You think access reviews are complete. Reality? Half of your apps, users, and privileges are still unknown.
User access reviews are a core requirement for identity governance and compliance. They’re meant to help you regularly verify that every user has the right level of access–nothing more, nothing less. Whether for SOX, HIPAA, ISO 27001, or SOC 2, access certifications are a must-have control.
Most organizations are doing them. The problem is how they’re being done.
Despite good intentions, access reviews are often fragmented, manual, and disconnected from actual risk. Critical apps go unreviewed, reviewers approve access without context, and even after the review cycle, access isn’t always removed.
In fact, a 2025 Help Net Security report found that 53% of security teams lack continuous and up-to-date visibility into their cloud and SaaS environments, making it difficult to run comprehensive and meaningful access reviews.
It’s not a lack of effort. It’s a lack of alignment between the review process and how access actually works today, across cloud apps, hybrid teams, contractors, and constantly shifting roles.
This article breaks down the most common access reviews challenges IT teams face, and how leading organizations are solving them with better visibility, automation, and risk-aware governance.
Why Access Reviews Fail, Even When You’re Doing Them
Even in organizations that take compliance seriously, access reviews often fail to meet expectations. You’re running quarterly certifications, tracking approvals, and generating audit logs, yet access-related gaps still appear in audits.
Why? Most access review processes weren’t built for SaaS-first environments with decentralized ownership, app sprawl, and constantly shifting user roles. In regulated industries, the gap between intent and execution becomes a liability.
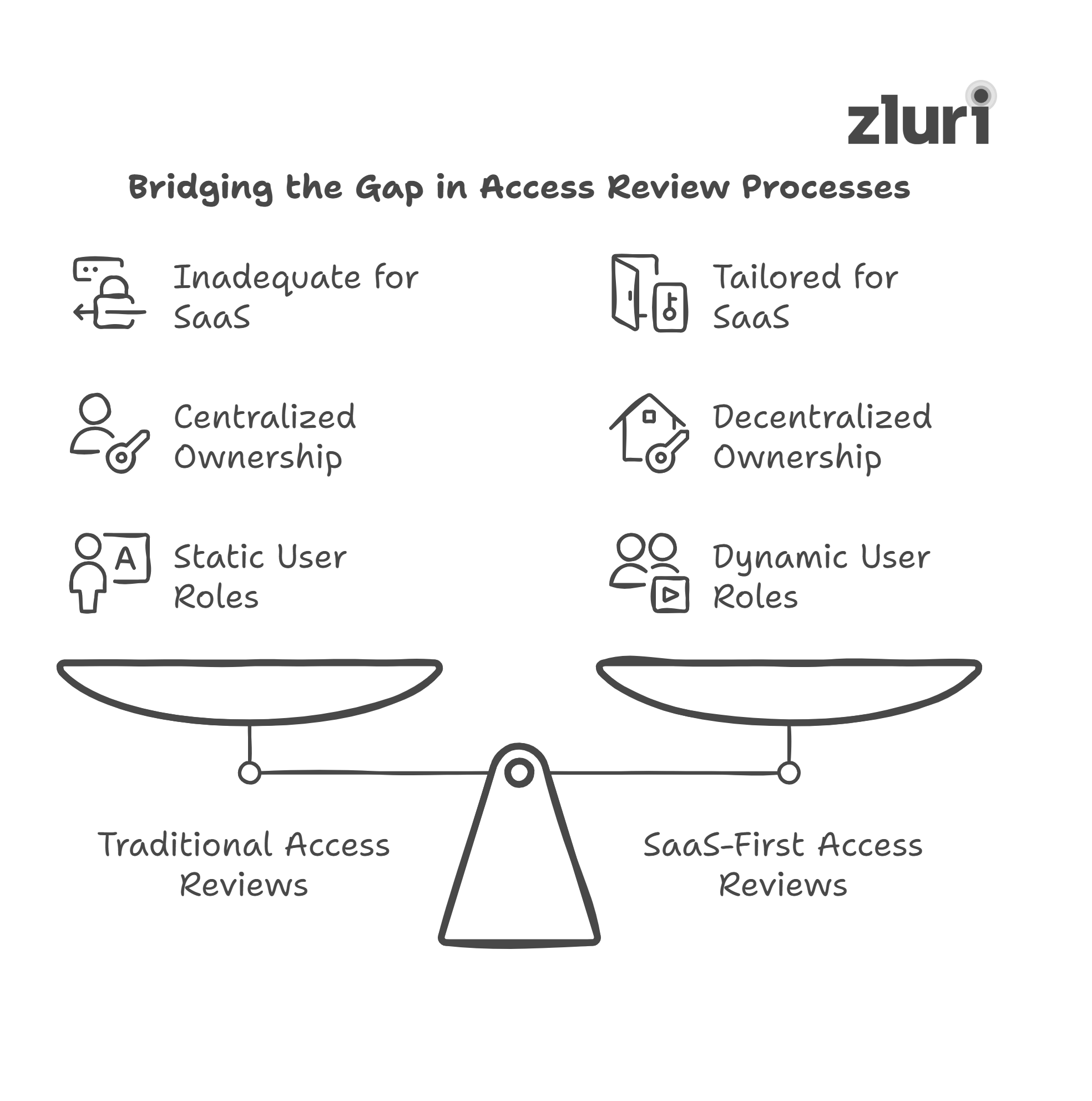
Here are the common reasons access reviews fail to deliver, along with what IT teams are doing differently to address them.
- You’re not reviewing every app that matters
Most access reviews only cover the apps that IT already manages, typically those connected to your SSO or HRMS. But that leaves a significant portion of your SaaS environment out of scope.
In modern organizations, teams adopt their own tools. Users join apps using Google or Microsoft logins. And not every application supports SAML, SCIM, or centralized provisioning. As a result, many users gain access to apps that never undergo formal IT control and are never included in your review cycle.
That’s a problem. These unmanaged or “invisible” apps often contain sensitive business data, including marketing content, customer information, contracts, and financial details. If they’re excluded from access reviews, you’re missing risk exposure that won’t show up until some issue happens, or until the next audit.

What can you do?
- Go beyond SSO-based discovery: Use a multi-source SaaS discovery engine that goes beyond SSO metadata. Look for tools that combine:
- Browser agent data to capture direct-to-site logins
- Desktop agents to detect installed apps & login activity
- Finance & expense systems to be aware of the SaaS apps purchased outside of procurement
- API integrations to identity account connections (e.g., via Google/Microsoft accounts)
- Map user-to-app relationships even without formal provisioning: Even if it isn’t integrated with your IdP or IAM, its usage can be tracked and added to your review cycle.
- Include department-owned & shadow IT apps in your access governance platforms: Whether it’s Notion, Airtable, Canva, etc., review access to ensure sensitive data is being handled securely.
- Enrich identity data with department, role, and app owners: This will help you know who should be responsible for each review, even for apps outside traditional IT scope.
You can’t govern what you can’t see. Access reviews are only as strong as the discovery layer underneath them.
- Reviewers don’t have enough context to make informed decisions
Most access reviews rely on managers or app owners to certify who still needs access. However, in many cases, reviewers lack sufficient information to make that call with confidence.
They’re shown a list of users and roles, but not whether the user is still active in the app, how often they log in, or whether their role has changed. And they’re often asked to do this for dozens of users across multiple systems, with little context on what matters.
Without a clear context, approvals become a default action. Access gets rubber-stamped, not reviewed.
And this isn’t just a procedural weakness; it’s a governance gap. If reviewers don’t understand the access or how it’s used, you lose the intent behind the review, which is to verify whether that access is still justified.

What can you do?
- Surface usage insights: Be aware of key insights, including last login, activity trends, and account status. If a user hasn’t logged in for 90 days, the reviewer should be notified.
- Highlight role or department changes: If someone switched teams but retained access, flag it.
- Tie access back to business function: If the app is sensitive or restricted to specific job functions, indicate whether the user still belongs to that group.
- Break up review loads & prioritize high-risk items: Use segmentation and automation to reduce reviewer fatigue and focus attention where it matters most.
You can’t expect reviewers to make informed decisions without context. When you provide the right information/context, they can focus on access that actually needs attention, and stop blindly approving everything.
- Everything is too manual & fragmented
Even when access reviews are scheduled, the underlying process is often disjointed. Access data resides in one system, while approvals occur via email or spreadsheets. And revocation, if it happens at all, relies on a separate ticket to the IT team or the app owner..
Every step takes time. Every delay introduces risk.
As your environment becomes more complex, with an increasing number of users, apps, and teams, managing reviews manually becomes increasingly challenging. You end up spending time chasing approvals, updating access in multiple systems, and reconciling mismatched user data. And without a reliable audit trail, you have no easy way to prove what was reviewed, when it was reviewed, or by whom.

What can you do?
- Automate the complete review cycle: That means triggering certifications, notifying reviewers, capturing decisions, and enforcing revocations, without switching between systems.
- Utilize platforms with deep integrations into your SaaS apps & IAM stack: The goal is to enable your reviewers to make a decision once, and have the change automatically reflected where it matters.
- Promote multi-level approvals: This can be implemented wherever needed, with built-in escalations, reminders, and timeouts to ensure reviews progress smoothly.
- Generate audit-ready logs as part of the process, not a manual step.
When access reviews run across disconnected tools, they become a burden. Automating the workflow isn’t just about speed; it’s about closing risks faster with fewer errors.
- You’re using a one-size-fits-all review schedule
Most organizations schedule access reviews on a fixed timeline, such as quarterly, biannually, or annually. However, this approach treats all access equally, regardless of the sensitivity of their access or how frequently their role changes.
That’s a problem.
Because not all access carries the same level of risk, a finance administrator with broad data permissions requires more frequent review than a junior employee with limited access. And if someone switches teams, gets promoted, or takes on a high-risk role, that access is often left unchecked until the next scheduled review.
Fixed schedules also lead to review fatigue. Reviewers are asked to certify that access hasn’t changed, while riskier changes often go unnoticed between cycles.

What can you do?
- Adopt a risk-based approach to certifications: Review high-risk apps more frequently, while reducing the frequency of reviews for low-risk access.
- Trigger event-based reviews: Department change? Promotion? New high-risk access? Let those drive ad-hoc reviews rather than waiting for the next scheduled cycle.
- Build dynamic policies that adapt over time, utilizing user context and app risk to determine when a review is truly necessary.
Not all access needs the same level of attention. Review what matters, when it matters–based on risk, not routine.
- Access Isn’t Actually Removed After the Review
Marking access as “no longer needed” in a review is only half the job. The bigger risk? That access never gets revoked at all.
In many organizations, the access review ends with a spreadsheet or a certification in a governance platform. However, the actual revocation relies on a separate workflow, which involves creating a ticket, notifying IT teams, and waiting for app owners to take action. And without frequent follow-ups, things slip through the cracks.
This creates a false sense of completion. On paper, the review looks clean. But in reality, users still have access to sensitive systems they no longer need. If auditors dig deeper, or if an incident occurs, you will need to explain why access wasn’t revoked when it should have been.

What can you do?
- Automate revocations wherever possible: When a reviewer flags access for removal, the change should propagate directly into the app via native or API-based integrations.
- Establish closed-loop workflows: Ensure clear accountability for every action flagged during the review, whether automated or manual.
- Track and report on review outcomes: It’s not enough to show who reviewed what; you need proof that remediation actually happened, and when.
If access remains active after a review indicates otherwise, you haven’t reduced risk; you have just deferred it.
- You Can’t Easily Show Audit-Ready Evidence
Even when access reviews are completed on time, many teams struggle to provide clean, audit-ready documentation. Decisions are buried in spreadsheets, approvals live in disconnected systems, and there’s no central log that ties it all together.
So, when auditors ask, “Who has access to this system, who approved it, and when was it revoked?” – you’re left chasing emails, trying to piece together logs from multiple sources, or rushing to recreate the review trail.
That’s a red flag during compliance audits, and a major time wastage for your team.

What can you do?
- Centralize your review record: Store reviewer decisions, timestamps, comments, and remediation actions in one system of record.
- Ensures review logs can’t be altered: Make it easy to demonstrate that certifications weren’t tampered with or backdated.
- Generate audit-ready reports by default: Your access review platform should produce exportable reports that align with SOC 2, ISO 27001, SOX, or any other applicable compliance framework, without manual formatting.
If access reviews are meant to prove control, you need more than a checklist. You need evidence that you can hand to an auditor at any time.
- Contractors and Vendors Fall Through the Cracks
Access reviews often focus on full-time employees, because that’s where identity data is most structured — linked to HRMS records, formal roles, and onboarding workflows. But contractors, vendors, interns, and other non-employees typically fall outside those systems.
Their access might be provisioned manually, tracked in a spreadsheet, or granted directly by a business unit. And when review cycles come around, these identities are either missing from the scope or there’s no clear owner responsible for certifying them.
That’s a serious oversight. Non-employees often have access to sensitive data and systems, but without lifecycle triggers (like terminations or department changes), their accounts are more likely to be orphaned or over-provisioned.

What can you do?
- Classify users by identity type: Your access review should distinguish between employees, contractors, vendors, and service accounts, so each can be reviewed appropriately.
- Establish ownership for non-employee access: Tie reviews to project managers, vendors, or department heads who can validate whether access is still required.
- Automate access expiry for time-bound users: Set predefined access durations for contractors and trigger re-certifications before access is extended.
If contractors and vendors are outside your review process, they’re outside your governance. And that’s where risk grows fastest.
- Reviewers aren’t linked to identity lifecycle events
Most access reviews happen on a schedule, but access risk doesn’t wait for the next quarter.
When access reviews aren’t tied to identity lifecycle changes, like onboarding, role transitions, or offboarding, you miss the most important windows to catch overprovisioning. A user gets promoted and gains broader access, but no one revisits what they already had. A contractor’s project ends, but their access remains until someone remembers to remove it.
The review process becomes reactive rather than responsive.

What can you do?
- Trigger reviews based on identity events: Joiner, mover, and leaver events should prompt targeted access checks, not just provisioning updates.
- Monitor high-impact changes: Changes to department, location, manager, or job function should trigger review workflows, especially for sensitive apps.
- Pair reviews with deprovisioning automation: When access is no longer needed, revoke it immediately, don’t wait for the next cycle.
Reviews that aren’t tied to lifecycle events are always a step behind. Spotting issues in real-time requires reviews that move with your identities.
How Zluri Helps You Overcome Access Reviews Challenges?
Zluri isn’t just another access review platform; it’s built to address the root causes behind ineffective and fragmented reviews. It provides you with the visibility, context, workflows, and automation necessary to make access reviews reliable, scalable, and truly risk-reducing.
Here’s how Zluri addresses the core problems most teams face:
- Complete app discovery: From shadow IT to lifecycle-driven reviews
Access reviews fail when they’re incomplete, when orphaned accounts, sanctioned apps, or external users fall outside the scope. Zluri eliminates those blind spots from day 1.
Its discovery engine discovers apps missed by SSO by pulling data from:
- Browser and desktop agents (for direct logins and app usage)
- Finance systems (to surface unsanctioned subscriptions)
- OAuth-based integrations (to map access even without formal provisioning)
It also identifies:
- Orphaned accounts not tied to active identities
- External identities, like contractors or vendors, still have access
- Inactive users or standing privileges occupying app licenses without usage
Beyond just who has access, Zluri also connects reviews to the appropriate time. Instead of waiting for static quarterly reviews, you can trigger them based on:
- Role or department changes
- Privileged access assignments
- End-of-contract timelines for external users
Why it matters: You’re no longer reviewing only what’s convenient or visible. Zluri lets you govern the entire identity and access landscape – when it matters most.
- Delivers real context, so reviewers stop rubber-stamping
Zluri equips reviewers with deep, actionable context, right inside the review interface. No need to switch tabs or ask around.
Reviewers can see:
- When a user last logged into an app
- How often do they use it
- Whether the access is admin-level or standard
- If the account is inactive or tied to an external identity
This level of detail enables reviewers to move beyond role-based assumptions and make informed, risk-aware decisions.
Why it matters: When reviewers understand access in real-world terms — usage, risk, and exposure — they can stop rubber-stamping and start governing.
- Supports multi-level reviews
With Zluri’s access review solution, your IT team (or any individual assigned to create an access certification workflow) can set up multi-level reviews (up to 5 levels maximum) within the access certification workflow.
Additionally, they can assign a primary reviewer and a fallback reviewer (in case the primary reviewer is unavailable, the fallback reviewer steps in and carries forward the access review) for each level.
Why it matters: Multi-level reviews reduce the risk of oversight. If one person misses something, another can catch it, without a bottleneck or skipped steps.
- Automates enforcement with closed-loop remediation
Zluri doesn’t stop at access decisions; it acts on them.
The moment a reviewer flags access for revocation, Zluri routes that decision to the IT team and automatically triggers pre-configured playbooks to enforce it. These workflows can handle deprovisioning, license downgrades, or privilege adjustments across 800+ applications.
For recurring anomalies (like multiple inactive accounts), Zluri also supports bulk review and remediation, saving hours of repetitive work.
Why it matters: You reduce time-to-remediation from days or weeks to minutes without things falling through the cracks.
- Always ready for the next audit
Zluri, through its access review process, logs every review decision, action, and justification. No last-minute scrambling for evidence, and no gaps for auditors to challenge.
You get:
- Unalterable logs with timestamps, reviewer identities, comments, and remediation outcomes.
- Framework-aligned reports tailored to SOC 2, ISO 27001, SOX, and more.
- Exportable review history with a full audit trail for every certification cycle.
- Real-time dashboards to track review completion, exceptions, and policy violations.
Why it matters: When auditors ask who has access to a critical system and why it was approved, Zluri gives you a complete trail without the spreadsheet chaos.
Zluri helps you shift access reviews from a burdensome compliance task to a scalable risk-aligned process. With deeper coverage, smarter decisions, faster remediation, and always-on audit readiness, you finally get a system that works, at the speed your business needs.
Getting Access Reviews Is Just the Beginning
Access reviews are one of the most visible controls in identity governance, but also among the most frequently mishandled. As SaaS sprawl, external identities, and hybrid access patterns grow, reviews can’t remain a box-checking exercise. They need to evolve into a continuous, risk-aware process that feeds into your broader security and compliance posture.
The good news? Fixing access reviews creates momentum for everything else: faster deprovisiong, stronger least privilege enforcement, cleaner identity data, and greater confidence during audits.
The most forward-thinking teams aren’t just trying to “complete” reviews; they are striving to continually improve them. They’re using them to understand how access actually works across the business, identify governance gaps, and determine how to close them.
It’s not about more reviews. It’s about better ones, aligned with how access really works today.






.svg)














