Managing third-party risks can be problematic, as vendor relationships expose your organizations to security and compliance issues. To avoid this, you need a structured approach. Without that, assessing each vendor’s risk becomes prone to oversight. That's where the vendor risk assessment template helps.
But what should the template include? This article covers the key components of a vendor risk assessment template.
Creating a vendor risk assessment template requires understanding the key elements impacting vendor reliability, compliance, and security. In fact, 59% of organizations say third-party risk is one of the top challenges in their cybersecurity strategy. By focusing on specific risk factors—data protection practices, financial stability, and regulatory compliance—this template can prove to be a checklist. This ensures a thorough evaluation process that helps mitigate potential threats and aligns with your organization’s overall risk management goals.
Let’s go ahead and get aware of the key components that you must include in your vendor risk assessment template.
6 Key Components To Include in a Vendor Risk Assessment Template
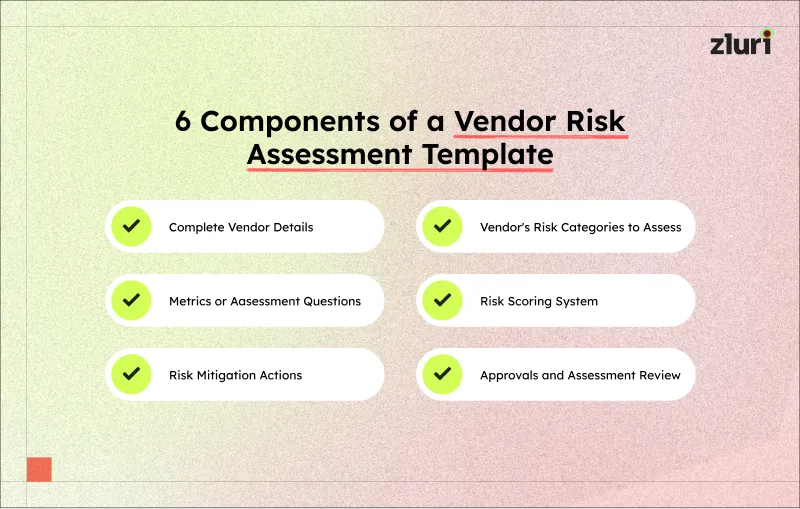
In this section, we will discuss the various components that a vendor risk assessment template should include.
1. Complete Vendor Details
A proper vendor risk assessment template must have detailed information about all your vendors. This component acts as a foundation for assessing potential vendor's risk. Here is the information required about a vendor.
- Vendor identification and background: This includes the company's name, location, industry sector, and contact person. It also includes the vendor's financial status, organizational structure, service department, etc. This background information helps you determine whether the vendor aligns with your organization's values and standards.
- Security policies and practices: You should document your vendor's security policies and practices, including their approach to data encryption, network security, and access control. This information helps you assess whether the vendor can protect your organization's security posture effectively.
- Compliance with regulatory standards: The information should include your vendor's compliance details with standards like GDPR, CCPA, HIPAA, etc. Also, ask if they have been audited for regulatory compliance or if they maintain regular compliance checks. It will help you ensure that the vendors meet the regulatory requirements.
- Data privacy and handling: This should include your vendor's data handling, storage, and retention policies. Ask and note how they manage data privacy, breaches, and more. This information will help you understand how they protect the data.
- Previous risk history: Note your vendors' past incidents, security breaches, or legal disputes. If the vendor has faced any security issues before, what did they change afterward? A clear record of their response to risks will help you determine if they are a reliable partner for your organization.
2. Vendor’s risk categories to assess

This component of the vendor risk assessment template should list and explain the different types of vendor risks that might impact your organization. Each risk category will help you evaluate your vendor’s potential in your organization, data security, and overall operations.
Now, let’s examine and discuss these risk categories.
- Financial Risk: This risk category helps you assess the vendor’s financial stability. Vendors with stable finances are more reliable partners, reducing the risk of service interruptions.
- Security Risk: This risk category focuses on data protection, network security, and the vendor’s response to cyber threats. Reviewing this risk helps ensure the vendor can protect your organization’s sensitive information, strengthening the overall security posture.
- Compliance Risk: This risk category involves checking if the vendor meets industry regulations and standards. Reviewing this helps your organization avoid legal issues or regulatory fines if the vendor fails to meet these requirements.
- Operational Risk: This section helps you look at the vendor’s internal processes and stability. The risk category covers your vendor’s processes, workforce skills, and ability to deliver consistent services. Evaluating this helps you identify any issues that could affect the quality or reliability of their service.
- Reputational Risk: This risk category focuses on your vendor’s image in the market. Reviewing this will help you avoid vendors whose reputation might negatively impact your brand.
Thus, including a section for each risk type ensures that you examine the vendor’s risks from all perspectives.
This will provide you with a structured approach to evaluating each risk category, making it easier to identify high-risk vendors. You can easily see which risks are higher or lower, helping prioritize actions.
3. Metrics or assessment questions to evaluate your vendor’s risk levels
This component of the vendor risk assessment template gathers measurable insights into your vendor’s risk level. Using targeted questions or metrics helps you assess different risk areas and determine how prepared the vendor is to meet your organization’s standards. This will simplify your risk analysis and ensure consistency across vendor risk assessments.
The section should include specific questions or performance metrics that cover key risk areas, such as financial stability, security practices, compliance, and operational reliability. Each question should be easy and aim to identify potential risks in your vendor’s processes or policies.
Moreover, including both qualitative and quantitative questions allows you to capture a complete view of your vendor’s capabilities and reliability. To make these questions effective, they should align with the critical risk areas identified in the assessment template.
Example 1: The questions below can be included to assess the vendor’s compliance risk.
- Does the vendor comply with relevant regulations like GDPR, HIPAA, or CCPA?
- How does the vendor ensure ongoing compliance with these regulations?
- Have they been audited or fined for non-compliance in the past?
Example 2: The questions below can be included to assess the vendor’s financial risk.
- What is the vendor’s current financial status? (Include revenue, profit margins, and debt-to-equity ratio if available)
- Does the vendor have any recent or ongoing financial challenges that could affect service delivery?
Example 2: The questions below can be included to assess the vendor’s operational risk.
- How often does the vendor test and update their disaster recovery and business continuity plans?
- What internal controls does the vendor use to maintain service quality?
By answering these questions, your vendors provide transparency, making it easier to assess their overall risk. The responses will help you identify gaps in your vendor’s policies or practices. Also, indicate where additional oversight or action might be needed.
Also Read: If you want to know the KPIs for evaluating your vendor’s performance, please go through Vendor Management KPIs.
4. Risk scoring system to prioritize your vendors’ risk
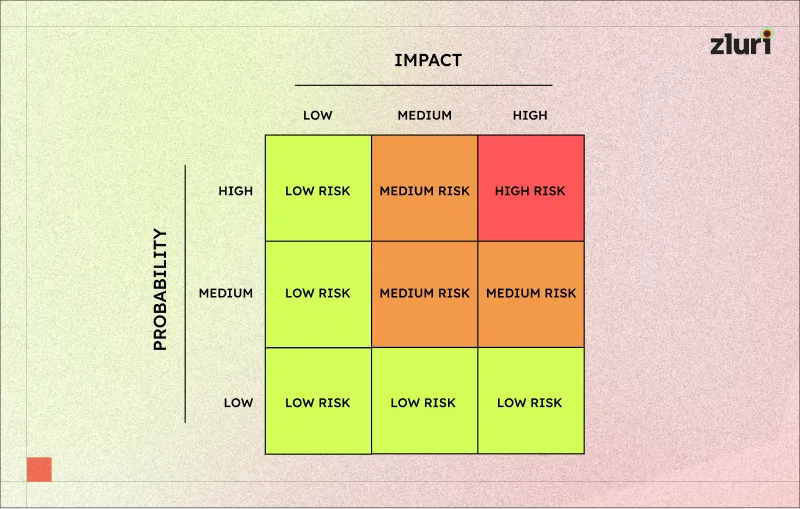
The risk scoring system is important in the vendor risk assessment template, as it will help you prioritize risks based on their risk levels. This scoring system typically uses three levels: low, medium, and high. Each level represents the potential impact of a vendor’s risk on your organization. Let’s understand them in detail.
Low Risk: A vendor with a “low risk” score indicates minimal risk to your organization. This vendor will have a strong track record of reliability, security practices, and compliance with industry standards. These vendors are financially stable and have a minimal history of incidents or issues.
Medium Risk: Vendors scoring as “medium risk” carry a moderate level of risk. They might have minor issues, such as occasional service delays or partial compliance with specific regulations. However, these issues are not severe enough to disrupt your operations. Still, they need regular monitoring to maintain compliance.
High Risk: Vendors classified as “high risk” indicate a significant risk to your organization. This could be due to weak security practices, financial instability, or a history of regulatory violations. These vendors require immediate attention, close monitoring, and possibly additional security controls.
Once the scoring is defined, using this in the vendor risk assessment template helps you compare your vendors and identify those with the highest risks. This prioritization allows you to immediately address high-risk vendors and make a risk mitigation plan.
5. Risk mitigation actions to record and track your response plans
Risk mitigation action is an important element of the vendor risk assessment template. It helps you record and track your incident response plans, offering a structured way to manage and mitigate your vendor risks. Moreover, it simplifies how you monitor and manage each identified risk.
Now, each risk entry section should include fields for key details like the suggested action, the person responsible, and a timeline for completion. This makes it easy to see what steps must be taken, who will carry them out, and when, and it will also help you monitor the progress of each action item.
For example, if a vendor has weak data encryption practices, a recommended mitigation action might be to require encryption upgrades or add stricter data access controls. In this case, the “mitigation action” column in the vendor risk assessment template would document the exact action that the vendor needs to implement.
In addition, to keep your vendor risk mitigation actions organized, the template can also include status fields, such as “In Progress,” “Completed,” or “Pending.” These updates ensure that every action is monitored from start to finish. Using this, you can ensure that vendor risks are addressed properly, reducing potential threats to your organization’s security.
6. Approvals and assessment review to record
Including a section for approvals and follow-up actions in a vendor risk assessment template ensures that all the actions are formally acknowledged and tracked. This structure helps you ensure that relevant stakeholders have properly assessed and signed off on each identified risk.
Why include a section for approvals in the vendor risk assessment template?
A section for approvals provides space for key decision-makers to review and formally approve risk assessments. This can include the IT manager, compliance officers, or other responsible stakeholders. By including this in the vendor risk assessment template, your organization creates a clear record that each risk has been reviewed and the proposed actions are approved.
Additionally, you can add a section for periodic reassessment dates that can further improve risk tracking. Setting reassessment dates helps your team monitor vendors over time and addresses any new risks that may arise. This practice ensures a continuous risk evaluation as business and vendor conditions evolve.
With structured fields for approvals and reassessment dates, your organization can:
- Maintain an organized approach to vendor risk assessment by keeping a clear record of decisions and actions.
- Track progress and accountability effectively, ensuring all risks are addressed.
- Adapt risk assessments to reflect current business and vendor conditions.
Now, once you know what to include in your vendor risk assessment template, it's important to implement it efficiently. However, manually collecting all the details mentioned above will consume time. Therefore, you need to automate it by leveraging a suitable and efficient tool. One such tool is Zluri.
Zluri offers a SaaS management platform that helps you centralize your vendors and their relevant information in one place. These details include vendors' contracts, spend, cost, status, and more. The details are fetched automatically, saving you time and providing you with accurate information.
Download our free vendor risk assessment template!
Simplify your Vendor Risk Assessment with a Suitable Template
In conclusion, a vendor risk assessment can be effectively performed if proper components are included in the template. It provides an organized way to evaluate potential vulnerabilities, making sure vendors meet your security standards and don’t put your organization at risk of unknown risks.
Now, to make the most out of your vendor risk assessment template, you need to consider the following:
- Ensure your template covers all necessary risk factors, such as data security, compliance, financial stability, and operational performance. A thorough assessment gives you a complete view of each vendor’s potential risks.
- Update the template regularly to reflect any new risks or changes in regulations. As technology and compliance standards evolve, so should your vendor risk assessment approach. This keeps your evaluations relevant and aligned with the latest standards.
- Use the template to support your decision-making and rely on your team’s expertise to address unique cases or specific concerns with the critical vendors. A balanced approach ensures that your vendor risk assessment process is both efficient and effective.
Also Read: If you want to know how to manage your vendor risks, consider reading vendor risk management policy.
Frequently Asked Questions (FAQs)
1. What is a vendor risk assessment questionnaire?
These questionnaires check a vendor’s security, data handling, and compliance practices. This helps cybersecurity teams make smart choices to protect their company’s assets and customer data.
2. What is a third-party risk assessment?
A third-party risk assessment looks at the risks from a company’s partners along the supply chain, including suppliers, vendors, and service providers.
3. What is third-party risk management?
Third-party risk management (TPRM) is a type of risk management that focuses on finding and reducing risks related to using third parties, like vendors, suppliers, partners, contractors, or service providers. This can be also referred to as supplier or vendor risk management.
4. What do you mean by security ratings?
A security rating, or cybersecurity rating, is a measurable score of an organization’s security strength. Basically, security rating helps teams make informed, data-based decisions about the security performance of their own company and their third-party vendors.
5. What are the top 5 cybersecurity threats?
Top 5 cybersecurity threats are below mentioned:
- Social Engineering
- Third-Party Exposure
- Configuration Mistakes
- AI-Based Cyber Threats
- DNS Tunneling.








.svg)














