Salesforce Identity is a cloud-based identity management and access control service provided by Salesforce. As a result, IT teams can securely manage employee identities and access Salesforce and other SaaS applications from a single platform.
However, it has certain limitations, such as inefficient ways of customizing the platform and the need for advanced technical skills or experts' assistance.
Salesforce Identity allows IT teams to grant the right access to the right people at the right time. In addition, they can control who can access the organization's data and applications running on the Salesforce platform, cloud, on-premises, and on mobile devices.
Furthermore, IT teams define policies for user authentication, authorization, and data access with this tool based on roles, groups, and attributes. Employees can access Salesforce and other apps using a single set of credentials. IT teams can monitor employee activity and revoke/restrict access if they try to make unauthorized access attempts.
Despite its many benefits, Salesforce identity has certain drawbacks, such as the platform can slow down when you try to work with large amounts of data or complex workflows. It also lacks the ability to integrate fully with other applications, so you have to develop certain categories on your own, like categorizing employees' identities based on their designation to grant them access.
Also, updated employee details take time to appear in the system as it takes time to refresh and operate very slowly.
Apart from that, you don't get notified when employees ask for access to applications; because of that, IT teams can miss out on urgent access requests.
However, organizations can always opt for other alternatives to avail full functionalities that will help their IT teams streamline the identity access management process. This blog will discuss a few alternatives to Salesforce Identity that you can consider deploying in your organization.
Here're The Top 8 Salesforce Identity Alternatives
Below are the top 8 Salesforce alternatives that cater to your IT team's specific requirements, improving their productivity and efficiency.
1. Zluri

Zluri is an intelligent automated platform that offers app access management capabilities to manage access permissions, ensuring the safety and security of the organization's crucial data. It helps IT teams give the right level of access permissions to authorized users/employees at the right time.
With Zluri, IT teams can create onboarding/offboarding workflows, which allows them to grant and revoke access automatically.
Let's assume your company hires a new employee who requires access to SaaS apps, and you may want to streamline the process by automating it. With Zluri, IT teams can create onboarding workflow using pre-built templates to automate the process of granting SaaS application access.
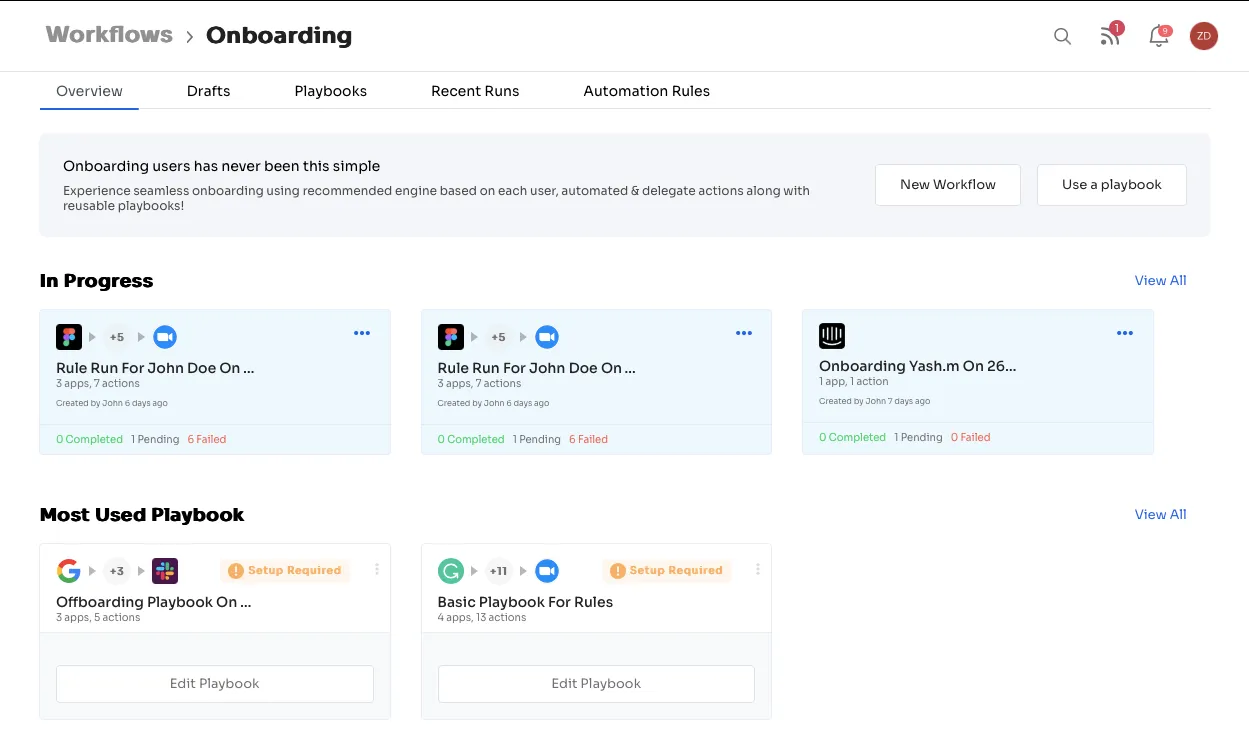
By selecting the required SaaS apps, such as Slack, Trello, Grammarly, and Google Docs, and grouping them into workflows, you can quickly assign them to new employees. This ensures that new hires can access the applications they need to perform their work quickly and efficiently without unnecessary delays.
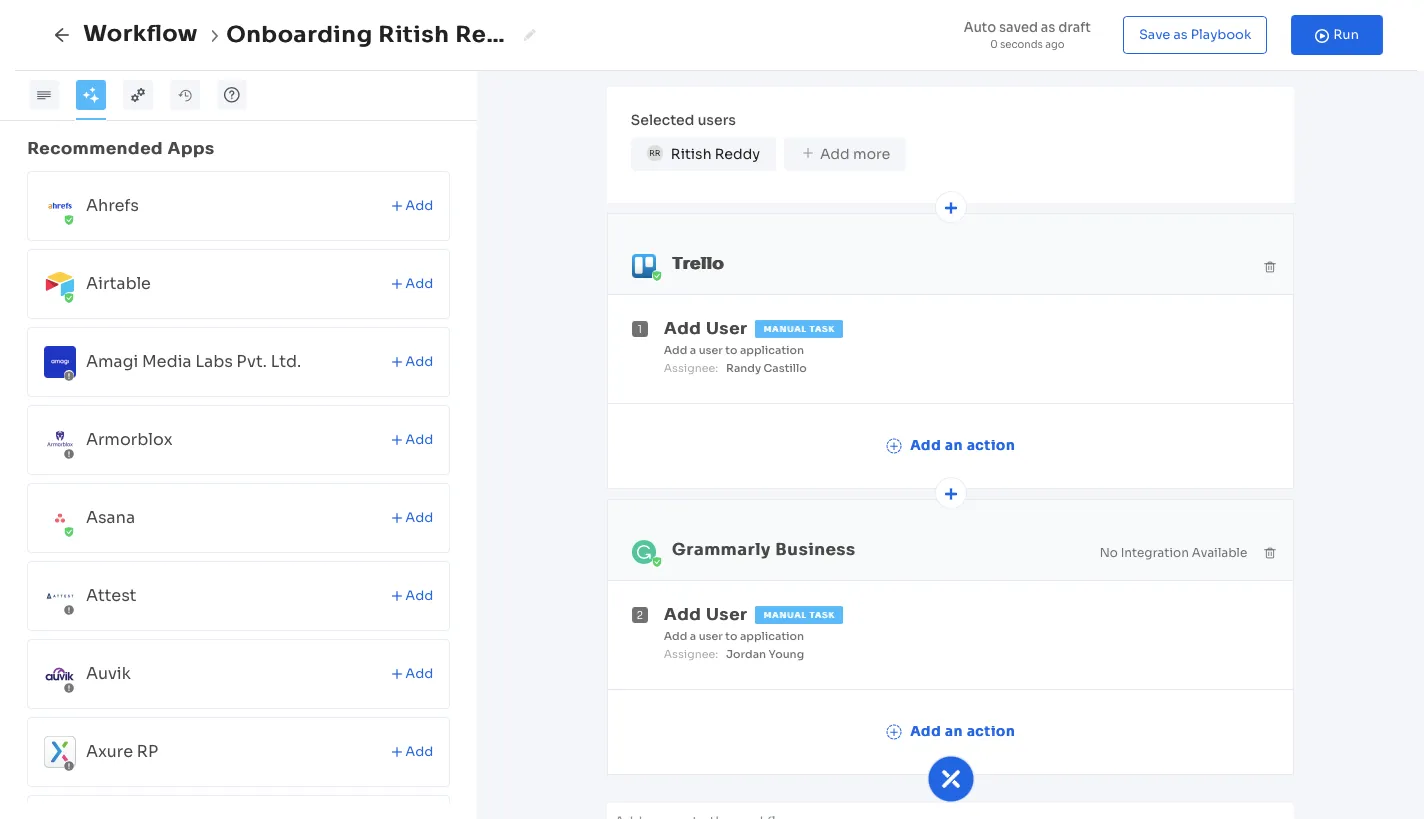
Moreover, by creating workflows based on employee roles, designation, and departments, Zluri simplifies the onboarding process for new hires. In addition, it provides in-app suggestions for projects, channels, and groups to add them to enhance the employee experience further. IT teams can also save these workflows as a "playbook" for future use.

Similarly, with Zluri, you can create offboarding workflows for employees departing the organization, allowing IT teams to efficiently revoke access and suspend their accounts with just a few clicks, ensuring the former employees don't have any access to the company's data or application. Also, existing workflows can be edited or deleted as needed.
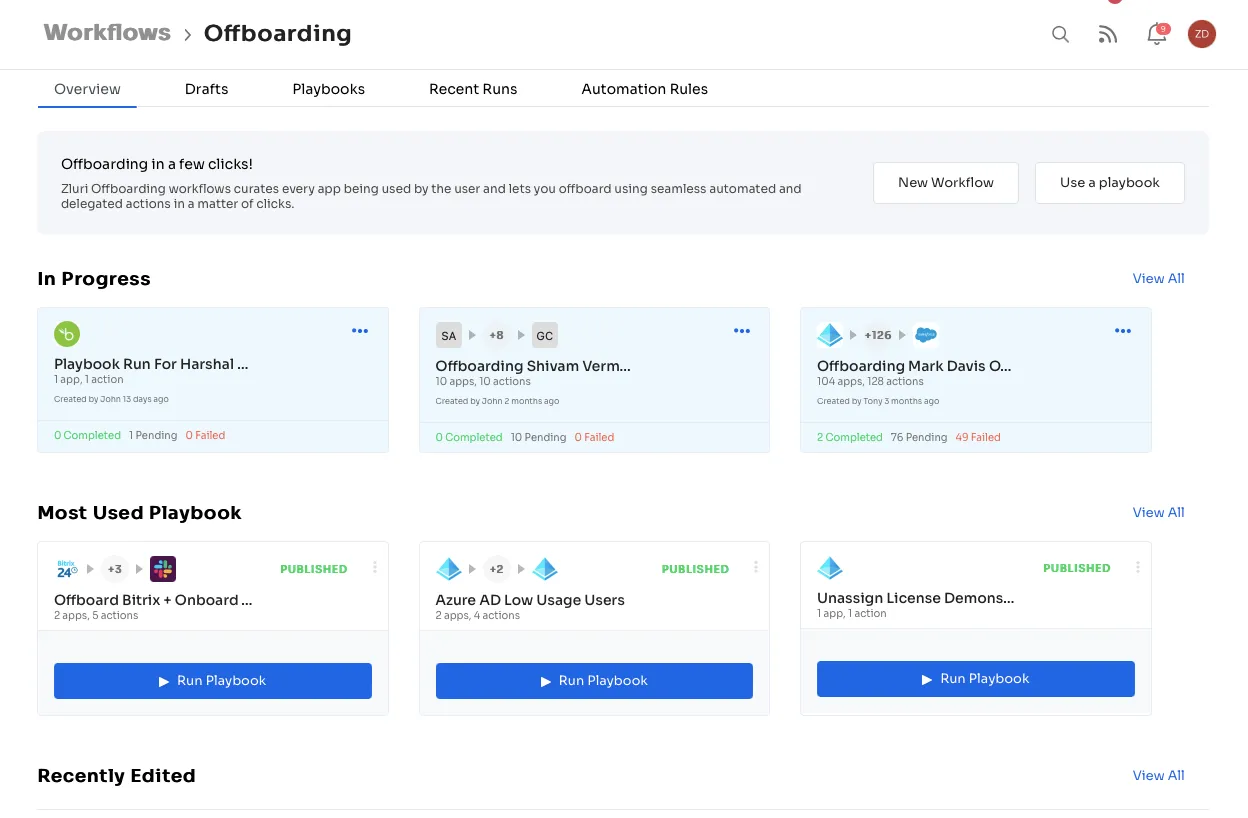
Zluri doesn't stop here. It adds an extra layer of security by replacing weak passwords, which is one of the major reasons for security breaches, with a single set of credentials integrated with SSO and MFA. With it, the verification/authentication process gets more strict and efficient as employees have to verify their credentials/Identity to gain access, preventing unauthorized users from barging in.
To learn more about Zluri, you can book a demo and check for yourself whether it can cater to your needs.
Pros
- Zluri offers more than 300+ APIs to connect with different systems, enabling custom integrations with a turnaround time of 36 hours and helping to streamline the various IT processes.
- It streamlines the login process by allowing users to sign in with a single set of credentials with the help of its SSO capabilities, which improves the employee experience for employees and saves time.
- It provides a single dashboard where you can examine and monitor all employee access activities to prevent security breaches or unauthorized access attempts.
- It notifies IT Teams in real-time of unauthorized access attempts so that you can implement required measures to secure sensitive data from getting compromised.
Customer Ratings
- G2: 4.8 /5
- Capterra: 4.9/5
2. Okta
Okta is a cloud-based identity and access management platform that assists IT teams in granting employees secure access to applications, data, and devices. In addition, IT teams can manage user authentication, authorization, and Single Sign-On (SSO) across different systems and applications.
Moreover, Okta enables IT teams to control employee identities and application access from a single location, streamlining identity management and enhancing security posture. Additionally, it seamlessly integrates employee identity across your security stack with capabilities like FastPass, Okta's Risk Engine, Directory connectors, and workflows.
Pros
- With Okta, the verification process is very secure. It verifies each employee's identity/ credentials twice or thrice before providing access to the organization's app and data, preventing cyberattacks and unauthorized access attempts.
- You can set permissions for employees quickly, and with customization functionalities, you can even modify the access permissions with changes in employees' roles during their mid-lifecycle change.
Cons
- The notifications are multiplied sometimes, like for a single login, you receive multiple login notifications/alerts, which creates confusion and delays the login or approval process.
- It takes a lot of work to integrate Okta with other apps and needs the involvement of technical expertise. Also, each application needs to integrate with it separately, which consumes additional time and resources.
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
3. OneLogin
OneLogin is an identity and access management platform that provides IT teams with the required solutions to secure access control. This tool secures applications, end-users, and devices from potential security threats by granting access permissions to defined roles, rules, and policies.
Furthermore, it conducts periodic audits to view who has access to what type of data, systems, and applications. If any employees try to make unauthorized attempts, IT teams will terminate their access or their access permissions will be restricted.
Pros
- It strengthens your security system by adding an extra layer of the verification process, each employee has to verify themselves fully with Onelogin before login into the organization's SaaS applications.
- It helps It teams instantly disable app access for employees who depart for the organization in real time by removing them from Active Directory, preventing security breaches or unauthorized access attempts by former employees.
Cons
- At times you have to log in multiple times a day because it automatically logs you out on a timely basis, consuming productive time and disrupting the flow of work.
- You have to pay the additional cost for other applications to integrate with OneLogin to authenticate the login process, such as Google Authenticator, increasing SaaS expenses.
- Its reporting is not intuitive, and pulling the field required to filter employees' identity and identify subgroups can be difficult.
- You may not receive any alerts/notifications that your password is expired or close to the expiry time, creating a last-minute hassle for you.
Customer Rating
- G2: 4.3/5
- Capterra: 4.6/5
4. JumpCloud
JumpCloud is a centralized identity access management platform that allows IT teams to manage one set of credentials per user and one Identity. In addition, it automates and unifies identity creation and deactivation.
Furthermore, it uses group-based access control, including automated group suggestions that helps IT teams grant new employees to apps and data based on their role or department instantly. Upon employees' departure, it suspends their account, and their app or data access gets terminated, allowing IT teams to keep confidential data secure.
Pros
- You can significantly reduce the number of passwords that employees need to manage with the help of Jumpcloud app integration and SSO features, improving the employee experience and simultaneously enhancing security by reducing password fatigue.
- IT admins can save productive time by using it to suspend employees from multiple groups when they depart the organization with a single click. Simplifying the complex process of revoking access to specific applications for IT admins.
Cons
- Lacks the ability to run a command or a batch of commands on one time basis to automate IT tasks, resulting in the involvement of manual methods to manage it, which consumes IT teams' productive time and effort.
- You get locked out from your own device sometimes, and you have to verify your identity multiple times to regain access to applications.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
5. Oracle Identity Management
Oracle Identity Management (OIM) is a security software solution offered by Oracle that provides access entitlement controls functionalities for both cloud and on-premises. With its microservice support, it discovers common access patterns, automates the identity access management process, and optimizes role-based access control.
Furthermore, it minimizes the complexity of the process for IT teams by providing an easy-to-use access catalog that suggests provisioning and access requests based on entitlements and roles. Also, for employees, it offers self-service features integrated with Rest APIs and an extensive set of connectors, allowing them to gain quick access to cloud and on-premises apps.
Pros
- You get the flexibility to customize the OIM platform as per your IT team's specific needs.
- You can easily edit and transfer data from one place to another and access all the data with a few clicks, which enhances productivity and efficiency as there is no manual intervention.
Cons
- Lacks the capability to assign application certification tasks to multiple users, leading to time-consuming processes.
- The data transferring process could be faster, due to which users need help transferring data in bulk. For instance, when exchanging data of the new employee from HR to the IT system.
Customer Rating
- G2: 3.7 /5
- Capterra: 4.4/5
6. SailPoint Identity IQ
SailPoint Identity IQ seamlessly automates the provisioning, certification, and access request procedures, making it a perfect fit for complex companies. Moreover, SailPoint IdentityIQ, which comes with a library of connections and connectors, may be used by IT teams to control access to applications.
To prevent security breaches, it performs timely audits, generates reports on which employees can access which applications, and keeps track of employees' access actions.
Pros
- Sailpoint Identity IQ enables IT teams to view all access permissions an employee has within the business, making it easier to keep track of employee access activities like what level of permissions they have, login attempts, and logout timings.
- This tool offers you with the flexibility to create custom integrations using SCIM (System for Cross-Domain Identity Management) and REST (Representational State Transfer) connectors.
Cons
- This platform demands a high level of coding knowledge to debug or troubleshoot issues, so organizations need to make the additional investment in experts to deal with it which increases Saas expenses.
- Absence of transparency on request status, it does not notify employees or provide updates on the status of application access requests.
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
7. PingIdentity

PingIdentity delivers a seamless experience by centralizing adaptive authentication. It becomes easier for IT teams to connect to any application on any device. This tool provides seamless access to employees that enhance the employee experience.
Also, it follows a zero-trust security strategy that helps maximize connectivity and minimize friction. During provisioning, it verifies the role of the individual employee and accordingly grants authorized access to SaaS apps, and at the time of deprovisioning, it deactivates the employee's account.
Pros
- Ping makes use of open standards, which increases its interoperability with other SaaS apps, making s it a perfect platform to streamline the authentication process.
- It ensures employees can safely and securely access organizations' data and applications quickly without having to remember multiple passwords/usernames by integrating with SSO and MFA.
Cons
- Occasionally, the application automatically unpairs from your device, and you must redo the setup process, wasting your time and effort.
- Login times out very quickly,it doesn't give you enough time to verify/authenticate your set of credentials or identity, which gets very frustrating and disrupts the flow of work.
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
8. Microsoft Azure AD
Microsoft Azure AD, an enterprise identity service, is a part of Microsoft Entra that guards employees' identity and crucial data against cyberattacks with multi-cloud Identity and access management, including SSO, MFA, and conditional access control.
Furthermore, it provides a single identity control plane that grants IT teams complete visibility and control of all the access permissions. Ensuring only the authorized employees have access to assigned applications or data.
Pros
- Microsoft Azure AD provides a single dashboard that helps IT teams navigate through all the access activities without hassle, increasing efficiency and productivity.
- It provides IT teams with transparent data encryption functionality to protect sensitive data by encrypting it. This ensures that unauthorized users cannot access the data stored on your servers. Thus, adding an extra layer of security to strengthen the security posture.
Cons
- This platform is not apt for non-technical users, as it involves complex coding.
- It supports a limited number of integration tools, affecting the workflow as developers cannot rely on specific integration tools to develop apps for protecting crucial data and the identity of employees.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5







.webp)

.svg)














