Keycloak is an open-source solution for Identity and Access Management (IAM) that gives users access to modern apps and services. With Keycloak, you can easily add authentication to apps and secure services with minimum effort.
Moreover, it lets users sign in with multiple identity providers and use fine-grained permissions to control access to SaaS apps.
Keycloak enables you to make a database of users with custom roles and groups. It offers features like managing & registering users and enforcing password policies, which makes it a complete IAM solution for modern applications. Keycloak's API allows you to add all of the functionalities to your app without any code.
Despite having multiple features, there are certain limitations to Keycloak as well, such as its implementation being a bit tedious. However, the list doesn't end here; below listed are some of the drawbacks of Keycloak.
Drawbacks
- In Keycloak, the manual process for server deployment is complicated and, thus, can hinder overall productivity.
- Besides its great functionalities, Keycloak doesn't provide efficient and comprehensive support documentation, making it difficult for users to find appropriate solutions for their problems.
This article will come in handy if you're looking for software with no such limitations. It will walk you through a comprehensive list of Keycloak alternatives.\"
7 Best Keycloak Alternatives
When looking for alternatives to Keycloak, you should consider their reliability and ease of use. So, we've made a list of the best alternatives to Keycloak that focus on the most sophisticated IAM features. Let's get started!
1: Zluri
Zluri offers an access management platform that simplifies access rights management throughout your organization. IT teams can easily assign, adjust, or remove access to applications and resources through an intuitive dashboard. This centralized system offers unprecedented control over who can access critical systems and sensitive data.
Through seamless integration with identity providers, HRMS tools, SCIM and non-SCIM apps, and ITSM tools, Zluri becomes a seamless part of your tech setup. Once integrated, it provides a detailed view of access across your organization, identifying all internal and external users, along with their application access and permissions.
This heightened visibility enables teams to manage all accesses effectively, easily supporting various identity and access management strategies.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Unique key points that set us apart
- Zero-Touch Provisioning

Revolutionize onboarding with Zluri's zero-touch provisioning, seamlessly automating the process without disrupting your Single Sign-On (SSO) provider. By integrating with your identity provider, HRMS, SSO, and tech stack, Zluri ensures efficient onboarding. For instance, when HRMS flags a new employee for onboarding, Zluri automatically provisions access to necessary applications.

Also, as per Kuppingercole's research and analysis report unlike traditional SSO or LCM tools, Zluri offers flexibility in setting onboarding conditions, like delaying access until the employee's joining date, enhancing the employee experience, and saving IT teams' time. Additionally, user-friendly onboarding triggers based on SSO data streamline processes with automation rules and notifications.
Also Read: Want to know how to efficiently provision, you can go through User Provisioning Best Practices.
- Secure User Offboarding

With Zluri's secure user offboarding, security remains paramount even during user departures. Automate user deprovisioning, transferring data, setting up email forwarding, and revoking access seamlessly with pre-populated playbooks.
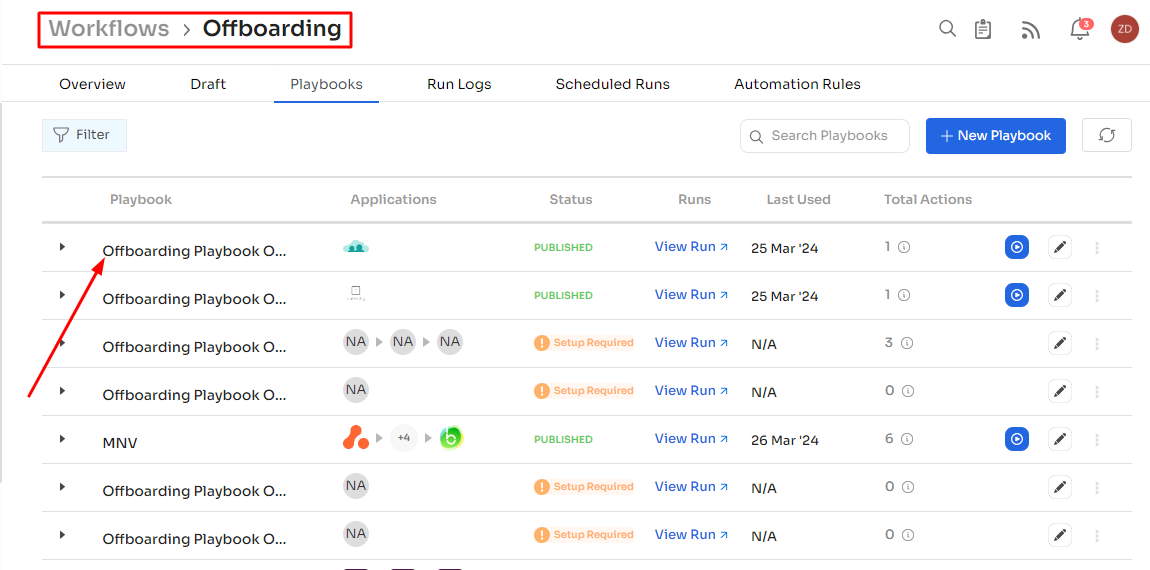
Customize offboarding policies triggered by user status changes in SSO for efficient and secure offboarding workflows. You can effortlessly create, edit, and duplicate playbooks to gain insights into run statuses and configure automation rules for a seamless process. Zluri minimizes the risk of unauthorized access and potential security breaches, ensuring a smooth transition during user offboarding.
Also Read: To know more about automating deprovisioning, you can go through How IT Teams can Automate Deprovisioning.
- Facilitate Automated Access Requests

Zluri simplifies access request management through automation. It provides an Employee App Catalog with pre-approved tools for employees to select based on their preferences and needs.
Features like automated license assignment, customizable approval policies, and the ability to override stalled requests enhance productivity and compliance. Users can also request access to specific applications not in the catalog directly through the platform, ensuring timely access to necessary resources.
Also Read: Want to know more about Zluri’s access requests? You must go through Self-service access requests blog.
- Manage Access Beyond SCIM

Zluri extends access management beyond SCIM, providing control and visibility over all applications irrespective of SCIM or SSO support. Zluri goes beyond and overcomes the challenges of managing access for applications without SCIM connectors with direct API integration, enabling automated provisioning for non-SCIM apps. IT teams can discover, manage, and control access to all apps, regardless of SCIM or SSO support.
Easily connect with over 300+ apps using API connectors and automate user provisioning, ensuring enhanced control, visibility, and security across the organization's entire access landscape.
Also Read: To know the role of SCIM in access management, you can read SCIM provisioning.
- Contractor/Third party Access Management

Zluri automates contractor access rights management, ensuring time-bound and automated access control. This feature enhances security and compliance measures, reducing risks associated with contractor access to sensitive data.
Pros
- It gives the IT team real-time reporting and analytics to monitor the overall app usage and make data-driven decisions.
- Zluri provides over 300+ APIs to connect with different systems and obtain individual insights, such as user names and usage details of each application.
Customer Rating
- G2: 4.8 /5
- Capterra: 4.9/5
Interested in exploring Zluri? Schedule a personalized demo today!
2: Auth0

Auth0 is a software that lets organizations set up a platform for authenticating and authorizing access management policies that work and can be accessed through the web, IoT, mobile phones, and other apps that have been around for a long time. This software gives better and stronger security checks that have multiple layers.
It helps clients meet the strictest industry standards and rules by using cutting-edge technology and good business practices. Auth0 lets organizations give their employees, partners, and customers the freedom to use Single-Sign-On (SSO) for multiple apps they have been permitted to use.
Pros
- It connects to several systems through its Single Sign-On (SSO) feature, which lets users sign in from a single platform anywhere in the world using a custom domain
- It provides an authentication API that connects to all the major database providers, making it easy and secure for users to access
Cons
- The custom login is hard to implement, making the authentication processes difficult for admin
- The pricing is quite high compared to other software options, which may be a hurdle for small-sized organizations
Customer Rating
- G2: 4.3 /5
- Capterra: 4.6/5
3: Okta
Okta is an identity and access management platform that securely connects an enterprise's suppliers, partners, and customers in a single loop. This gives users a great experience and makes management easy. It is an identity provider deeply integrated with hundreds of apps and can be accessed safely from multiple devices.
Okta sets a standard for identity that is independent and neutral. It's a place where the right people can connect to the right technologies at the right time. The tool gives you instant access to all apps with a single sign-on and provides an extra level of authentication to prevent identity attacks.
Further, Okta encourages lifecycle management, centrally manages a universal directory in your organization, and even controls and manages API access securely.
Pros
- It makes your organization’s entire lifecycle management easier by centrally managing a universal directory in your organization.
- Okta's login alerts require you to enter a code every time you log in, keeping your accounts 100% safe.
Cons
- Okta's lifecycle management and provisioning tools are difficult to configure, which may be problematic for users.
- The platform needs to be integrated with each application separately, which can be time-consuming.
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
4: Microsoft Azure Active Directory

Microsoft Azure Active Directory (AD) is an identity and access management system with features like SSO and multi-factor authentication (MFA) to secure your business from cyberattacks. Organizations can streamline user provisioning and lifecycle by automating individual workflows. It provides self-service features that enhance employees' productivity.
Azure Active Directory makes it easier for businesses to work together by granting outside parties, such as vendors and contractors, secure access to internal systems. The system's authentication methods use multiple factors to verify user identities, providing a higher level of safety.
Pros
- It supports integration with several other SaaS applications. Hence, multiple platforms can be consolidated in your existing active directory setup.
- With this IAM solution in place, you can manage identity and track users & their activities in your organization.
Cons
- Troubleshooting technical issues by the Microsoft team can be time-consuming and may cause difficulties in daily business processes.
- Azure AD is slightly on the expensive side especially if you have a lot of users and a large infrastructure to manage and maintain.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
5: WSO2 Identity Server

WSO2 Identity Server offers IAM solutions that are customer-focused and driven by AI. With the tool, businesses can give their digital customers a smooth, safe experience with no extra steps. For a better digital experience, the software supports SSO between apps that are logged in. It lets organizations use open identity standards like OIDC, SAML, and WS Federation to share access to their web and mobile apps across multiple domains.
It has modern identity and access management features that can be easily built into your organization's customer experience (CX) applications or used to meet the workforce's identity, and access management (IAM) needs.
With WSO2 Identity Server, businesses can evaluate user consent, revoke it, and keep track of it while following privacy rules. Its open-source nature makes it possible to get to the program's codebase. The API-driven solution can be scaled up or down to meet the needs of each business.
Pros
- It offers multiple authentication methods through federated IDP, making it easy to connect to a service through Facebook and Google developer APIs.
- The platform is highly customizable, thus, you can customize it as per your business requirements.
Cons
- It's difficult to install and configure for medium to large implementations. Thus, it might not be suitable for some organizations.
- The tool lacks identity governance features and possible PAM integration. As a result, you cannot manage identities and multiple admin profiles.
Customer Rating
- G2: 4.5 /5
- Capterra: 4.3/5
6: Ping Identity

PingIdentity is an IAM platform that lets companies give their employees authorized access to their networks, APIs, cloud apps, and on-premise apps. It helps businesses by giving secure access to the right people. Beginning with a PingOne solution package allows you to pay for only what you need and allows you to expand, whether you're merely looking for a single sign-on (SSO) or a risk-based, adaptive identification authority.
Ping Identity also combines, synchronizes, and stores data from multiple sources in a single repository to create access policies for restricted resources. The platform's SSO and MFA features make it easy for users to access the resources they need, which helps them be more productive. It also saves time and money for IT departments by making user IAM processes more efficient.
Pros
- The platform has built-in support for VPNs; hence, it's quite simple to integrate into your existing environment.
- You can download the app both on your laptop and on your smartphone.
Cons
- It has complexities with role management and entitlement creation that may cause hurdles in organizational processes.
- Synchronization can be an issue as it gets stuck sometimes and can result in power data quality.
Customer Rating
- G2: 4.4 /5
- Capterra: 4.7/5
7: OneLogin
OneLogin is a user-friendly and cost-effective IAM solution that provides every feature you need to protect your employees, customers, and business partners' data. You can use policy-based multi-factor authentication (MFA) and modifiable APIs to set up safe and adaptable authentication flows. It protects your business by putting all your applications, devices, and end users in one place and ensuring they are all secure.
AI-Powered SmartFactor Authentication from OneLogin makes it easier to see login attempts in real-time, so you can act quickly and stop high-risk activities. You can set risk thresholds easily and have authentication requirements changed automatically.
OneLogin's cloud infrastructure and Sandboxes let users run detailed tests on their codes before using them. This makes change management more accurate. Also, features like smart factor authentication, single sign-on, advanced directory, and identity lifecycle management help IT teams protect the identities of their employees from unnecessary threats.
Pros
- With OneLogin’s centralized repository, you can view all your applications on one screen. Thus, you no longer have to toggle between multiple tabs.
Cons
- UI is a bit confusing and may interrupt your user experience with the product.
- It can be expensive to set up, especially for small businesses, which can affect the budget of an organization.
Customer Rating
- G2: 4.3 /5
- Capterra: 4.6/5







.png)

.svg)














