With their increased adoption in recent times, SaaS apps make up for the major portion of shadow IT. They are the main driver of shadow IT, and this is a growing concern for IT teams.
SaaS applications are easily accessible and have led users to use them without the knowledge of IT teams. You need to provide your email address and credit card details; you can sign up for apps within a minute. Some SaaS providers don’t even ask the users for their credit card details to try it.
Freemium business models have further made the sign-up process more effortless. You need not pay anything upfront for the basic features of a few SaaS apps. In addition, there is no involvement of complex setup, unlike the on-premise software.
For example, your product team is working on a new project. The IT teams have already subscribed to Adobe XD, but the team decides to use Figma for this project. They thought this app would better simplify their work and make it more productive.
SaaS is accelerating the growth of shadow IT. According to research by Netspoke, 97% of cloud apps used in the enterprise are shadow IT, unmanaged, and often freely adopted.
So, the need to find new ways to eliminate shadow IT is imperative. The old methods that are followed in the majority of organizations are mainly focused on on-premise software. But this is not sufficient for the SaaS world.
Identification of apps is the preliminary step in the elimination of shadow IT. In this post, we have discussed the different ways to identify shadow IT apps and eliminate them.
6 Ways to Identify Shadow IT Apps

1. Conduct Employees Survey
A survey is a manual process for detecting shadow IT apps. When a large number of employees are involved, it is pretty time-consuming to conduct a survey. It is good for small organizations but not feasible and efficient for larger organizations.
The survey is entirely dependent on what information users are providing. The users might take their own time to respond to the survey. Sometimes, even after multiple reminders, the response time is slower.
Since accessibility is not a problem, users tend to use new apps to simplify their work. Due to this, the survey needs to be conducted regularly to avoid the growth of shadow IT in the organization.
If the survey is conducted monthly or quarterly, only then can update the data periodically. You have to wait for the entire period to get the complete data and stay up to date. Even then, the data is not accurate.
Manually verifying the reports is not impossible, leading to a higher rate of inaccuracy. It is because sometimes the users miss mentioning any application intentionally or unintentionally.
2. Single Sign-On for Access Management
SSO or single sign-on is a convenient way to log into applications needing an identification source to validate and authorize the users.
SSO is one such way that can help you to identify the app's users' use as they log in. But it fails to identify all the SaaS apps as not all apps require SSOs to log in.
Additionally, SSO setup requires considerable effort and reasonable time to configure SSO for each application. This is why app providers offer SSO as a feature with the highest pricing tier and is one of the most expensive ways to discover apps in the organization.
The implementation of SSO takes longer than expected. Because each IT environment is different, and customization requirements require additional steps.
The entire technology is dependent on the service providers and identity providers to link their systems together. Additionally, many standards are associated with SSO like LDAP, CAS, SAML, etc., and each vendor has a unique implementation creating incompatibility issues. Hence, making the integration difficult.
3. CASB to Secure Cloud Data
A cloud access security broker (CASB) helps primarily in scanning security threats and keeping your cloud data safe. In addition, it acts as a source to discover the unsanctioned apps by the IT teams as it works as a middleware between your organizational infrastructure and cloud service providers.
CASB systems are suitable for visibility but mainly focus on IaaS and Paas. CASB fails to give you complete visibility of SaaS apps. Hence, you might not have complete information about the discovery of shadow IT apps, leading you to a step back in eliminating the shadow IT apps.
For example, if you are using Slack and have 15 channels in addition to 100 different teams, CASB will not provide specific information like who is operating these channels. Neither any information associated with the license is provided.
Moreover, CASB becomes a single point of failure. That means, if for any instance, it fails, there will be no traces to discover the unsanctioned apps. Since the source to identify the apps is entirely dependent on the CASB.
4. Use IT Asset Management Tools
IT asset management processes involve managing all your organization's IT assets and are mainly focused on hardware like servers, computers, printers, etc. There are multiple dedicated software applications for asset management to manage your assets efficiently.
Note that the traditional ITAM tools mainly focus on harware assets and on-premise apps. Although they help to discover and manage the hardware assets, the bulk of shadow IT lies in the form of SaaS apps.
5. Software Asset Management
Software asset management (SAM) is a business practice to manage the software applications within the organization but majorly focuses on on-premise software. It manages the traditional licenses that are installed on your computer.
In today's world, SaaS contributes a lot to shadow IT as SaaS applications are easier for teams and employees to adopt new tools for productivity, collaboration, and training.
Through SAM tools, you will be able to detect the on-premise software in your organization. Note that the focus of most SAM tools is on traditional licenses and not the cloud data.
6. SaaS Management Platform - The Best Solution to Eliminate Shadow IT
The emergence of cloud or disruptive digital technologies has further aggravated the shadow IT. Shadow IT includes purchases of SaaS apps, AWS cloud and colocation, or Rackspace.
SaaS apps contribute majorly to the growth of shadow IT. When employees purchase independently SaaS apps to increase productivity and streamline their work. It is due to the easy accessibility of SaaS apps and the many options available in the market.
Zluri, a SaaS management platform, helps the organization eliminate shadow IT with adequate sources of SaaS discovery. The visibility that Zluri provides to the IT leaders facilitates the empowerment of their business units, can measure value, determine thresholds for centralized governance, and benchmark costs.
With Zluri, there is no requirement to disturb the users, unlike in surveys. It assists you in staying up to date on apps being used and left idle to take relevant actions. Our primary focus is on SaaS, so it is best to discover SaaS apps.
Zluri is cost-efficient as compared to other tools. It provides all the information associated with SaaS apps, licenses, security and compliance, and more. It has 300+ directly integrated SaaS apps, and there is no dependency on other tools to discover the SaaS apps in the organization.
Zluri uses nine discovery methods to find 100% of SaaS apps accurately in your organization: MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
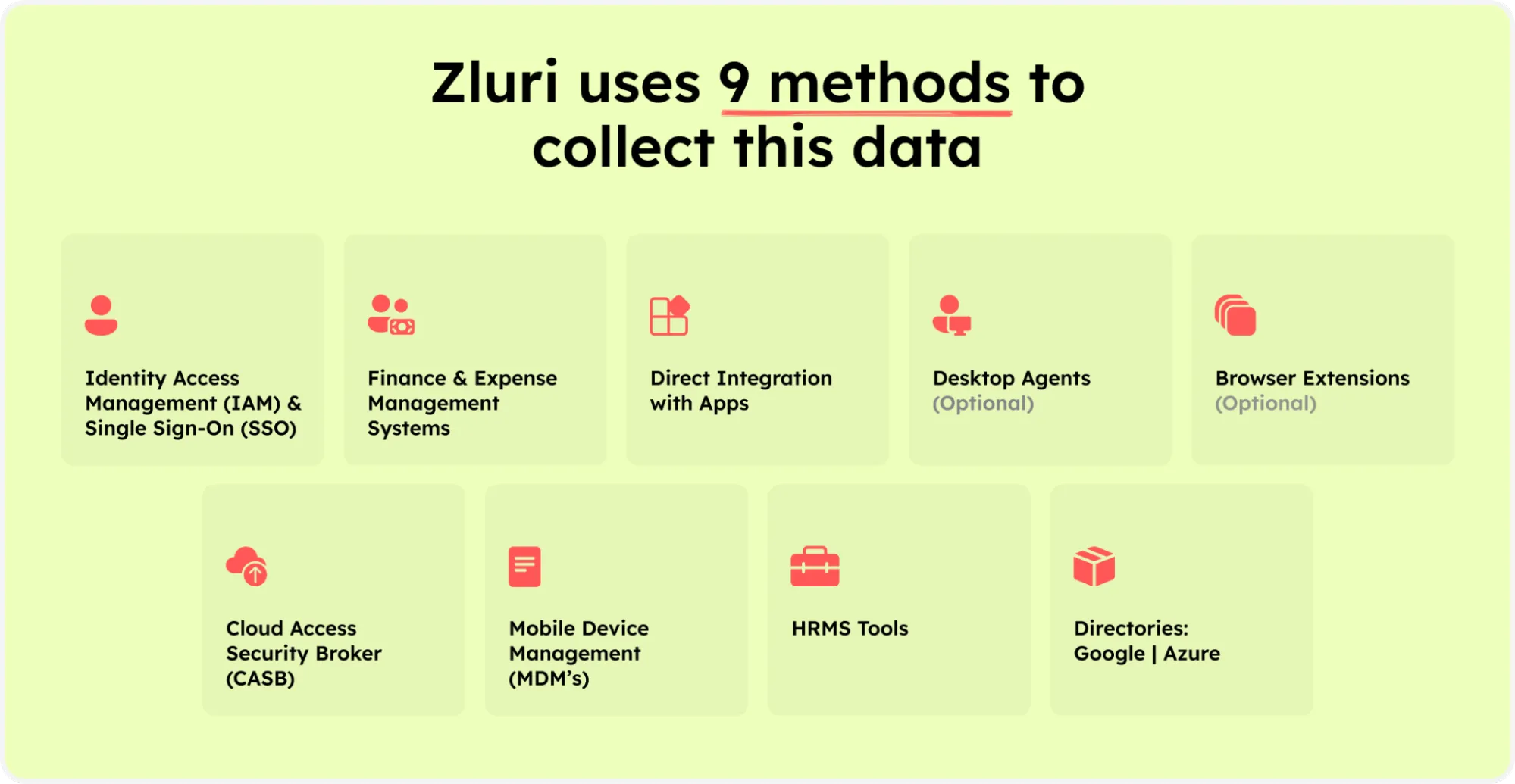
Zluri’s nine discovery methods
- Single Sign-On (SSO) and Identity Providers (IDP): Zluri connects with your SSO and ID providers such as Google Workspace, Okta, Azure Active Directory, etc. It traces the app users, their departments, hierarchy, and type of applications.
You have control over the source for these data points. To set your source for department, users, and their designation, visit Your Organisation in Settings.
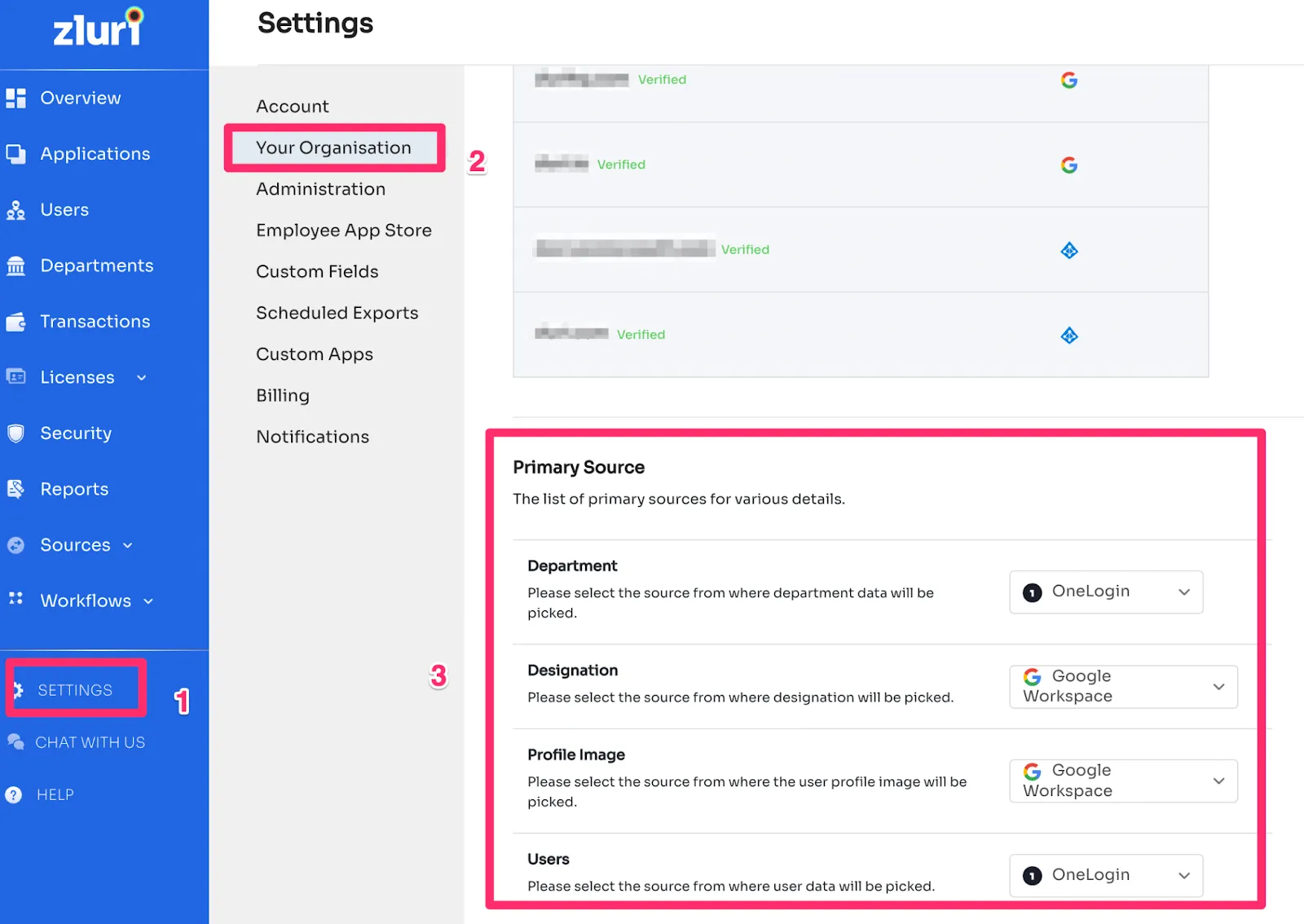
It collects different types of data, starting with directory information that provides information about the users. A list of authorized apps via your SSO. Login events such as user sign-in attempts, the number of times they accessed the apps, and if they were successful.
Last but not least is data shared with third-party apps. The last thing we collect from your SSO is what information is requested by apps for authentication. Example, name, email, or other details.
- Finance and Expense Management Systems: Zluri gets hold of the apps missed in SSO and IDP levels via this discovery method. To collect further applications, we connect with your expense and finance management systems such as Quickbooks, Netsuite, Zoho books, etc.
It finds the apps purchased by the employees either with the corporate card or their personal card. It further collects the transaction details, such as the amount spent on apps and the expense date.
The basic idea behind collecting the transaction data and the transaction's value is to find the apps mapped with the transactions. - Direct Integration with Apps: Zluri can obtain the information directly from apps, connecting directly with 300+ SaaS apps to get app-level usage insights. Each integration with apps takes 2 mins to join and is a one-time setup during the onboarding process. The connection happens at the admin level.
We can offer you data access levels, license tiers, and access and audit logs with direct integration.
Access level gives you an understanding of which users have access to the SaaS app and their permission levels like a user or admin. The license tier will help you get visibility of each user's license plans, such as plan, pricing, and features available in the tier. Access and audit logs will help you understand the changes made to know the app usage. - Desktop Agents (Optional): A desktop agent is an optional SaaS discovery method that helps to keep track of fundamental insights such as device information, apps installed, and time spent on each app.
With desktop agents, we collect the number of apps installed on a device, device-level information like product ID, hardware information, etc., app sign-in and sign-out details, and all the apps running in the background.
Though it's optional for users and not mandatory for Zluri to perform its core tasks, we still focus on the previous methods to achieve the best to surface your SaaS landscape. - Browser Extensions (Optional): Browser extensions run locally in the organization to read browser activities and report them to Zluri's server for analysis. You can find SaaS apps in Chrome, Firefox, Microsoft Edge, and Safari extensions.
Browser extensions are optional; we do not use them to read the cookies or the browser history. Our focus is to collect data on the websites visited by the users, like the URL, title, timestamp of opening/closing the tab, etc.
With Zluri, you can gain real-time visibility into all the SaaS apps across the organization. It offers 100% accurate SaaS discovery methods that will help in eliminating shadow IT and enable you to stay compliant and the data secured.
Now IT directors can work collaboratively with other departments and add value to the business with automated data discovery of SaaS apps.









.svg)














