This blog, "RBAC vs ABAC," will explain the differences between these two access control methods to help you choose the best approach for your organization.
Choosing the right access control model for your organization is crucial for securing sensitive data and ensuring proper access management. However, deciding between role-based access control (RBAC) and attribute-based access control (ABAC) can be challenging, as each model offers unique features and benefits. Missteps in this decision can lead to inadequate security measures or overly complex access controls, impacting your organization’s efficiency and security.
Further, implementing the wrong access control model can result in unauthorized access, data breaches, and compliance failures. With the increasing complexity of IT environments and the need for flexible, fine-grained access controls, the pressure to choose the most appropriate model has never been higher.
In this blog, we will explore the differences between RBAC vs ABAC, breaking down their core access control principles, use cases, and advantages. By comparing and contrasting these two methods, we aim to shed light on their strengths and limitations, empowering you to make informed decisions. So, let's dive in and discover more about RBAC and ABAC!
RBAC: An Introduction
Role-Based Access Control (RBAC) is an access control method that restricts system access to authorized users based on their assigned roles within an organization. In an RBAC model, permissions are associated with specific roles, and users are assigned to these roles, granting them access to resources based on their role assignments. This approach simplifies the management of permissions, especially in large organizations, by grouping access rights into roles rather than managing permissions for each user individually.
RBAC is particularly useful in environments where roles and responsibilities are clearly defined, such as in corporate settings where employees' duties align closely with their access needs.
For example, an HR manager might have access to employee records, while a finance team member has access to financial data. This role-based approach enhances security by ensuring that users only have access to the information necessary for their role, reducing the risk of unauthorized access and potential data breaches.
ABAC: An Introduction
Attribute-Based Access Control (ABAC) is a more flexible and dynamic access control method that grants or denies access based on attributes associated with users, resources, and the environment. Unlike RBAC, which relies on predefined roles, ABAC uses attributes such as user roles, department, location, time of access, and data sensitivity to make access decisions. This fine-grained approach allows for more nuanced and context-aware access control policies.
In ABAC, policies define how attributes interact to determine access rights. For example, an access policy could stipulate that only users in the sales department can access customer data, and only during business hours. If a user attempts to access this data outside these parameters, access is denied, regardless of their role.
ABAC is particularly beneficial in complex environments with diverse and dynamic access needs, such as organizations with a wide range of user types and data classifications. It provides a more granular level of control compared to RBAC, making it ideal for scenarios where access needs are context-dependent and cannot be adequately addressed by role-based controls alone.
RBAC Vs ABAC: Which Method Is Right For You?
Although both RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control) share the vital role of managing user permissions; they take distinct routes to achieve their objectives. Here’s a quick comparison table for RBAC vs ABAC:
Let's delve into the key differences of RBAC vs ABAC, shedding light on how they operate, their strengths, and their respective use cases.
1. Scopes & Approaches
RBAC and ABAC differ significantly in their scopes and approaches to access management. While RBAC relies on predefined roles to grant access, ABAC considers various attributes to determine access rights, offering a more dynamic and fine-grained approach. Let’s see in detail:
- RBAC: RBAC is centered around predefined roles associated with specific permissions. Users are assigned to these roles, and their access rights are determined by the role they belong to. While this simplifies management in relatively static environments, it can become limiting when users' permissions need to be more fine-grained or dynamic. Modifying access control for specific scenarios might require creating new roles or changing role assignments, making it less flexible in such cases.
- ABAC: ABAC, on the other hand, offers a more dynamic and granular approach to access control. It centers on evaluating specific characteristics related to the user, the requested access, the requested resource, and the conditions or environment of the access request. These attributes, encompassing the user, request, resource, and environment, are pivotal in determining access permissions under the ABAC model. This attribute-based evaluation allows for more nuanced access control rules, making ABAC better suited to handle complex scenarios. Further, this makes it more adaptable and flexible when access rules are subject to frequent changes.
2. Ease of Access Management
The administrative overhead involved in maintaining access control models is an important consideration:
- RBAC's simplicity in design often leads to easier management in small to medium-sized organizations with relatively stable access requirements. However, RBAC administration can become burdensome as organizations grow or if there is a need for frequent changes in access control.
Creating granular access policies often necessitates the continuous addition of more roles. This can quickly result in what is known as a "role explosion," burdening IT admins with the task of managing an overwhelming number of organizational roles, sometimes reaching into the thousands.
Thus, managing role assignments and ensuring each user has the appropriate roles can be time-consuming and error-prone.
- ABAC's flexibility might initially introduce more complexity in defining attribute-based policies. However, once established, ABAC can significantly reduce management overhead, especially in dynamic environments. Changes to access rules can be made by modifying policies based on attributes, which can be more intuitive and less prone to errors compared to updating roles for each user.
In ABAC, IT teams benefit from a wide array of attributes at their disposal, enabling them to create highly precise rules for access management. There is no necessity to alter existing rules to accommodate new users; administrators simply assign the appropriate attributes to newcomers. Finally, when it comes to revoking or granting permissions, modifying attributes proves far simpler than defining or altering roles.
Thus, ABAC provides greater versatility and adaptability through attribute-based control. Choosing the right model depends on the organization's specific needs and the complexity of access control scenarios.
3. Data Security & Compliance
Evaluating the security implications and strengths of RBAC vs ABAC models is crucial, here is an overview:
- RBAC's simplicity and clear role-to-permission mapping can contribute to a higher level of security, especially when access control requirements are well-defined and relatively static. However, RBAC might struggle to enforce finer-grained access policies, potentially leading to overprivileged users or role proliferation, which can become security risks. This can result in potential data security risks, as users within a role may have unnecessary privileges. Moreover, ensuring compliance with specific data protection regulations might be challenging due to the rigid nature of role assignments.
- ABAC excels in data security and compliance by considering multiple attributes before granting access. With fine-grained control over permissions based on user attributes, resource attributes, and environmental factors, ABAC ensures that users only have the necessary access rights, reducing the risk of unauthorized data exposure.
ABAC's dynamic approach allows for more precise compliance enforcement and minimizes the chances of data breaches. Further, it enables real-time access decisions based on various contextual attributes, reducing the risk of unauthorized access. However, designing and managing ABAC policies requires careful consideration to avoid unintended vulnerabilities arising from misconfigured or conflicting attributes.
4. Scaling: Performance in Large Systems
In large systems with a vast number of users, resources, and permissions, scalability becomes a critical factor:
RBAC tends to scale well in moderately-sized environments where roles and permissions are well-defined and relatively stable. However, the management and maintenance overhead can become cumbersome as the number of roles and permissions increases. Additionally, as the number of users grows, RBAC might struggle to provide the necessary granularity for fine-tuned access control.
- ABAC is inherently designed to scale in complex environments. Since access decisions are based on attributes, ABAC can handle large-scale systems more effectively. ABAC allows you to add attributes based on location and time zone, ensuring seamless access management in a geographically distributed environment. As new users and resources are added, access rules can be defined using various attributes without constantly creating new roles. This attribute-based approach allows for better performance and flexibility in handling growing systems.
5. User-Friendliness in their Implementations
- RBAC implementations are generally straightforward and user-friendly, as they involve assigning permissions based on pre-defined roles. The simplicity of RBAC makes it relatively easy for administrators to manage access rights for large user groups. However, maintaining RBAC's user-friendliness may become challenging as the organization grows and role complexity increases.
- ABAC implementations can be more complex initially, as they involve defining and managing various attributes to grant access. However, once the attributes are set up, ABAC becomes highly flexible and user-friendly. Administrators can easily customize access policies based on specific user characteristics, resource properties, and contextual conditions, leading to a more intuitive access control system as the organization's needs evolve. ABAC's dynamic nature and granular control offer an unmatched level of user-friendliness in complex access management scenarios..
Even after comparing these parameters, you might still be unsure about which approach is better in practical scenarios. Let’s explore the real-world applications to clarify.
Making The Choice: RBAC vs ABAC
Here are some practical scenarios and examples to understand which model might best fit your organization.
Scenario 1: An Organization with Clear, Stable Roles
Example: Imagine a small company where employees have clearly defined roles, such as "HR Manager," "Sales Associate," and "IT Support." The tasks and access requirements for these roles don’t change frequently, and the organization values simplicity in managing permissions.
Best Fit: RBAC
In this scenario, RBAC is the ideal choice. Since each role corresponds to a set of permissions, managing access is straightforward. The HR Manager role can access payroll systems, while the Sales Associate can access customer relationship management (CRM) tools. RBAC simplifies administration because roles are clearly defined, and access control is easy to manage as employees change or move between roles.
Scenario 2: A Dynamic Enterprise with Complex Access Needs
Example: Consider a large enterprise where employees often work on multiple projects, and access needs vary based on factors like the department, project involvement, and even the time of day. For instance, a developer might need access to a particular database only during a specific project’s lifecycle.
Best Fit: ABAC
ABAC shines in environments with complex and dynamic access requirements. Instead of being limited to predefined roles, ABAC uses a combination of attributes—like job title, project involvement, and time of access—to make access decisions. This flexibility allows organizations to enforce fine-grained access control policies that adapt to changing conditions. For the developer in our example, access can be automatically granted or revoked based on project status and other contextual attributes, ensuring that permissions are precise and timely.
Scenario 3: Regulatory Compliance in a Financial Institution
Example: A financial firm needs to comply with strict regulatory requirements, ensuring that only authorized personnel can access sensitive financial data. The access control model must be robust enough to meet these legal obligations while still allowing employees to perform their duties effectively.
Best Fit: ABAC
In this case, ABAC is the preferred model because it allows for the implementation of detailed policies that take into account various compliance factors. For example, an employee might need access to financial records only if they are in a specific role, during business hours, and have completed the necessary compliance training. ABAC’s ability to incorporate these attributes into access control decisions helps the institution meet regulatory requirements while maintaining security.
Overall, the choice between RBAC vs ABAC depends on your organization's specific needs. RBAC is well-suited for simpler environments with stable access requirements, while ABAC shines in complex and evolving systems where fine-grained control is essential.
A hybrid approach that combines RBAC and ABAC elements may also be viable for organizations with diverse access control needs. Let's explore Zluri, a unique solution that goes beyond both approaches, providing capabilities from both to offer you a distinctive and comprehensive solution.
Zluri: Transforming Access Management Beyond RBAC & ABAC
To establish effective access control and governance, it's crucial to first ascertain who has access to what resources. However, many existing methods fall short in providing the necessary granularity of data to achieve this level of precision. Recognizing this gap, Zluri steps forward with its innovative access management platform built for modern enterprises.

Zluri is designed to streamline and simplify identity and access management processes, including managing user accounts, granting, modifying, and revoking access, and enforcing detailed access policies. This solution ensures compliance with stringent regulatory standards and secures access by ensuring that the right users have access to the appropriate applications and resources at the right time. This approach helps maintain a secure access environment.
In addition, as per KuppingerCole’s report, Zluri’s role-based access provides relevant SaaS information to a wide range of stakeholders, including IT, security, finance, procurement, GRC, and HR.
Let's explore how it works and the benefits it offers:
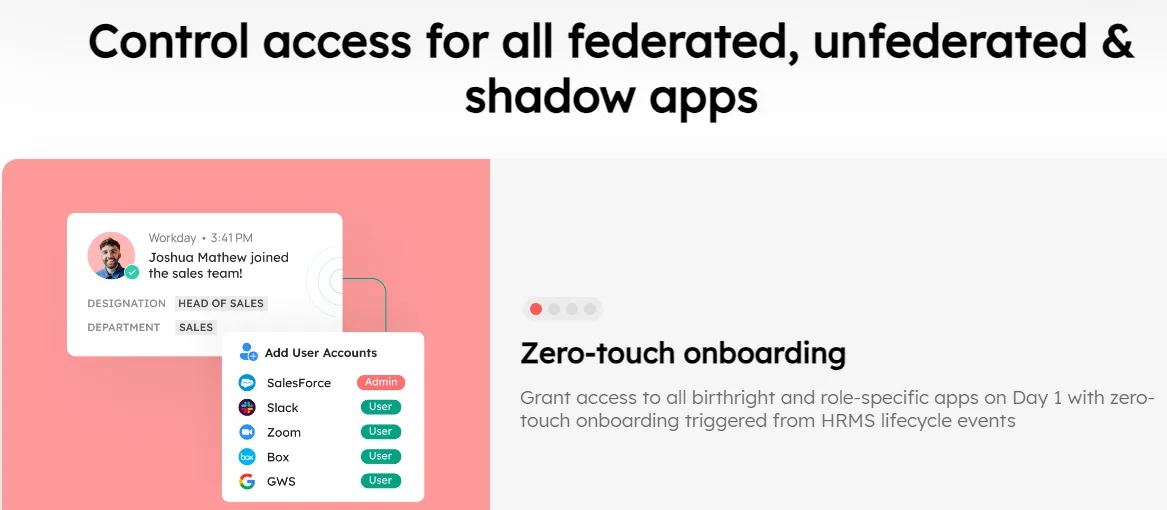
- Zero-Touch Onboarding
Zluri simplifies onboarding by automatically assigning new employees their digital identities. It integrates with HRMS to retrieve all relevant data and assigns the appropriate identity. Once set up, Zluri grants new employees the necessary access to SaaS applications with just a few clicks, ensuring they can start working effectively from day one.
- Identity Authentication Before Access
After assigning digital identities to new employees, Zluri's access management enables the IT team to create user accounts and verify these identities before granting access. This step ensures that access is granted accurately and securely.
- Managing Access During Mid-Lifecycle Changes
When employees change roles, departments, or positions, they require access to different applications. Zluri automates this process by updating their access rights, assigning the necessary tools and permissions based on their new roles, thereby maintaining productivity and security.
The screenshot below shows how an access request for Zoom is displayed, including all the relevant details for the approver to review.
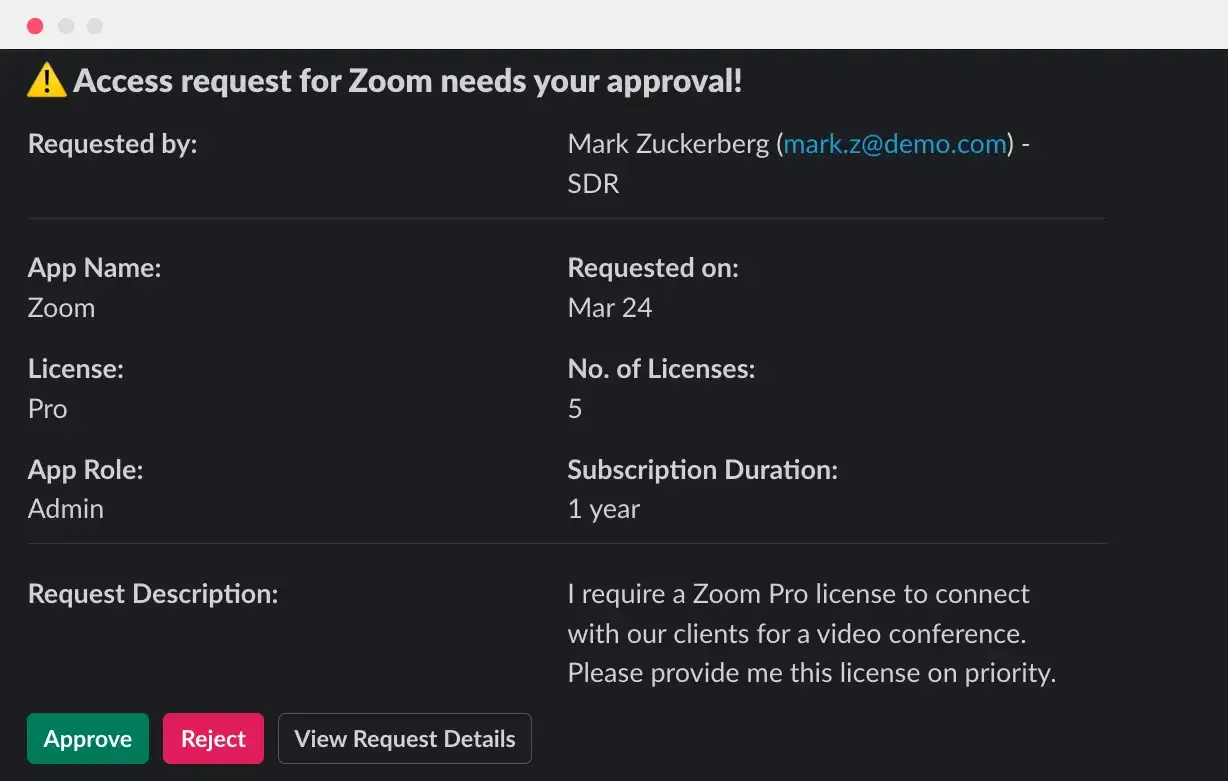
- Automated Access Request Management
Zluri streamlines the access request process through automation. IT teams can set up multi-step approval workflows and rules for automatic approval or rejection. Notifications are sent via Slack, allowing managers to review and approve requests efficiently. Once approved, Zluri quickly implements the necessary access changes.
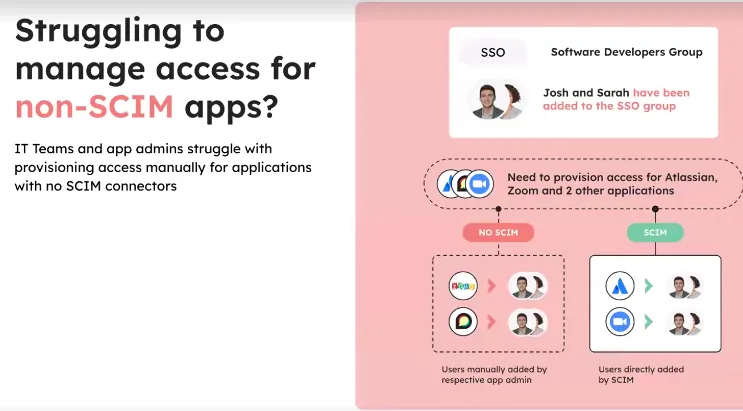
- Extended Access Beyond SCIM
Zluri overcomes the challenges of provisioning access for applications without SCIM connectors by integrating with Single Sign-On (SSO) systems. This centralizes and automates access management, making the process more efficient. For apps without SCIM connectors but with public APIs, Zluri uses API-first, no-code integrations, and supports SCIM actions through SSOs like Okta, providing a unified access management platform.
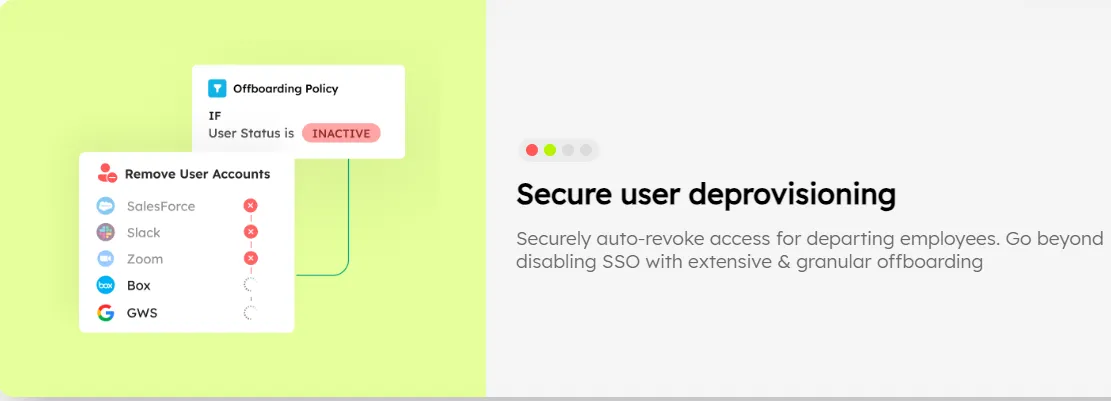
- Secure Offboarding
Upon an employee's departure, Zluri ensures secure offboarding by promptly revoking all access, mitigating the risk of data breaches from lingering access rights. After deprovisioning, Zluri ensures data continuity by taking a backup of the data and securely transferring it to the next assigned user, preventing any data loss during the transition.
- Monitoring Access Activities
Zluri provides comprehensive monitoring of access activities, including tracking which users have access to which applications, their activity status, and permission levels. This monitoring helps the IT team understand access patterns and user behavior, ensuring that only authorized users access sensitive data, thus maintaining a secure environment.
- Enforcing Access Control Policies
Zluri supports the enforcement of various access control policies such as Segregation of Duties (SoD), Role-Based Access Control (RBAC), Principle of Least Privilege (PoLP), and just-in-time access. These policies are essential for ensuring that users only access necessary resources, which is crucial for compliance with regulations like GDPR, SOX, and SOC 2.
- Insightful Reporting
Zluri generates detailed reports on identity and access management, providing insights into who has access to specific systems and data. These reports are vital for understanding user privileges, identifying potential security risks, and ensuring that access controls are aligned with organizational policies and compliance requirements.
Experience the future of access control with Zluri, Book a demo right away!
Frequently Asked Questions (FAQs)
1: What’s the difference between RBAC and PBAC?
RBAC vs PBAC are two distinct approaches to managing user permissions and access control.
- RBAC is often better for organizations with clear, stable role definitions and simpler access control needs. It’s straightforward to implement and manage when role definitions don’t change frequently.
- PBAC is ideal if you need more flexibility and dynamic access control based on various attributes and conditions. It’s suitable for complex environments where access requirements change often or where fine-grained control is necessary.
2: Can RBAC and PBAC be used together?
Yes, RBAC and PBAC can be used together to leverage the strengths of both models. For example, an organization might use RBAC for general role-based access control and PBAC for more granular, context-specific access decisions. Combining the two allows for a more flexible and comprehensive access management strategy.
3: Can RBAC and ABAC Be Used Together?
Yes, RBAC and ABAC can be effectively combined to create a robust and flexible access control system. Integrating these two models allows organizations to leverage the benefits of both approaches, providing a more nuanced and adaptable method for managing access permissions.







.png)

.svg)














