Identity governance is crucial in our tech-driven world, with tools like RSA Identity Governance playing a vital role in managing access requests and more. However, considering its limitations, you might be looking for other RSA alternatives and competitors to maximize your team's effectiveness in access governance.
RSA Governance & Lifecycle is an identity governance and administration (IGA) tool that empowers your IT team with a range of capabilities for managing identities and user access to applications. It gives your IT team enhanced visibility into user access, enabling them to accurately track and monitor resource utilization within the environment. Further, it facilitates access certification processes for enhanced identity governance.
Let's learn more about RSA Governance and lifecycle.
Key Features of RSA Governance & Lifecycle
Let's explore a wide range of essential features of RSA.
- Comprehensive Identity Governance: RSA Governance and Lifecycle provides a centralized hub for managing identities across your organization. With a comprehensive view of identity data, you can promptly detect and mitigate potential security risks, maintaining a tight grip on your organization's overall security.
- Automated Lifecycle Management: RSA's solution automates the entire lifecycle of user identities, from onboarding to offboarding. This automated process reduces the burden on your IT team and minimizes the risk of human error.
- Role-Based Access Control (RBAC): Tailor access permissions with precision using RSA Governance and Lifecycle's Role-Based Access Control. This granular control ensures that each user has precisely the access they need, minimizing the risk of unauthorized access and data breaches.
- Compliance and Audit Trail: RSA's solution simplifies compliance management by providing a robust audit trail. Easily track and monitor user activities, access requests, and policy changes. This comprehensive audit capability facilitates adherence to regulatory requirements and provides valuable insights for continuous improvement of your security measures.
- Self-Service Capabilities: RSA Governance and Lifecycle offer a user-friendly interface for access requests and approvals, making the process more efficient and user-centric. This not only improves productivity but also enhances user satisfaction within your organization.
- Risk Analytics and Intelligence: The solution employs sophisticated algorithms to identify and assess potential user access and behavior risks. Proactively address and mitigate these risks, bolstering your organization's resilience against evolving cybersecurity challenges.
While the RSA Identity tool offers many exceptional capabilities, it is crucial to acknowledge that even the most impressive solutions may have certain limitations. In the case of RSA, specific drawbacks can hinder your team's efficiency and effectiveness in managing user identities and access. Therefore, it is prudent to consider exploring alternatives to address these limitations and provide a more tailored solution for your specific requirements.
Some Drawbacks of the RSA Identity Governance Platform
Below are a few potential drawbacks of RSA Identity Governance that you should consider:
- If affordability and user-friendliness are key factors for choosing an IGA tool, this solution may not be the most suitable choice. Its Aveska package (suite of IAM products) is relatively expensive, and new users may need to invest time in learning the tool's functionalities to manage and govern access effectively.
- Due to its collection-based architecture, the system delays access provisioning and user account setup for groups. This means it requires collecting account information from end targets before provisioning groups, causing delays in the overall provisioning process within your organization.
- The tool lacks advanced automation capabilities, which can limit its effectiveness in streamlining processes and reducing manual efforts. With minimal automation capability, everyday tasks need to be performed manually, leading to an increased workload for your team.
Let's move to our RSA alternative options list based on these considerations.
List Of Top 9 RSA Alternatives
Let's delve into the world of alternatives to RSA Governance & Lifecycle, exploring 9 compelling options that can meet your identity governance and administration needs:
1. Zluri
Zluri introduces a remarkable identity governance and administration platform that equips your IT team with the tools they need to manage and monitor user access efficiently. While traditional platforms are tailored for on-premises environments, Zluri's Identity Security platform is specifically designed for the evolving world of SaaS and AI.
Zluri's Identity governance and administration solution focuses on essential IT functions, including authentication, authorization, privacy, data protection, and regulatory compliance.
By leveraging Zluri's IGA platform, your IT team can effectively govern user identities, streamline access provisioning, and enhance overall security in the SaaS and AI landscape.
Let's explore how Zluri stands out from other IGA tools by offering unique capabilities.
1. Powerful Discovery Engine
Zluri simplifies the process for your IT team to analyze and discover valuable data related to your SaaS applications and users. The platform employs nine robust discovery methods - MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional), ensuring a thorough identification of crucial information.
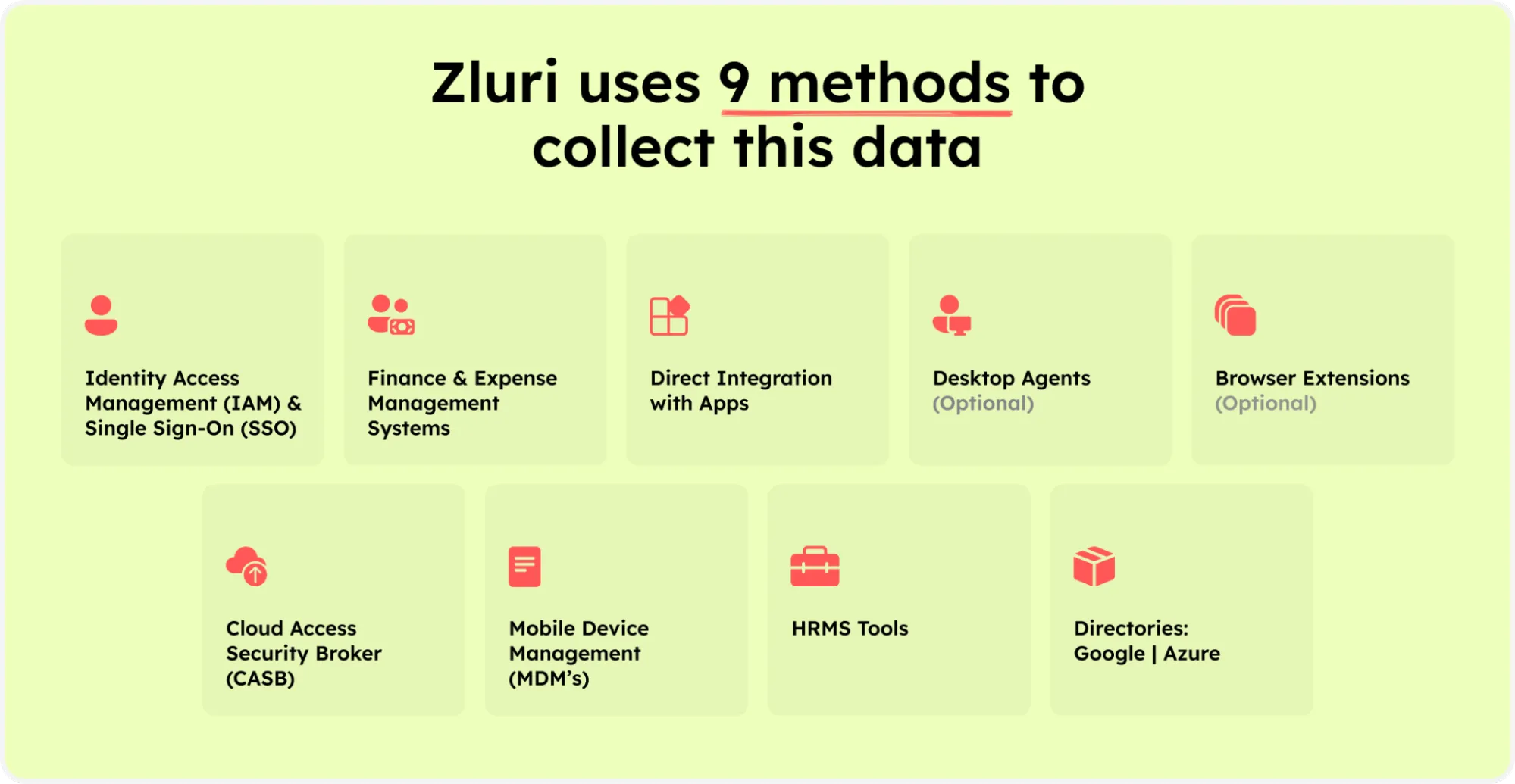
Zluri’s nine discovery methods
Why should you choose Zluri?
- Seamless Integration with 300+ SaaS Applications: Zluri doesn't just stop at discovery; it takes it to the next level by seamlessly integrating with over 300 SaaS applications. This integration allows for real-time data access, valuable insights, and AI-powered alerts, keeping you updated and well-informed.
- Thorough Data Discovery Through API Integrations: Zluri ensures comprehensive data discovery across all your SaaS applications through API-based integrations. This guarantees no hidden information, providing 100% visibility into your entire SaaS environment.
- Extensive Library of 240,000+ Apps: What sets Zluri apart is its vast library containing over 240,000 apps. This extensive collection enables detailed access to data, allowing you to dive deep into specifics. Gain effortlessly a comprehensive understanding of user permissions and access levels within your SaaS ecosystem.
- Effortless and Effective SaaS Management: With Zluri, managing and securing your SaaS applications becomes effortless and effective. The discovery engine ensures you have the tools to maintain control and optimize your SaaS environment.
2. Robust Automation Engine for Access Management
Imagine Zluri's automation engine as the self-driving system for your organization. Effortlessly managing access workflows, this advanced engine guarantees seamless and efficient automation through meticulous reviews and adherence to a well-defined set of rules and policies.
- User Lifecycle management
Zluri simplifies the entire user lifecycle journey, covering everything from onboarding to offboarding. With Zluri's unified provisioning and de-provisioning capabilities, you can efficiently manage user access in the cloud environment. This streamlined process ensures that users have the necessary resources and privileges during their tenure while seamlessly revoking access when they no longer require it.
Why should you choose Zluri?
- Custom Workflows for Effortless Transitions: Zluri introduces personalized workflows that revamp organizations' onboarding and offboarding processes. These tailored workflows are crafted to suit specific roles, departments, or individual preferences, ensuring every user's seamless and personalized experience.
- Reusable Playbooks for Time Savings: Zluri provides the capability to save onboarding and offboarding workflows as reusable playbooks. This eliminates the need to recreate workflows for each user, saving valuable time and effort for IT teams.
- Consistency Through Predefined Playbooks: Using predefined playbooks, IT teams can ensure consistent adherence to necessary steps during onboarding and offboarding. This reduces the chance of errors or omissions, enhancing efficiency and accuracy in managing user transitions within the organization.
- Personalized App Recommendations for Optimal User Experience: Zluri offers personalized app recommendations based on an employee's role and department. This ensures access to their job's most relevant and approved tools, enhancing the overall user experience.
- In-App Suggestions for Enhanced Guidance: Zluri provides in-app suggestions that guide users within applications. This helps new users follow best practices, adhere to security protocols, and avoid risky behaviors while using various software tools, promoting productivity and adherence to organizational policies.
You can refer to these linked blog posts to learn more about creating onboarding and offboarding workflows.
- Ad-hoc access request management
Zluri revolutionizes access request management with its self-serve model, the Employee App Store (EAS). This innovative feature simplifies handling ad-hoc access requests, particularly during role changes.
As per KuppingerCole’s report, with Zluri’s EAS, access requests are streamlined, improving employee experience, and removing friction for IT teams.
With EAS, your IT team gains full control over granting access to essential tools based on employees' job roles and permissions. You can customize the content and determine which apps are visible to each employee, ensuring a personalized and relevant experience.

With EAS, your IT team gains full control over granting access to essential tools based on employees' job roles and permissions. You can customize the content and determine which apps are visible to each employee, ensuring a personalized and relevant experience.
Why should you choose Zluri?
- Streamlined SaaS Management:
- Zluri's EAS simplifies the management of SaaS requisitions, approvals, and revocations.
- No more dealing with a multitude of tickets, allowing your team to focus on strategic tasks.
- Efficient Approval Workflow:
- IT admins or designated approvers can quickly review and approve access requests.
- Ensures requested permissions align with employees' job responsibilities.
- Robust Governance Mechanism:
- Prevents unauthorized access to sensitive information within your organization.
- Higher-level authorities can override decisions for efficient access control.
- Empower Decision-Making:
- Enables higher-level authorities to override decisions by lower-level admins or managers.
- Facilitates efficient decision-making in the access control process.
- Transparent Request Tracking:
- Employees can easily track the status and updates of their requests.
- The \"changelog\" feature provides comprehensive information on approvals, rejections, and any changes made by admins.
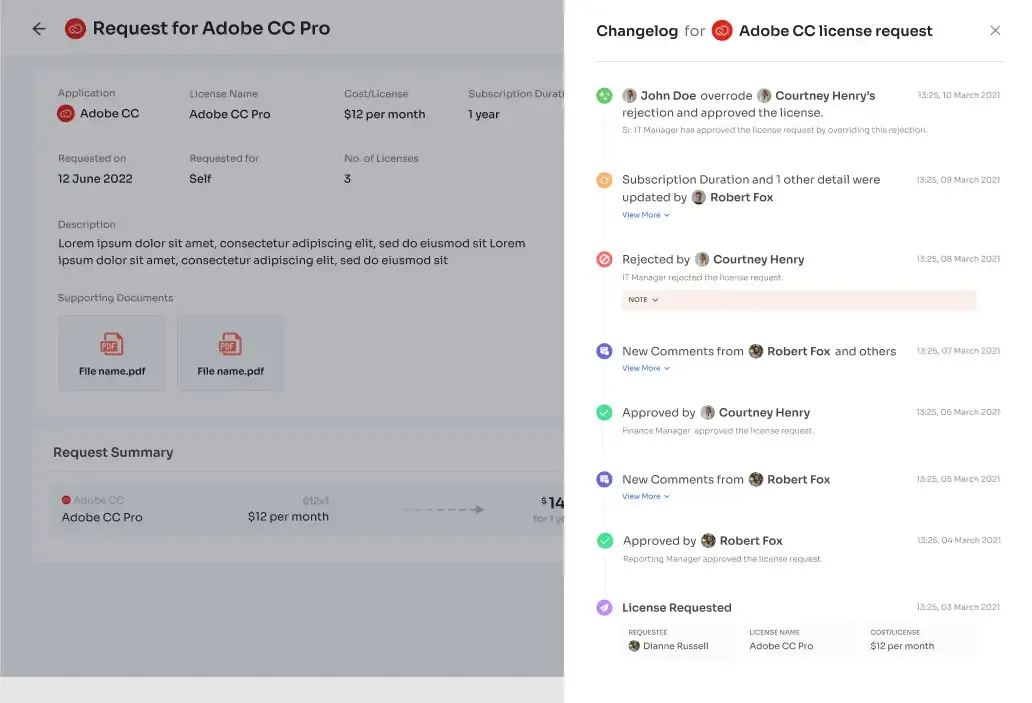
- Enhanced Visibility and Accountability:
- Ensures visibility throughout the secure access management process.
- Comprehensive changelog information includes approval/rejection details and admin comments.
3. Robust access certifications for Governing Access
Zluri's IGA solution streamlines your user access review process and permission management. With Zluri, your team and auditors can effortlessly review and report on user access all in one centralized platform.
Why should you choose Zluri?
- Intelligent Automation for Efficiency:
- Automation saves time and minimizes errors compared to manual methods.
- Easily set review parameters, select reviewers, and schedule campaigns with a user-friendly platform.
- Auto-Remediation for Enhanced Security:
- The unique auto-remediation feature takes immediate action on detected access violations.
- Enhances organizational security by revoking access for terminated employees or those with outdated privileges.
- Comprehensive Reporting for Informed Decisions:
- Detailed reports give valuable insights into access patterns, vulnerabilities, and compliance status.
- Demonstrate compliance with auditors and make informed decisions about access management.
- Real-time Access Reviews with AI:
- Zluri stands out with continuous and real-time access reviews using AI capabilities.
- Proactively identify unusual or risky activities, bolstering security measures to protect sensitive data.
- Certification Templates for Simplified Processes:
- Industry-standard certificate templates simplify access certification processes.
- Recurring and scheduled certifications maintain control over access privileges, reducing the chances of missing critical issues.
- Alignment with Industry Regulations:
- Zluri's AI compliance capabilities align access controls with industry regulations.
- Mitigate the risk of compliance violations, making it easy to meet regulatory requirements seamlessly.
Experience the full potential of Zluri's Identity Governance by scheduling a personalized demo today!
Pros
- Zluri distinguishes itself from traditional IGA tools through its effortless implementation process and intuitive user interface, ensuring a smooth and user-friendly experience for your IT team during adoption and usage.
- Its alerting system ensures timely notifications of unauthorized access, empowering your IT team to proactively safeguard sensitive data.
- Zluri empowers your team to personalize actions and effectively limit or revoke access to critical applications and users. This capability enhances the security of your organization's data.
Cons
- With Zluri's extensive integration ecosystem, your IT team may find themselves grappling with an increased workload. The more integrations you adopt, the higher the overhead for your IT team. This can lead to stretched resources, potentially affecting their ability to focus on strategic initiatives or promptly address critical issues.
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. OpenIAM Identity Governance
OpenIAM Identity Governance, one of the best RSA alternatives, is a robust solution that empowers organizations to manage and govern user identities and access rights effectively. With OpenIAM Identity Governance, your IT team gains centralized visibility and control over user identities across multiple systems and applications. This comprehensive view allows for streamlined management of user onboarding, provisioning, and offboarding processes.
The solution enables you to enforce granular access controls, ensuring users have the appropriate access privileges based on their roles and responsibilities. Through role-based access control (RBAC) and attribute-based access control (ABAC) mechanisms, OpenIAM Identity Governance helps your IT team maintain a strong security posture while enabling efficient access provisioning.
Furthermore, Your team can generate detailed reports on user access, activities, and compliance status, which are crucial for meeting regulatory obligations and supporting audit processes.
Pros
- The platform allows your IT team to customize access policies based on the employees' roles, providing granular control over permissions and ensuring security in your organization.
- It helps you assign access permissions and policies based on your employees' roles within the organization. Thus, aids in efficient and granular control over user access, ensuring that team members only have access to the resources necessary for their specific job responsibilities.
Cons
- It occasionally saves passwords incorrectly, resulting in the need for manual intervention to rectify and update them. This can be a time-consuming and inconvenient process for your team.
- This tool lacks a substantial user base, making it challenging for your team when seeking support or assistance, as the availability of resources and expertise may be limited
Customer Rating
- Capterra: 4.3/5
3. ManageEngine AD360

ManageEngine AD360 is among the notified RSA competitors and is a powerful identity governance and administration (IGA) solution to manage and secure identities across your organization.
From provisioning to deprovisioning and every change in between, AD360 allows you to manage identities across multiple platforms such as Active Directory (AD), Microsoft 365, Exchange, Google Workspace, and more. All these can be done conveniently from a single window, simplifying the management process.
It helps you ensure compliance, prevent unauthorized access, and mitigate threats with AD360's real-time auditing and alerting capabilities. With over 1000 preconfigured reports, you can easily monitor and track activities across various platforms, including AD, file servers, Windows Server, Microsoft 365, workstations, and Exchange. With AD360, you can effectively manage and secure identities across your organization, ensuring compliance and protecting your valuable assets.
Pros
- The platform offers your team a single console for managing a suite of Manage Engine apps. This centralized console allows them to conveniently access and control multiple applications from a unified interface, saving time and effort by eliminating the need to switch between different tools or interfaces.
- It provides strong reporting features, allowing your team to retrieve any kind of information from their Active Directory objects. This empowers your team to generate comprehensive reports tailored to their specific needs, enabling better insights and analysis of their Active Directory data.
Cons
- AD360 may not display the full features of the Manage Engine Suite of applications within its console. However, when accessed individually outside of the console, all the features within the same installation set become available. This can cause inconvenience and may require users to switch between different interfaces to access all the required functionalities.
- It lacks certain options for auditing OneDrive sharing and local Active Directory auditing. Thus, creating specific reports can be challenging for your team. This limitation may hinder their ability to accurately track and monitor these specific activities within the identity environment.
Customer Rating
- G2: 2.5/5
4. One Identity Manager
One Identity Manager, a notified alternative to RSA, is an identity management software that prioritizes business needs over IT capabilities. A strong focus on governance and security enables your team to manage and protect their data and users effectively. One Identity Manager helps users meet uptime requirements, reduce risks, and ensure compliance by granting users access to the necessary data and applications.
It provides:
- A centralized platform for managing identities and access rights.
- Streamlining the process.
- Ensuring consistency across the organization.
The software enables organizations to provision and deprovision user accounts efficiently, manage user roles and permissions and enforce strong authentication methods.
Additionally, One Identity Manager offers advanced features for access governance, such as access certifications and compliance reporting. These capabilities enable your IT team to regularly review and validate access rights, ensuring compliance with regulations and internal policies.
Pros
- It enables your team to perform most configurations without requiring coding knowledge. This user-friendly approach simplifies the setup process and empowers them to customize the tool according to their specific requirements.
- The tool provides robust support for integrating with various cloud-based applications, making it easy for your team to connect and manage all the applications in a unified manner. It enables smooth collaboration and access management across the organization's cloud ecosystem.
Cons
- The platform lacks a user self-service portal, so users cannot independently request access for themselves, groups, or specific roles. The lack of this feature causes additional manual work for your IT teams and potential delays in granting access, impacting productivity and user satisfaction.
- If you are considering migrating from one IGA tool to another, it's important to note that this may not be ideal as it lacks user-friendliness during the initial stages. Your IT team might require additional time and effort to become familiar with its functionalities and interface.
Customer Rating
- G2: 3/5
- Capterra: 5/5
5. Microsoft Azure Active Directory

Microsoft Azure Active Directory, one of the best RSA alternatives, offers robust identity governance and administration (IGA) capabilities that enable your Governance, Risk, and Compliance (GRC) IT team to meet compliance requirements effectively. With Azure AD, your team can automate various critical processes such as access request workflows, access reviews, and certifications. One notable feature of Azure AD is its ability to provide secure user access, including external users. This means your team can extend access to external collaborators or partners while maintaining control and governance.
This solution empowers you to streamline user access management by automating repetitive tasks and ensuring consistent compliance. Regular access reviews can be conducted effortlessly to verify that access rights align with policies and regulations. Additionally, Azure AD provides a comprehensive audit trail, enabling your team to track and monitor user activities for enhanced security and accountability.
Pros
- The tool equips your team with the capability to effectively manage external identities such as vendors, contractors, freelancers, and more. It empowers them to grant access to external identities with restricted permissions, ensuring the protection of sensitive data
- The tool empowers your team to enforce robust authentication policies, such as multi-factor authentications (MFA) or privileged access, granting them control over access management and effectively preventing unauthorized access.
Cons
- If your organization relies heavily on on-premise systems, this tool may not be optimal for managing and governing user access. Due to its limited features for on-premise systems, it may hinder your team's ability to perform their tasks effectively.
- The tool presents a significant learning curve, posing challenges for your team in mastering certain tasks, such as creating access workflows and monitoring user access levels.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
6. Bravura Identity
Bravura Identity (formerly known as Hitachi ID), one of the prominent RSA alternatives, offers a seamless solution for managing the entire identity lifecycle. From user onboarding and provisioning to access certification and offboarding, the platform provides a centralized view of user identities and their access rights.
The platform enforces granular access controls, allowing users to access only the resources necessary for their roles. You can configure role-based access controls through a user-friendly interface, implement segregation of duties, and establish approval workflows.
An added benefit of Bravura Identity is its generation of detailed audit logs, capturing all changes made to user accounts and access rights. This feature empowers your team to effortlessly track user activity, monitor access requests and approvals, manage data governance, and generate compliance reports for both internal and external stakeholders.
Pros
- The tool offers a robust app approval workflow that significantly reduces waiting times for employees' app requests. This enhances productivity and mitigates security risks by ensuring employees have timely access to the tools they need.
- If you are looking for a user-friendly solution, this tool is well-suited for your needs. Your IT team can easily adopt and utilize the tool to govern, mitigate security risks, and ensure compliance effectively.
Cons
- One significant challenge your team may face is the lack of timely support and difficulty in reaching the support team via phone.
Customer Rating
- G2:4/5
- Capterra: 4.2/5
7. Okta Identity Governance
Okta's Identity Governance, one of the best alternatives to RSA, provides a powerful platform that empowers your IT team to manage user access across various systems and applications effectively. By consolidating all access controls in one central location, the platform simplifies the process of granting or revoking access to resources.
The platform offers robust auditing and reporting features, equipping your team with the ability to closely monitor user activities. With these capabilities, you can easily track and analyze user actions, generate detailed reports, and ensure compliance with regulatory requirements during audits. This comprehensive approach to security enables you to maintain a strong governance framework and protect sensitive data effectively.
By leveraging Okta's Identity Governance, your IT team can optimize user access management, streamline administrative tasks, strengthen security measures, and stay compliant with industry regulations.
Pros
- The tool's user identity verification system uses a six-digit passcode to confirm the identity of a user and grant them appropriate access. This added layer of security helps protect your organization against potential threats like unauthorized entry.
- It empowers your team with robust integration capabilities, allowing them to seamlessly integrate applications either directly or manually. This integration functionality enables efficient access tracking for audit purposes.
Cons
- The tool's push notifications for user requests may occasionally encounter delays, necessitating users to obtain the access passcode manually for the desired application.
- Okta's pricing structure may not be the most suitable option if cost-effectiveness is a priority. Its pricing model can be confusing and challenging to navigate, making it difficult to determine the exact costs associated with your specific needs.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
8. Omada Identity
Omada Identity, one of the prominent RSA competitors, presents a solution designed to streamline identity governance within your organization. With a robust suite of features, Omada Identity empowers your team to efficiently manage identities and access privileges.
By consolidating identity data, Omada Identity establishes a centralized hub for all user-related information. This single source of truth gives your team comprehensive visibility and control over user access across diverse systems and applications. With this holistic view, you can effectively monitor and govern user access, reducing the risk of unauthorized or inappropriate access.
Furthermore, Omada Identity simplifies and automates the entire user lifecycle management process. The platform offers intuitive workflows and role-based access controls from onboarding to offboarding. This ensures that users are granted appropriate access rights based on their specific roles and responsibilities, enhancing security and compliance while reducing administrative overhead.
Pros
- If your team is involved in database exploration, you'll discover that the tool's structure and functionality are easily customizable and easy to understand. This allows your team to gain deeper insights and make more informed decisions based on the available data
- The tool provides exceptional account management capabilities, empowering your IT team with a streamlined and efficient process for enabling access. Its user-friendly interface makes the task remarkably easy and swift, enhancing overall productivity and efficiency.
Cons
- The initial setup process of the tool can be time-consuming, leading to delays in efficiently managing user access and potentially impacting users' productivity.
- The tool's interface may not provide a smooth user experience, posing challenges for your team in efficiently managing user access. This delay can consume valuable time that could have been dedicated to more critical tasks.
Customer Rating
- G2: 3.8/5
9. ForgeRock Identity Governance
ForgeRock Identity Governance, a notified RSA cheaper alternative, helps you to enhance your identity and access management processes, prioritizing security, compliance, and efficiency. This powerful tool enables your team to manage user access, mitigate risks, and establish a robust governance framework effortlessly.
With ForgeRock Identity Governance, the complexities of user onboarding, changes, and offboarding are simplified, ensuring that the right individuals have timely access to the appropriate resources. This streamlines the process, improves operational efficiency, and minimizes the potential for unauthorized access or data breaches.
Your team can generate detailed reports on user access, permissions, and activities, which are invaluable for meeting regulatory requirements and successfully passing audits. These reports demonstrate adherence to industry standards and regulations and address any areas that require attention or improvement.
Pros
- The tool's highly flexible interface can be customized to perfectly align with various identity management requirements. Additionally, it offers extensive integration capabilities, ensuring seamless connectivity with existing systems.
- The tool's OIDC compliance simplifies authentication and enhances security by leveraging industry-standard protocols. This compliance allows your team to connect with a wide range of identity providers, ensuring compatibility and interoperability.
Cons
- The tool has limitations when it comes to integrating with certain systems, such as Unix-based systems. This restricts your team's ability to effectively manage access to these systems, potentially leading to security risks for your organization.
- Moreover, its reporting capabilities may not meet your expectations, limiting your visibility to check various access levels and identify any gaps during audits, potentially affecting your ability to stay compliant.
Customer Rating
- G2: 4.4/5
- Capterra: 5/5
Govern Your User’s Access Efficiently: Select the Suitable RSA Alternative
As we've delved into various RSA alternatives, it's evident that these solutions address the core tenets of identity governance and bring innovation to the forefront. The dynamic nature of contemporary cyber threats necessitates a proactive stance, and these alternatives stand ready to meet the evolving demands of identity security.
As an IT manager, evaluate your IGA needs; considerations around scalability, user experience, and regulatory compliance become paramount. The alternatives discussed in this article provide a nuanced understanding of how different solutions can align with specific organizational requirements, enabling you to make informed decisions based on their unique contexts.
FAQs
What is RSA authentication?
Enhancing the security landscape within the Flexible Management Topology is made effortless through the utilization of the RSA Authentication Mechanism. This multi-factor authentication mechanism streamlines the process of securely registering new servers to the Flexible Management Topology, ensuring a seamless and robust extra layer of security.
What is the main purpose of RSA?
Empower your communication with RSA, allowing you to secure your messages proactively before transmission. This advanced technique ensures the confidentiality of your data and allows you to certify your notes, assuring recipients that they remain unchanged and unaltered during transit. Recognized as one of the most widely adopted encryption tools in the current landscape, the RSA algorithm stands as a stalwart safeguard for your data integrity.
What are the key parameters of RSA?
In the foundation of the RSA cryptosystem lie three key parameters: the public exponent (e), public modulus (n), and private exponent (d). The robust security of RSA hinges on the complexity of factorizing large integers—a formidable challenge. Therefore, selecting the appropriate size for these parameters is paramount, among other critical considerations, to fortify the resilience of the RSA cryptosystem.







.png)

.svg)














