Ensuring robust access governance and permission management for user identities is paramount in a security-focused SaaS environment. While Microsoft Entra has been a popular choice for overseeing permissions across different platforms, it does have some drawbacks.
Consequently, many IT managers are exploring Microsoft Entra alternatives, offering advanced features and greater flexibility.
IT managers must prioritize and safeguard sensitive data by ensuring the right user access and minimizing potential risks. Microsoft Entra serves as a solution that simplifies access governance and permission management within your organization. The platform presents a comprehensive suite of features, enabling your IT team to efficiently handle identities and access privileges.
By consolidating identity data, Entra Identity establishes a unified source of truth for all user-related information. This capability allows your team to achieve full visibility and control over user access across diverse systems and applications.
This blog post discusses leading Microsoft Entra alternatives, highlighting their distinctive features, pros, cons, and overall benefits. This list will equip you with the necessary insights to make a well-informed decision. But first, let's learn more about the Microsoft Entra platform and its drawbacks, due to which you might need an alternative to Microsoft Entra.
Microsoft Entra- Permission Management Tool
Microsoft Entra stands out as a leading permission management software renowned for its identity and access governance prowess. It streamlines the intricate task of managing user access rights, providing a unified solution for efficient permission management across your multi-cloud infrastructure.
With its user-friendly interface and robust automation features, Entra streamlines the processes of assigning, tracking, and revoking permissions across diverse applications and platforms. The platform adheres to the principle of least privilege, automating this practice and offering usage analytics to ensure that user identities always maintain the appropriate permissions.
However, despite its unique features, Microsoft Entra, as a permission management software, does have limitations. These limitations may prompt you to explore alternative solutions, which can vary based on your specific requirements and preferences.
Potential Limitations of Microsoft Entra
Let's delve into some drawbacks of this permission management platform, which may lead you to consider Microsoft Entra alternatives:
- The tool imposes limitations on configuring certain advanced features, such as advanced hunting, which can hinder your IT team's ability to fully utilize the tool, leading to inefficiencies.
- If you have budget constraints, this solution may not be cost-effective for your access management needs, as it is comparatively more expensive than other available products.
- If you are leveraging the tool in the cloud, this might not be the optimal choice for automating your permission management task, as cloud access can be slower due to security measures in place.
Having explored the limitations of Microsoft Entra, let's now examine essential factors to consider before selecting any specific alternative to Microsoft Entra.
10 Key Considerations Before Choosing the Right Microsoft Entra Alternatives
Before opting for Microsoft Entra alternatives, weighing several key considerations is essential. Here are 10 pivotal factors to carefully assess in the process of selecting the right alternatives to Microsoft Entra:
- Functionality and Features: Delve into alternative solutions' detailed functionality and features. Ensure they meet and align precisely with your organization's unique requirements and objectives. Look for functionalities that seamlessly integrate with your workflow.
- Scalability: Consider the scalability aspect of Microsoft Entra alternatives. Verify that they can easily accommodate your organization's anticipated growth and evolving needs over time. Scalable solutions are crucial to ensure a smooth transition as your organization expands.
- Integration Capabilities: Assess how well the alternative solutions integrate with your existing systems and applications. The goal is to ensure a seamless and efficient workflow, minimizing disruptions and facilitating a harmonious integration into your current IT ecosystem.
- Security Measures: Give precedence to solutions that implement robust security measures. Safeguard sensitive data and user identities by choosing alternatives that maintain high data protection. Look for features such as encryption, access controls, and compliance functionalities.
- User-Friendly Interface: Prioritize alternatives with an intuitive and user-friendly interface. A user-friendly design promotes easy adoption and usage across your organization, reducing the learning curve for IT teams and end-users alike.
- Cost and Licensing: Dive into alternative solutions' cost structure and licensing options. Analyze them meticulously to ensure they align seamlessly with your budget and financial considerations. Consider both initial and ongoing costs for a comprehensive evaluation.
- Vendor Reputation: Research the reputation of the vendors providing the alternatives. Consider factors such as reliability, customer satisfaction, and industry standing. A reputable vendor ensures a dependable partnership, reducing potential cyber risks associated with adopting their solutions.
- Compliance and Regulations: Ensure that the chosen alternatives comply with industry regulations and standards relevant to your organization. Mitigate risks associated with non-compliance by selecting solutions that prioritize adherence to legal and regulatory requirements.
- Support and Training: Assess the availability and quality of vendors' support services and training resources. A smooth implementation process and ongoing use are facilitated when robust support and comprehensive training options are readily available.
- User Feedback and Reviews: Consider user feedback and Microsoft Entra alternative reviews from organizations that have already adopted the alternatives. Gain valuable insights into real-world experiences and satisfaction levels. This information aids in making informed decisions based on the practical experiences of other IT teams.
Considering this, let's move towards our compilation of the top Microsoft Entra alternatives.
List Of 10 Best Microsoft Entra Alternatives
Listed below are the top 10 Microsoft Entra alternatives that offer extensive features, user-friendly interfaces, and robust capabilities to meet your access management needs:
1. Zluri
Zluri revolutionizes access control and governance, providing IT teams with effective tools to manage privileged access and protect valuable assets from theft or misuse. The platform ensures users have a clear view of privileged accounts, assets, and credentials, promoting transparency and security.
The centralized access hub simplifies managing and monitoring privileged access, ensuring a seamless process for granting or revoking access. Also, as per Kuppingercole's report Zluri initiates granular access control by identifying authorized individuals in the organization, laying a strong foundation for comprehensive access management. Informed decisions about user permissions can then be made, ensuring compliance and enhancing overall data security.
Beyond the basics, Zluri offers advanced features for precise control over access rights. With fine-grained permission management, IT teams can customize user privileges, alleviating concerns about unauthorized access and enhancing security measures. In short, Zluri is a complete solution, empowering organizations to confidently and efficiently manage modern access governance.
Key features
- Discovery Engine for Access Insights
Zluri incorporates a sophisticated discovery engine that identifies users' relationships with resources. Zluri uses 9 discovery methods to gain complete visibility into your organization's SaaS landscape. These methods include browser agents, IDPs & SSO, direct integrations, desktop agents, active directories, HRMS platforms, MDM platforms, finance systems, and CASB platforms. This empowers your team to identify and manage SaaS applications effectively.
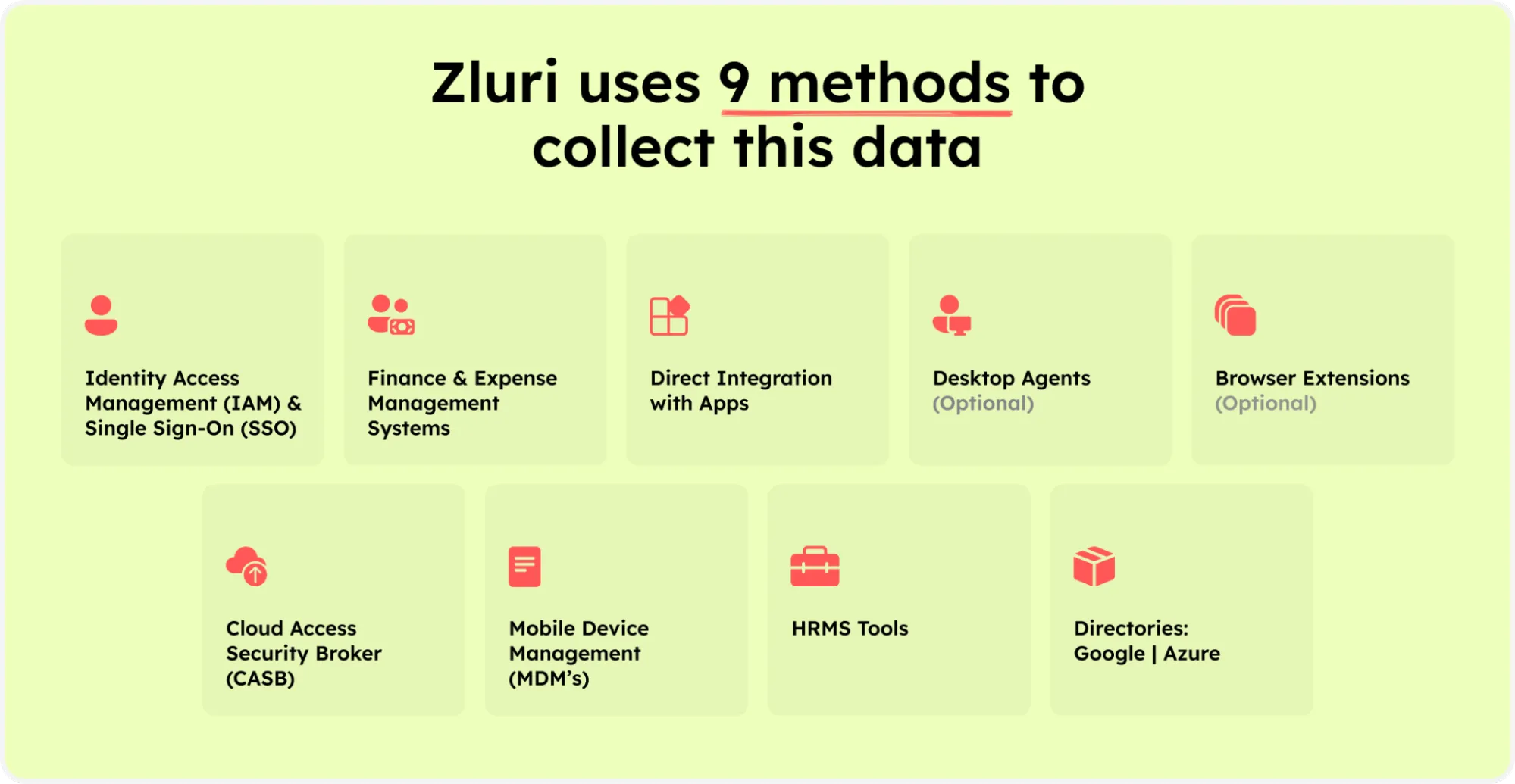
Zluri’s nine discovery methods
This capability enables the quick and detailed identification of application access, active user presence, granted authorizations, and user classifications, providing immediate insights into user access permissions.
- Automation Engine for Access Governance
Enhancing access governance, Zluri employs a robust automation engine overseeing access workflows. This ensures accurate authorization assignments and unwavering policy compliance.
The platform facilitates tailored and self-sufficient access and review workflows by instituting automation rules and triggers. This automation-centric approach streamlines access governance, optimizing administrative procedures and maximizing the potential of IT management.
- User Lifecycle Management with Automation
Zluri's access management solution streamlines the entire user lifecycle journey, offering unified provisioning and de-provisioning capabilities. IT teams can create and customize onboarding and offboarding workflows, ensuring users have the right resources and privileges during their tenure while seamlessly revoking access when needed.
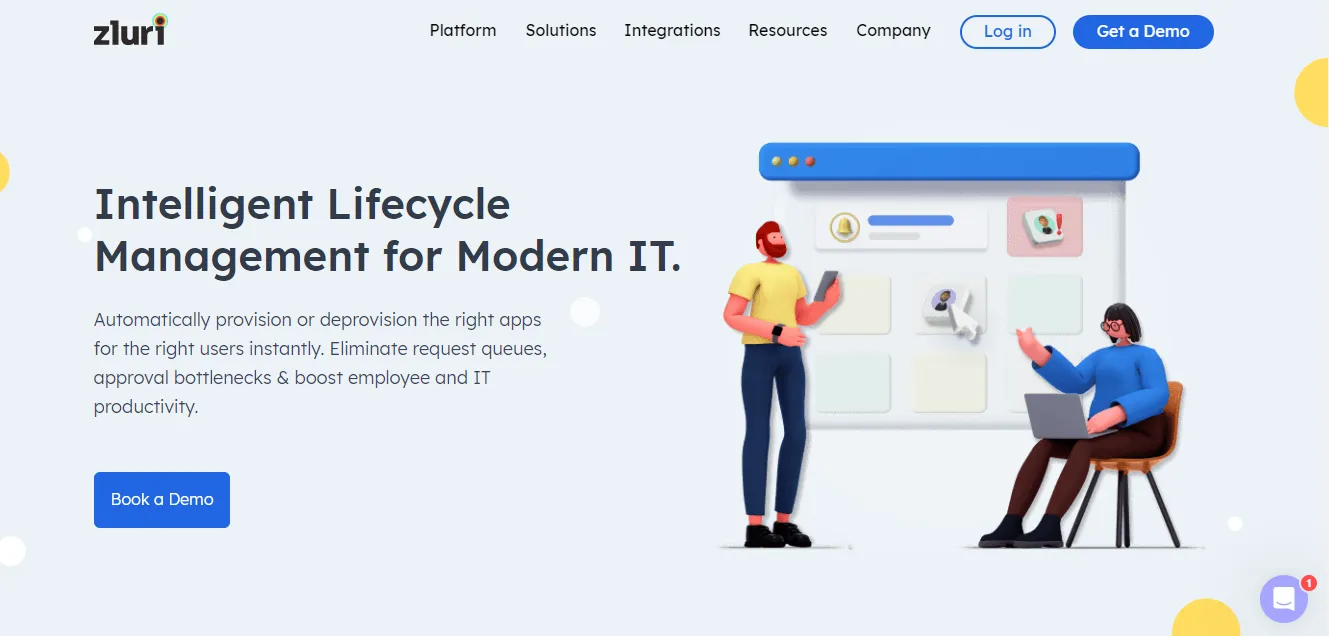
Personalized workflows, reusable playbooks, and smart app suggestions optimize user lifecycle management, enhancing efficiency and security.
- Self-Serve Model for Ad-Hoc Access Requests
Zluri introduces a self-serve ad-hoc access request management model called the Employee App Store (EAS). This platform streamlines the handling of ad-hoc requests, allowing IT teams to evaluate and grant temporary access as needed while maintaining overall access control.
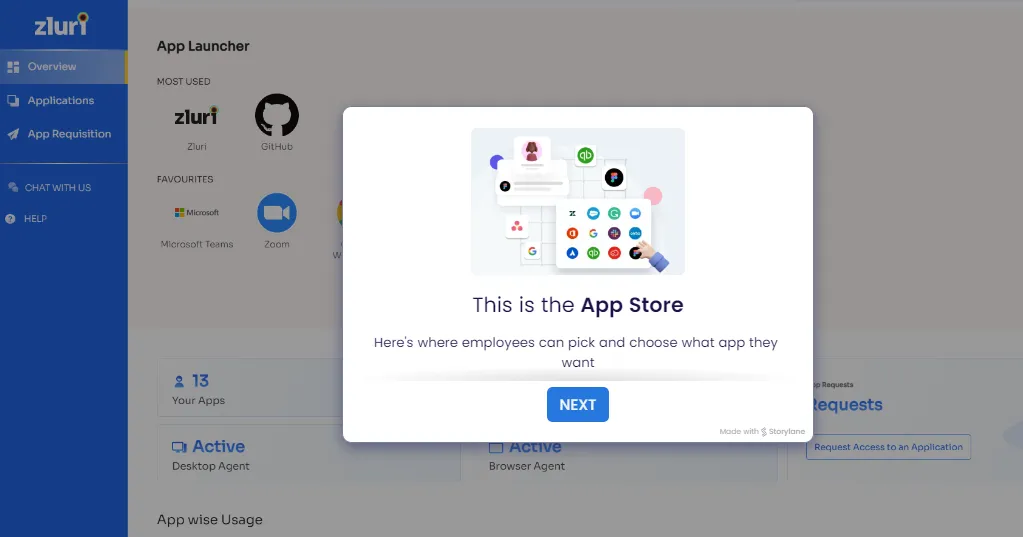
The employee app store provides a user-friendly interface for employees to track the status and updates of their requests, fostering transparency and efficiency in the access management process.
- Security & Compliance with Access Certifications
Zluri simplifies access control and fortifies compliance through centralized user access reviews and permissions management. The platform's access certifications offer a comprehensive audit trail, ensuring clarity on who accesses critical resources.
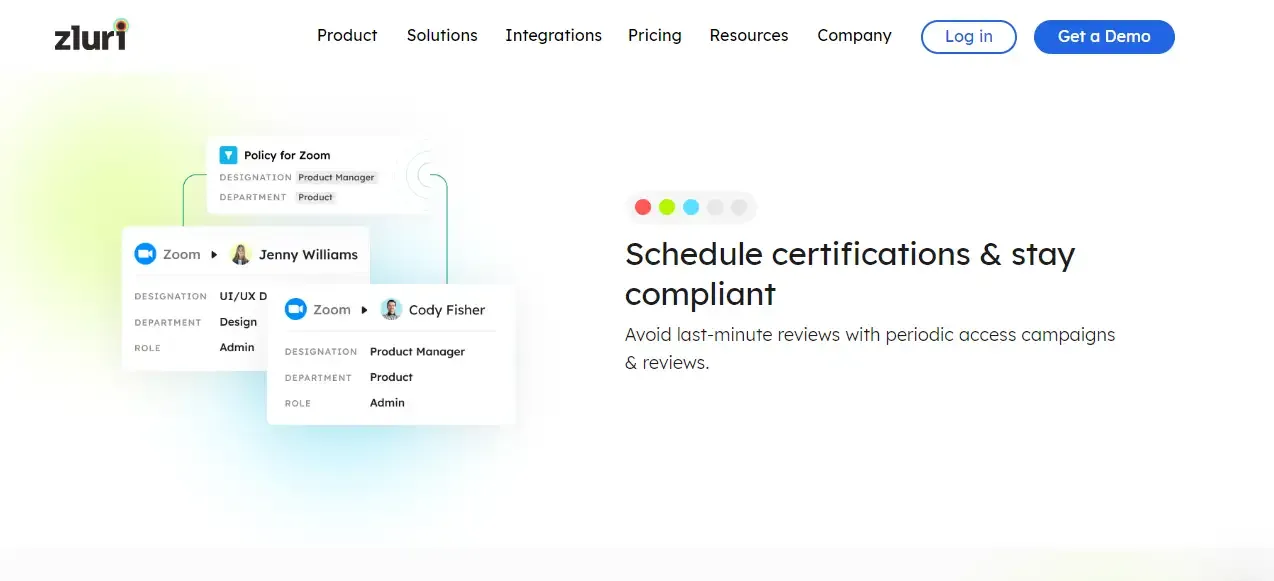
Automated access certifications, intelligent automation, auto-remediation capabilities, and real-time access reviews with anomaly detection provide proactive security measures while aligning with industry regulations and standards. The tool's AI-powered compliance insights and industry-standard certificate templates further contribute to robust compliance efforts.
Pros
- Zluri boasts an extensive library of 300+ API integrations, and you have the flexibility to effortlessly add custom integrations to your system within a remarkable 36-hour timeframe.
- With Zluri, you can establish conditional triggers that automate intricate IT processes, freeing up valuable time and effort for your IT teams while eliminating the potential for manual errors.
- Furthermore, Zluri provides a centralized hub for all your business data, granting your IT teams enhanced visibility into the organization’s performance. This consolidated view enables data-driven decision-making, empowering your organization to thrive.
Cons
- Zluri is intricately designed with a focus on mid-sized businesses, and therefore, it may not be the most suitable option for small organizations or those with fewer than 100 employees.
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Sailpoint Technology ( Clod Identity Platform)

The SailPoint Identity Platform offers a comprehensive solution for identity management within your organization. It centralizes processes such as user provisioning, deprovisioning, and lifecycle management, providing your team with complete visibility and control over user access.
With the SailPoint Identity Platform, you can implement precise access controls, ensuring users have the appropriate level of access for their job functions. Using role-based access controls (RBAC) and attribute-based access controls (ABAC), your IT admin can define and enforce access policies based on user roles, responsibilities, and contextual factors.
This approach enhances your security posture, reduces the risk of unauthorized access, and facilitates compliance with regulatory requirements.
Pros
- This solution is ideal for those searching for a streamlined access governance tool. It allows your team to integrate with existing systems effortlessly while offering comprehensive visibility throughout your entire access management infrastructure.
- The tool gives your IT team a thorough insight into users' access privileges across the organization, simplifying their capacity to monitor, manage, and ensure regulatory compliance with user permissions.
Cons
- The tool necessitates a significant time investment for your team to undergo training and achieve proficiency, diverting time and effort that could be directed toward other crucial tasks.
- This may not be optimal if you prefer a tool that offers easy customization and adaptation to specific needs. It exhibits limitations in terms of customization, potentially impacting its efficiency in managing user access within your organization
Customer rating
- G2: 4.4/5
- Capterra: 4.2/5
3. Okta
Okta is a versatile platform that offers an extensive range of features, and thus, it is one of the leading Microsoft Entra alternatives. The tool simplifies access to SaaS applications through passwordless authentication, ensuring a seamless and secure login experience.
The platform helps mitigate risks by implementing Okta Privileged Access, a comprehensive solution that enables unified access and governance management for on-premises, cloud, or multi-cloud privileged resources. With Okta Privileged Access, you gain enhanced control and security over critical digital assets, ensuring that privileged resources are accessed and managed in a unified and secure manner.
Moreover, Okta empowers your IT teams by offering automation capabilities and a low-code platform. This allows for streamlined workflows, reducing manual tasks and boosting overall productivity. With Okta, your IT teams can accomplish tasks more efficiently, focusing on high-value initiatives rather than repetitive processes.
Pros
- The tool acts as a centralized hub, consolidating multiple apps into a single platform, helping you gain access to all these tools, and creating a convenient one-stop shop for your application needs.
- The tool offers a user-friendly and straightforward dashboard, making it easy for your team to learn, navigate, and automate the access management processes efficiently.
Cons
- Sometimes, the platform may experience delays in loading; as a result, some components or pieces of content may take longer to load initially, thereby delaying the overall user experience.
- The platform has a minimal session period. If you use the app frequently, you'll need to go through the verification process with each login, which can be time-consuming
Customer rating
- G2: 4.5/5
- Capterra: 4.7/5
4. Ping Identity
Ping Identity streamlines the process of adaptive authentication & permission management by offering a centralized approach. Its comprehensive suite of features enables users to securely access data on-premise and remotely, facilitating network activity monitoring and offering user-friendly login options.
This tool significantly improves the employee experience by providing effortless access to resources. Ping Cloud Identity maximizes connectivity while minimizing friction by adopting a zero-trust security strategy. It carefully verifies an employee's role during provisioning and grants authorized access to relevant SaaS applications.
Similarly, when deprovisioning an employee, Ping Identity promptly deactivates their account, ensuring proper security measures are upheld throughout the employee lifecycle.
Pros
- The tool offers your team a super intuitive and easy-to-use platform, making it convenient for them to use the access management capabilities at their full potential.
- Due to Ping Identity's API-based approach, every activity performed on the console becomes accessible programmatically. This enables the automation of various tasks, streamlines processes, and saves valuable time and resources in your organization.
Cons
- Sometimes, your team needs to allocate extra time and effort to connect with the software because it may experience synchronization problems, delaying the process and the tasks involved.
- If you're considering migrating from one tool to another for access management, this option may not be ideal due to its initial complexity, which demands extra time and effort to set up.
Customer rating
- G2: 4.4/5
- Capterra: 4.8/5
5. Jumpcloud
JumpCloud facilitates managing and controlling access to various resources through its open directory solution, ensuring secure access to owned assets from anywhere.
With a mission to streamline work processes, JumpCloud enables seamless access to your organization’s data across devices and locations. The JumpCloud Directory Platform empowers your team to efficiently manage and govern all aspects related to employees, their devices, and the principles of Zero Trust that you have adopted.
JumpCloud simplifies access management by centralizing access to multiple systems, regardless of location, through its browser-based admin console. It automates identity creation for new hires, facilitates access changes during role transitions, and revokes all access promptly when an employee departs.
Pros
- The platform offers seamless integration with various relevant systems, allowing your team to effortlessly automate access management processes and enhance efficiency.
- If you're limited with your budget, this is an affordable solution, as the tool’s pricing levels are reasonable and include integrations and several other features.
Cons
- This might not be the best choice if you prefer a straightforward platform, as it offers many features that can make the platform time-consuming and complex for your IT teams to navigate and utilize effectively.
- Due to the absence of robust reporting capabilities, the tool may restrict your team from effectively viewing, analyzing, and managing workflows, potentially causing inefficiency.
Customer rating
- G2: 4.5/5
- Capterra: 4.6/5
6. Auth0
Auth0 offers a cloud-based access management and authentication platform that empowers you to manage and control access within your organization efficiently. This robust platform ensures high identity protection, safeguarding all inputs and access points.
With Auth0, you can secure your login activities, user profiles, and credentials using a combination of hosted and on-premise solutions. The platform provides an array of features, including custom domains, embedded authentication, single sign-on (SSO), database migration, account linking, and log retention and streaming.
By leveraging these features, you can enhance the security and convenience of your authentication processes while benefiting from seamless integration and comprehensive protection for your identity-related activities.
Pros
- The platform is simple to set up and configure, allowing your team to use it immediately and efficiently, automating the access management procedures.
- This tool offers your IT teams the utmost flexibility as it seamlessly integrates with various platforms and systems, ensuring effective usage without encountering any compatibility issues.
Cons
- This tool may not be ideal if you're looking for an affordable option. This is because the tool's price may increase when your team requires access to its advanced features.
Customer rating
- G2: 4.3/5
- Capterra: 4.6/5
7. CyberArk
CyberArk Privileged Access Manager is a robust solution designed to safeguard critical assets and protect against cyber threats. The platform helps you to effectively manage and control user access to privileged accounts and sensitive information.
This powerful platform offers a range of features, including secure authentication and authorization mechanisms, multi-factor authentication, and advanced access control policies. Implementing these capabilities helps your team prevent unauthorized access and minimizes the risk of data breaches.
CyberArk Privileged Access Manager also provides comprehensive visibility and auditing capabilities, allowing you to monitor user activities, detect suspicious behavior, and generate detailed reports for compliance purposes. This level of transparency enables you to proactively address security incidents and ensure regulatory compliance.
Pros
- Its password and session management capability ensures automatic logouts when users are inactive for a specific period, minimizing the chances of unauthorized access in case users forget to log out.
- The platform empowers your team to harness the full potential of its access management capabilities conveniently with its intuitive and straightforward user interface.
Cons
- Implementing and deploying the tool into your organization's systems may pose some challenges, requiring your team to invest extra time and effort to successfully automate access request workflows.
- Pricing poses a significant challenge when it comes to CyberArk solutions as its licensing model is based on a per-user basis, which can result in substantial expenses, particularly for larger organizations.
Customer rating
- G2: 4.1/5
- Capterra: 4.2/5
8. OneLogin
One Identity Privileged Access Management (PAM) solution effectively addresses security risks and ensures compliance. Whether you prefer a SaaS-delivered or traditional on-premises deployment, One Identity PAM provides comprehensive capabilities to secure, control, monitor, analyze, and govern privileged access across various environments and platforms.
With One Identity PAM, you can choose the level of access that suits your team's needs. This includes providing full credentials when necessary or adhering to Zero Trust and least-privileged operating models to restrict access. This enables you to establish a robust security framework tailored to your organization's specific requirements.
By leveraging One Identity PAM, you can mitigate security risks associated with privileged access and establish granular control over user permissions. The solution allows you to monitor privileged activities, detect suspicious behavior, and generate valuable insights for analysis and audit purposes.
Pros
- This tool provides your IT teams maximum flexibility by seamlessly integrating with various platforms and systems. Hence, it ensures easy and effective utilization by giving you access to all platforms and mobile applications.
- It offers extensive features like custom connectors that greatly enhance the platform's capabilities and features. This extension of functionality allows for smooth connectivity with various other SaaS apps.
Cons
- This might not be your best option if you're seeking powerful reporting capabilities. This is because the tool does not provide sufficient functionality for generating reports that could offer deeper analytical insights.
- The tool's user interface is complex, making it challenging for your team to simplify the access management operations. As a result, it consumes a lot of time of your team that could have been used in some important tasks
Customer rating
- G2: 4.3/5
- Capterra: 4.6/5
9. Rippling
Rippling's role-based permission system empowers you to grant access to specific Rippling services and third-party apps based on individuals' roles, departments, and levels within your organization. This automated process ensures that your team has appropriate access privileges. It also lets you maintain precise control over the information they can view and modify in Rippling.
From sensitive details like salaries and social security numbers to device operating systems, you have the ability to define exactly what data they can access.
By leveraging our role-based permission system, you can streamline access management, enhance data security, and ensure that individuals only have access to the information they need to perform their roles effectively.
Pros
- The tool boasts an intuitive interface that facilitates a smooth learning curve for your team, enabling them to easily navigate and start using it efficiently.
- This tool is a great choice if you're looking for an easy-to-implement platform. It's extremely straightforward to implement, allowing your team to complete the process easily.
Cons
- If you are limited on financial resources, it may be an expensive option as the tool’s prices are calculated per user. This means each user is associated with a specific cost and the overall expense increases with the number of users.
- The platform occasionally experiences glitches, causing the inconvenience of receiving numerous automated emails throughout the day, which can be quite bothersome for your admin.
Customer rating
- G2: 4.8/5
- Capterra: 4.9/5
10. LastPass
LastPass is a leading identity & access management solution, empowering users to effortlessly generate, store, and securely share login credentials with IT administrators. Beyond password protection, it gives admins transparency and authority through robust security guidelines and reporting mechanisms.
Distinguished by its extensive integration network, LastPass seamlessly connects with over 1200 pre-integrated single sign-on applications, expediting SSO access setup and streamlining the user experience.
At its core, LastPass features a robust zero-knowledge security architecture, ensuring the utmost confidentiality and fortification of user information. Additionally, it offers strong authentication options, including single sign-on and two-factor authentication, elevating access security to unprecedented levels.
Pros
- LastPass enhances login security by providing biometric multi-factor authentication, adding an extra layer of protection to user accounts.
- LastPass streamlines user experience by automatically populating login information for all saved websites. It also allows users to save login details for new websites they encounter.
Cons
- LastPass's auto-fill feature might encounter challenges when used simultaneously with other website form-fill features, leading to potential compatibility issues.
- Integrating LastPass within an organization may present obstacles during employee onboarding due to its technical requirements and the expertise demanded for efficient use.
Customer ratings
- G2: 4.4/5
- Capterra: 4.6/5
Zluri: Elevating Access Management Beyond Microsoft Entra Alternatives
In conclusion, Zluri emerges as the unparalleled choice for access management when compared to other alternatives, including Microsoft Entra. With its robust features, seamless integration capabilities, and user-friendly interface, Zluri not only meets but exceeds the expectations for efficient access management. The platform's commitment to innovation, security, and adaptability positions it as the optimal solution, providing organizations with a superior access management experience.
As businesses navigate the complexities of modern IT landscapes, Zluri stands out as the trusted partner, offering a comprehensive and cutting-edge solution that empowers organizations to enhance security, streamline processes, and elevate overall access management efficiency.
Choose Zluri for a future-proof and unparalleled access management experience. Book a demo!
Frequently Asked Questions (FAQs)
1. Is Microsoft Entra replacing Azure?
No, Microsoft Entra is not replacing Azure. Entra is an identity and access governance solution that works in conjunction with Azure Active Directory (Azure AD). Azure AD is a cloud-based identity and access management service that enables users to sign in and access resources.
2. What is Microsoft Entra vs Azure AD?
Microsoft Entra and Azure AD serve distinct but complementary roles. While Azure AD focuses on providing identity and access management services, Entra is specifically designed for identity and access governance. Entra helps organizations manage and govern user access rights effectively.
3. What are the key factors to consider when choosing Microsoft Entra alternatives?
While exploring Microsoft Entra alternatives, key factors include functionality, scalability, integration capabilities, security measures, user-friendliness, cost structure, vendor reputation, compliance with regulations, and user feedback. Assessing these factors will help determine the most suitable alternative for your organization.
4. What is Microsoft Entra used for?
Microsoft Entra is used for identity and access governance. It simplifies the complex task of managing user access rights within an organization. Entra provides a unified solution for effectively managing permissions for any identity across multi-cloud infrastructures, ensuring the right levels of access are granted to users.









.svg)














