Meeting ISO 27001 compliance’s standard can be complex and challenging. That's why we've curated this ISO 27001 checklist to help you easily navigate and ensure compliance that strengthens your organization's cybersecurity measures.
Managing information security is no small feat. You may be juggling numerous security protocols, training employees, and constantly updating software to prevent cyber threats. On top of that, the pressure to meet ISO 27001 standards adds another layer of complexity. You might find yourself asking, "Where do I even start?" or "How can I ensure we don't miss any crucial steps?"
Fortunately, there's a way to streamline this process: an ISO 27001 checklist. This checklist breaks down the standard into manageable tasks, guiding you step-by-step through the requirements. It ensures that you cover all bases, from identifying potential risks to implementing robust security controls.
With ISO 27001 checklist, achieving ISO 27001 compliance becomes much more manageable, allowing you to focus on maintaining a secure and resilient IT environment.
Benefits of ISO 27001 Checklist
The benefits of an ISO 27001 checklist are significant:

- Risk Management: ISO 27001 checklist helps identify and assess risks to information security, enabling you to take proactive steps to mitigate them.
- Compliance Assurance: Regular use of the checklist ensures ongoing compliance with ISO 27001 standards, which can be vital for meeting regulatory and legal requirements.
- Enhanced Security Posture: By adhering to ISO 27001 checklist, you can ensure that security measures are not only in place but are also effective and aligned with best practices.
- Efficiency in Audits: ISO 27001 checklist streamlines the preparation for internal and external audits by clearly outlining what needs to be reviewed and documented.
- Improved Management Support: When you and your team show organized and documented compliance efforts, they are more likely to gain support from senior management for further security initiatives or investments.In this article, we will explore the steps involved in the ISO 27001 checklist to efficiently adhere to the standard.
10 Steps Involved in a ISO 27001 Checklist
Now, let’s discuss the ISO 27001 checklists in detail.
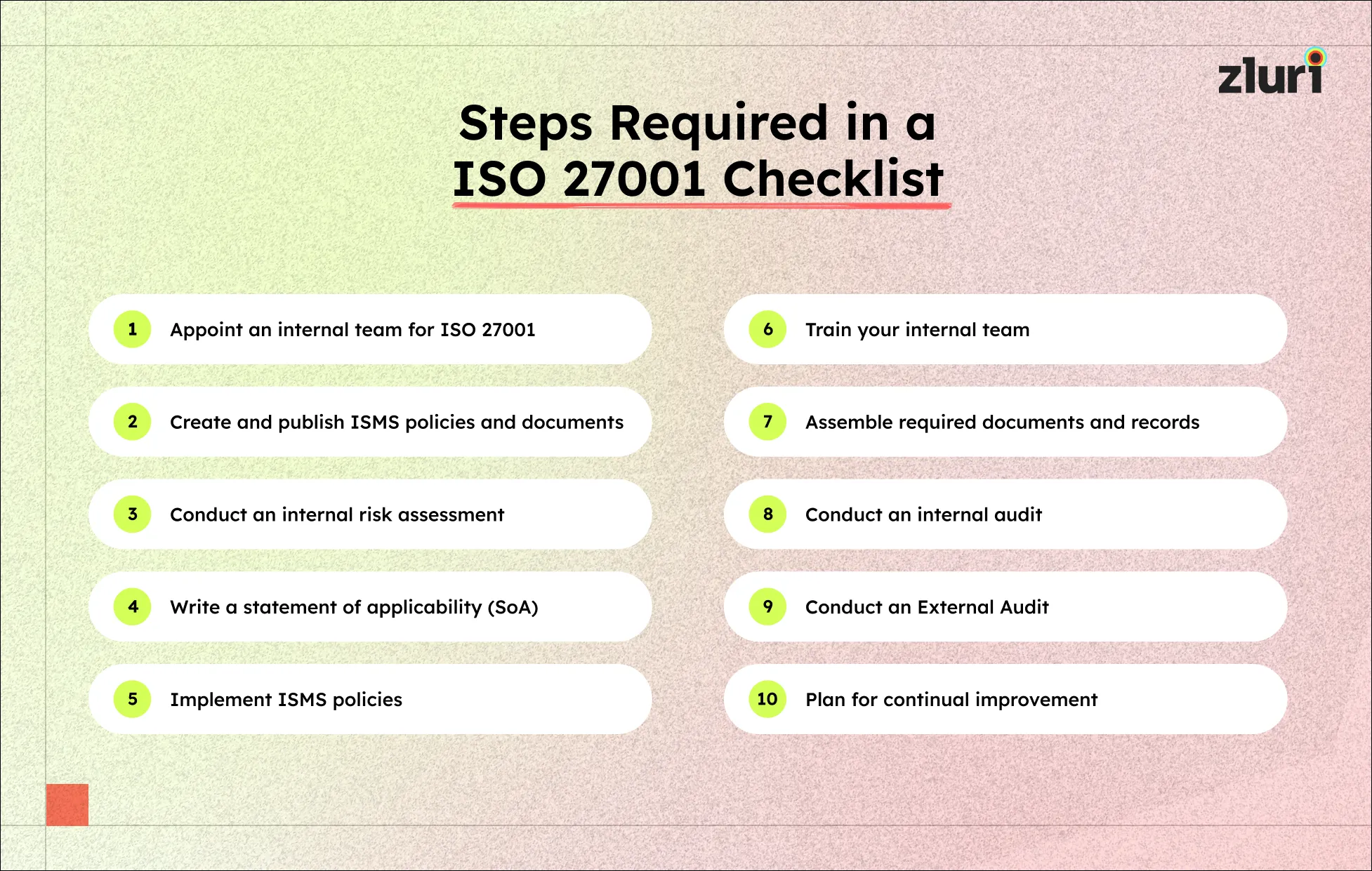
1: Appoint an internal team for ISO 27001
One of the first steps in achieving ISO 27001 certification is to appoint an internal team dedicated to this task. This team will be instrumental in overseeing the entire implementation process from start to finish.
The team should include an IT team that understands your company's IT infrastructure, risk management, and security processes, as well as representatives from various departments such as HR, legal, and operations. This diversity ensures all aspects of your organization are considered in the information security management system (ISMS).
The appointed team's first task is to familiarize themselves with the ISO 27001 standards and identify the scope of the ISMS. This involves determining which parts of your organization will be covered by the ISMS and what information assets need protection. Understanding these elements is crucial for developing an effective security management system that is compliant with ISO 27001 requirements.
Additionally, the internal ISO 27001 team will be responsible for developing policies and procedures that address the standard's security controls and objectives. This includes drafting the risk assessment methodology, setting up a risk management process, and ensuring continuous improvement mechanisms are in place.
2: Create and publish ISMS policies and documents
When working towards ISO 27001 certification, an essential step in your compliance checklist is to create and publish your Information Security Management System (ISMS) policies and documents. This step is crucial as it forms the backbone of your organization's security framework. It clearly outlines your company's stance and procedures for managing information security.
ISMS policies are formal guidelines and procedures that define how your organization manages and secures its information assets. The policies must cover various aspects such as risk management, employee roles and responsibilities, access control, incident management, and more. They should align with the specific requirements of ISO 27001, ensuring that every potential security issue is addressed.
Creating these documents involves several steps. Conduct a thorough risk assessment to identify your organization's potential threats and vulnerabilities.
Based on this assessment, develop policies that mitigate these risks effectively. These policies must be clear and accessible, ensuring all employees understand their responsibilities in upholding the organization's security protocols.
Once your ISMS policies and documents are drafted, management must formally approve them. This approval process validates the policies and demonstrates management's commitment to information security.
After approval, the next step is to publish these documents in a way that makes them readily accessible to all employees. They should be distributed through your internal communication channels, and training sessions should be conducted to familiarize everyone with the documents.
Moreover, ensure that policy updates are similarly distributed and compliance is regularly monitored and reviewed.
3: Conduct an internal risk assessment
.webp)
One crucial step in achieving ISO 27001 is conducting an internal risk assessment. This process involves identifying, evaluating, and prioritizing potential risks, such as cybersecurity threats to your organization's information security.
By conducting an internal risk assessment, you gain a comprehensive understanding of the potential threats and vulnerabilities that could compromise your organization's sensitive data. This proactive approach enables you to anticipate and mitigate risks before they escalate into security breaches or compliance failures.
Moreover, the internal risk assessment process allows you to prioritize risks based on their severity and likelihood of occurrence. By categorizing risks according to their impact on your organization's objectives, you can allocate resources more effectively to address the most critical vulnerabilities first, thereby maximizing your security posture.
Additionally, conducting an internal risk assessment fosters a culture of accountability and awareness within your organization. By involving key stakeholders from various departments in the risk assessment process, you promote cross-functional collaboration and ensure that security considerations are integrated into all aspects of your operations.
Furthermore, the insights gained from the internal risk assessment can inform strategic decision-making and resource allocation. By identifying areas of weakness or gaps in your current security measures, you can implement targeted controls and measures to strengthen your defenses and mitigate potential threats effectively.
4: Write a statement of applicability (SoA)
The statement of applicability (SoA) is like a roadmap specifically designed for your organization. It outlines the controls and measures necessary to address the risks identified during the information security risk assessment process. Think of it as a customized plan tailored to your organization's unique needs and circumstances.
So, how does this benefit you as an IT manager? Well, for starters, the SoA provides clarity. It clearly defines which security controls are relevant and applicable to your organization's information security management system (ISMS). This helps you focus your resources and efforts where they are most needed, avoiding unnecessary expenses or overlooking critical areas.
Moreover, the SoA serves as a communication tool. It communicates to internal and external stakeholders the specific security measures your organization has in place. This transparency builds trust and confidence, reassuring customers, partners, and regulators that you take information security seriously.
Furthermore, the SoA facilitates compliance. By mapping out how your organization meets the requirements of ISO 27001, it simplifies the auditing process. It provides auditors with clear evidence of your adherence to the standard, streamlines assessments, and potentially reduces compliance costs.
In addition, the SoA promotes continual improvement. As your organization evolves, so do the risks it faces. The SoA is not a static document but rather a living one that should be regularly reviewed and updated. This ensures that your security controls effectively address emerging threats and vulnerabilities.
5: Implement ISMS policies
Implementing ISMS policies is a crucial step in the ISO 27001 checklist for safeguarding sensitive data and ensuring the integrity of your organization's systems. By implementing ISMS policies, you can effectively establish a structured framework for managing and protecting your organization's information assets.
One of the key benefits of implementing ISMS policies is enhanced security posture. These policies provide clear guidelines and procedures for identifying, assessing, and mitigating information security risks. By following these policies, you can proactively address potential vulnerabilities and threats, thereby reducing the likelihood of security breaches and data leaks.
Moreover, implementing ISMS policies helps ensure compliance with regulatory requirements and industry standards. This can be particularly beneficial for organizations operating in industries where regulatory compliance is mandatory, such as healthcare or finance.
Furthermore, by establishing standardized processes and controls for managing information security, you can streamline their workflows and reduce the likelihood of errors or inconsistencies. This enhances productivity and helps mitigate the impact of security incidents by enabling swift and coordinated responses.
6: Train your internal team
As part of the ISO 27001 checklist, training your internal team is crucial to fortifying your organization’s defenses against cyber threats. Let’s explore why this step is indispensable and how it benefits your company.
- Investing in the training of your internal team cultivates a culture of security awareness within your organization. By imparting knowledge about information security practices, policies, and procedures, you empower your team to proactively recognize and respond to potential risks.
- Through comprehensive training programs, your team gains insights into handling confidential data securely, adhering to regulatory requirements, and implementing best practices in safeguarding information. This mitigates the risk of data breaches and instills confidence among stakeholders, including clients and partners, regarding your commitment to data protection.
- Furthermore, training your internal team fosters a responsive and agile security posture. Equipping your team with up-to-date knowledge and skills enables them to promptly detect and address emerging threats, thereby minimizing the potential impact on your organization’s operations and reputation.
- Investing in employee training demonstrates your organization’s dedication to compliance with industry standards such as ISO 27001. Compliance enhances your credibility and competitiveness and opens doors to new business opportunities.
- Furthermore, training your internal team contributes to long-term cost savings and efficiency gains. You mitigate the associated financial and reputational losses by reducing the likelihood of security incidents and data breaches.
7: Assemble required documents and records
Assembling the necessary documents and records is a pivotal step. This phase encompasses gathering an array of materials essential for demonstrating adherence to the ISO 27001 standards and ensuring that the organization's information security management system (ISMS) is robust and effective.
First and foremost, you must compile policies and procedures that outline the framework of your organization's ISMS. These documents serve as the cornerstone, delineating the approach toward information security, risk management, and compliance with ISO 27001 requirements.
Next, documentation related to risk assessment and treatment becomes indispensable. This includes risk registers, risk treatment plans, and evidence of risk mitigation activities. You must thoroughly understand potential risks to your organization's information assets and demonstrate proactive measures taken to mitigate these risks effectively.
Furthermore, records about the management of information security incidents are vital. Incident reports, investigation findings, and subsequent actions taken are all integral components. These records demonstrate the organization's capability to respond to security incidents promptly and provide valuable insights for the continuous improvement of the ISMS.
In addition, you must also gather evidence of compliance with legal and regulatory requirements relevant to information security. This may include compliance certificates, audit reports, and documentation of regulatory assessments. Ensuring alignment with external requirements enhances the organization's credibility and trustworthiness in the eyes of stakeholders.
8: Conduct an internal audit
One critical step in achieving this is conducting an internal audit as part of the ISO 27001 internal audit checklist. This audit is a systematic review of your organization's ISMS, ensuring it meets the stringent standards outlined by ISO 27001.
The internal audit is about assessing the effectiveness of your ISMS. It involves a thorough examination of your policies, procedures, and controls to identify any vulnerabilities or gaps that could compromise the security of your data. By conducting this audit, you're proactively identifying areas for improvement and taking preemptive measures to mitigate risks.
The internal audit process follows a structured approach. It begins with planning, where you define the audit's scope, objectives, and criteria. This phase is crucial for setting the direction and ensuring that the audit addresses key areas of concern. Next comes the execution phase, where auditors gather evidence, assess compliance, and identify any deviations from the established standards.
During the audit, auditors employ various techniques to evaluate the effectiveness of controls and processes. This may include reviewing documentation, interviewing personnel, and conducting on-site inspections. The goal is to understand how well the ISMS is functioning and whether it aligns with the requirements of ISO 27001.
Once the audit is complete, the next step is to analyze the findings. This involves identifying strengths, weaknesses, and opportunities for improvement within the ISMS. By analyzing the results, you can prioritize corrective actions and allocate resources effectively to address any identified deficiencies.
Moreover, the internal audit serves as a valuable tool for continuous improvement. By regularly reviewing and evaluating your ISMS, you can adapt to evolving threats and industry best practices. This proactive approach enhances security and demonstrates your commitment to maintaining a robust information security management framework.
9: Conduct an External audit
When it comes to ensuring the security of your company's information, conducting an external audit is a crucial step in the ISO 27001 compliance checklist. An external audit involves bringing in an accredited auditor from a trusted organization to assess your company's compliance with ISO 27001 standards.
The first step is selecting the right auditor for the job. It's important to choose an auditor who is accredited by a recognized certification body. These auditors have undergone extensive training and are equipped with the knowledge and expertise to effectively evaluate your company's information security management system.
Once you've chosen an auditor, they will thoroughly examine your company's policies, procedures, and controls to ensure they align with the requirements set forth in the ISO 27001 standard. This may involve reviewing documentation, interviewing key personnel, and performing on-site inspections.
During the audit, the auditor will assess your company's compliance with various aspects of ISO 27001, including risk management, access control, and incident management. They will identify any areas where your company may not be meeting the standard requirements and provide recommendations for improvement.
After the audit is complete, the auditor will issue a report detailing their findings and any non-conformities that were identified. This report will serve as a valuable tool for your company to address any gaps in its information security management system and work towards achieving full compliance with ISO 27001.
10: Plan for continual improvement
Continual improvement is a proactive approach to refining and enhancing your ISMS over time. It's about staying agile and responsive to emerging threats, evolving technologies, and changing business needs. It helps to ensure that your organization's security measures remain effective and resilient in the face of new challenges.
So, what does a plan for continual improvement entail?
- It involves establishing clear objectives and key performance indicators (KPIs) to gauge the effectiveness of your ISMS. These objectives should be aligned with your organization's overall strategic goals and reflect the evolving nature of the cybersecurity landscape.
- Regular monitoring and evaluation are essential. This means conducting regular audits, risk assessments, and security reviews to identify areas for improvement and measure progress against your objectives.
- Encourage feedback from employees at all levels, promote knowledge sharing and collaboration, and incentivize proactive risk management initiatives. By empowering your team to contribute ideas and insights, you can tap into a wealth of expertise and drive meaningful improvements to your ISMS.
- It's crucial to follow a structured approach to change management. Assess the potential impact of proposed changes, develop an effective implementation plan, and communicate effectively with stakeholders to ensure buy-in and minimize resistance.
Remember that continual improvement is an ongoing journey, not a one-time destination. Regularly revisit and revise your improvement plan in light of new developments, lessons learned, and feedback received. By staying proactive and adaptive, you can keep pace with evolving threats and maintain a resilient security posture that aligns with your organization's strategic objectives.
Once you are aware of the steps, it's highly important to leverage a suitable tool to automate the process to achieve compliance. There are several tools available in the market, but if you're looking for a solution to help you achieve ISO 27001 compliance, then Zluri can be a suitable fit. Let's learn how.
How can Zluri Help you Achieve ISO 27001 Compliance?
Ensuring compliance with ISO 27001 can be complex, especially when it comes to managing access rights efficiently. That's where Zluri steps in, offering a robust platform tailored to automate access reviews, a critical aspect of ISO 27001 compliance.
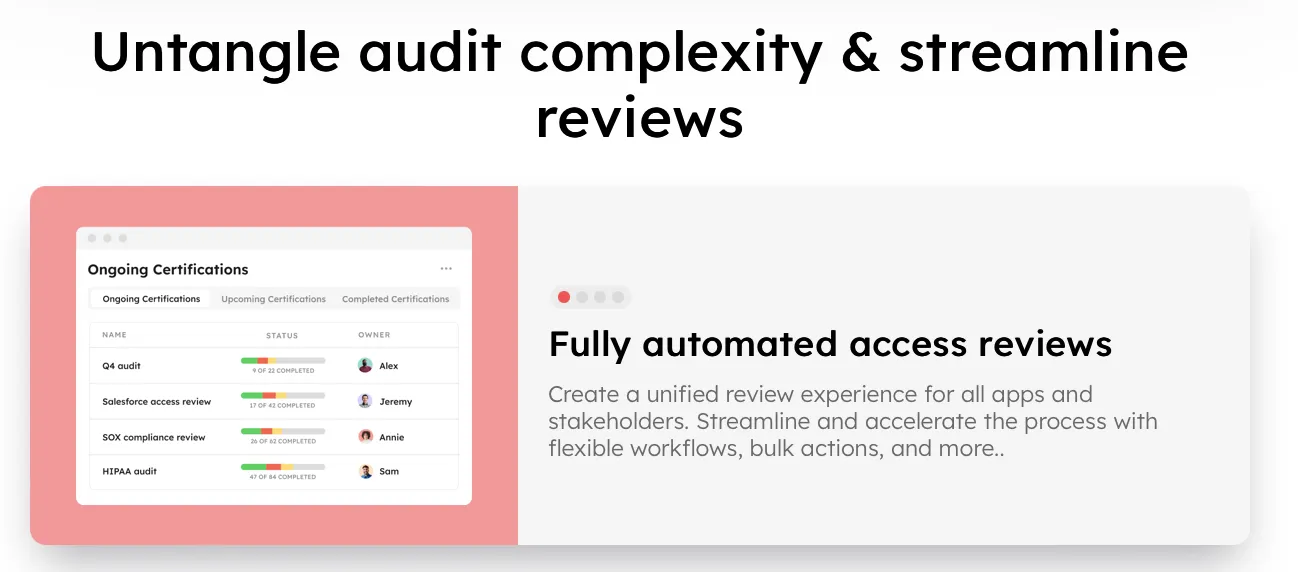
Let’s see how.
Automated Access Reviews: Zluri's platform simplifies the process of conducting access reviews, eliminating manual assessments that consume valuable time. By harnessing advanced algorithms, it swiftly identifies and addresses any discrepancies or unauthorized access, empowering you to rectify issues promptly and effortlessly maintain ISO 27001 compliance.
Centralized Access Governance: With Zluri, you gain centralized visibility and control over users' access throughout your IT infrastructure. This centralized approach streamlines compliance management by offering a single platform to monitor, review, and manage access rights, ensuring alignment with ISO 27001 requirements alongside other standards like SoX and SOC 2.
Customizable Reporting Capability: Zluri's access review solution empowers you to effortlessly generate detailed access review reports with just a few clicks. These reports include all the data related to users' access, such as how many accesses have been modified, revoked, and more.
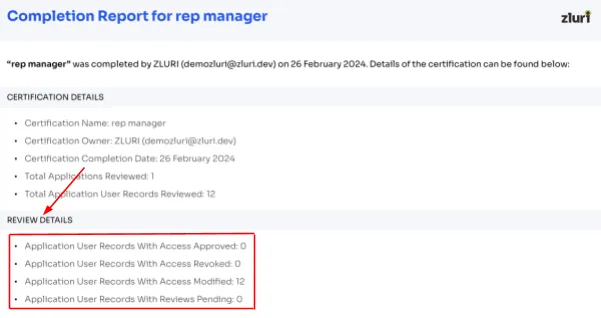
It also provides valuable insights into access patterns and user behavior. Such insights can be presented to achieve ISO 27001 compliance in the audit process.
So, don't wait any longer! Book a demo now!
Frequently Asked Questions (FAQs)
1: What is the ISO 27001 framework?
ISO/IEC 27001 stands as the globally recognized benchmark for information security, providing a comprehensive framework for establishing and maintaining a robust ISMS (Information Security Management System). By delineating precise specifications, ISO 27001 empowers organizations to fortify their information security posture.
2: What is a certification process?
The certification process refers to the procedural framework established and adhered to by an Authorized Inspection and Certification Agency. This framework is designed in strict accordance with predefined criteria for conducting certification of conformity.
3: What is the purpose of a recertification audit?
During the recertification audit, one crucial aspect is to verify that the Quality Management System (QMS) has effectively evaluated and documented any alterations and subsequently executed relevant training programs. Additionally, a recertification audit confirms that businesses integrate adjustments into their QMS in response to updates in ISO standards.









.svg)














