As organizations expand and their user base grows, manually managing the access of a large number of users becomes increasingly daunting. However, this challenge can be mitigated by implementing user provisioning software. In this article, we’ll explore top 8 user provisioning software that will help your team automate and streamline the user access management process.
Provisioning plays a significant role in managing the identity life cycle from onboarding to exit. A well-planned user provisioning approach can ensure the problem, like giving/revoking access, doesn't go out of your control.
Moreover, an automated user provisioning software is much needed by organizations today to streamline and automate the user provisioning process.
With an automated user provisioning tool, you can automate the process of adding, updating, and deleting users, as well as managing their access. It reduces the difficulties and delays associated with manually managing profiles and account rights while also increasing work efficiency.
Organizations can use user provisioning tools to improve work efficiency and productivity, gain visibility into user access, and enhance security.
Below mentioned are some of the benefits of user provisioning software:
- User provisioning tools help minimize the impact of human error and manual work, leading the IT department to concentrate on more impactful projects and improve productivity.
- It reduces administrative costs and time through automated procedures for governing user provisioning.
- It provides users with access only when it is necessary. Thus, preventing any security gaps that hackers could exploit to gain unauthorized access to sensitive organization information.
- In addition, userprovisioning software makes compliance easy as on-demand, detailed reports readily demonstrate who has access to which resources and when licenses expire. It gives the admin more insights to understand who has access to what applications.
Now that you are aware of the benefits offered by user provisioning tools, let’s explore some well known options that you can implement in your organization.
List Of 8 Best User Provisioning Software
Given below are the top 8 user provisioning software that you as an IT manager can consider opting for:
1. Zluri
Zluri offers an advanced access management solution that enables your IT team to ensure the right user gains access to the right applications at the right time. It also promptly revokes users' access upon their departure, which helps ensure no departing user holds access to organization SaaS apps and sensitive data.
Nonetheless, this streamlined approach allows your team to maintain a well-governed access environment and provides them with complete control over user access.
To provide you with a better understanding of how Zluri's access management works, let's explore its capabilities:
- Zero-touch onboarding and offboarding
With Zluri's access management, your team no longer has to manually assign and revoke employees' access, which is error-prone and time-consuming. This solution enables your team to create onboarding and offboarding workflows.
With just a few clicks, these workflows automate the onboarding and offboarding process, ensuring swift transitions for new hires joining your team and departing employees. This reduces the likelihood of errors and saves a significant amount of time.
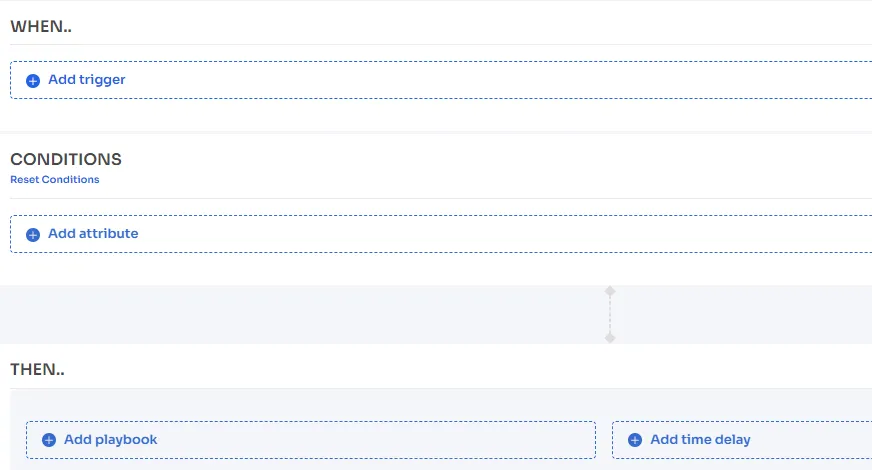
- Automated Triggers
With Zluri's access management, your team can create its own set of rules and triggers to automate specific IT tasks/actions. For instance, your team can use when and then conditions to onboard all the marketing department new hires on a specific date.
- Access beyond SCIM
IT teams find it challenging to manually provision access for apps without SCIM connectors. This process is typically cumbersome because most SSO and LCM tools rely on the SCIM protocol to manage access to Software as a Service (SaaS) applications.
When an application lacks an SCIM connector, these tools cannot automatically add or remove users from the application. Your team will have to manage onboarding and offboarding manually.
Zluri addresses this challenge by offering a solution that extends beyond SCIM connectors. Zluri utilizes direct API integration with apps, allowing for the automation of user provisioning even for applications without SCIM connectors.
- Secure user deprovisioning
Zluri's access management streamlines the process of revoking application access for departing employees by automating every crucial step. This helps ensure secure user deprovisioning.
In simple terms, Zluri offers a centralized platform where your team can revoke access in one swift action rather than manually disabling access for each application.
Moreover, to ensure departing employees have no lingering access to company data and applications, Zluri conducts thorough access audits. This helps minimize the risk of unauthorized access and safeguard sensitive data from potential breaches.
To learn more about Zluri's access management capabilities, book a demo now.
Features
- HRMS integration: Zluri's access management directly integrates with HRMS, which helps provide your team with up-to-date information about employees' profiles. For instance, if a new employee is hired or an employee role is being changed, by integrating with HRMS, Zluri updates all this data in a centralized dashboard, which makes it easier for the IT team to access
- Contextual apps recommendation: While creating an onboarding workflow your team gets a contextual apps recommendation which suggests apps based on the employee's department and role. This saves a significant amount of your team time as they don't have to manually search for applications that align with employees' roles.

- In-app suggestions: With this feature of Zluri's access management, your team can add employees to different channels, groups, or projects.
- App catalog & access request: Zluri's access management enhances employee experience by offering them an app catalog (a collection of pre-approved SaaS apps), from which they can choose any applications and gain access to them within no time.
- All they have to do is raise an app access request, and the IT team will further verify their identity, review the applications, and grant them access.
Customer Rating
- G2: 4.9/5
- Capterra: 4.9/5
2. Okta
Okta offers identity and access management for organizations. It helps IT teams manage the user authentication process.
It enables centralized identities and delivers access to thousands of users, keeping in mind the security and compliance requirements of the organization.
Okta helps organizations to manage the provisioning and deprovisioning of users without compromising any security protocols. These protocols allow the users to access the data from any device and be safe.
It allows integration with the existing Directories and identity systems, and third-party applications.
Features
- It provides Single sign-on to users to sign in to multiple applications and websites with single credentials.
- It offers multi-factor authentication to provide secured access to the users.
- It provides security for both on-premises and cloud-based applications.
- It automates the process of onboarding and off-boarding.
- In addition, it provides API access management.
Pros
- It integrates all your apps in one place and makes it easy to manage
- Easy to use
- Easy managing the users for user provisioning within the organization for the access management
- Easy logins to all the platforms with Okta
Cons
- Lacks in customization
- Multiple times log in a day as it times out frequently
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
3. SailPoint
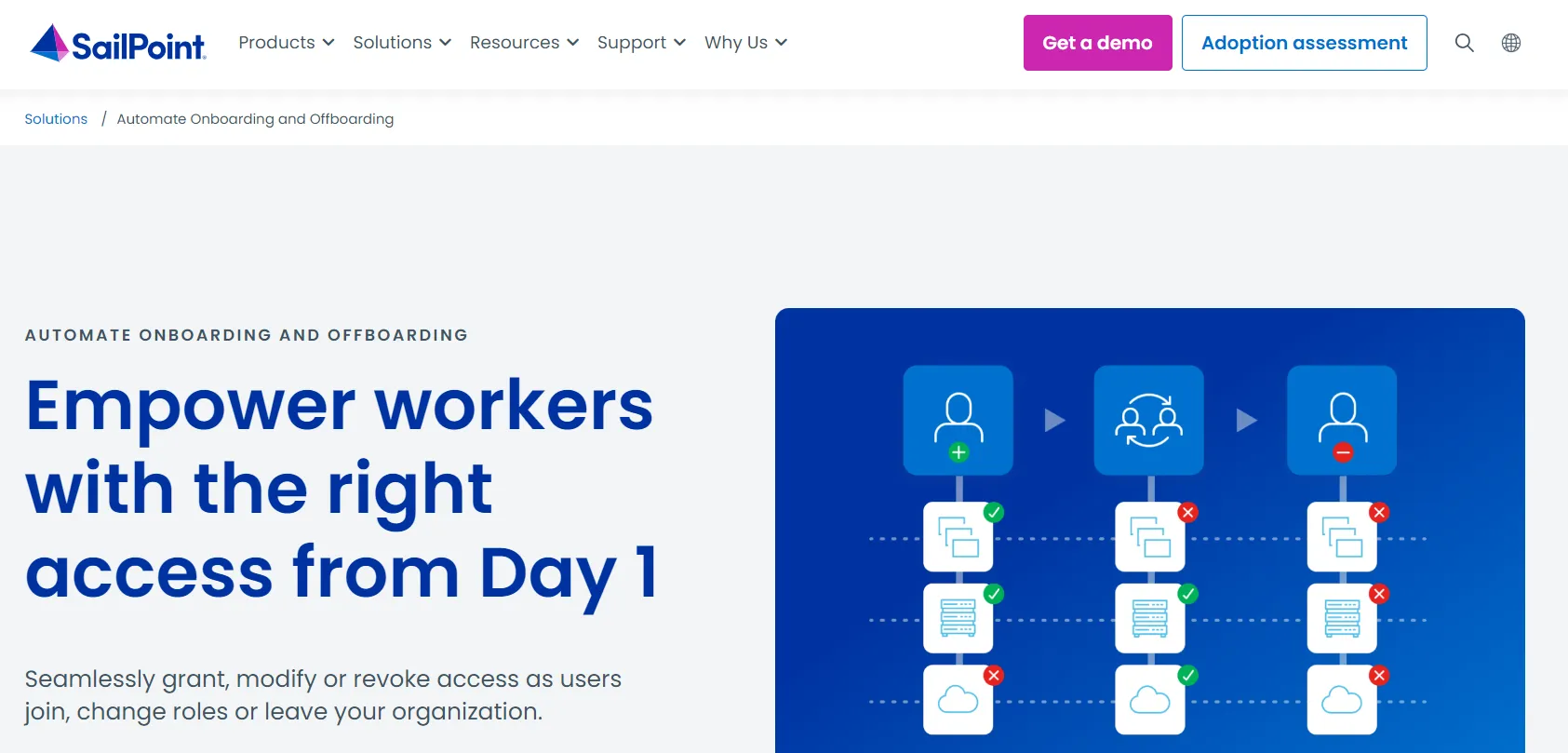
SailPoint is an identity access management software that can be deployed on-premise, in the cloud, or in a data center. With identity governance, automated user provisioning where you can grant employees access to applications. It allows you to block entry violations to ensure total security.
It provides you complete visibility to all access across your organization and replaces manual processes with automated workflows to deliver, manage, and secure access.
Features
- Identity governance.
- Password management.
- Automated user provisioning.
- Account management.
- Access rights request.
- Compliance control.
Pros
- UI is simple, clean, and intuitive
- Consistent reliability and frequent updates
Cons
- Poor customer support
- Setup is a little complicated
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
4. OneLogin
OneLogin is an identity and access management tool for businesses of every size that provides onboarding and off-boarding users with a secure, one-click process. With OneLogin, when there is a new user, based on their role and responsibilities, they are granted access to the required applications.
OneLogin provides layered security to the users and the organization with multi-factor authentication. It provides real-time account control that enforces access immediately whenever there is any change of roles or any user leaving the organization. It simplifies the process for IT teams and end-users.
Features
- OneLogin enables single sign-on to provide the right, secure access for each user.
- It integrates with directories like Active directory, Workday, Google Workspace, etc., and synchronizes the users with your directories.
- It enables single sign-on from mobile devices, and users can access the organization apps from any location and any device.
- Disable the access for the users for any change of roles or who has left the organization.
Pros
- Simple login with single credentials and get access to several applications.
- Centralized location for the apps
- User-friendly and straightforward to use to it
Cons
- Sometimes loading takes time
Customer Rating
- G2: 4.3/5
- Capterra: 4.7/5
5. JumpCloud

JumpCloud is an open directory and a cloud-based platform that secures identities, manages devices, and provides safe access to all types of IT resources such as on-prem, cloud, across windows, mac, or Linux.
It simplifies identity management and allows you to centralize and manage all the users and their devices and track activities.
Features
- JumpCloud offers a cloud directory with protocols including SAML, SCIM, LDAP, and RADIUS.
- It provides complete user lifecycle management across single sign-on applications and other resources.
- It provides group-based access control.
- It provides easy remote onboarding and off-boarding of the users.
Pros
- It is simple to use
- Good customer support
- Easy to configure in all the platforms Windows, Mac, and Linux
Cons
- Lack of policies for Mac and Linux
- Need more clarity in reports
Customer Rating
- G2: 4.6/5
- Capterra: 4.7/5
6. Microsoft Entra AD
Microsoft Entra ID formerly known as Azure Active Directory is a cloud-based directory and identity and access management solution that provides single sign-on to access your apps from anywhere. With this, the user can access all the services which have been granted permission by the administrator.
It allows companies to protect account credentials with detailed authentication and conditional access policies.
It provides governance that ensures the right user has access to the right resources and only when it is required.
Features
- Microsoft Azure protects access to resources and data using strong authentication and risk-based adaptive policies.
- It provides a fast sign-in experience to keep your users productive, reduce time managing passwords, and minimize friction.
- It centrally manages all your identities and access to your applications for both cloud and on-premise to improve visibility and control.
- It ensures that only authorized users have access to apps and data for all users and admins with automated identity governance.
Pros
- Easy to use, fast and reliable
- Easy to integrate with web applications
- Good customer support
- Allows to move between applications with ease
Cons
- Lack of insight into the federation process
- Synchronization might take a long time
Customer Rating
- G2: 4.4/5
- Capterra: 4.8/5
7. Oracle Identity Management

Oracle identity management is a comprehensive identity solution with identity governance, access management, and a directory. Oracle identity governance combines identity management, role analytics and management, entitlement management, access certification, and segregation of duties. Oracle Access Management provides web access management, single sign-on, and multi-factor authentication.
Features
- With Oracle identity management, application onboarding is easy that brings users and their app access to Oracle identity governance.
- It offers Access certification.
- It automates the user identity and account provisioning.
- It offers a password manager that allows you and your team to change or reset the password.
Pros
- User provisioning is smooth
- Easy to use and reduces operational expenses
- User-friendly interfaces
Cons
- Customization is difficult
- Hard for maintenance
Customer Rating
- G2: 3.7/5
- Capterra: 4.4/5
8. SAP Identity Management
SAP Identity Management centralizes user access management across your organization. It manages user access in hybrid environments securely and efficiently.
It aligns organization identity management with its key business processes and helps to ensure that access to corporate assets is compliant with corporate policies and legal regulations.
It utilizes one central place to manage user accounts in a complex system landscape, including both SAP and third-party systems. It helps to extend your identity management into the cloud by integrating with SAP Cloud Identity Services for user provisioning.
Features
- SAP Identity Management streamlines and maintains user access rights across multiple systems.
- It provides self-service password reset and password synchronization across connected systems.
- It leverages centralized reporting functionality.
- It integrates with SAP access control for effective mitigation of segregation of duties.
Pros
- Easy to understand and navigate
Cons
- Steep learning curve
- Little expensive
Customer Rating
- G2: 3.5/5
- Capterra: 4.5/5









.svg)














