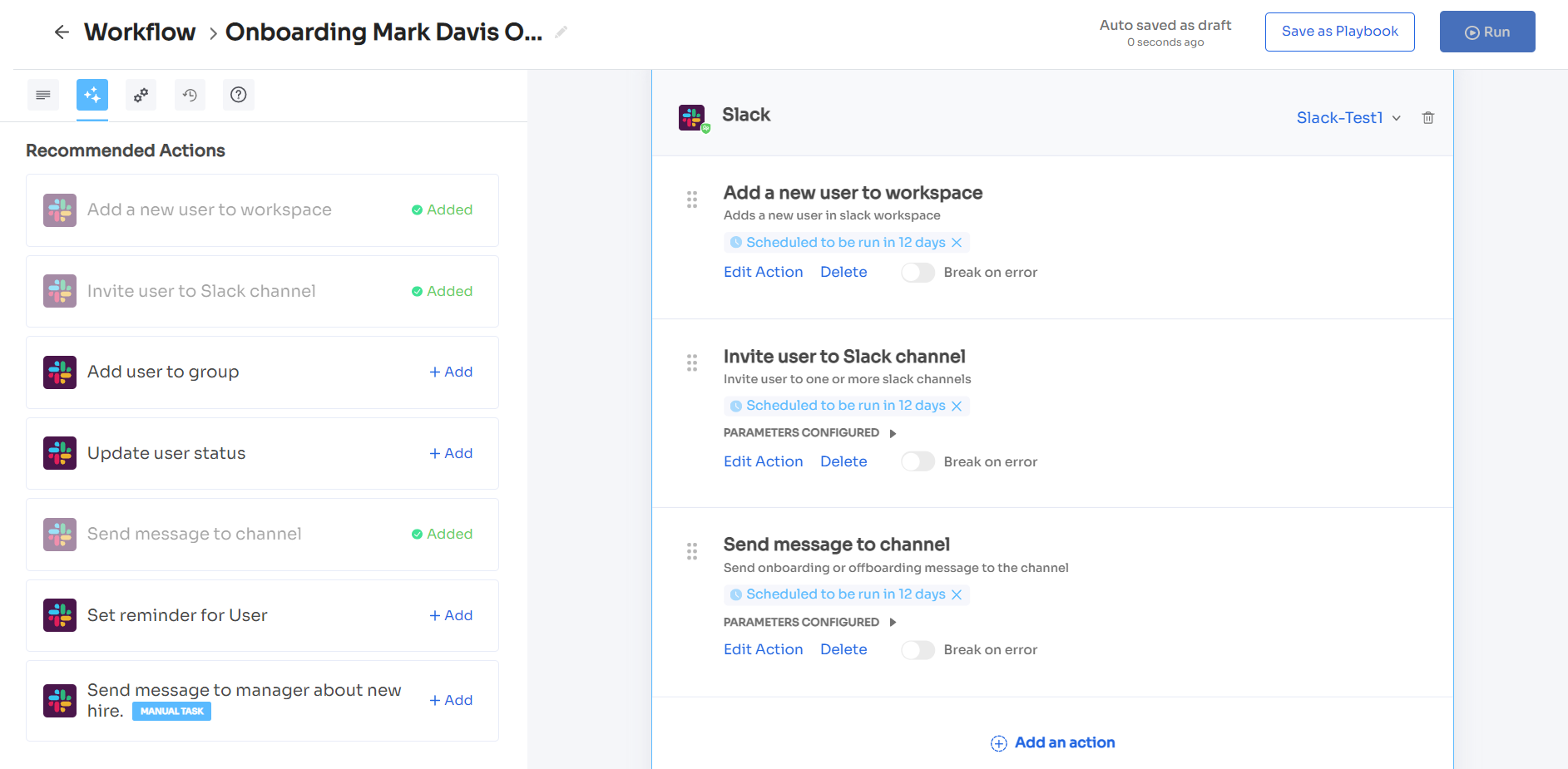
Zluri enables IT teams to automate the complete onboarding process by setting rules and conditions, further reducing the risk of errors and enhancing security and compliance.

Zluri's role-based access control (RBAC) feature can help IT professionals in organizations to mitigate user provisioning mistakes. It enables IT admins to grant access based on user roles and responsibilities, ensuring that users have access only to the resources they need to do their jobs.
This helps implement a least-privilege access model and reduces the risk of over-provisioning or under-provisioning.
In addition to RBAC, Zluri also provides user activity monitoring features that help detect and prevent security breaches. For example, Zluri enables IT teams to audit user access to sensitive resources and detect suspicious activity, which is essential for maintaining compliance and security.
Take a look at what our customers have to say about us:

Zluri is a powerful solution that helps avoid user provisioning mistakes, ensures compliance and security, and improves efficiency and user experience.
So what are you waiting for? Book a demo and try it out yourself today!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)