This article helps you explore the various CSPM tools of 2024. Find out how to safeguard your critical data and maintain compliance effortlessly.
As an IT manager, one of your paramount responsibilities is safeguarding the digital assets and sensitive information your company relies on. This is where Cloud Security Posture Management (CSPM) tools step in as a crucial element in improving your organization's security posture.
An effective cloud security posture management (CSPM) tool ensures that your cloud environment aligns with security best practices. This minimizes vulnerabilities and mitigates potential risks. However, choosing the suitable CSPM tools for your organization can be a daunting task.
Therefore, it is important to explore the various CSPM tools along with their features to make an informed decision. But before exploring the top CSPM tools, let’s discuss the key features to look for in an efficient CSPM tool.
Key Features to Look For in CSPM Tools
Below are the various key features of your suitable CSPM tool.
- Real-time Monitoring and Alerts: A robust CSPM tool should offer real-time monitoring capabilities, providing immediate insights into your cloud security posture. Alerts for suspicious activities or misconfigurations allow you to respond promptly and prevent security incidents.
- Automated Remediation: Look for CSPM tools that identifies issues and automates the remediation process. Automation streamlines security protocols, ensuring a swift response to threats without overwhelming your IT team with manual tasks.
- Comprehensive Compliance Reporting: Compliance with industry regulations is non-negotiable. A good CSPM software should provide detailed compliance reports, helping IT managers demonstrate adherence to standards and regulations to auditors and stakeholders.
- User-friendly Dashboard: The complexity of cloud environments requires a user-friendly interface. A well-designed dashboard centralizes information, making it easy for your team to grasp the security status at a glance and delve into specifics when needed.
- Integration Capabilities: Seamless integration with existing security infrastructure is vital. A CSPM tool should complement your current security stack, allowing for a cohesive and interoperable defense strategy.
How Do You Choose the Best CSPM Tool?
Selecting the appropriate Cloud Security Posture Management (CSPM) tool can pose a significant challenge. To aid in your decision-making process, take into account the following factors:
- Cloud Provider Compatibility: Evaluate the cloud provider your organization relies on and verify that the chosen CSPM tool seamlessly integrates with and supports that specific provider.
- Essential Features: Identify the key features crucial for your organization's security posture management. It's imperative to ensure that the selected CSPM tool aligns with and provides these essential features to meet your specific requirements.
- Integration with DevOps Tools: Assess the DevOps tools employed within your organization and confirm that the CSPM tool is capable of integrating seamlessly with these tools. This ensures a cohesive and efficient workflow across your development and security teams.
- Cost Analysis: Consider the financial implications of implementing the CSPM tool. Perform a thorough cost analysis to determine its affordability and alignment with your organization's budget constraints. This ensures that the chosen solution not only meets your security needs but also falls within financial parameters.
- Support Services: Gauge the level of support provided by the CSPM tool vendor. Ensure that the support services offered align with your organization's requirements. A robust support system is vital for addressing any issues promptly and maintaining the effectiveness of your security posture management.
By carefully evaluating these factors, you can make an informed decision when selecting a CSPM tool that best suits your organization's cloud security needs.
There are many CSPM tools available in the market. This post will discuss 11 cloud security posture management (CSPM) tools you can use to secure your organization's cloud data.
But before discussing the CSPM tools, let's take a moment to introduce who we are and what solutions we provide at Zluri for you.
Enhance Your SaaS App Security with Zluri
Zluri offers a cutting-edge SaaS management platform that helps you to centralizely manage your corporate suite of SaaS applications. Zluri's SMP platform provides an advanced SaaS discovery capability. The platform uses five discovery methods, ensuring a 100% discovery of all SaaS applications in active use and the app insights within your organization.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Zluri doesn't just stop at discovery; as per Kuppingercole's report it also offers a range of security and compliance information. Your team can access event and statistic tracking capabilities, shared data insights, and tailored security and compliance assessments for SaaS applications. This approach aids in achieving compliance objectives while advancing overall security posture.
- Events Monitoring: Zluri actively monitors and aggregates news related to your applications, providing you with real-time updates on potential threats such as ransomware, data breaches, patches, and security vulnerabilities. The risk score assigned to each app is based on event analysis, aiding you in prioritizing security measures.The below mentioned image shows the app events for Slack.
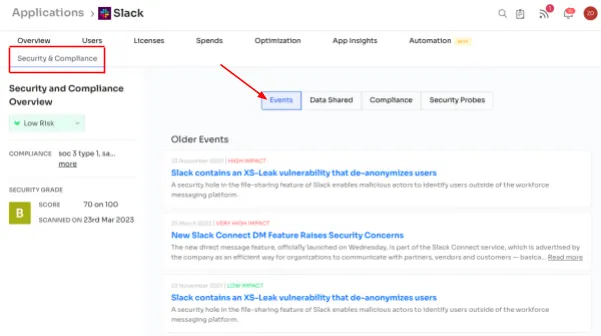
- Events of each app
- Data Shared Insights: Gain control over data access by understanding how linked apps interact. Zluri highlights potential threats based on the sensitivity of shared data, allowing you to assess and mitigate risks effectively.Zluri highlights potential threats based on the sensitivity of shared data, allowing you to assess and mitigate risks effectively.
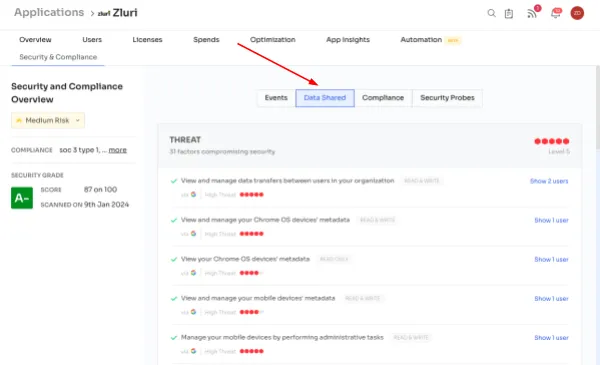
- Apps data shared information
- Compliance Details: Zluri provides you with comprehensive compliance details for each app, indicating specific frameworks with which the app aligns. The risk score increases with adherence to more compliance frameworks, assisting your team in ensuring regulatory alignment.In the below mentioned image, you can see Zluri in action, identifying compliance details seamlessly on its own!
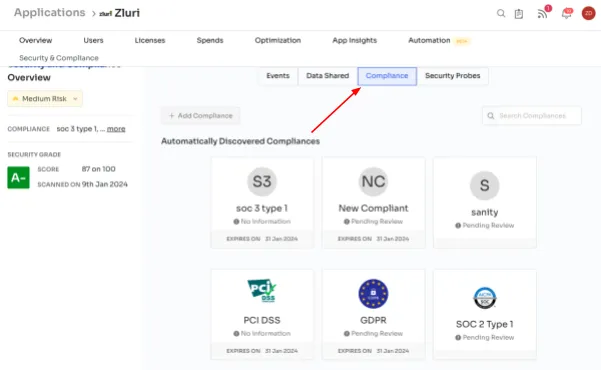
- Compliance information
- Security Probes: You can benefit from a transparent view of the technical scanning process, with the flexibility to customize scanning frequencies. Robust encryption algorithms and detailed logs of security-related activities enhance overall security management.
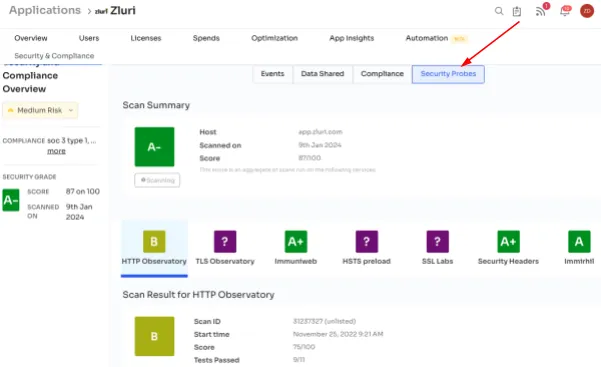
- Security probes information
Moreover, Zluri goes beyond security features, providing alerts regarding critical apps with scopes, threat levels, and risk levels.
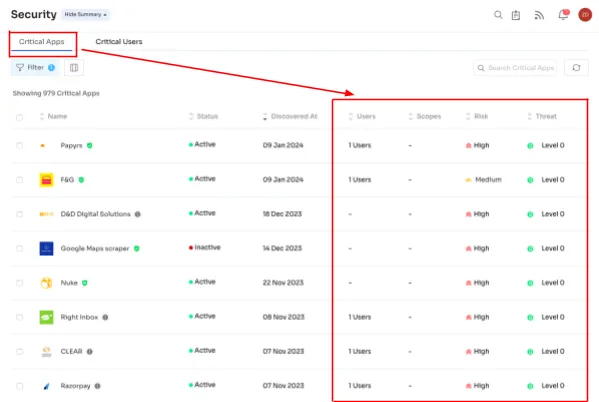
Critical appsIt also gives you information like users using the critical apps, their level of access to the critical apps, and more. This data helps you take proactive cautionary measures, prevent data compromise, and protect against cyber threats, supporting you in maintaining a secure digital environment.In addition to the security and compliance information, Zluri also provides an access review solution that empowers you to audit the users' access. In the event of any unauthorized access, Zluri provides the auto-remediation capability that helps you revoke the access or modify the access as per the requirement. This helps elevate your organization's security posture while effortlessly maintaining compliance with industry standards. For more details, schedule a demo with Zluri!
Also Read: If you’re interested in knowing the SPPM solutions, you can skim through SaaS security posture management tools
Top 11 CSPM Tools
Let's explore a wide range of CSPM tools and their advanced features that will help you improve your organization's security posture.
1. Lacework
Lacework, one of the notable CSPM tools, helps organizations gain visibility over cloud infrastructure. It continuously tracks every cloud interaction to reduce risks and ensure the services comply.
Lacework enables organizations to control multi-cloud environments and eliminate silos and blind spots. It also gives recommendations on how to fix non-compliant resources. Lacework is a single platform for all AWS, Google Cloud, Azure, and Kubernetes configurations. Integrations with tools like Jira and Slack help organizations accelerate remediation.
Key Features
- Continuous Monitoring and Visibility: Lacework provides real-time monitoring of your cloud environment, delivering unparalleled visibility into your infrastructure. You can gain insights into the security posture of their cloud deployments, identifying vulnerabilities and potential threats as they emerge.
- Automated Threat Detection: One of Lacework's standout features is its advanced threat detection capabilities. Leveraging machine learning and behavioral analytics, the platform automatically identifies and alerts your team to any anomalous activities, potential security breaches, or policy violations.
- Comprehensive Risk Assessment: Lacework offers a comprehensive risk assessment beyond mere threat detection. You can assess the impact of vulnerabilities and misconfigurations on their overall security posture, enabling informed decision-making to prioritize remediation efforts.
- Multi-Cloud and Hybrid Environment Support: Recognizing the diverse cloud landscapes that organizations operate in, Lacework seamlessly supports multi-cloud and hybrid environments. You can centralize security management across different cloud providers, ensuring a consistent and effective security posture across the entire infrastructure.
- Automated Compliance Checks: Lacework simplifies the often complex task of compliance management. With automated compliance checks, you can ensure that the cloud deployments adhere to industry regulations and internal policies. This not only reduces compliance-related risks but also streamlines the auditing process.
- Customizable Alerts and Reporting: Tailoring the security monitoring experience to your organization's specific needs, Lacework allows you to set up customizable alerts. The platform offers detailed reporting features, providing insights into security trends and helping your team demonstrate compliance to stakeholders.
Customer Rating
- G2: 4.4/5
- Capterra: 5/5
2. Fugue
Fugue, one of the best CSPM tools, empowers organizations to gain full visibility into cloud security posture and continuously comply with different regulatory requirements. It helps to visualize all cloud resources and find out if there are any compliance issues or misconfigurations. Fugue also evaluates cloud environments against industry standards like CIS. Further, it allows you to create custom compliance rules per your organization's needs.
Key Features
- Automated Compliance Assurance: Fugue takes the hassle out of compliance management by automating the assessment and enforcement of security policies. Your team can effortlessly ensure their cloud infrastructure aligns with industry standards and regulations, minimizing the risk of non-compliance.
- Real-time Visibility: Fugue provides real-time insights into your infrastructure's security posture, allowing you to identify and address vulnerabilities promptly. This visibility aids in proactively managing risks and maintaining a resilient cloud infrastructure.
- Infrastructure as Code (IaC) Security: Fugue integrates seamlessly with Infrastructure as Code (IaC), ensuring security measures are implemented from the ground up. You can enforce security policies at the code level, preventing misconfigurations and vulnerabilities before they manifest in the live environment.
- Risk Assessment and Prioritization: Fugue doesn't just highlight security issues; it prioritizes them based on potential impact and risk. You can focus the efforts on addressing the most critical vulnerabilities first, optimizing resource allocation, and enhancing the overall security posture of the cloud infrastructure.
- Continuous Monitoring and Remediation: Security is an ongoing process, and Fugue recognizes this by providing continuous monitoring capabilities. It identifies issues and offers automated remediation, ensuring that your cloud environment remains secure even as it evolves over time.
- Collaborative Security Management: Fugue fosters collaboration among your IT team by providing a centralized platform for security management. With features like role-based access control, your team can work cohesively to secure the cloud infrastructure and streamline the security management process.
Customer Rating
- G2: 4.8/5
3. Prisma Cloud
Prisma Cloud boasts an intuitive CSPM tool by Palo Alto Network, ensuring that your security team can easily navigate and utilize its features. The dashboard presents a comprehensive overview of the security landscape, allowing for quick assessments and informed decision-making. The simplicity of the interface contributes to a streamlined experience, making it a valuable tool for your IT team.
Prisma Cloud increases visibility in cloud environments and significantly reduces the need to respond to security incidents. Threat Stack sends alerts for any anomalous behavior and helps to maintain continuous compliance.
Key Features
- Real-time Risk Visibility: Prisma Cloud provides real-time visibility into its cloud infrastructure's security posture. With continuous monitoring and assessment capabilities, it identifies potential risks and vulnerabilities, enabling proactive responses to threats before they escalate.
- Compliance Assurance: Navigating through the intricate web of compliance requirements can be challenging. Prisma Cloud simplifies this process by automating compliance checks against industry standards and regulations. This ensures that your cloud environment adheres to the necessary security protocols, giving you peace of mind.
- Cloud-Native Security: Tailored for cloud-native environments, Prisma Cloud seamlessly integrates with popular cloud platforms. Its support for multi-cloud architectures ensures that your team can maintain security consistency across diverse infrastructures, enhancing overall operational efficiency.
- Automated Remediation: Prisma Cloud goes beyond mere detection, offering automated remediation for identified security issues. You can set predefined policies to address vulnerabilities swiftly, reducing the manual workload and fortifying the security posture of the cloud infrastructure.
- Threat Intelligence Integration: Prisma Cloud integrates threat intelligence, providing up-to-date information on the latest cybersecurity risks. This proactive approach helps organizations mitigate potential threats promptly, bolstering the resilience of their cloud environments.
Customer Rating
- G2: 3.9/5
- Capterra: 4/5
4. Trend Micro Cloud One Conformity
Trend Micro Cloud One Conformity, one of the best CSPM tools, provides comprehensive visibility into cloud infrastructure. It monitors the entire cloud environment in real time and provides alerts for any misconfiguration. One Conformity helps organizations to improve their cloud security and compliance posture. It also gives a view of risk status and resolves violations with step-by-step guides or auto-remediation.
Key Features
- Real-Time Visibility and Monitoring: Cloud One Conformity provides you with real-time visibility into their cloud environments. This feature empowers them to monitor the security posture of their assets continuously.
- Automated Compliance Checks: Streamlining compliance management, Cloud One Conformity automates the process of checking your cloud infrastructure against industry best practices and regulatory standards. This ensures adherence to compliance requirements and saves time and resources that would otherwise be spent on manual audits.
- Continuous Threat Detection: Equipped with advanced threat detection capabilities, Cloud One Conformity actively identifies vulnerabilities and potential risks within your cloud environment. This proactive approach enables you to stay one step ahead, addressing security issues before they escalate and impact business operations.
- Customizable Policy Enforcement: Recognizing each organization's unique needs, Cloud One Conformity offers customizable policy enforcement. This security posture management solution ensures the tool adapts seamlessly to diverse cloud architectures.
- Remediation Workflow Integration: Cloud One Conformity integrates a remediation workflow that simplifies the process of fixing vulnerabilities. Your team can implement corrective actions directly from the platform, minimizing downtime and reducing the window of exposure to potential threats.
- Multi-Cloud Support: Acknowledging the prevalence of multi-cloud environments, Cloud One Conformity supports various cloud service providers. This adaptability allows your team to consolidate security management across different platforms, promoting a unified and consistent approach to cloud security.
Customer Rating
- G2: 4.6/5
5. CheckPoint CloudGuard
CheckPoint CloudGuard, a notified CSPM vendor, empowers organizations to gain visibility and control across multi-cloud environments. It helps to automate cloud security and provides advanced threat prevention for all cloud assets. CloudGuard defends and monitors cloud environments from different threats and vulnerabilities. It automatically ensures users conform to regulatory requirements and security best practices and updates users on security and compliance posture.
Key Features
- Automated Cloud Security Assessment: CloudGuard's automated assessment capabilities empower you to thoroughly evaluate your cloud security posture. By analyzing configurations, permissions, and potential vulnerabilities, the solution provides a clear picture of your organization's security landscape, facilitating proactive risk mitigation.
- Real-time Threat Intelligence: The solution integrates seamlessly with threat feeds, continuously monitoring your cloud environment for emerging risks. IT managers can make informed decisions and swiftly respond to evolving security challenges, bolstering the resilience of their cloud infrastructure.
- Policy Enforcement and Compliance: CloudGuard simplifies the enforcement of security policies and ensures compliance with industry regulations. You can define and enforce policies consistently across multiple cloud platforms, minimizing the risk of misconfigurations and ensuring adherence to compliance standards.
- Visibility and Monitoring: Gain a comprehensive view of your cloud environment through CloudGuard's advanced monitoring capabilities. This heightened visibility allows for proactive threat detection and rapid response, reinforcing the security posture of your cloud assets.
- User-Friendly Dashboard and Reporting: CloudGuard's intuitive dashboard provides a user-friendly interface to monitor and manage cloud security effectively. The solution generates detailed reports, offering insights into security incidents, compliance status, and overall system health.
- Integration with DevOps Workflow: CloudGuard aligns with your organization's agile development practices by recognizing the importance of seamless integration with DevOps processes. You can effortlessly incorporate security into the DevOps workflow, minimizing friction between security and development teams while maintaining the integrity of cloud environments.
Customer Rating
- G2: 4.4/5
6. Orca Security
Orca Security, one of the notable CSPM tools, provides a comprehensive view of cloud security posture and, shows issues in misconfigurations anywhere in the entire cloud infrastructure, and also suggests recommendations. It is an easy tool to set up and integrate with your cloud environment within a few minutes. Orca cloud security posture management platform is an easy-to-use and quick-to-start tool.
Key Features
- Deep Visibility without Agents: Orca Security offers unparalleled visibility into your cloud environment without the need for any agents. This agentless approach eliminates the hassle of deployment and maintenance, allowing IT managers to understand their cloud security posture better.
- Continuous Monitoring and Risk Assessment: With Orca Security, you can automatically assess risks and vulnerabilities, providing proactive insights into potential security gaps. This enables your IT team to address issues promptly, reducing the risk of security breaches and ensuring a resilient security posture.
- Compliance Assurance: The tool comes equipped with predefined policies and regulatory frameworks, making it easier to ensure that your cloud infrastructure adheres to industry standards and specific compliance requirements.
- Contextualized Security Alerts: Orca Security goes beyond generic alerts by providing contextualized information. This feature streamlines the response process and enhances the overall effectiveness of the security strategy.
- Seamless Integration with Existing Tools: Orca Security seamlessly integrates with existing IT tools and workflows to facilitate a smooth transition. This ensures that the implementation of the CSPM tool does not disrupt ongoing operations, and IT managers can easily incorporate it into their existing security stack.
Customer Rating
- G2: 4.6/5
- Capterra: 4.8/5
7. CrowdStrike Falcon Cloud Security
CrowdStrike Falcon Cloud Security, one of the prominent CSPM vendors, is designed to fortify your organization's cloud security posture. It provides a holistic approach to threat detection, prevention, and response, specifically tailored to the cloud environment's challenges. By leveraging advanced technologies, Falcon ensures that your cloud infrastructure remains resilient against evolving cyber threats.
Key Features
- Real-time Threat Detection: Falcon Cloud Security excels in real-time threat detection, leveraging artificial intelligence and machine learning to identify and neutralize potential security risks. With continuous monitoring, the platform offers proactive defense against a wide range of cyber threats, ensuring your cloud environment remains secure.
- Cloud Security Posture Management (CSPM): A standout feature of Falcon is its Cloud Security Posture Management tool, which gives you a granular view of its organization's cloud security landscape. This tool empowers you to assess, monitor, and manage security configurations, ensuring compliance with industry standards and internal policies.
- Automated Remediation: Falcon Cloud Security goes beyond detection by providing automated remediation capabilities. The platform can automatically take corrective actions, minimizing the impact and reducing the response time needed to address security incidents.
- Threat Intelligence Integration: Falcon Cloud Security seamlessly integrates threat intelligence feeds to stay ahead of emerging threats. This ensures your organization benefits from the latest insights into evolving cyber threats, enabling proactive defense strategies and informed decision-making.
- User-friendly Dashboard: Understanding the importance of user experience, Falcon offers a user-friendly dashboard that provides a comprehensive overview of your cloud security posture. You can easily navigate through key metrics, alerts, and reports, facilitating efficient monitoring and management.
Customer Rating
- G2: 4.6/5
8. Zscaler Posture Control
Zscaler Posture Control is a cloud security posture management platform that helps your organization gain visibility and mitigate violations across cloud environments. Further, it ensures adherence to the industry regulations so that organizations remain compliant.
It identifies misconfigurations and prevents data breaches. Zscaler CSPM ensures that configurations of all cloud applications follow industry and organizational best practices.
Key Features
- Real-time Visibility: Zscaler Posture Control provides you with unparalleled real-time visibility into their cloud environments. This complete view empowers your IT team to promptly identify and rectify potential vulnerabilities.
- Automated Compliance Checks: Simplify the complex task of compliance management with Zscaler's automated checks. Ensure that your cloud configurations align with industry standards and internal security policies. Receive instant alerts and recommendations for any deviations, enabling proactive remediation and adherence to regulatory requirements.
- Risk Assessment and Prioritization: Streamline your security efforts with Zscaler's risk assessment and prioritization capabilities. Identify high-risk areas that demand immediate attention, allowing you to allocate resources strategically.
- Policy Enforcement Across Multi-Cloud Environments: Zscaler Posture Control excels in providing consistent policy enforcement across diverse cloud platforms. Manage security policies effortlessly, ensuring uniform protection across your organization's entire cloud infrastructure. This feature not only simplifies operations but also enhances the overall security posture.
- Continuous Monitoring and Threat Detection: Leverage Zscaler's continuous monitoring and threat detection capabilities to stay ahead of evolving cyber threats. The tool's advanced threat intelligence ensures that your organization is equipped to detect and respond to emerging threats promptly.
Customer Rating
- G2: 4.5/5
- Capterra: 4.1/5
9. CloudCheckr
CloudCheckr, one of the best CSPM solutions, helps your organization monitor for secure AWS and Microsoft Azure cloud configurations to maintain posture and ensure compliance with different standards. Your IT team can implement various cloud security best practices with the help of CloudCheckr. It sends alerts for any deviation from cloud security standards to prevent security breaches.
With features ranging from continuous monitoring and compliance to automated best practice checks, CloudCheckr empowers you to navigate the complexities of cloud security with confidence. Stay ahead of potential threats, optimize costs, and achieve a resilient cloud infrastructure with CloudCheckr as your comprehensive CSPM tool.
Key Features
- Continuous Monitoring and Compliance: CloudCheckr provides real-time visibility into your cloud environment, allowing you to monitor and assess the compliance of your infrastructure against industry standards and regulatory requirements. This ensures that your organization remains resilient despite ever-changing security landscapes.
- Automated Security Best Practices: Take advantage of CloudCheckr's automated best practice checks that scan your cloud configuration for potential vulnerabilities. This feature empowers you to proactively address security gaps and implement corrective actions, reducing the risk of security breaches and ensuring a robust security posture.
- Customizable Alerts and Notifications: Stay ahead of potential security threats with CloudCheckr's customizable alerting system. Tailor alerts to match your organization's specific needs, allowing you to respond promptly to any suspicious activities or deviations from established security policies.
- Cost Optimization and Resource Utilization: Beyond security, CloudCheckr offers insights into your cloud spending and resource allocation. By identifying underutilized resources and recommending optimization strategies, CloudCheckr helps you balance cost efficiency and security without compromising performance.
- Comprehensive Risk Assessment: CloudCheckr provides a comprehensive risk assessment beyond mere compliance checks. Evaluate your cloud environment's risk posture, prioritize security issues based on severity, and make informed decisions to fortify your organization against potential threats.
- Multi-Cloud Support: As organizations increasingly adopt multi-cloud strategies, CloudCheckr stands out with its ability to support multiple cloud platforms. Whether your infrastructure is on AWS, Azure, Google Cloud, or a combination thereof, CloudCheckr offers a unified solution for streamlined security management.
Customer Rating
- G2: 4.1/5
- Capterra: 5/5
10. BMC Helix Cloud Security
BMC Helix Cloud Security is a comprehensive CSPM solution crafted for you, prioritizing security without compromising efficiency. With its robust features, real-time monitoring, and automation capabilities, BMC Helix Cloud Security empowers you to proactively manage your cloud security posture, ensuring a resilient defense against evolving cyber threats. Stay ahead in the cloud security game with BMC Helix Cloud Security – your ally in securing the future of your business.
Key Features
- Real-time Visibility and Monitoring: BMC Helix Cloud Security provides unparalleled real-time visibility into your cloud infrastructure. Track your assets, configurations, and vulnerabilities across multi-cloud environments effortlessly.
- Automated Security Assessments: BMC Helix Cloud Security automates security assessments, scanning your infrastructure for misconfigurations and vulnerabilities. This proactive approach ensures that potential risks are identified and addressed promptly, minimizing the exposure window.
- Policy Enforcement and Compliance: With BMC Helix Cloud Security, you can enforce security policies consistently across your cloud environment, ensuring adherence to industry standards and compliance requirements. Stay ahead of audits and regulatory checks effortlessly.
- Incident Response and Remediation: BMC Helix Cloud Security empowers you with swift incident response capabilities. Detect and respond to security incidents promptly and leverage automated remediation processes to mitigate risks efficiently. Minimize downtime and ensure the continuity of your operations.
- Customizable Dashboards and Reports: BMC Helix Cloud Security provides customizable dashboards and reports, allowing you to tailor the information to your specific needs. Monitor key performance indicators, track security trends, and generate reports facilitating informed decision-making.
Customer Rating
- G2: 4.5/5
11. Microsoft Defender for Cloud
Microsoft Defender by Cloud stands as a comprehensive and user-friendly CSPM tool. It streamlines your compliance efforts and empowers your team with the tools they need to safeguard your organization's digital assets
Microsoft Defender by Cloud employs cutting-edge threat detection algorithms that operate in real-time. This ensures prompt identification and mitigation of potential security threats, safeguarding your cloud infrastructure against evolving cyber threats.
Key Features
- Automated Security Assessments: Streamline your security protocols with automated security assessments offered by Microsoft Defender by Cloud. Conducting regular assessments ensures that your cloud environment adheres to industry best practices, minimizing vulnerabilities and enhancing overall security posture.
- Continuous Compliance Monitoring: Microsoft Defender by Cloud provides insights into your cloud configuration's compliance status, helping you address any deviations promptly and maintain a secure and compliant environment.
- Intuitive Security Dashboard: Microsoft Defender by Cloud presents a user-friendly interface, offering a consolidated view of your cloud security status, enabling you to make informed decisions and respond swiftly to potential threats.
- Integrated Threat Intelligence: Microsoft Defender by Cloud integrates seamlessly with Microsoft's extensive threat intelligence network, ensuring that your defenses are updated in real-time to counteract emerging threats.
- Adaptive Security Policies: Tailor your security policies to your organization's unique needs with adaptive security policies. Microsoft Defender by Cloud allows you to customize security configurations, providing a flexible approach to address specific requirements and mitigate potential risks.
- Incident Response and Investigation Tools: In the event of a security incident, Microsoft Defender by Cloud equips your team with robust incident response and investigation tools. Quickly identify an incident's source, scope, and impact, facilitating a swift and effective response to minimize any potential damage.
Customer Rating
- G2: 4.5/5
- Capterra: 4/5
Choose the Suitable CSPM Tool for Your Organization
In today's market, several CSPM tools await your consideration. Navigate through the array of options, explore the unique offerings, and delve into the functionalities each tool brings to the table. Assessing how these tools align with your organizational requirements is crucial. It's not just about the present – the chosen tool should seamlessly integrate with your budget constraints and scale to accommodate your future growth.
In addition to features, don't overlook the importance of a robust knowledge base, dependable support, and user-friendly interfaces. Opting for a cloud security posture management (CSPM) tool that combines efficient support, swift onboarding, and a comprehensive knowledge base is a strategic move. Such a tool, meeting your expectations and aligning with your budgetary considerations, ensures a seamless experience while addressing common concerns in your cloud security framework.
FAQs
Why do you need a CSPM tool?
Elevating your security posture, CSPM tools enable enterprises to proactively pinpoint and address potential risks through robust security assessments and automated compliance monitoring. It's a common misconception for organizations transitioning to the cloud to rely solely on their hosting provider for security, overlooking the need for a comprehensive solution to fortify their digital landscape.
What is an example of CSPM?
In uncovering risks across multi-cloud environments, a trustworthy Cloud Security Posture Management (CSPM) tool goes beyond the surface by offering advanced threat intelligence. This intelligence is pivotal in identifying both external and internal threats. These threats encompass various scenarios, such as malicious actors trying to exploit stolen credentials, instances of crypto mining, ransomware attacks, and other forms of malware and hacking endeavors.
What is CSPM in AWS?
Use Cloud Security Posture Management (CSPM) tools to elevate your cloud security stance. These tools are crucial in conducting ongoing compliance assessments and pinpointing potential risks linked to evolving workloads. Discover effective strategies for prioritizing security controls specifically tailored for safeguarding sensitive assets within your AWS environment.
What is a cloud workload protection platform?
Experience the power of a Cloud Workload Protection Platform (CWPP), an integrated cloud security solution designed to provide seamless and ongoing threat monitoring and detection for diverse cloud workloads within various modern cloud environments.
What is a cloud access security broker?
Elevate your cloud security with a cloud access security broker (CASB), a solution that instills zero-trust access control and robust policy enforcement within cloud environments. All traffic destined for the cloud undergoes scrutiny through the CASB solution, empowering it to seamlessly enact and uphold corporate security policies.







.png)

.svg)














