As an IT manager, your responsibility extends to safeguarding your organization's sensitive data, intellectual property, and infrastructure against an evolving landscape of cyber threats.
To effectively counter these challenges, a strategic method known as a \"layered security approach\" proves highly effective.
Imagine your organization's defense system as a multi-layered shield, where each layer adds a unique level of protection. This approach involves implementing interconnected security measures, each addressing specific vulnerabilities. These layers work collaboratively to create a robust and multi-faceted defense mechanism.
In today's intricate digital environment, merely relying on a single security measure isn't enough. The layered approach acknowledges this reality and builds resilience by combining various lines of defense. Each layer plays a critical role, from perimeter safeguards that block initial intrusion attempts to authentication protocols that ensure authorized access.
You can create an intricate web of safeguards fortifying your organization's information infrastructure by implementing multiple security controls. This strategy of defense works harmoniously, enabling your teams to effectively repel and neutralize threats while ensuring the continuity and resilience of their operations.
Let’s delve deeper into the principles and advantages of the layered approach to security, exploring how it offers a comprehensive and proactive solution in an ever-evolving digital landscape.
Unveiling the Layers of Security - MFA & SSO
Safeguarding sensitive data and maintaining robust security measures is paramount for businesses of all sizes. Two essential security controls that have become cornerstones of modern organizations' security strategies are multi-factor authentication (MFA) and single sign-on (SSO).
Let's delve into these powerful tools and discover how they can fortify your business against potential threats.
1. The power of multi-factor authentication (MFA)
MFA takes security to the next level by surpassing the traditional username and password combination. It adds an extra layer of protection by requiring users to provide multiple authentication factors during the login process. These factors can include something the user knows, such as a password or a personal identification number (PIN).
Additionally, MFA incorporates something the user has, such as a physical token, a smartphone, or a smart card. Lastly, MFA can also utilize biometric data like fingerprints or facial recognition, making it even more secure.
By combining these different factors, MFA significantly mitigates the risk of unauthorized access, thwarting potential cyber threats and safeguarding sensitive information.
2. Streamlining access with single sign-on (SSO)
SSO offers a seamless and efficient authentication experience for users while maintaining stringent access controls. With the ever-increasing number of applications and systems employees need to access daily, managing multiple credentials can become a burden, leading to security vulnerabilities.
SSO solves this challenge by allowing users to access multiple platforms using a single set of login credentials. This means that users only need to remember one strong password or utilize other secure authentication methods, such as biometrics.
SSO also enhances user productivity by reducing login friction, eliminating the need for repetitive authentication, and streamlining the overall user experience.
Moreover, it ensures that access controls and permissions remain intact across various applications and systems, minimizing the risk of unauthorized access or data breaches.
Implementing MFA and SSO can bolster your organization’s security posture and protect vital business assets. Combining these two controls creates a formidable defense against unauthorized access attempts and strengthens your overall security infrastructure.
MFA reinforces user authentication, making it significantly more challenging for malicious actors to breach your systems. SSO simplifies user management, reducing administrative overhead, and enhancing user productivity, all while maintaining a robust security framework.
Navigating limitations of MFA & SSO
While MFA and SSO have proven effective in bolstering security, it is essential to acknowledge their limitations and explore additional measures to fortify your organization's defenses. Let's delve into some of the key limitations of MFA and SSO:
- Cyberattacks Targeting One-Time Passwords: One-time passwords, a staple of MFA, can be susceptible to interception or theft through techniques like SIM swapping, man-in-the-middle attacks, or social engineering.
- Brute Force Attacks and Phishing Threats: Attackers may exploit weak authentication processes through brute force attempts or phishing attacks, potentially bypassing MFA and compromising sensitive data.
- Credential Stuffing: Compromised credentials from one breach can be leveraged for unauthorized access to other accounts, rendering MFA ineffective if these credentials are compromised elsewhere.
- Dependency on User Devices: MFA and SSO rely on user devices for generating or receiving authentication codes. Compromised, lost, or outdated devices can lead to security vulnerabilities.
- Complexity and User Resistance: Implementing MFA and SSO introduces complexity that might lead to user resistance or errors, impacting adoption and security.
To mitigate these limitations, you should adopt a comprehensive security strategy that combines MFA and SSO with other security measures. This may include regular security awareness training, robust password policies, proactive monitoring for suspicious activities, and implementing advanced threat detection technologies.
By taking a layered approach to security, you can enhance defenses against evolving cyber threats. Enter identity governance and administration (IGA), a powerful solution that goes beyond MFA and SSO. By implementing IGA, you can enhance their security measures and gain peace of mind while effectively tackling compliance challenges.
Harnessing IGA’s Potential Through Layered Approach to Security
While MFA and SSO are crucial in securing digital environments, relying solely on them can inadvertently leave significant vulnerabilities unattended. To establish a robust defense against the constantly evolving landscape of cyber threats, it's imperative to adopt a more comprehensive security framework.
But what exactly does IGA contribute to this evolving security landscape? Let's delve into the tangible benefits it offers and why it holds the potential to be a transformative force for organizations.
- Automated User Lifecycle Management: IGA introduces streamlined user provisioning and deprovisioning processes. When a new employee joins the organization, IGA automatically assigns the appropriate access privileges based on their role, job responsibilities, and department. Likewise, when an employee leaves, IGA ensures their access to systems and sensitive data is promptly revoked.
By automating these lifecycle management steps, your teams can minimize unintentional and intentional unauthorized access risk. This is particularly important in large enterprises where the manual management of user access can be complex and prone to errors. - Strengthened Segregation of Duties: IGA solutions empower you and your teams to enforce clear separations between critical tasks and responsibilities. This principle prevents individuals from having excessive power that could lead to misuse or fraud.
For example, in financial institutions, IGA can ensure that the personnel responsible for initiating financial transactions are distinct from those who approve them. By mandating this separation, IGA enhances accountability, reduces potential conflicts of interest, and safeguards the organization's financial integrity. - Role-Based Access Controls: Leveraging IGA, you can implement access policies based on specific job roles and responsibilities. For instance, IGA can guarantee that doctors have access to patient records in a healthcare environment, while administrative staff can only manage appointment scheduling.
This finely tuned access control strategy minimizes the risk of accidental data exposure or unauthorized usage. Furthermore, it simplifies compliance with regulations like HIPAA (Health insurance portability and accountability act) by ensuring that only authorized personnel access sensitive healthcare information.
A comprehensive security strategy goes beyond MFA and SSO, and IGA emerges as a powerful ally in safeguarding digital assets. In light of these advancements, Zluri stands out as a leading provider of cutting-edge solutions that not only enhance your organization's security posture but also streamlines the often intricate administrative processes associated with security management.
Ensuring Security with Zluri’s IGA Solution
Zluri's IGA platform offers a comprehensive and informative solution for enhancing security in the SaaS landscape. Traditional identity governance and administration platforms are often designed for on-premises environments and may not fully address the unique challenges posed by cloud-based SaaS applications. However, Zluri's platform is specifically tailored to meet IT teams' evolving needs in these environments.
One of the key strengths of Zluri's platform lies in its ability to provide a layered approach to security. It focuses on essential IT functions such as authentication, authorization, privacy, data protection, and regulatory compliance. By addressing these critical areas, Zluri equips your IT teams with the necessary tools to manage and monitor user access efficiently.
Zluri's data discovery capabilities enable the platform to align perfectly with the unique requirements of your IT teams. With Zluri, your IT teams gain a holistic view of all the SaaS applications through a unified dashboard. This centralized approach simplifies user access management, ensuring that only authorized individuals have secure entry to critical applications.
Zluri's platform encompasses essential elements contributing to its effectiveness as an IGA solution.
Unleashing the power of data with Zluri's cutting-edge discovery methods
Zluri presents a cutting-edge data engine, revolutionizing how your IT team analyzes and uncovers SaaS app and user-related data. Your organization gains an all-encompassing view of its application landscape through nine discovery methods, including MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
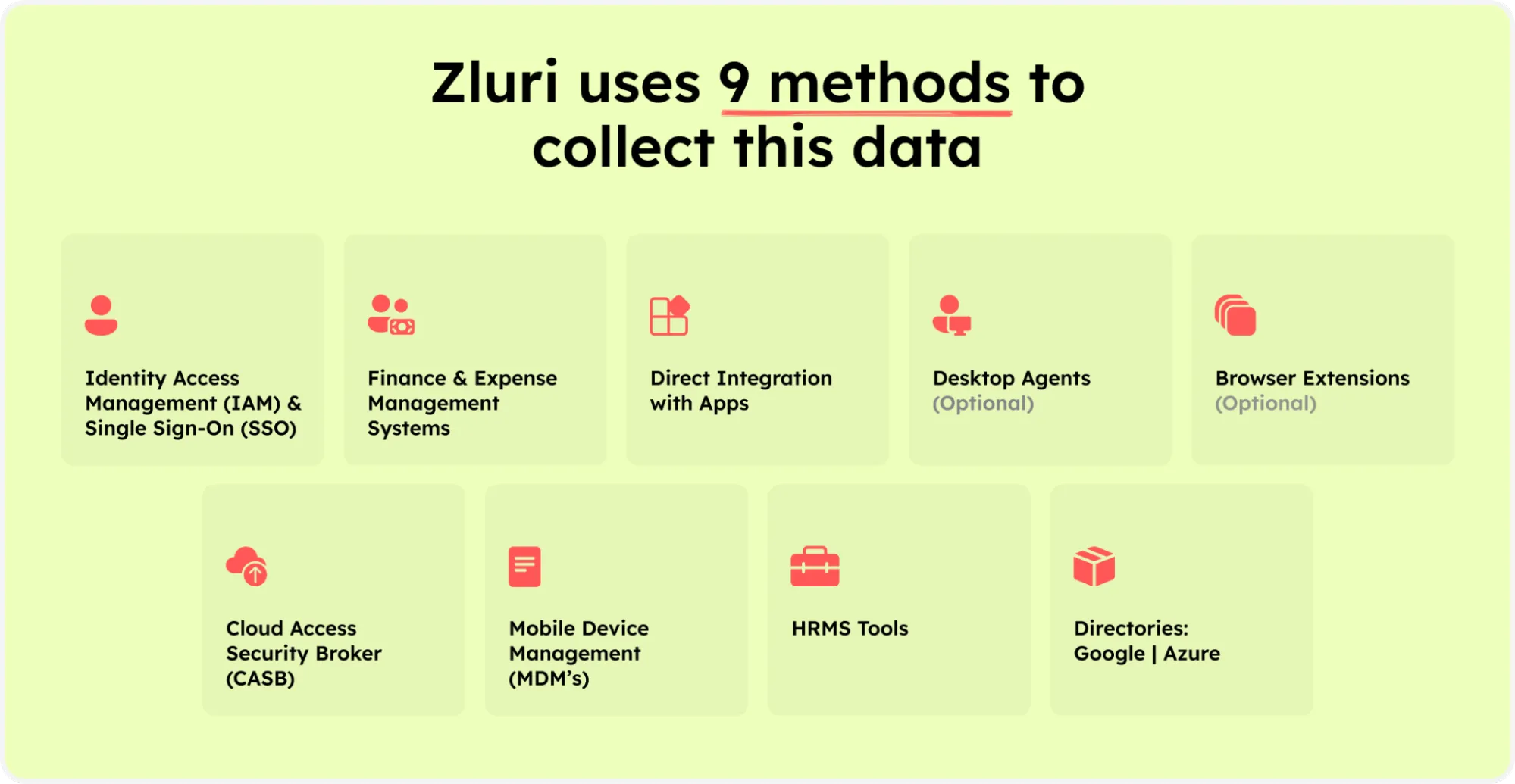
Zluri’s nine discovery methods
These discovery methods allow your team to swiftly identify specific application access, active users, scrutinize permissions granted, and even pinpoint critical users accessing the apps. This level of granularity offers invaluable insights that bolster your organization's security posture and compliance endeavors.
Gone are the days of time-consuming and resource-intensive manual categorization of SaaS apps and recording user access data. Zluri's data engine takes automation to new heights, automatically identifying managed and unmanaged apps. This empowers your IT team to reclaim precious time and resources, bidding farewell to tedious tasks and embracing a more efficient way of managing your app ecosystem.
Maintaining a secure access environment is paramount, and Zluri simplifies it for your IT team. With the intelligent IGA solution, you can ensure that the right employees have appropriate permissions for service accounts, effectively eliminating the risk of unauthorized access. Take charge of access permissions, tighten security, and stay ahead of potential threats with Zluri by your side.
Seamless user lifecycle management: Zluri's streamlined automation engine
Discover a seamless blend of efficiency and security with Zluri's advanced automation engine, reshaping how your business approaches access and user lifecycle management. Say goodbye to time-consuming manual processes as Zluri empowers your teams to concentrate on what truly matters, automating complex access management tasks.
This automation engine transcends traditional user access management, focusing on optimizing the entire user lifecycle. From granting appropriate access to dynamically adapting permissions as roles evolve, Zluri guarantees that your organization maintains peak efficiency while upholding data security. Embrace a new era of streamlined user lifecycle management with Zluri.
1. Simplified User Access Provisioning for Enhanced Security and Productivity
Zluri offers an innovative solution that redefines user access provisioning, prioritizing both security and productivity. Say goodbye to time-consuming onboarding processes, as Zluri streamlines the entire procedure, freeing your IT team from repetitive tasks.
By using Zluri, you can ensure that only authorized employees receive precisely the right level of access to essential SaaS applications and data, effectively reducing the risk of human errors and over-provisioning that can lead to security vulnerabilities.
At the heart of Zluri's mission is empowering your IT team. The platform provides an intuitive interface that allows IT professionals to effortlessly create and customize onboarding workflows for new employees based on their specific job entitlements, roles, positions, and departments. With this newfound efficiency, your team can simultaneously grant secure access to multiple new hires, ensuring a seamless and secure process.
Gone are the complexities of designing workflows. Zluri's user-friendly interface allows your IT team to configure access privileges based on job roles and responsibilities with just a few clicks. Experience a remarkable increase in efficiency and employee productivity as Zluri's powerful workflow capabilities come into play, guaranteeing the right access for the right users while maintaining the utmost security for your SaaS app data.
To streamline the onboarding process using Zluri, follow these straightforward steps:
Step 1: Access Zluri's workflow module and choose \"Onboarding\" from the dropdown menu. Click on \"New Workflow\" to begin creating your onboarding process.
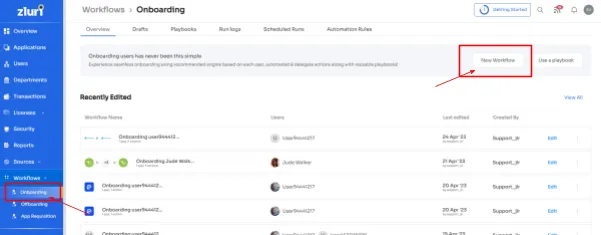
Step 2: Easily select the user(s) you want to onboard by using the search bar or manual selection. Click \"Continue\" to proceed.

Step 3: On the left side, explore the recommended apps and select the necessary ones for the user. Tailor the onboarding process by defining desired actions for each application.
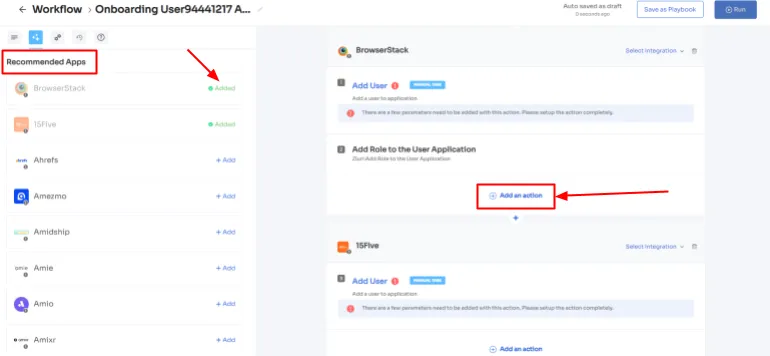
Step 4: Customize actions by selecting \"Edit Action\" and providing the required details. You can even schedule these actions to be executed on the day of onboarding. Once finalized, save the actions by clicking \"Save Task.\"
Step 5: To ensure future efficiency, preserve the workflow by selecting \"Save as Playbook.\" Name your playbook in the prompted dialogue box and click \"Save Playbook.\" Your onboarding workflow is now ready to be utilized.

Note: The power of Zluri's playbooks lies in their ability to offer a consistent onboarding experience to every new employee. By following a well-defined and structured approach, you ensure that important steps and information are not missed, leading to a more organized and efficient onboarding process. This consistency fosters a sense of belonging and inclusion among new hires, as they immediately feel valued and supported by the organization.
Moreover, Zluri's playbooks contribute significantly to employee engagement. When new hires are equipped with the necessary knowledge, resources, and connections right from the start, they are more likely to feel motivated and enthusiastic about their roles. This engagement translates into higher levels of productivity, as new employees can quickly become productive contributors to the team.
2. Simplified User Access Provisioning for Enhanced Security and Productivity
One of the standout advantages of utilizing Zluri is its automated revocation of access to all devices, apps, and systems. When an employee leaves, Zluri promptly disables their access, effectively preventing any unauthorized entry to sensitive information. This feature guarantees that former employees cannot access company resources, significantly reducing the risk of data breaches or security incidents.
Furthermore, Zluri takes care of data backup and transfer to a new owner, mitigating the risk of essential information being lost during the deprovisioning process. This ensures that critical data is securely handed over to the appropriate personnel, facilitating a seamless transition even after an employee's departure.
Additionally, Zluri simplifies the revocation of employee licenses and eliminates their single sign-on (SSO) access, effectively blocking ex-employees usage of any organization applications. This step further enhances data security and prevents potential misuse of company resources.
By adopting Zluri's user-friendly approach to employee offboarding, your team can ensure consistent and secure deprovisioning for all departing employees. This level of efficiency and security allows HR and IT teams to handle departures with ease and confidence, reducing the burden of administrative tasks and providing peace of mind during potentially sensitive situations.
Now, to streamline the Offboarding process with Zluri, follow these straightforward steps:
Step 1: Access Zluri's user-friendly main interface and head to the workflow module. Simply choose the \"Offboarding\" option from the drop-down list, and click on \"New Workflow\" to begin.
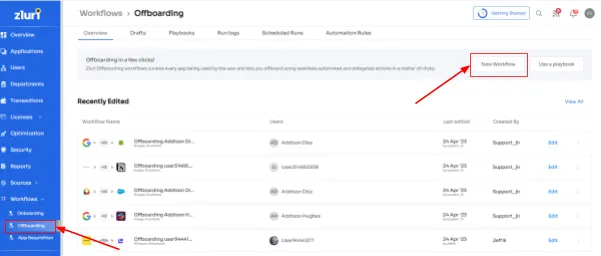
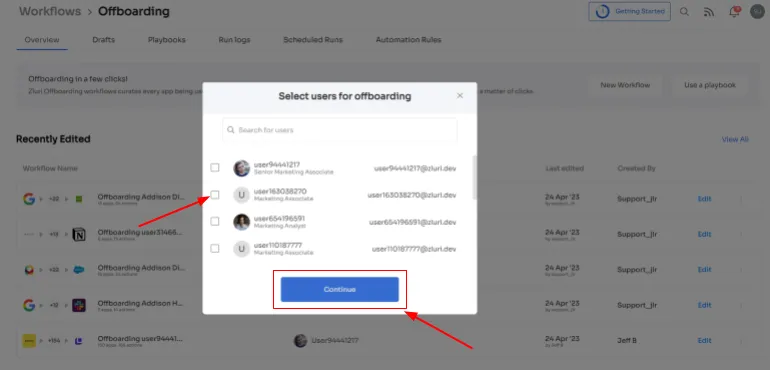
Step 2: Choose the user(s) you wish to offboard by selecting \"Select the user for offboarding.\" Once you've made your selection, click \"Continue.\"
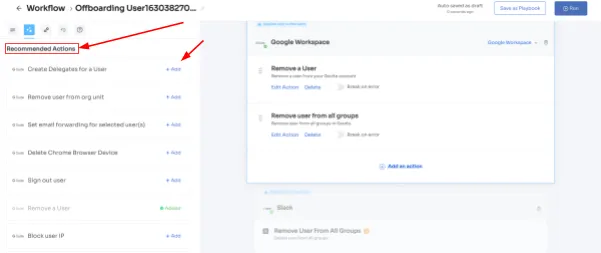
Step 3: Zluri provides recommended actions tailored to specific apps. Effortlessly choose from a range of suggested actions and execute them across the selected applications.
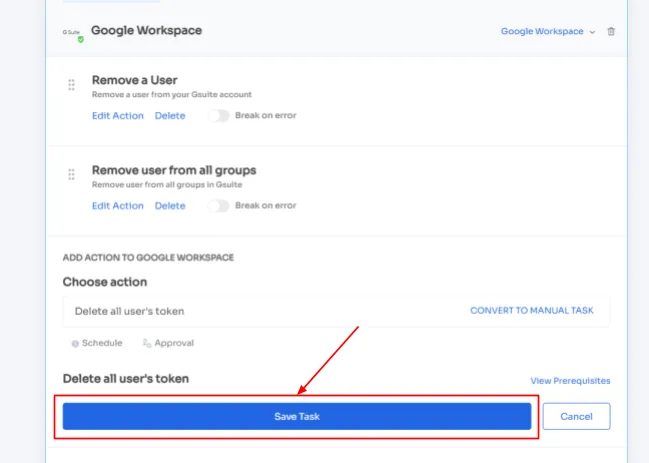
Step 4: To include additional actions, click \"Add an Action.\" Fill in the necessary details and save the task by clicking \"Save Task.\".
Step 5: Finalize the workflow by saving it as a playbook. Provide a name, and click \"Save Playbook,\" your offboarding workflow is now set and ready to go.
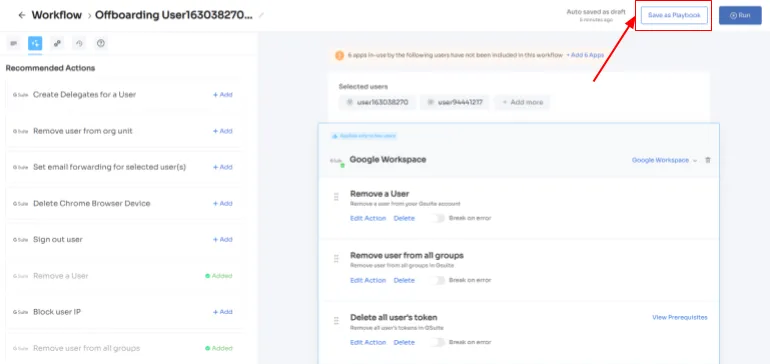
Note: Zluri's offboarding playbook ensures that no crucial steps are missed in the offboarding journey. It acts as a guiding hand throughout the process, making sure that all necessary actions are taken in a timely and systematic manner. This not only enhances efficiency but also minimizes the risk of errors or oversights that could compromise security or lead to data leakage.
In essence, Zluri's offboarding playbook empowers your team to embrace a new level of offboarding efficiency and precision. By automating repetitive tasks and enabling customization, you can streamline your offboarding process and focus on more strategic endeavors. This not only saves time and resources but also reinforces your commitment to data security and compliance, making the offboarding experience a seamless and positive one for everyone involved.
3.Effortless Access Request Management with Zluri's Self-Serve Model
Streamlining access permissions during employee transitions has never been easier. Zluri presents a game-changing self-serve model, the Employee App Store (EAS), designed to simplify access request management, ensuring efficiency and security.

Gone are the days of cumbersome manual processes for handling permissions. With Zluri's EAS, team members and approvers can seamlessly review and approve access requests tailored to specific job roles. This granular approach guarantees that employees have precisely the access they need to fulfill their responsibilities effectively, all while safeguarding sensitive information from unauthorized access.
Zluri puts unprecedented control over access privileges directly into your hands, creating a secure environment within your organization. The cutting-edge technology empowers you to effortlessly safeguard critical data, reducing the risk of unauthorized access and maintaining complete control over tools and resources accessible to employees.
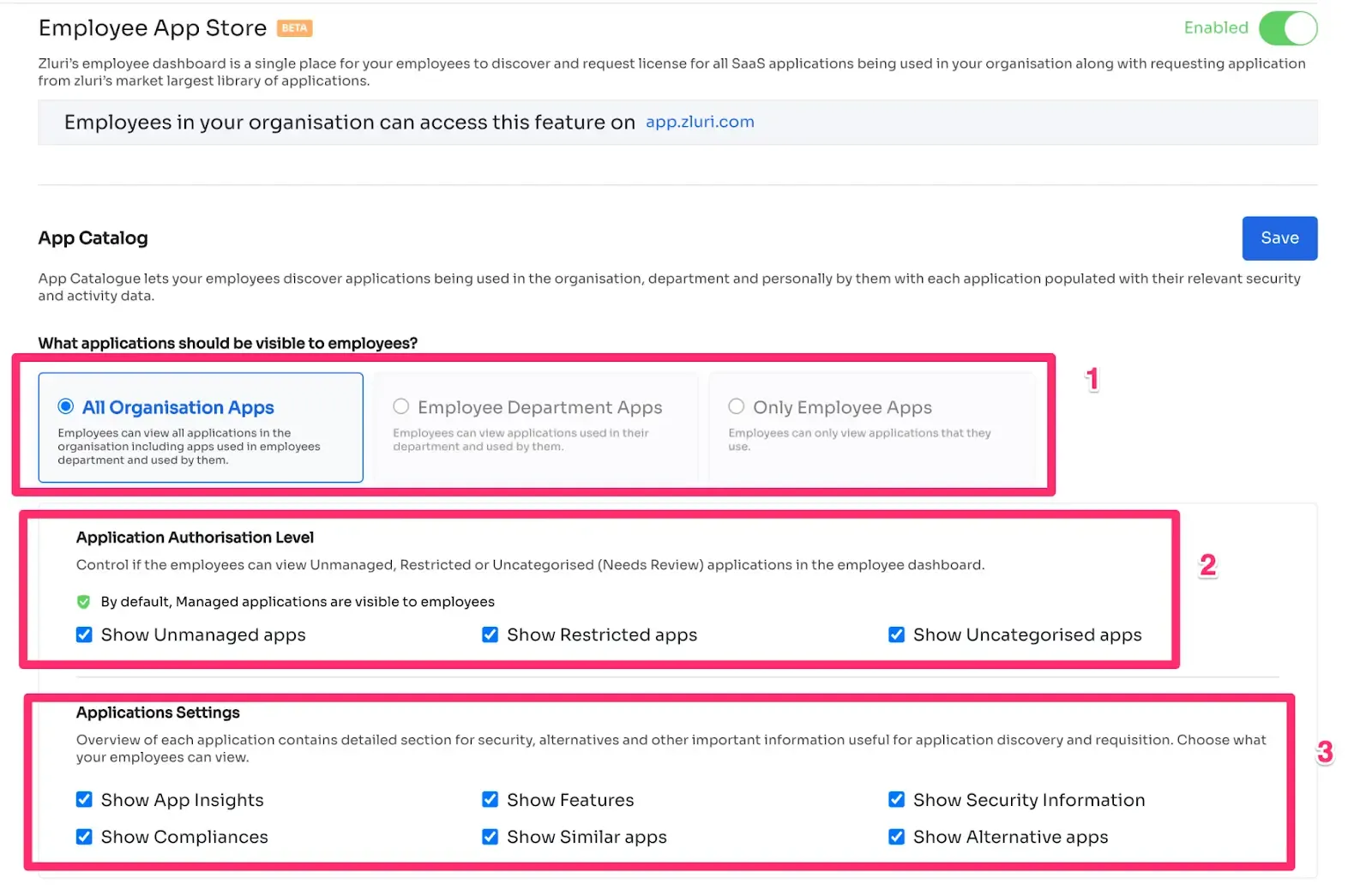
The EAS operates on a robust approval system, involving three distinct levels: app owners, reporting managers, and IT admins.
This multi-tiered approach allows higher authorities to make necessary decisions swiftly and with precision, even overriding lower-level admins or managers when required.
Transparency and collaboration lie at the heart of Zluri's access management process. Approvals and rejections of access requests come with comprehensive explanations and comments, ensuring that employees understand the reasoning behind each decision. This fosters a clear and communicative environment within the organization.
But that's not all! Zluri's intelligent solutions enable approvers to modify specific access requests, tailoring permissions to suit the organization's unique requirements. Keeping stakeholders informed is vital, which is why Zluri's IGA solutions offer a comprehensive \"changelog\" feature. This allows users to track updates, from approvals and rejections to changes in license duration or tier.
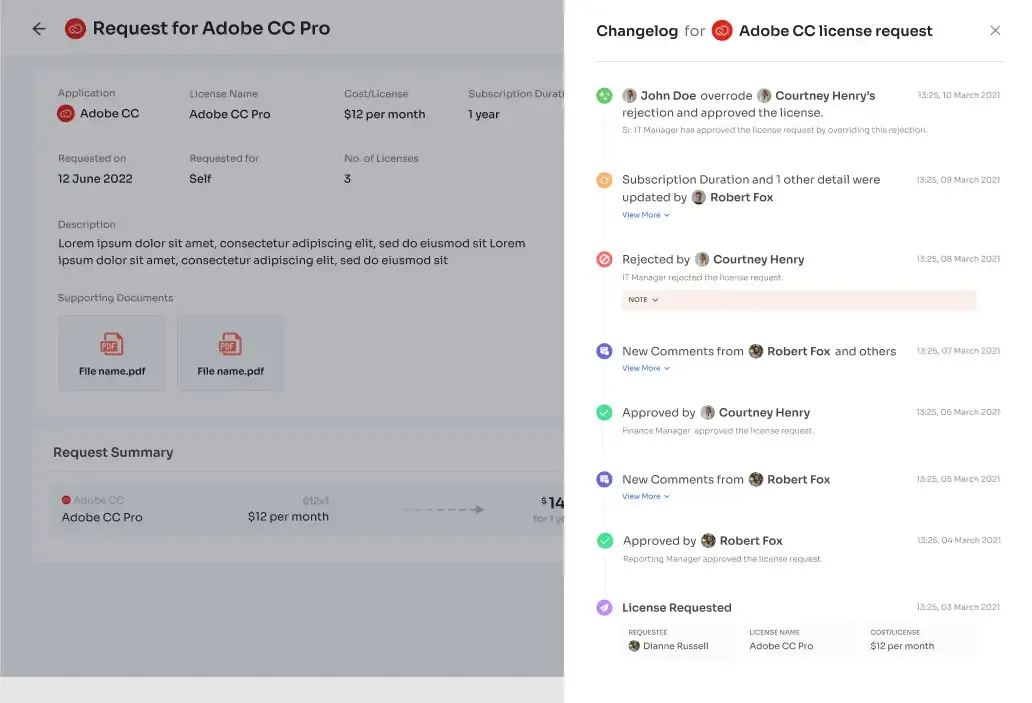
Moreover, the changelog captures valuable insights, including comments added by any admin, promoting a collaborative and well-informed approach to access management. With Zluri's EAS, handling access requests has never been more efficient, transparent, and secure, empowering your team to navigate employee transitions with confidence.
Streamlining access certifications: Embrace Zluri's IGA solution for remarkable efficiency
Zluri's IGA solution revolutionizes access certifications, offering a groundbreaking approach that recognizes the importance of time in the corporate landscape. Through the power of automation, access reviews, which used to be time-consuming and burdensome, are now streamlined. This allows admins to concentrate on critical tasks.
With Zluri's IGA solution handling the majority of the review process, efficiency in reviews increases tenfold, eliminating the need for laborious manual reviews and welcoming rapid access assessments.
By leveraging Zluri's IGA, your team can experience an impressive tenfold boost in review efficiency, saying goodbye to manual reviews and embracing swift access assessments.
Unified Access: A Comprehensive View of Digital Identities
Zluri's IGA solution revolutionizes access management by providing organizations with a unified approach to handling digital identities. This comprehensive system offers a complete view of an organization's access landscape, streamlining access-related information from various sources into one intuitive platform.
This eliminates the need to manage multiple directories or identity repositories, simplifying the complex task of overseeing user access and privileges.
- Access Directory: At the heart of Zluri's IGA lies its robust capability to capture and organize user information from diverse sources. The platform ensures that every user identity and associated access privileges are meticulously recorded and readily accessible for review. By maintaining accurate and complete records of user identities and their permissions, the system leaves no room for oversight or inaccuracies, enhancing overall security and compliance.
- Access Privileges: Zluri's unified access empowers administrators with unparalleled visibility into managing user access privileges across the entire organization. This heightened oversight allows for the swift identification of potential access discrepancies or suspicious permissions. By promptly detecting and rectifying any inconsistencies, the organization can strengthen its defense against cyber threats and ensure that access rights are always aligned with the principle of least privilege.
- Activity & Alerts: Taking a proactive security approach, Zluri's IGA solution continuously tracks user activity in real-time. This vigilant monitoring enables the system to trigger instant alerts in response to anomalous behavior or unauthorized access attempts. By providing an early warning mechanism, this alert system empowers administrators to respond promptly to potential security risks, mitigating the impact of any attempted breaches or malicious activities.
Automated Reviews: Empowering Efficiency and Security through Automation
Manual access review processes can become a significant hindrance, slowing down productivity and exposing organizations to potential security risks and compliance issues. Zluri's IGA solution comes to the rescue with its groundbreaking automated review capabilities, which harness the power of automation to streamline access management and bolster security measures.
- Access Rules: Zluri's IGA solution empowers organizations to take full control of defining access rules and policies based on roles, responsibilities, and specific business requirements. Integrating automation into the access management process allows the platform to conduct instant reviews and validations of user access against pre-established criteria. This automated approach leaves no room for ambiguity, ensuring only authorized personnel can access critical resources. Consequently, security risks are minimized, and compliance with industry regulations is reinforced..
- Scheduled Certification: Irregular access reviews can lead to lapses in security, as changes in roles and responsibilities might not be promptly updated, potentially exposing sensitive information. Zluri's IGA addresses this concern by introducing a forward-thinking scheduling feature. The platform automates system-generated reviews regularly, keeping access rights up-to-date with the organization's evolving security policies. This proactive approach fosters a consistent and compliant environment, reducing the likelihood of security breaches.
- Auto Remediation: When it comes to security, quick and efficient action is crucial. Zluri's IGA solution goes beyond just identifying potential risks; it also takes automated remediation actions to address them promptly. Whether it's revoking access, notifying users and managers, or initiating access request workflows for necessary approvals, the platform ensures that your organization can respond swiftly to security threats. By automating these remediation processes, your team can efficiently tackle security vulnerabilities, bolstering the organization's overall security posture.By embracing Zluri's IGA, you can experience a game-changing 70% reduction in manual efforts related to access reviews. Gone are the days of tedious and time-consuming access management tasks that eat away at your team's valuable time. The automation capabilities of Zluri's solution streamline the entire access review process, allowing your team to work smarter, not harder.The impact of this automation is profound. With a considerable reduction in manual work, your team gains the freedom to reallocate their time and talents to more strategic and high-impact initiatives. Instead of being bogged down with repetitive administrative tasks, your workforce can unleash their full potential and focus on driving the organization forward.Imagine the possibilities when manual access reviews no longer burden your team. They can delve deeper into critical projects, strategize for growth, and innovate within their areas of expertise. This newfound efficiency and focus can lead to increased productivity, improved employee satisfaction, and a more agile and responsive organization overall.With Zluri's IGA solution handling the access reviews automatically, you can trust that security and compliance are still top priorities. The automated process ensures that access rights remain up-to-date and in line with established policies, reducing the risk of security breaches and compliance gaps.
Wondering how to automate user access reviews? Zluri’s comprehensive ‘Access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the \"Access certification\" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the \"Application\" review method if desired and add the relevant application(s) to be audited for users' access.
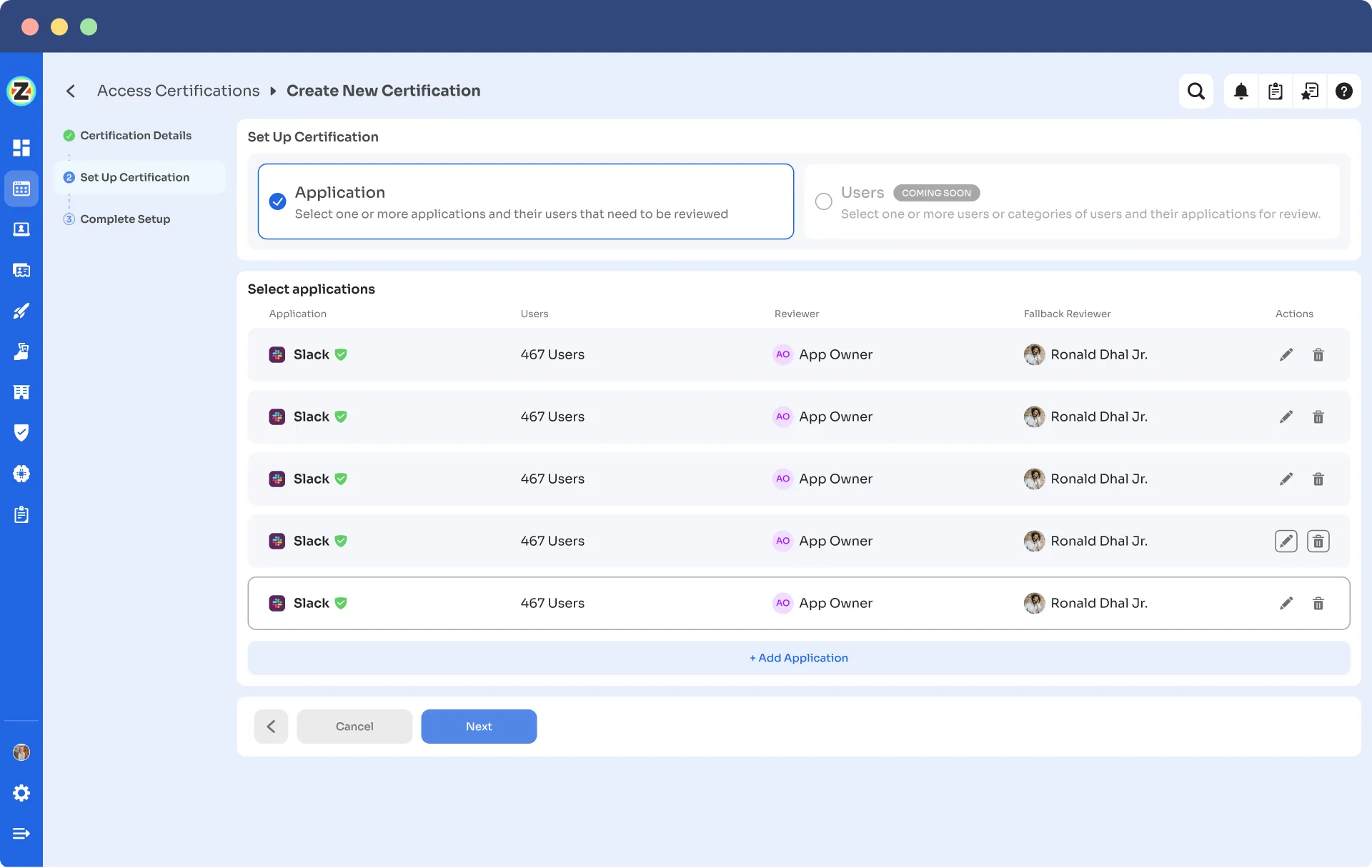
- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.
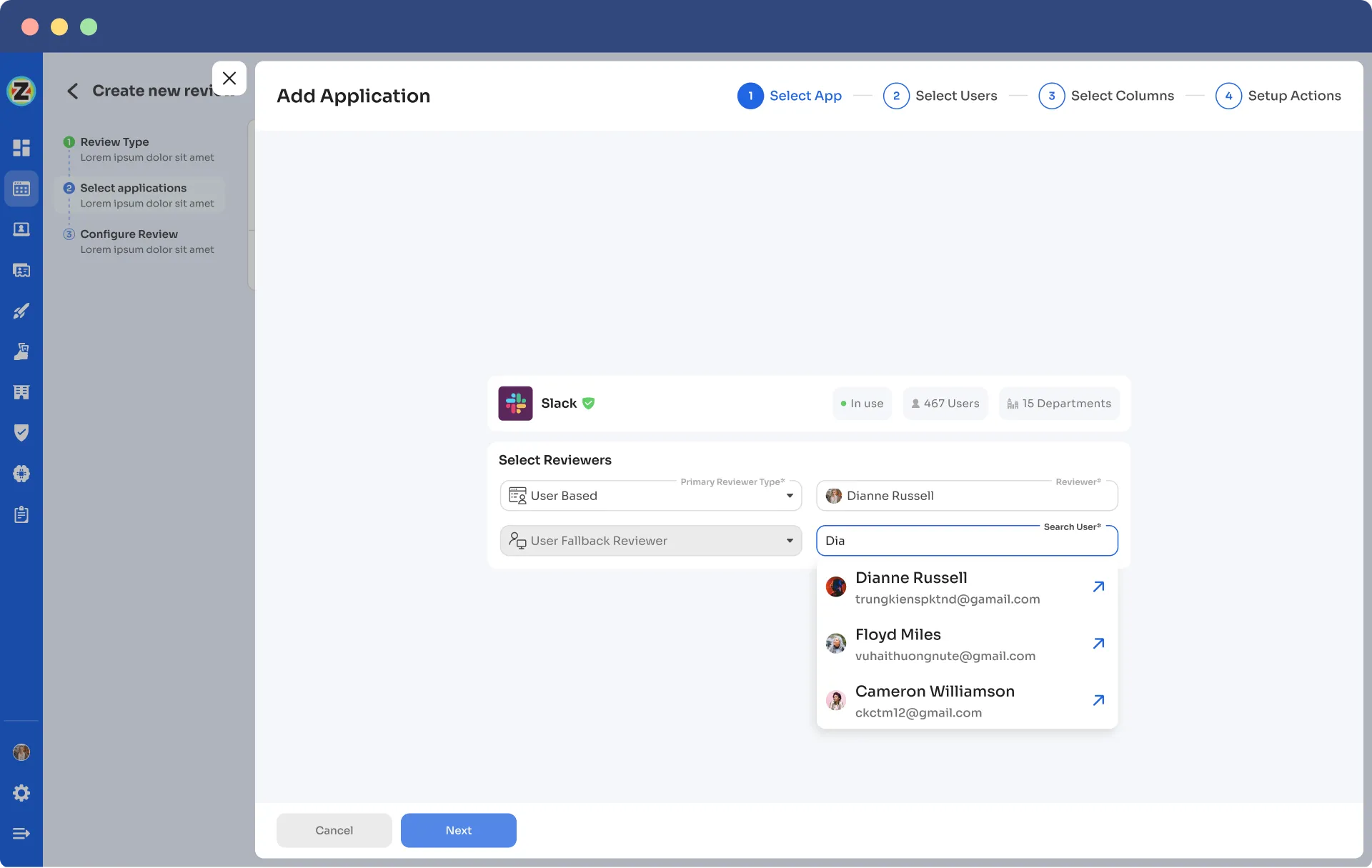
- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.
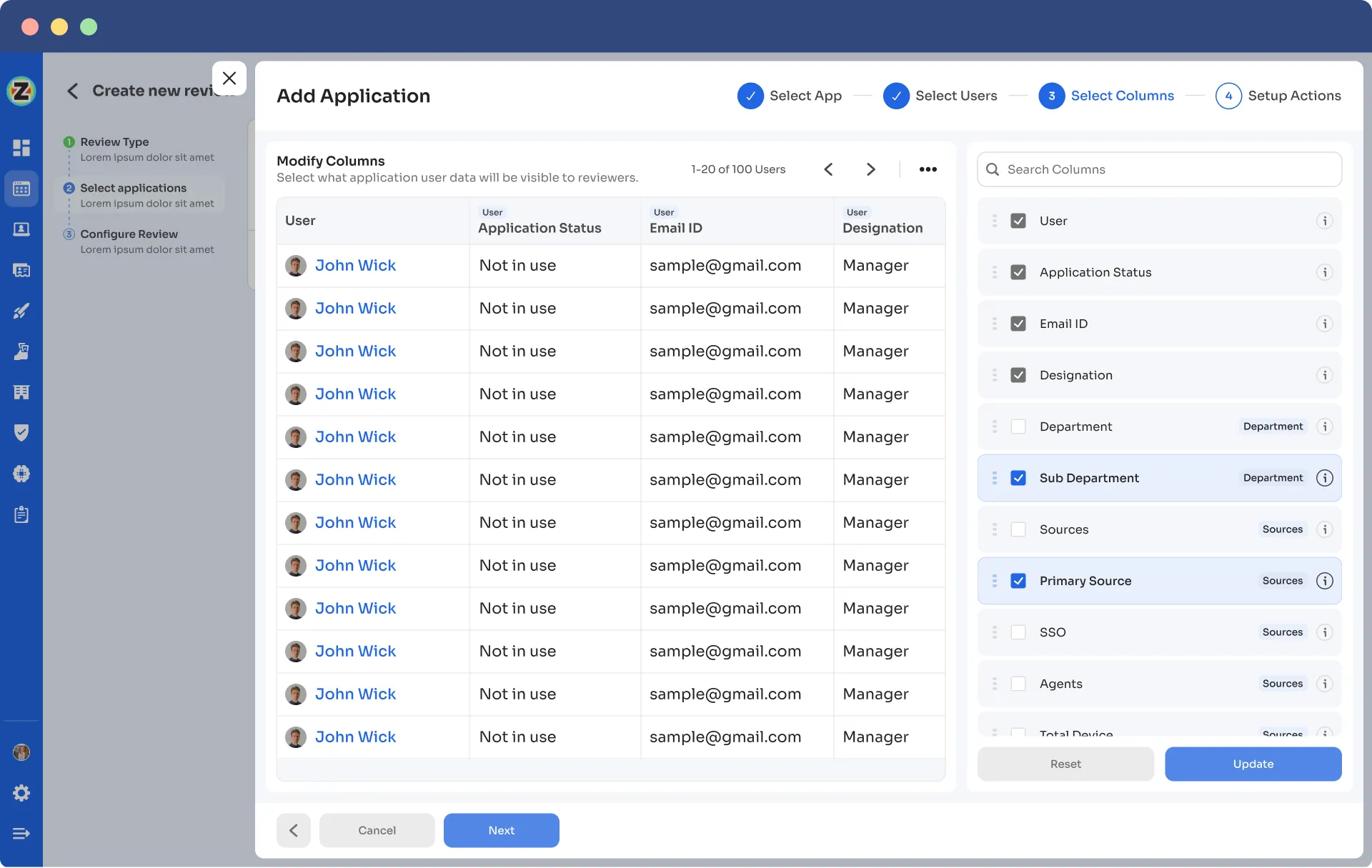
- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the \"Save Template\" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the \"Review Stage\" section.So what are you waiting for? By leveraging Zluri's IGA, you can enhance your organization’s security posture in the SaaS landscape. The platform's layered approach, data discovery capabilities, and personalized workflows provide comprehensive visibility, control, and efficiency in managing user access. With Zluri, you can effectively govern user identities, streamline access provisioning, and bolster overall security in the rapidly evolving world of SaaS. Book a demo now!







.png)

.svg)














