As an IT manager, you understand the importance of maintaining a secure and compliant environment for your organization's sensitive data. With the ever-increasing number of users, devices, and access points, ensuring that the right individuals have appropriate access to the right resources at all times becomes crucial. This is where access recertification comes into play.
In this article, we will explore the concept of access recertification and its process involved in effectively managing user access rights within your organization.
What is Access Recertification?
Access recertification, also known as access attestation or entitle review, enables you to review and validate the access privileges of your users regularly. This ensures their access rights are still necessary, appropriate, and compliant with your organization's policies and regulations.
The primary objective of access recertification is to mitigate the risk of unauthorized access and reduce the potential for data breaches or compliance violations. By conducting regular access reviews, you can promptly identify and address any gaps or vulnerabilities in your access control systems.
This proactive approach safeguards your sensitive data and helps you demonstrate compliance with industry regulations and standards.
Moreover, access recertification involves systematically evaluating user permissions, entitlements, and organizational roles. During the recertification process, you collaborate with the relevant stakeholders, including business unit managers, data owners, and system administrators, to ensure that each user's access privileges align with their job responsibilities.
Key Benefits of Access Recertification
- Enhanced visibility into your data
One of the primary benefits of access recertification is the enhanced data transparency it provides. With this, you gain a comprehensive overview of who has access to your systems, applications, and sensitive data.
By conducting periodic access reviews, you can identify and eliminate any unnecessary or excessive user privileges, minimizing the risk of unauthorized access and potential security breaches. This level of transparency strengthens your security posture and helps you comply with regulatory requirements, ensuring a secure environment for your organization's critical information.
- Effortless and flexible access management
Access recertification brings efficiency and simplicity to your access management processes. Automating the recertification process allows you to easily repeat it regularly without requiring manual intervention. This automation saves valuable time and effort for both your IT admin and end-users, streamlining the overall access review process.
Moreover, as your organization grows and evolves, access recertification scales effortlessly to accommodate the changing needs of your user base. Whether you have hundreds or thousands of users, ensure consistent and standardized access reviews, simplifying your management tasks.
- Demonstrate compliance
You often need to maintain compliance and prove that proper access controls are in place. Access recertification allows you to generate detailed reports and audit trails quickly. These reports provide evidence of compliance during internal audits, regulatory inspections, or any other instances where proof of access control is required.
With access recertification, you can significantly reduce the time and effort required to gather the necessary documentation, enabling you to respond promptly to compliance requests and showcase the effectiveness of your access management practices.
Access Recertification Process
1. Identify the access rights to be reviewed
The access recertification process begins by identifying the access rights needing review. This involves compiling a comprehensive list of user accounts, permissions, and entitlements across various systems and applications.
You can effectively evaluate and validate user privileges by establishing a clear understanding of the access landscape.
2. Notify users and reviewers
Once the access rights have been identified, it is crucial to notify both users and reviewers about the upcoming recertification process. Users should be informed about the importance of reviewing their access rights and their role in maintaining a secure access environment.
Reviewers, often department managers or supervisors, should be aware of their responsibilities and the significance of participating in the recertification process.
3. Conduct the review
The review phase involves evaluating each user's access rights to determine whether they align with their current job roles and responsibilities. Reviewers assess the appropriateness of the assigned permissions and entitlements, considering factors such as changes in job roles, transfers, or terminations.
You can identify discrepancies, unauthorized access, or potential security risks by conducting a thorough review.
4. Report and escalate
After completing the review, it is essential for you to generate comprehensive reports summarizing the findings. These reports provide valuable insights into the current state of user access and highlight any issues or anomalies discovered during the recertification process.
If any critical concerns are identified, it is important to escalate them promptly to the appropriate stakeholders, such as your IT security teams or management, for further investigation and remediation.
5. Remediation follow up
Addressing identified issues is crucial to maintaining a secure access environment. The remediation follow-up phase involves taking corrective actions to resolve any discrepancies, unauthorized access, or security risks.
This may include revoking unnecessary access rights, updating user roles, or providing additional training or support to users. By promptly addressing these issues, you can mitigate potential risks and ensure that access rights align with business needs.
6. Document and maintain
Accurate documentation is key to maintaining an effective access recertification process. Maintaining records of the review outcomes, remediation actions taken, and any changes made to user access rights is essential.
This documentation provides a historical trail and serves as a reference for future recertification cycles. Additionally, it aids in compliance audits and helps ensure organizational transparency and accountability.
7. Repeat the process
Access recertification is an ongoing process that should be repeated at regular intervals to ensure continued security and control over user access. By establishing a recurring schedule for recertification, you can proactively identify and address any changes in user access requirements or potential risks.
This iterative approach helps maintain a dynamic and adaptable access environment that aligns with the evolving needs of your organization.
The Challenges Associated with Access Recertification
Here are a few challenges associated with access recertification.
1. Manual and time-consuming processes
One of the primary challenges in access recertification is the reliance on manual processes. Often, IT managers find themselves burdened with reviewing and confirming access rights for a large number of users across multiple systems.
This manual effort is not only time-consuming but also prone to errors. Keeping up with the constant changes in user roles, responsibilities, and organizational structures can be overwhelming.
To overcome this challenge, implementing automated access recertification tools can streamline the process, reduce manual effort, and ensure accurate reviews.
2. Lack of visibility and accountability
Another challenge you might face in access recertification is the lack of visibility into your user access activities and their associated risks. Without proper tracking and monitoring mechanisms, it becomes difficult to identify dormant accounts, unauthorized access, or potential security breaches.
To address this challenge, it is crucial to leverage robust identity governance and administration (IGA) solutions that provide real-time visibility into user activities, generate audit trails, and enable granular access control.
3. Complex organizational structures
Access recertification becomes increasingly challenging in organizations with complex hierarchical structures, multiple business units, or geographically dispersed teams. Defining appropriate user roles and responsibilities can be complex in such environments, leading to confusion and delays in recertification processes.
For this reason, you should strive to establish clear organizational policies, collaborate with departmental stakeholders, and maintain effective communication channels to ensure accurate and timely recertification.
4. Fail to adhere to required regulatory compliance
Complying with industry regulations and standards poses another significant challenge in access recertification. Organizations operating in healthcare, finance, or government sectors need to adhere to specific compliance requirements, which often involve stringent access control measures.
As an IT manager, you must stay updated with relevant regulations, ensure your access recertification processes align with these requirements, and maintain proper audit documentation.
Enhance Access Recertification with Zluri’s IGA Solution
With the rapid growth of SaaS, it's now easier for your employees to get special access rights, but it's also more challenging to control and manage those privileges due to increased complexity.
To ensure a secure and compliant environment, giving the right people the right permissions is crucial. That's where Zluri's identity governance and administration (IGA) solution transforms how you handle access. With Zluri's IGA solution, you can streamline IT audits, comply with regulations, and completely control who gets access to what.
Zluri's IGA solution offers a powerful feature for reviewing user access, making it simple to manage and assess users' access permissions. This feature helps reduce security risks and gives you better control over access in your organization.
So, how does Zluri achieve this? First, it helps you identify all the SaaS systems and applications being used. Zluri provides a centralized platform where you can see a comprehensive list of all the apps used in your organization's SaaS environment. This gives your IT teams complete visibility into your SaaS ecosystem.
With this visibility, you can effectively manage user access across your SaaS applications, handling access requests and reviews to ensure compliance with regulations and maintain the right access levels.
Let's take a closer look at how it works.
Empower your user’s data with Zluri’s unified access
With its unified access feature, Zluri simplifies the complex task of managing user access across different systems and applications. This boosts your organization's security, enhances operational efficiency, and ensures compliance with industry regulations.
Unified access includes three key components:
Access Directory: With Zluri, you gain centralized control over your organization's access directory. This means you can easily see who can access which resources and applications. This clear visibility helps maintain a secure environment and prevents unauthorized access.
For example, in a large organization with multiple departments and employees, Zluri makes it effortless to keep track of access rights and maintain data safety.
Access Privileges: Understanding the access privileges of your users is crucial for effective access management. Zluri allows you to define and monitor user roles and contextual information, like job roles or project involvement, to determine their access levels.
This granular control ensures that each user only has access to the resources they need for their specific tasks, reducing the risk of data breaches and enhancing overall security.
For instance, an employee in the marketing team will have access to all the required social media platforms and marketing tools while being restricted from sensitive areas of the IT infrastructure.
Activity & Alerts: Zluri provides real-time insights into user activity, such as login/logout times for various applications. This information helps you track user behavior and identify any suspicious activities that may indicate security threats.
Additionally, Zluri's proactive alerting system notifies you immediately of unusual activities or potential security breaches via email. This enables you to take swift action and minimize the impact of security incidents, ensuring the overall safety of your IT environment.
Streamline your access review process with automation
Discover the power of Zluri's automated review capabilities, designed to streamline your access control system and enhance data security. With Zluri's automated reviews, you can ensure the protection of your sensitive information while staying compliant with regulations.

Here's how Zluri empowers your organization:
Access Rules: Gain a comprehensive understanding of your access landscape with Zluri's access insights. This knowledge forms the basis for creating precise access rules.
For example, if certain employees have unnecessary access to sensitive data, you can quickly restrict their permissions to bolster data security.
Scheduled Certification: Zluri simplifies the certification process by allowing you to schedule certifications proactively. These certifications ensure employees' access aligns with your organization's policies and regulatory requirements. Keeping access permissions up-to-date and compliant is effortless with scheduled certifications.

Auto-remediation: Taking access management to the next level, Zluri introduces auto-remediation capabilities. This feature goes beyond reviews and automatically responds to access violations. Any unauthorized access or potential security breaches trigger immediate corrective actions, enhancing your organization's security posture and ensuring compliance with industry standards.
For example, when users from your marketing team grow or change roles, Zluri makes it effortless to adjust access privileges accordingly. Whether it's a promotion or a role change, access privileges can be seamlessly modified to match new responsibilities. Additionally, unnecessary access can be swiftly revoked as part of the auto-remediation process, minimizing potential security risks.
Moreover, Zluri's automated reviews eliminate the manual effort and time required for access reviews. The burden is significantly reduced by 70%, and the review process becomes ten times faster, thanks to intelligent automation. Your IT team can focus on strategic initiatives while Zluri handles the heavy lifting, from collecting access data to analyzing patterns effectively.
Now, let’s discuss the steps to automate the access review process.
- Step 1: Open Zluri's main interface and go to the "Access Certification" module.
- Step 2: Now, to create an access certification, click on "Create a New Certification." Now, add a suitable name for the certification and assign a responsive owner.
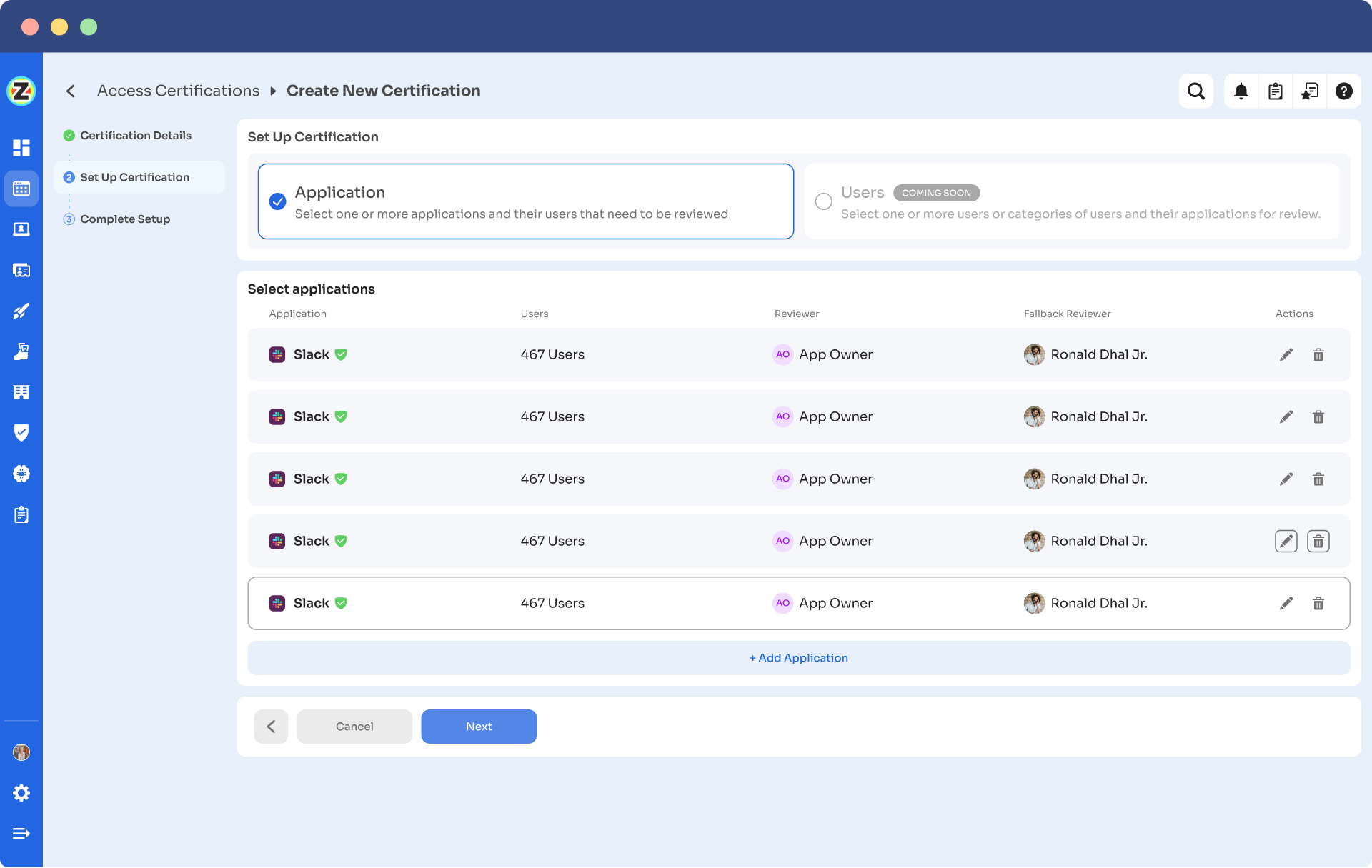
- Step 3: Under the setup certification, choose how you want to review users' access: either by Application or Users.
For example, if you select to review access by Application, add the application to audit users' access.
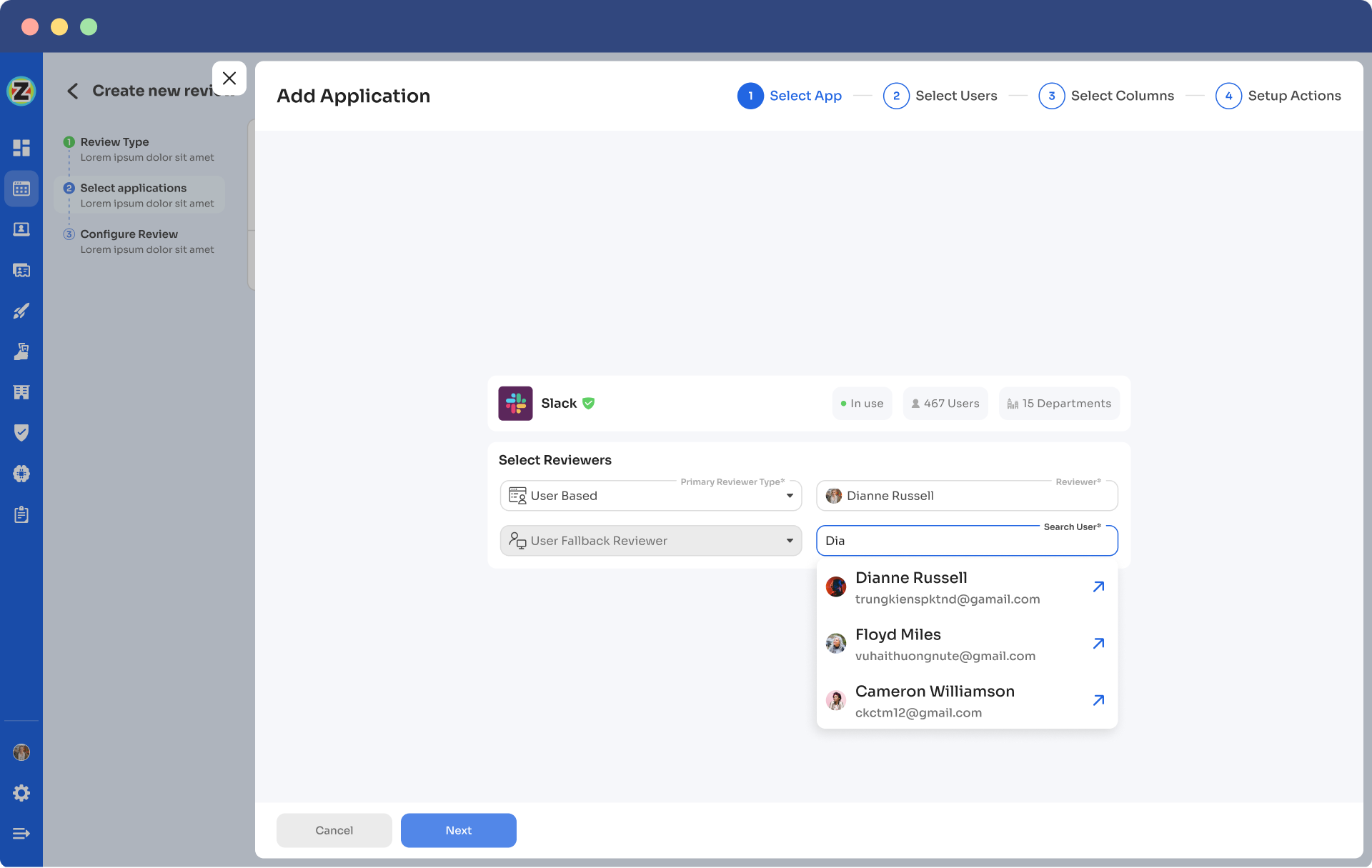
- Step 4: Choose a primary reviewer and a fallback reviewer from the drop-down menu. Once you are done selecting the reviewers, you can click on Next.
Note: Generally, the primary reviewers are app owners. Also, choose the fallback reviewer carefully whom you think is responsible.
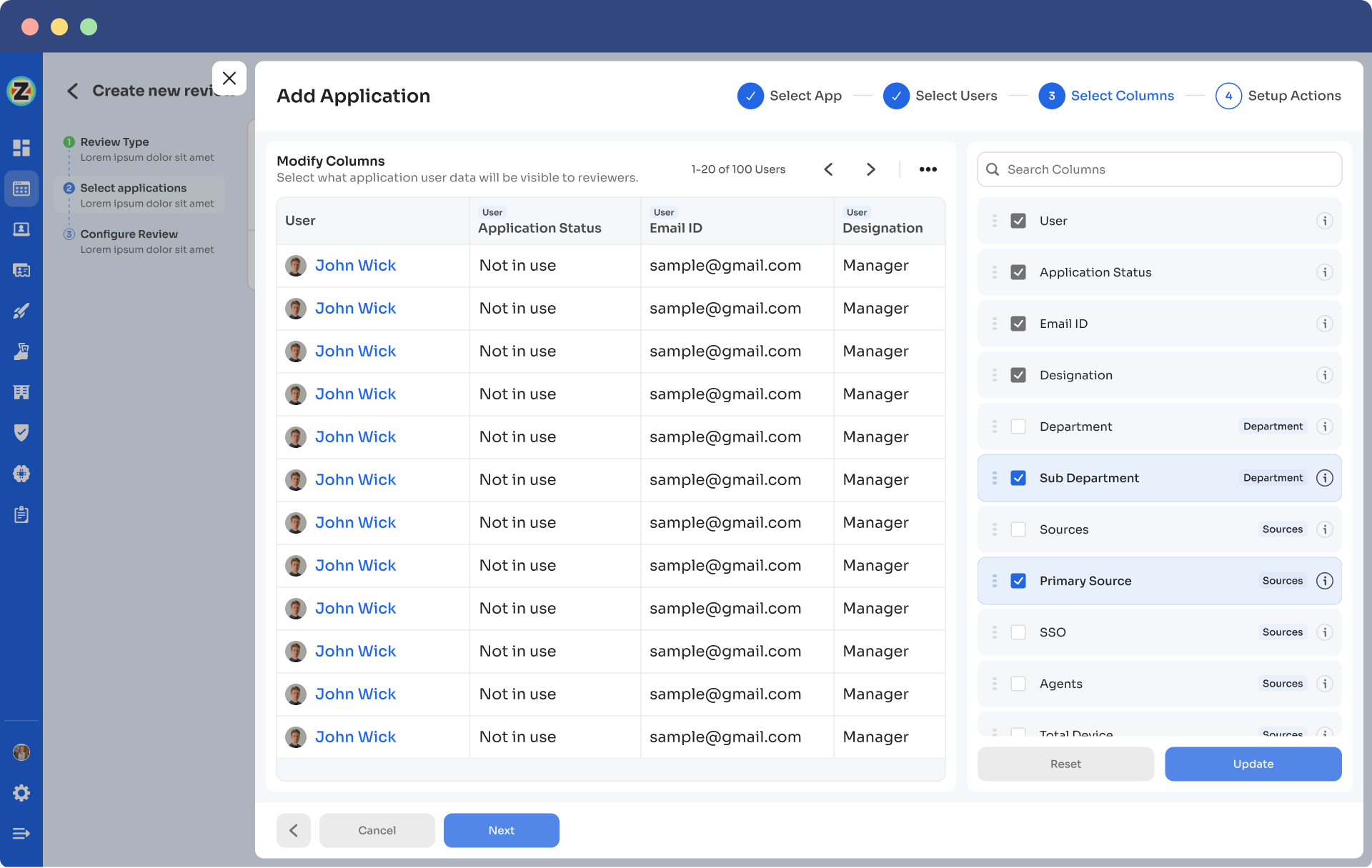
- Step 5: Choose the specific users to include in the certification process. You can also filter the data points, such as user department, job title, usage, and more, as per your certification requirements. Then, click on "Next."
Note: Select those relevant data points only that you wish your reviewers to see while reviewing the access. By filtering the criteria appropriately, you enable your reviewers to make swift and well-informed decisions, streamlining the review process and ensuring efficiency.
- Step 6: Now configure actions based on your needs and choose from the drop-down options.
For example, for rejection action, you can select the respective deprovisioning playbook to revoke the unnecessary access of the users.
Once you set up the action, you can click on “add applications”.
Note: You can add multiple applications for the same certification.

- Step 7: Set the start and end dates for the certification process, depending on within what time span you want the review to be completed.
Note: You can also click "Save Template" to save it for future use.
- Step 8: Lastly, you can keep track of the automated access review process by clicking on the ‘Review Status’ and viewing whether the review is still pending, modified, declined, or approved.
Finally, you can easily track the entire review process on a chart. Once the review is complete and the assigned reviewer approves it, you can click 'conclude' to instantly send the reports to their email.
Experience the transformative power of Zluri in your access management and compliance processes by booking a quick demo today!









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)