Access reviews catch problems. Access management fixes processes. In most organizations, these two activities never talk to each other.
That disconnect creates predictable failure. You review the same problems every quarter. Your workflows drift further from reality every month. Your governance becomes fiction.
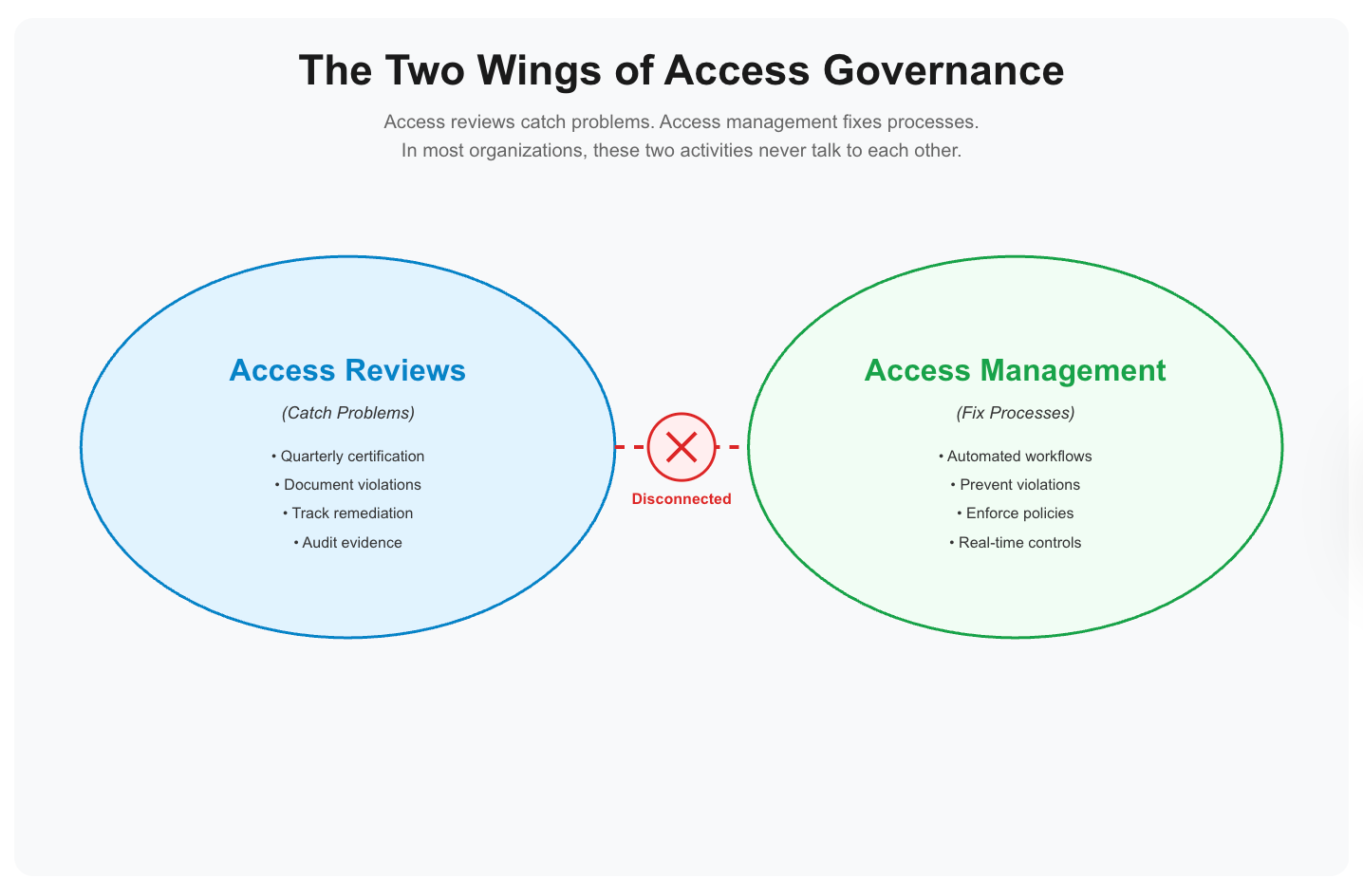
The fix isn't better reviews or better management—it's connecting them.
Access reviews and access management are two wings of the same bird. Try to fly with just one, and you're going in circles.
The One-Wing Problem: When Reviews and Management Work in Isolation
Reviews without management equals firefighting that never ends
You run quarterly access reviews. Bob still has Salesforce admin from that project eight months ago. Revoked. Sarah kept contractor-level GitHub access after her conversion to FTE. Revoked. The contractor who left in June? Still provisioned in Figma, Notion, and Slack.
Next quarter, same story. Different names, identical problems.
You're correcting provisioning mistakes, not fixing the provisioning process. Every review generates a cleanup list. Nothing changes upstream. Your audit trail looks great. Your actual access posture doesn't improve.
You're generating audit trails but not governance.
Here's the pattern that emerges. Quarterly reviews become predictable. You know before you start that you'll find over-provisioned contractors. You know former employees will still have access somewhere. You know department transfers will have zombie accounts in their old team's systems.
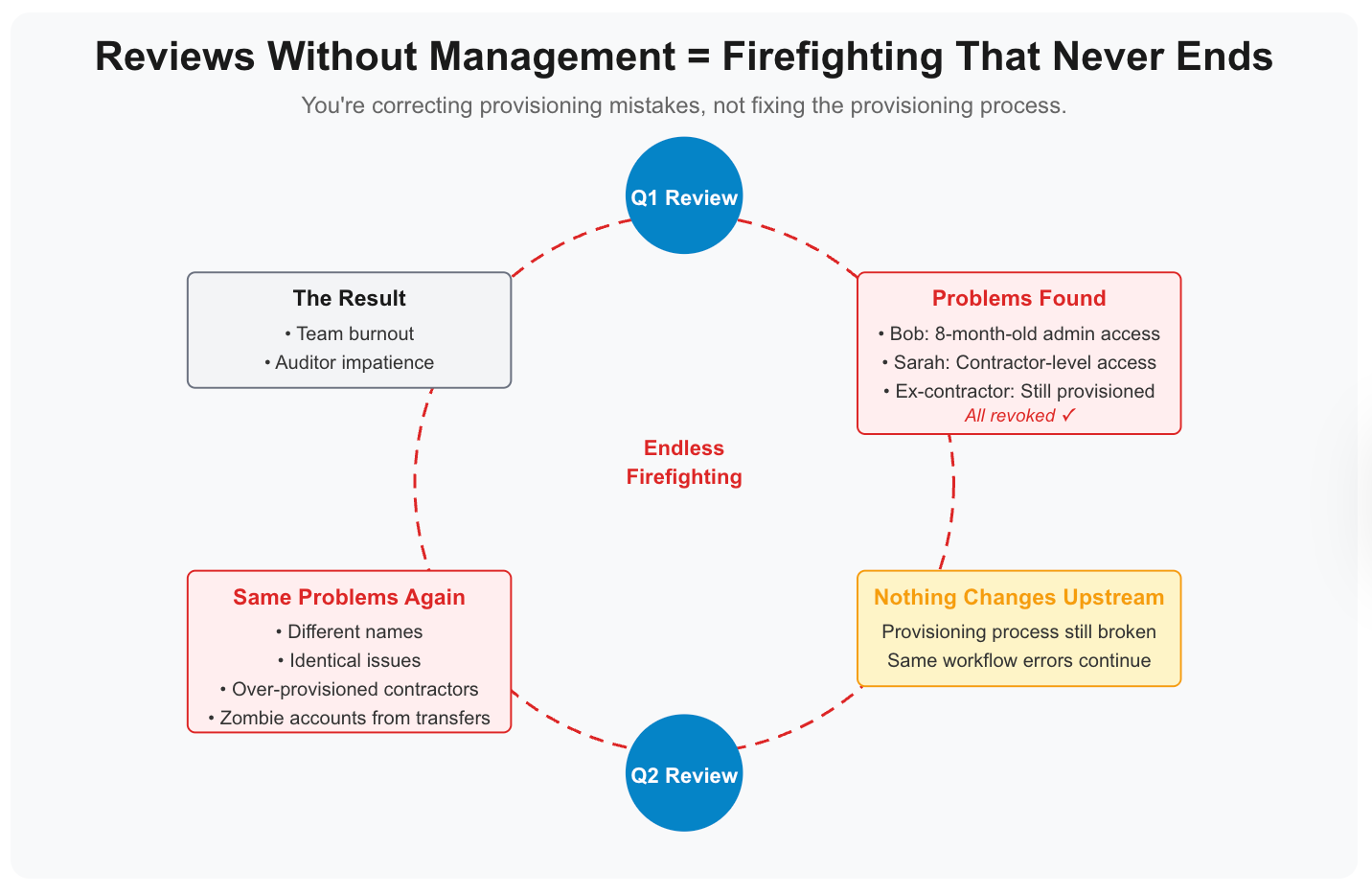
The problems are so consistent you could write the findings before conducting the review. That predictability isn't evidence of good governance. It's evidence that your provisioning workflows are systematically broken, and reviews aren't fixing them.
Your team burns out. Reviewing the same failures every quarter is demoralizing. Your auditors lose patience. They start asking why these findings persist. You have no good answer except "we're working on it," which you've been saying for three quarters.
Management without reviews equals controlled drift
You build RBAC policies. Automate provisioning workflows. Document everything. It's elegant.
Then reality hits. The "Marketing Contractor" role now means five different things across three departments. Nobody can explain why Sales has admin access to the data warehouse—but they do, and they need it, apparently. Your beautiful policies have 47 manual exceptions you've stopped tracking.
You have no feedback loop. No way to know if policies work. No signal that your governance model detached from actual access patterns six months ago.
The drift happens slowly. One exception becomes an acceptable precedent. That precedent becomes standard practice. Standard practice becomes undocumented policy. Before you notice, your actual access model bears no resemblance to your documented RBAC structure.
Your automated workflows execute perfectly, provisioning exactly what your policies specify. Unfortunately, your policies specify the wrong things. Nobody realizes because nobody's checking whether the policies still match how the organization actually works.

By the time you realize your offboarding workflow has been failing for six months, dozens of former employees still have active access. You're operating on assumptions that expired months ago.
These patterns aren't accidents. They're symptoms of a deeper structural problem.
Why This Happens (Organizational Silos and Misaligned Metrics)
Most organizations treat reviews and management as separate projects:
- Reviews live in the compliance team's calendar
- Management lives in IT's provisioning queue
They never talk to each other.
Reviews identify problems. Management fixes processes. But the problems reviews find never become inputs to the processes management builds. And the processes management builds never get validated by what reviews discover.
So you're stuck. Reviewing the same mistakes. Managing based on assumptions that expired last year.
The organizational split makes this worse. Compliance teams run reviews to satisfy auditors. They care about documentation, attestation, and evidence trails. IT teams build provisioning automation to reduce support tickets. They care about efficiency, workflow completion, and request velocity.
Neither team is measured on whether reviews and management actually improve access posture. Compliance gets measured on audit pass rates. IT gets measured on ticket resolution time. The metrics don't incentivize collaboration.
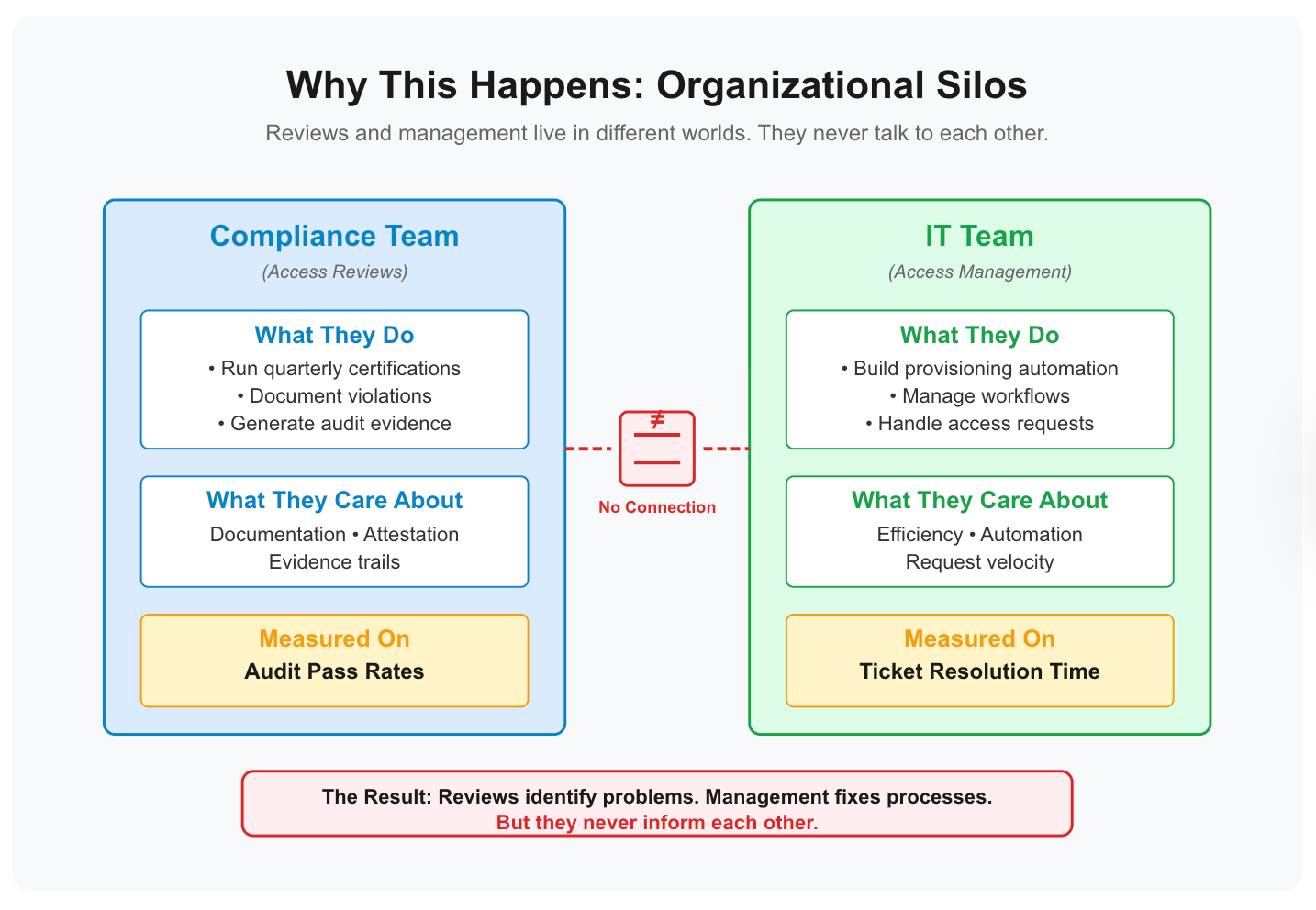
This disconnect persists even when one team handles both. In many mid-market organizations (500-5000 employees), there is no separate compliance or GRC team. IT owns both access reviews and provisioning workflows. But they still treat them as separate work streams. The findings from reviews don't inform how workflows get built. The failures in workflows don't trigger review process changes. Same team, same disconnect.
Even worse, the tools don't connect. Your access review platform exports remediation tasks into spreadsheets. IT manually translates those into provisioning changes. By the time those changes deploy, the next review cycle has started. The feedback loop takes three months minimum.
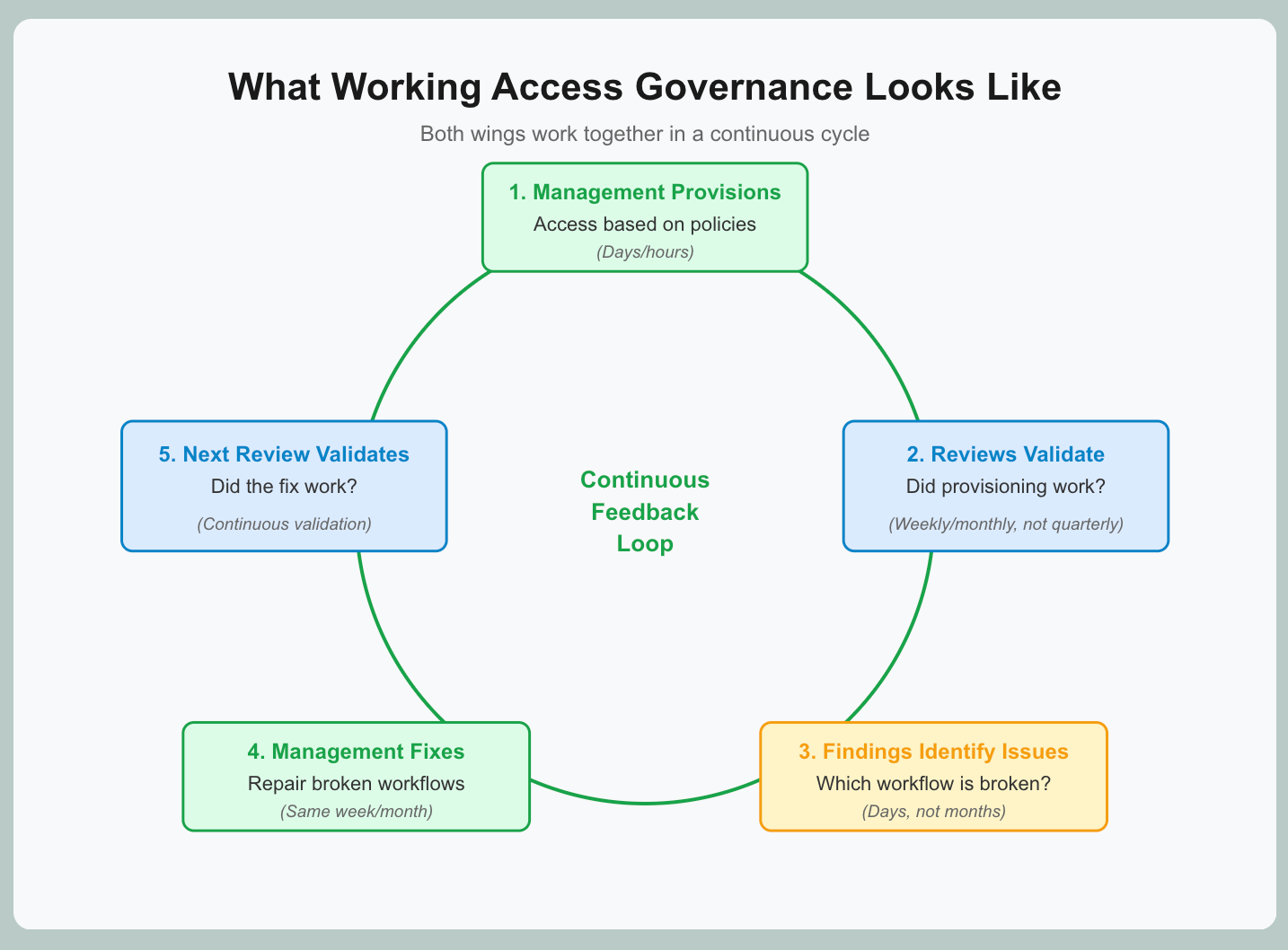
What Working Access Governance Looks Like (Reviews Inform Management, Management Validates Through Reviews)
Both wings work together in a continuous cycle:
Reviews inform management. When quarterly reviews consistently flag the same access patterns as wrong, that's not a review problem—it's a signal to fix the provisioning workflow. If every review finds ex-contractors still provisioned, your offboarding process is broken. Fix that, not just the access.
This means treating review findings as process telemetry, not one-time corrections. If 80% of inappropriate access comes from one broken workflow, that workflow needs fixing. If role assignments keep diverging from policy, your roles don't match reality.
The question every review should answer: which upstream process created this problem?
Management validates through reviews. When your RBAC policies generate exceptions that reviews rubber-stamp every quarter, your policies are wrong. The exceptions are telling you something. Listen.
Reviews reveal whether your automated workflows did what they were supposed to do. Did that offboarding workflow revoke access everywhere? Did that contractor role provision the right permissions? Did the department transfer remove old team access?
If reviews consistently find gaps, your workflows are failing. Automation that consistently produces incorrect results isn't automation worth keeping.
The continuous feedback loop. Access governance isn't quarterly events. It's continuous validation:
Reviews run continuously (weekly for high-risk access, monthly for standard reviews) instead of quarterly marathons. When a contractor's access expires, automated validation checks within 24 hours whether deprovisioning completed everywhere. When roles change, validation runs immediately to confirm old permissions were revoked.
Management responds to review findings within days, not months. If weekly reviews show offboarding gaps, IT investigates the workflow that week. If monthly reviews find persistent role drift, policies get updated that month.
This creates a tight cycle:
- Management provisions access based on policies
- Reviews validate that provisioning worked correctly
- Review findings identify broken workflows
- Management fixes those workflows
- Next review validates the fixes worked
Stop any one activity, and the cycle breaks.
How Reviews Should Inform Management (Turning Review Findings Into Workflow Fixes)
Here's what this looks like in practice:
Pattern recognition from review findings. Run monthly reviews for three months. Every review finds that support contractors accumulate admin permissions they don't need. The pattern is consistent: contractors start with viewer access, get temporary admin for one ticket, admin access never gets revoked.
Most teams revoke the admin access, check the box, and move on.
But when reviews inform management, you see something different: the provisioning workflow for temporary access is broken. It grants permissions but doesn't revoke them. Fix the workflow to auto-expire temporary permissions after 48 hours. Add automated validation that checks whether revocation occurred.
Next month's review validates the fix worked. If it didn't, you iterate. If it did, that entire category of findings disappears from future reviews.
Workflow failure signals. Department transfers consistently create zombie access. Employees move from Sales to Marketing but keep full Salesforce admin from their old role. Every quarterly review finds 10-15 cases.
The typical response is to revoke the orphaned access and document the finding.
When reviews inform management, you identify the root cause: the transfer workflow doesn't include access reconciliation. Build a transfer checklist that identifies old department access and triggers deprovisioning. Automate validation that runs when HR marks a transfer complete.
The review finding becomes a workflow improvement project, not a recurring cleanup task.
Exception analysis. Your RBAC policy says contractors get viewer access to the codebase. But reviews show 40% of contractor approvals include manual exceptions granting write access. Those exceptions always get approved.
Most organizations accept the exceptions because the business needs them.
When reviews inform management, you see the real problem: your contractor role definition is wrong. If 40% of cases need exceptions, the baseline is too restrictive. Redefine contractor roles to match actual needs. Maybe you need "Contractor - Developer" with write access and "Contractor - QA" with viewer access.
Reviews reveal when policies don't match operational reality. Management fixes the policies.
How Management Should Validate Through Reviews (Using Reviews to Catch Provisioning Failures)
The opposite direction is equally critical:
Automated workflow validation. You build automated provisioning for new hires. Day 1: SSO account, email, Slack. Day 2: Department-specific tools based on role. Day 7: Manager receives confirmation.
Without reviews, you assume it works. With reviews: Run weekly validation on all new hires from the past 30 days. Check whether they have the access their role requires. Check whether they have access they shouldn't.
If the workflow consistently fails to provision Jira for engineers, fix it. If it over-provisions Salesforce admin instead of viewer, fix it. Reviews tell you whether automation works.
Policy drift detection. Your RBAC policies were written two years ago. Surely they still match how the business operates, right?
Reviews reveal reality. If "Marketing Manager" now requires access to data analytics tools that aren't in the policy, update the policy. If "Sales Rep" no longer needs access to legacy CRM that everyone's migrated away from, update the policy.
Quarterly review findings show which roles have drifted. Management uses that signal to update policies before drift becomes chaos.
Offboarding completeness. Your offboarding workflow claims to revoke access within 24 hours across 15 core systems.
Run monthly reviews on all departures from the past 90 days. Check whether they still have access anywhere. If you find former employees with active access, your workflow missed those systems.
This is particularly critical because offboarding workflows fail silently. Nobody creates a support ticket when deprovisioning doesn't happen. Reviews are the only feedback mechanism that catches these failures.

Implementation: How to Connect Reviews and Management in Practice
Making this work requires changing how you structure access governance:
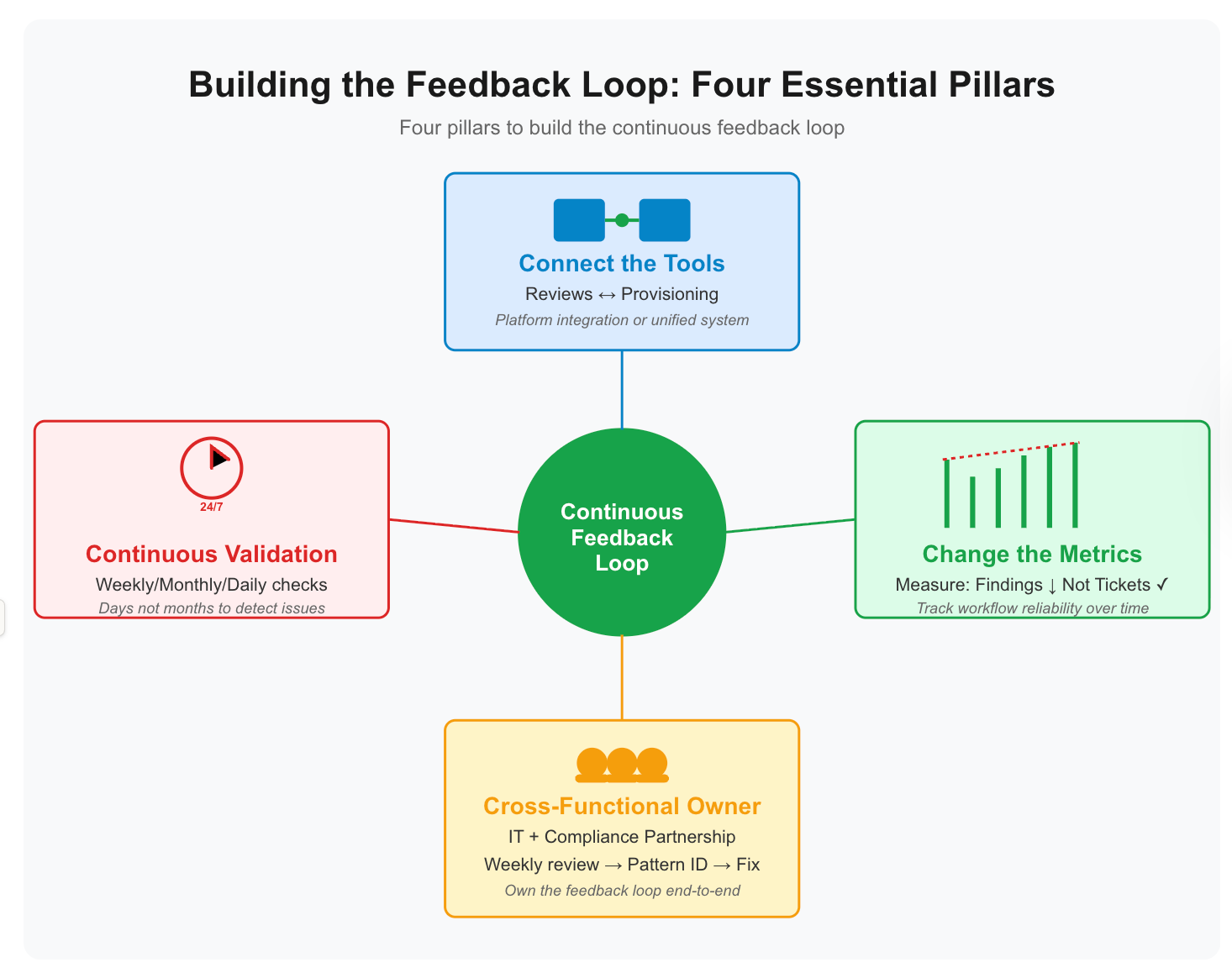
Connect the tools. Your access review platform and your provisioning system need to talk. Review findings should flow directly into workflow improvement backlogs. Provisioning changes should trigger automatic revalidation in the review system.
If you're using separate tools, build integration. Export review findings weekly. Import them into your IT workflow tracker. Tag findings by root cause (offboarding failure, role drift, manual exception, workflow gap). Prioritize workflow fixes by frequency.
This is where platform solutions like Zluri make the difference. When access reviews, access management, and access requests run on the same platform, your team can build this feedback loop without integration work. Review findings are immediately visible alongside your provisioning workflows. No manual exports, no custom APIs, no three-month delays waiting for integration projects.
Change the metrics. Stop measuring compliance by review completion rates. Start measuring whether review findings decrease over time.
If you're finding the same problems every quarter, your governance isn't improving. If quarterly findings drop 60% over six months, your workflow fixes are working.
Measure management by workflow reliability, not ticket velocity. Did automated provisioning work correctly for 95% of new hires? Did offboarding revoke access everywhere for 98% of departures?
Assign cross-functional ownership. Your IT team and compliance need a designated point person who owns the feedback loop. This role reviews findings weekly, identifies workflow patterns, prioritizes fixes with IT, and validates changes in the next review cycle.
Measure success by whether recurring findings decrease, not by how quickly remediation tickets close.
Continuous validation over quarterly events. Quarterly reviews create a 90-day lag between problem and detection. By the time you find offboarding failures, dozens of former employees have accumulated access.
Move to continuous validation:
- Weekly reviews of high-risk access (admin, production, financial systems)
- Monthly reviews of standard access
- Automated daily checks for critical workflows (offboarding, transfers, role changes)
When validation runs continuously, you catch failures in days instead of months. Problems get fixed before they compound.
Stop Flying with One Wing: The Continuous Review-Management Cycle

Access governance fails when you treat reviews and management as independent activities. Reviews become compliance documentation. Management becomes workflow automation. Neither improves security.
Access governance works when reviews and management form a continuous cycle:
- Management provisions access based on policies and workflows
- Reviews validate whether provisioning worked correctly
- Review findings identify which workflows are broken
- Management fixes broken workflows
- Next review validates fixes worked
- Cycle repeats
Every review should ask: which upstream workflow created this problem? Every workflow should ask: how will we validate this worked?
The organizations that get this right don't have separate review and provisioning teams. They have access governance teams where compliance and IT work together. Review findings become workflow improvement projects within days. Workflow changes get validated in the next review cycle.
Reviews catch what management misses. Management fixes what reviews keep finding. Neither works alone.
Stop trying to fly with one wing.







.png)

.svg)














