Safeguarding sensitive information and regulating access to critical resources has become paramount for IT managers. Amidst various security frameworks, attribute based access control (ABAC) stands out as a dynamic and versatile approach to managing access rights and permissions within systems and organizations.
The flexibility and granularity in access control not only bolster security measures but also facilitate compliance with stringent regulations and address the complexities of modern business workflows. Attribute based access control’s (ABAC) ability to adapt to diverse scenarios, considering nuanced details before granting access, empowers IT managers like yourself to ensure that sensitive data remains safeguarded while enabling legitimate users to carry out their tasks efficiently.
Let's delve deeper into ABAC's foundational principles, advantages over traditional access control models, workflow overview, and role in fortifying security postures across the SaaS landscape.
What is Attribute Based Access Control?
Attribute based access control (ABAC) is a security approach that determines resource access based on specific attributes associated with individual users, systems, or the environment. Unlike traditional access control methods that rely on roles or permissions, ABAC considers a broader range of factors. These attributes can include a user's identity, role, location, time of access, device characteristics, or any other relevant data.
For example, in an ABAC system, access to sensitive financial data might be granted only if the user's attribute includes:
- Being part of the finance department.
- Accessing during business hours.
- Using a company-registered device.
ABAC offers adaptability and scalability, allowing organizations to define complex access control rules that align with their specific security needs and compliance requirements. It's seen as an effective way to manage access in dynamic environments where traditional access control models might fall short.
4 Major Components of Attribute Based Access Control
Attribute based access control is a method where an organization's access policies govern access decisions based on various attributes associated with the subject, resource, action, and environment involved in an access event.
1. Subject attributes
The subject refers to the user seeking access to a resource to perform a specific action. Subject attributes encompass a range of identifiers present in a user profile. These include unique IDs, job roles, group affiliations, departmental and organizational memberships, managerial positions, security clearances, and other defining criteria. Attribute based access control systems typically source this data from HR systems and directories or glean this information from authentication tokens used during login.
For instance, imagine an employee who works in the marketing department. Their subject attributes might include employee ID, role as a marketing manager, membership in the 'marketing team' group, and a high-level security clearance due to their managerial responsibilities.
2. Resource attributes
Resources or object attributes denote the assets or objects (such as files, applications, servers, or APIs) the subject wishes to access. Resource attributes encapsulate identifying characteristics, such as a file's creation date, owner, file name, type, and the sensitivity of its data.
Moreover, resource attributes extend beyond mere technical details. They also encompass critical information like data sensitivity or classification levels, indicating whether the content is public, confidential, sensitive, or restricted. This classification plays a pivotal role in determining the level of access granted to different subjects.
For example, a human resources document containing sensitive employee information might have stringent access controls compared to a general company announcement.
3. Action attributes
The Action component in ABAC is crucial as it defines what a subject can do with a specific resource. These actions can indeed range from basic operations like read, write, edit, and delete to more nuanced or context-specific actions that align with the intricacies of the system or organization. ABAC's flexibility in defining actions allows for fine-grained control over access permissions, enabling a more tailored and secure approach to managing resources.
Imagine a user interacting with various resources, like documents or databases. For instance, regarding a document, actions might include reading its contents, making edits, or deleting it entirely—each action distinctly defined by associated action attributes.
The actions within attribute-based access control could involve:
- Querying the database for specific information.
- Modifying existing data records.
- Even deleting entire data sets.
These actions are discernible through their distinct action attributes, setting clear boundaries and permissions for what the subject can do with the database resources.
4. Environmental attributes
The environment encompasses the broader context surrounding an access request. It includes contextual factors like the time, location, device used, network protocol, encryption strength, and the user's typical behavior patterns.
Consider a scenario where an employee routinely accesses files within the usual office hours, utilizing an authorized company device within the office premises. In contrast, an access attempt to resources from a different time zone using an unfamiliar device might prompt heightened security measures.
Compared to the established patterns, this discrepancy in environmental attributes could trigger additional authentication or verification steps to ensure the legitimacy of the access request.
Key Benefits of Implementing Attribute Based Access Control
Implementing attribute based access control holds multifaceted benefits, revolutionizing how you and your teams manage access privileges and fortifying their security measures.
User-centric approach
attribute based access control simplify access control by directly tying permissions to specific user attributes, such as roles, responsibilities, department affiliations, or geographical location. Unlike traditional complex permission structures, ABAC operates through user profiles governed by these attributes.
This approach significantly diminishes administrative complexities, empowering authorized administrators to efficiently oversee and modify user attributes. Consequently, this streamlined process ensures precision and efficiency in access management while reducing the margin for errors or inconsistencies.
Flexibility and contextual decision-making
Attribute based access control's robust adaptability hinges on its capacity to integrate and leverage diverse attributes reflecting multifaceted user, resource, and contextual dimensions. This adaptability empowers organizations to craft access controls that respond dynamically to real-world scenarios.
For example, it enables the restriction of sensitive data access based on intricate contextual factors like the time of day, geographical location, or specific involvement in a project. This capability ensures nuanced and finely tuned identity and access management, significantly enhancing the precision and effectiveness of security measures.
Granularity and precision
Attribute based access control offers intricate control over access by evaluating multiple attributes simultaneously. This level of granular control empowers organizations to create highly specific access rules, dictating precisely who can access particular information and under what circumstances.
For instance, it can establish access rights by considering a comprehensive set of factors like user roles, specific geographic locations, device used, time of access, or even the action being performed. By combining these attribute values, ABAC ensures that only entities meeting all specified criteria can access sensitive data or critical systems.
This level of precision fortifies security policies and ensures adherence to stringent compliance regulations by tailoring access based on specific compliance requirements.
Adaptability to dynamic environments
Attribute based access control systems excel in environments characterized by frequent changes in user roles, data sensitivity, or evolving business requirements. Their standout feature lies in their ability to swiftly adapt to these changes by seamlessly incorporating new attribute values or adjusting existing ones without extensive reconfiguration.
This agility is paramount for businesses navigating constant evolution, guaranteeing that security protocols remain in sync with evolving demands while preserving operational efficiency. ABAC ensures that the access control framework remains resilient and adaptable amid ongoing transformations, thereby fortifying the organization's ability to sustain both security and productivity in a dynamic landscape.
Compliance and privacy protection
Attribute based access control plays a pivotal role in assisting organizations to comply with regulatory standards by implementing access policies rooted in particular attributes pertinent to compliance requirements.
This method enables the enforcement of access restrictions based on precise attributes like data classification, user clearance levels, or specific compliance regulations. ABAC significantly bolsters privacy safeguards by utilizing these attributes as control mechanisms, restricting data access solely to individuals with the appropriate authorization policy.
Consequently, this approach minimizes the likelihood of data breaches or privacy infringements by strictly regulating data exposure, aligning with regulatory mandates, and safeguarding sensitive information from unauthorized access.
How Does Attribute Based Access Control Work?
At its core, ABAC operates by dynamically assessing various attributes associated with users, resources, and contextual factors to make informed access decisions. Let's find out:
1. Attribute evaluation
In attribute based access control, attribute evaluation is the crucial first step, where various attributes tied to users, resources, and the environment are assessed to make access decisions. These attributes cover three main areas:
- User Attributes: These include roles, departments, job titles, clearance levels, or any identifiers linked to users within the system. For instance, in a hospital system, a user might be identified as a "nurse," "doctor," or "administrator," each with specific access rights.
- Resource Attributes: These attributes relate directly to the resources themselves, such as sensitivity levels, ownership details, or classifications within the system. For example, a file might be labeled as "confidential," "public," or "internal," determining who can access it based on these attributes.
- Environmental Attributes: These factors include time, location, network, devices used, or other variables affecting access decisions. For instance, access to certain data might be restricted outside office hours or from unauthorized locations.
Imagine a scenario in a bank's system using ABAC. A compliance officer trying to access sensitive client data has attributes indicating their role and necessary clearance levels. Meanwhile, the client data itself possesses attributes defining its confidentiality level.
The evaluation process considers these attributes alongside factors like the time of access and the device being used to decide whether the officer can access the information.
2. Policy creation
Policy creation is the next crucial step after evaluating attributes in access control. It involves setting up clear rules or guidelines based on these attributes to manage how access is granted or denied. These policies act as the framework governing access under specific conditions.
Role-based access is a critical policy framework ensuring that designated individuals, typically categorized by roles like "manager," possess access to highly sensitive data. This approach safeguards confidential information by restricting it solely to authorized personnel. By delineating access based on roles, your teams can maintain control over data and minimize the risk of unauthorized exposure or misuse.
Temporal restrictions complement role-based policies by limiting resource access concerning time and physical boundaries. For instance, sensitive data might be accessible exclusively during designated business hours, enhancing security by confining access to specific time frames.
Similarly, access restrictions within defined physical locations, such as secure office premises, further fortify data protection. These policies create additional layers of security, reducing vulnerabilities and ensuring data confidentiality by controlling access based on temporal or spatial parameters.
3. Attribute comparison
Attribute comparison is a fundamental process within attribute based access control. When a user initiates an access request within a system governed by ABAC, the system undergoes a meticulous evaluation of attributes. These attributes primarily revolve around three key elements: the user seeking access, the requested resource, and the contextual environment enveloping the access request.
- First, they look at who's asking—the user. They check things like their job, what they're allowed to do, and any special permissions they have.
- Then, they check out what they want—the resource. They see if it's sensitive, what kind of thing it is, and if the user can use it.
- Lastly, they look at the situation around the request—like where it's happening, what time it is, and what device they're using. This helps the system decide if giving access is okay based on what's going on.
Overall, the comprehensive comparison and assessment of attributes tied to the user, resource, and contextual environment of ABAC's robust access control mechanism. This approach enables nuanced and adaptive authorization models or frameworks that ensure secure, context-aware access while maintaining the integrity and confidentiality of the system's resources.
4. Access Decision
Following the comparison of attributes in the ABAC system, a crucial stage involves an access decision on whether to permit or deny access to the requested resource. This determination is based on the alignment between the presented attributes and the predefined policies:
Access is granted when the combination of attributes satisfies the policies' conditions. For example, if a user's role aligns with the policy allowing access to sensitive financial data for managers, access is granted accordingly.
Conversely, access is denied if the attributes do not meet the criteria outlined in the policies. For instance, access will be denied if a user attempts to access a resource outside of designated working hours, which contradicts the policy's time-based restrictions.
5. Implementation and Enforcement
Implementing and enforcing the attribute based access control framework involves utilizing specialized software tools for managing access control lists based on identified attributes. These tools play a crucial role in the following:
- Firstly, they quickly check if someone requesting access meets the requirements based on certain attributes. This happens instantly when a request is made. The software compares the attributes in the request with what's needed for access. If everything matches up, access is granted. If not, access is denied.
- Secondly, once the software determines whether access should be allowed or denied, it follows the rules already set up. These rules are like guidelines that determine who can access what. The software ensures these rules are followed when granting or denying access.
- Ultimately, the effective functioning of the ABAC framework hinges upon these specialized software tools. Their ability to conduct rapid attribute comparisons and enforce access decisions ensures access control operates seamlessly, safeguarding sensitive resources while facilitating authorized access efficiently.
What’s the Difference Between RBAC & ABAC?
RBAC (Role-Based Access Control) and ABAC (attribute based access control) are fundamental approaches to managing user permissions, yet they navigate distinct paths to accomplish their objectives.
The following table concisely summarizes the key differences between RBAC and ABAC across various aspects of access control, management, security, scalability, and user-friendliness in implementation.
A hybrid approach merging RBAC and ABAC elements could be advantageous for organizations with diverse access control rules and needs. Enter Zluri - a comprehensive approach to safeguarding sensitive data, mitigating risks, and fortifying defenses against potential security breaches. How does it achieve this? Let's find out!
Redefining Access Control & Governance Beyond ABAC with Zluri
Zluri revolutionizes access control with its Identity Governance and Administration (IGA) platform. By precisely managing access rights, it enhances security and compliance for organizations..

Now, let's delve into what makes Zluri's IGA stand out from other tools.
Empowering IT Insights with Zluri's Advanced Data Engine
Zluri's cutting-edge data engine provides a deep understanding of your organization's application landscape and user data, crucial for fortifying security measures and ensuring compliance.
- Nine Discovery Methods: Zluri's data engine incorporates nine powerful discovery methods, including MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). These methods offer a comprehensive view of your application ecosystem.

- Zluri’s nine discovery methods
- Granular Insights: By leveraging these methods, your IT team can swiftly identify specific users, scrutinize permissions, and pinpoint crucial user-app interactions, significantly enhancing security protocols and compliance efforts.
- Automated Efficiency: Zluri's automation eliminates the need for manual app categorization and access tracking, identifying managed, unmanaged, and shadow IT applications. This frees up valuable time and resources for your team to manage the app ecosystem efficiently.
Simplify User Lifecycle Management with Zluri's Advanced Automation Engine
Zluri's cutting-edge IGA platform presents a game-changing solution, revolutionizing the management of access controls for your organization's SaaS applications.
Optimize Access Control with Zluri's User Lifecycle Management Platform
Streamline your organization's access control strategy using Zluri's robust user lifecycle management. This solution fortifies security measures while simplifying operations, optimizing onboarding, and offboarding processes for enhanced efficiency.
- Enhanced Onboarding Experience
Zluri simplifies the onboarding process by securely granting new employees access to essential resources. Integrated with HR systems, it centralizes account creation across multiple applications, minimizing errors and ensuring correct access privileges from day one.
- Efficient Offboarding Procedures
Covering the entire employee lifecycle, Zluri's automated deprovisioning swiftly revokes user access across all applications during offboarding. This proactive approach minimizes security risks from abandoned accounts, ensuring a seamless transition during employee departures while safeguarding digital assets
Distinctive Access Control Features:
Zluri stands out with unique features tailored to enhance access control significantly.
Customizable Workflows: Eliminate manual access permission management with Zluri's customizable workflows. Tailor predefined workflows to your organization's specific needs, adapting to user roles, departments, and seniority levels to streamline access control according to your unique requirements.

Onboarding

Offboarding
Powerful App Recommendations & In-App Suggestions: Zluri analyzes user profiles, departments, and seniority levels to provide contextual-based app recommendations, ensuring optimal provisioning.

The platform also offers in-app suggestions, boosting user productivity by recommending necessary actions for efficient task execution. This capability empowers your IT team to make informed decisions, enhancing overall operational efficiency.
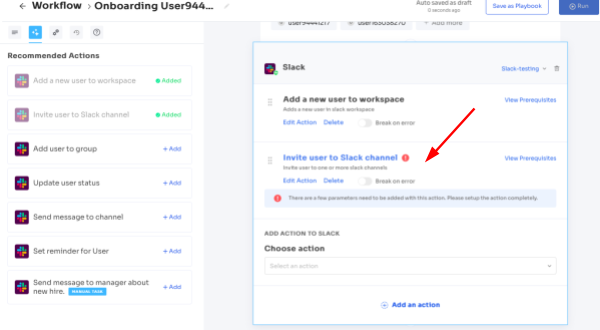
Reusable Playbooks: Save customized workflows as predefined "playbooks" with Zluri, eliminating the need to recreate processes for each user. This feature streamlines the access management process, saving time and ensuring consistency. Quickly apply these playbooks to maintain efficiency and consistency in access control procedures.

Streamline Access Requests with Zluri's Advanced Self-Serve Solution
Zluri's Enterprise App Store (EAS) redefines the management of access requests, offering a sophisticated self-serve solution that simplifies the intricate process of overseeing user access during role transitions within organizations.

Here's an in-depth look at its capabilities:
- Efficient Role-Based Access Control: It customizes access permissions based on individual job roles, ensuring employees have precisely what they need for their tasks and protects sensitive enterprise information from unauthorized access.
- Precision in Access Approval: Designated approvers can review access requests aligned with specific job roles, tailoring permissions to individual needs. For example, granting marketing tools access to a marketing manager or HR application access to an HR manager.

- Transparent and Hierarchical Approval System: EAS operates on a transparent hierarchical system involving app owners, reporting managers, and IT admins. This structure allows higher-level authorities to review and potentially override decisions by lower-level admins or managers, maintaining centralized control.
- Enhanced Transparency in Rejection Management: Detailed comments explain reasons for access request rejections, fostering understanding and collaboration within the organization. This transparency helps employees comprehend the basis for rejections.
- Flexibility with Customized Request Modifications: Approvers can adjust access requests to match evolving organizational needs. For instance, providing temporary access for project teams to specialized software and easily revoking permissions post-project completion.
- Empowering Users through Change Tracking: The "changelog" feature updates users about their access requests' status, including approvals, rejections, license alterations, and admin comments. This transparency encourages engagement and a collaborative culture.

Strengthen Security and Compliance with Zluri's Access Certification
Zluri's access certification solution is a pivotal tool for organizations seeking to fortify their security posture and adhere to stringent compliance standards. This platform is designed to meticulously review user access rights and permissions, ensuring that only authorized individuals have appropriate access to sensitive data and resources.

This unified platform brings teams together, streamlining access review processes and reinforcing the organization's security foundations. It empowers IT teams to oversee complex networks, ensuring a robust and compliant environment.
Employing sophisticated automation, Zluri minimizes errors, ensuring accurate and efficient access assessment. Its proactive auto-remediation swiftly addresses access violations, fortifying security and minimizing unauthorized breaches.
Detailed reports offered by Zluri furnish comprehensive analyses, enabling informed decision-making and strategic access management.
By leveraging Zluri's reporting capabilities, organizations gain a nuanced understanding of their access ecosystem. This information empowers stakeholders to make proactive decisions, optimize access controls, and fortify security measures effectively.
So what are you waiting for? Book a demo now and experience the power of Zluri’s attribute based access control and governance capabilities yourself.
FAQs
1. How does ABAC differ from other access control models?
Unlike traditional access control models like Role-Based Access Control (RBAC), ABAC doesn't solely rely on predefined roles. Instead, it evaluates multiple attributes associated with the user and the accessed resource to make access decisions.
2. Is ABAC suitable for all organizations?
ABAC is highly scalable and adaptable, making it suitable for organizations of various sizes and industries. However, its implementation complexity might make it more practical for larger enterprises or environments with dynamic access control requirements.
3. How does ABAC align with compliance and regulations?
ABAC can aid in compliance by enabling organizations to enforce access controls that align with specific regulations. Its granularity allows for fine-tuning access policies to meet compliance requirements.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)