Determining who can access sensitive apps, systems, and data under particular circumstances is a constant challenge for most organizations. However, this issue can be effectively addressed with the help of context based access control (CBAC). But what is CBAC? In this article, we'll discuss it in detail.
Before we dive into the details of context-based access control, let's first address one common misconception: Any access control can be used to meet any type of access requirements and security needs. Well, this assumption is completely wrong. Why?
Each access control is designed to serve a distinct purpose. Therefore, they simply can't be applied to every scenario (random situation). For example, to restrict access permissions, role based access control (RBAC) solely focuses on reviewing the users' roles, whether they are managers, employees, or admins. On the other hand, least privilege access control (PoLP) puts more emphasis on limiting users' access to apps post authentication. Both of them are designed for different use cases; therefore, you can't use RBAC in place of PoLP— if you do, they won't simply deliver the results you are looking for.
Likewise, you cannot use RBAC and PoLP to block users from accessing your app from a restricted location. In this case, context based access control (CBAC) will be more applicable. In short, you need to apply the right control in the right scenario to fully benefit from it— as simple as that!
So, now that the confusion is cleared and you have gotten a glimpse of context based access control, let's understand it in detail.
What Is Context Based Access Control?
Context based access control (CBAC) is a type of control that evaluates conditions/factors such as who (identity) is requesting access, what (device) they’re using, when (time) the request is made, where (geographic location) the access requester is located, and why(purpose) they need access to determine whether to grant or deny access to an app, systems, or database.
In fact, upon access approval, CBAC also decides what level of access permission (e.g., read-only access or write/modify access) should be given to the access requester (users).
Note: Unlike other access controls that rely solely on predefined roles or attributes to manage access, CBAC incorporates contextual conditions for more precise and adaptive access management.
Also Read: 4 Types of Access Control
However, to understand the context based access control concept better, you need to be familiar with key components. What are these key components? Let’s quickly go through them.
Key Components of Context Based Access Control
Below, we’ve explained the five key components of context based access control in a detailed manner:
1: IP Based Access
During the authentication process, CBAC evaluates the IP (internet protocol) address of the user requesting app/system access to check if it originates from a trusted source, network, or range and is legitimate. If the IP address matches a recognized and secure range, then CBAC further approves the request and grants the user access to the requested app/system.
If it doesn’t match any trusted source, context based access control sets up rules to deny access requests immediately.
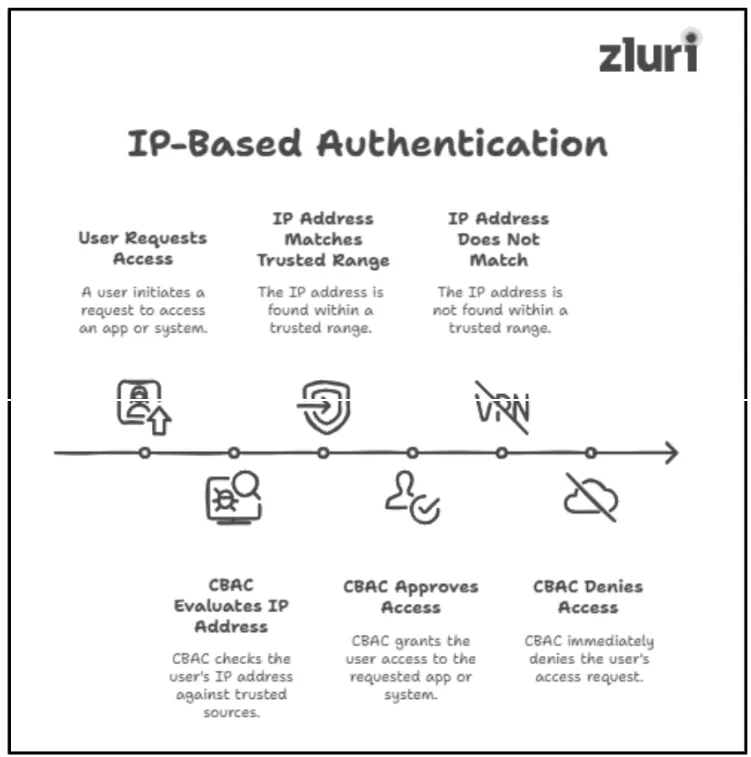
Note: Organizations generally maintain a whitelist (a list of trusted IP address ranges); any access request coming for an IP within that range is considered trusted. So, context based access control generally goes through this whitelist before approving any user from entering the organization’s ecosystem.
2: Geo-Location Based Access
During the authentication process, CBAC also considers verifying the geographic location of a user requesting app access and then decides whether to grant or deny their access requests accordingly.
For example, if users try to log in from an unapproved location, CBAC sets up rules to automatically restrict them from accessing the app or deny their access requests instantly.
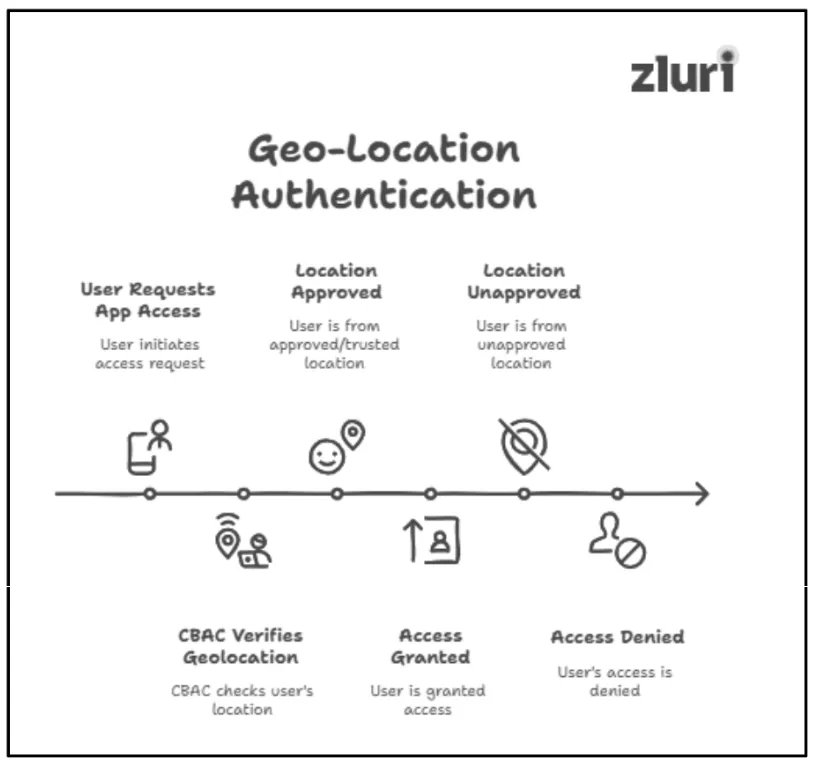
Note: Organizations maintain a record of all the restricted geolocations/regions (users can operate from these locations) and the reasons behind the restrictions. Context based access control typically uses these records to match and verify the user's geolocation.
3: Device Based Access
Before making the access decision (whether to grant or deny a user access request), CBAC also evaluates the specifications of devices that users use to connect to the system or application. These specifications include — device type (laptop, smartphone), operating system (Windows, Linux, macOS), device unique identifier (ID), and device security status (as in whether the device has updated security patches or meets encryption standards or not).
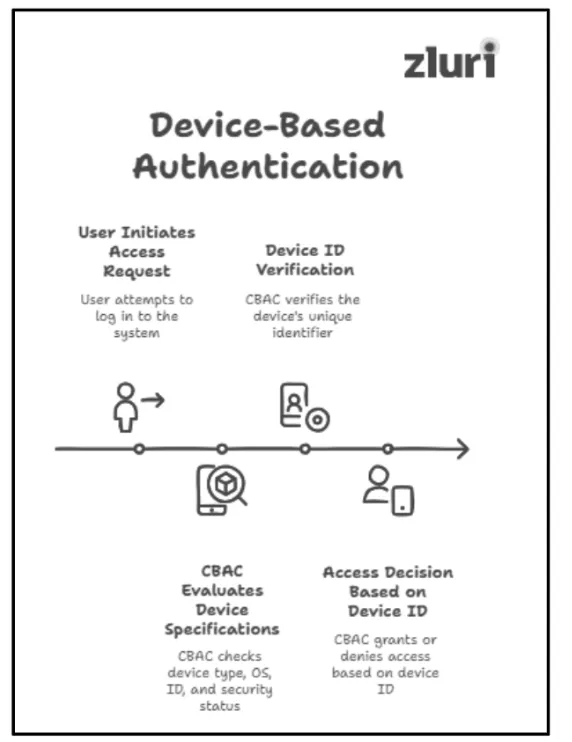
For example, if the user is using a device with an unfamiliar/non-verified unique identifier (ID), then CASB will deny the access request regardless of whether the user's identity is verified. Basically, CBAC works by going beyond just verifying who's logging in; it also checks what they are logging in with.
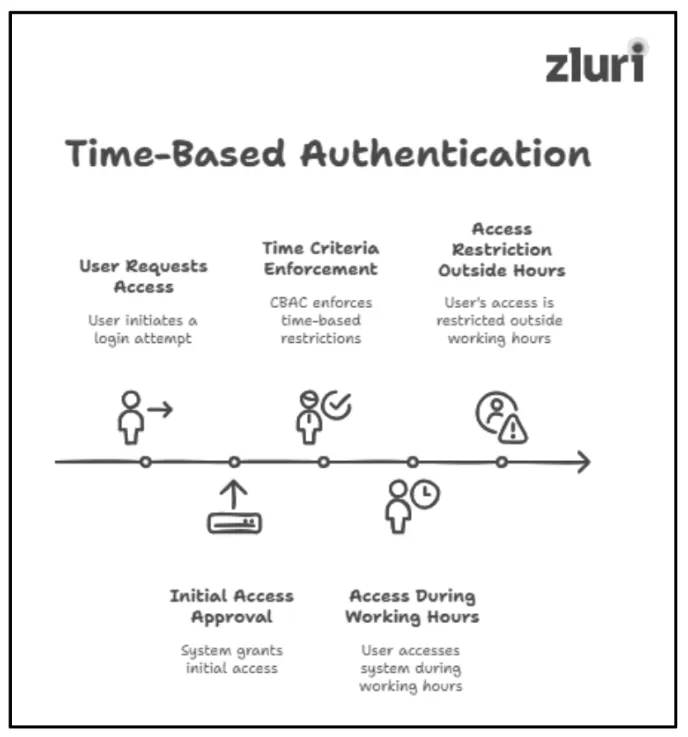
4: Time Based Access
Upon initial access approval (just approval to enter/log into the systems or apps), CBAC further enforces pre-defined time criteria restrictions, which means — users will only be allowed to access the application/system for a specific period of time.
For example, CBAC typically enforces rules that allow users to access office applications/systems only during standard working hours. Outside of these hours, access is automatically restricted — users will not be authorized to log in.
Also Read: What Are Time Based Access Controls? How To Implement Them?
The next section lists some context based access control examples to clarify how these controls work in different scenarios.
Context Based Access Control Examples
Mentioned below are two common examples of context based access control:
Example 1: Trying To Access the Organization's Internal Network From A New Geographic Location
Suppose you went on a business trip abroad (XYZ location), and there you tried to access your organization's internal network from a local restaurant. However, your network access request was continuously denied by your organization's network control system.
Why do you think this may have happened? It's because your organization may have implemented geo-location access restrictions to keep its application, system, and sensitive data safe. Since your XYZ location fell under a restricted area (defined by the organization), the network control system (configured as per CBAC to do so) may have automatically denied your login attempt for security reasons.
Example 2: Using A New Device To Access Company's File
Let's say, you usually use your laptop to access sensitive company files. However, due to some technical issue in your laptop, you tried to access this same file through your mobile phone (a device you have never used for this purpose before).
However, upon attempting to access the file from an unregistered device (mobile phone), your access was denied. Why did it happen? It happened because CBAC (which your organization has implemented) detected the change in your device and automatically denied access requests made by your unregistered devices.
Now you may say — 'The user may have used an authorized ID and correct password; won't CBAC consider that?' Well, CBAC doesn't solely rely on login credentials/ identity details. Rather, it considers multiple context factors for validation/authentication purposes, and in this case, it considers both the authorized ID of the user and the device they use. Since the device did not meet the CBAC device access guidelines, it simply restricted or denied access to the file. Basically, context based access control treats every unfamiliar device, location, and IP address as a potential threat that can compromise data security; that's why it takes such strict measures.
Benefits Of Context Based Access Control
Listed below are the two main benefits of context based access control:
1: Creates A Multi-Layered Defense Setup To Protect Organization’s Applications, System, & Datasets From Internal & External Threats
As discussed earlier (briefly), unlike other access controls (role-based access control, just in time access control, or least privilege access control), CBAC doesn't solely rely on one specific condition to restrict access to authorized users. Rather, it evaluates various context based factors to manage user access and keep the app, systems, and datasets secure from external and internal threats, such as:
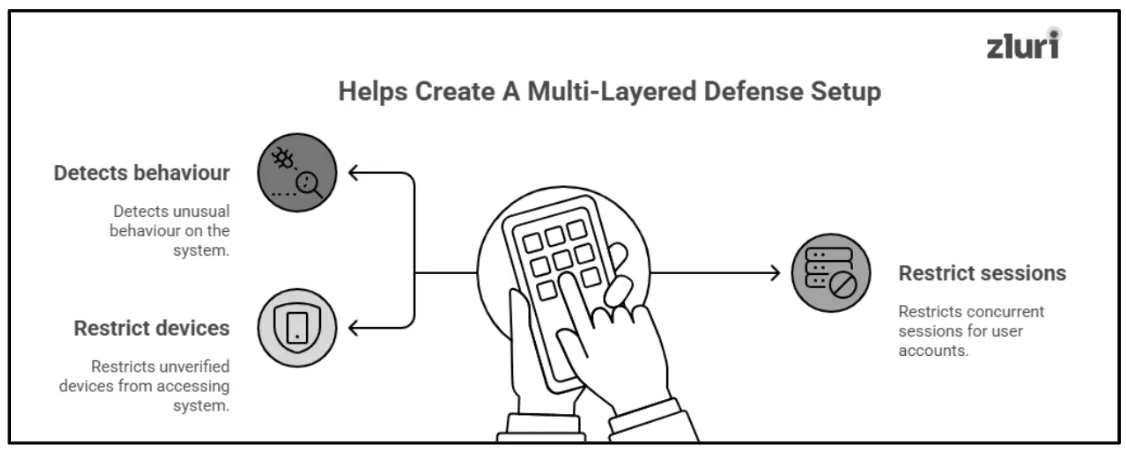
- Detects Unusual Behaviour
Generally, cybercriminals target user credentials or user identities to comprise organization devices, apps, and systems. In fact, they frequently change their access points, which makes it harder for IT teams, security teams, or intrusion detection systems to spot them. By performing these actions, attackers easily slip past defenses, gain access to the system, and comprise the organization's sensitive data.
However, CBAC creates a barrier between your sensitive data and attackers or unauthorized users and protects it from being compromised. It analyzes contextual data such as IP addresses and device information, identifies unusual behavioral patterns, and detects attackers or unauthorized users. If it finds any anomalies or suspicious behavior, it instantly blocks or restricts access in real-time (stopping the attacks before they become a major issue).
- Restrict Concurrent Sessions
CBAC also enforces session controls to ensure each user can only log in on one device at a time (i.e., allowing only one active session per user at a time). For example, if a malicious actor tries to gain access to the system using the same credential while the legitimate user is already logged in, the system will automatically block or deny the extra/second login attempt. This way, CBAC ensures only one authorized user and device is connected at a time – and no one else can gain entry to the system during this time, be it malicious actors or unauthorized users.
- Restricts Unverified Devices From Accessing the Organization's System And Applications
In fact, to prevent hackers from compromising remote users' identities and access, CBAC enforces device-based access control. In this practice, CBAC mandates that remote users/employees solely use company-owned or compliant devices to access the organization's data, systems, and apps.
Let's say that even if the hacker gets the remote worker's identity and access permissions, they will use their device to access the systems and apps. Since these devices are unregistered, they will be locked out immediately due to device-based access control.
Also Read: How IT Teams Can Prevent Insider Threats in Organization
2: Help Comply With Compliance Regulations Or Industry Security Standards

By restricting sensitive app/system (that stores sensitive data) access to solely authorized users (that meet the predefined context rules), CBAC helps keep data protected against unauthorized users and cyber criminals. This proactive practice/measures further helps organizations seamlessly meet compliance regulations like HIPPA, GDPR, PCI DSS, ISO 27001, SOC 2, and other compliance regulations that mandate to maintain security, confidentiality, and privacy of sensitive data.
Now that you are familiar with the benefits of context based access control, let’s understand how you can implement this control within your organization.
Leverage Access Management Solution To Implement Context Based Access Control
To enforce context based access control (or any other control for that matter) —
- You either have to configure your systems/applications (change the system/app general settings or modify the system/app code script) so that they support CBAC rules directly.
- Or have to define policies that validate contextual factors before granting access approval.
Depending on your specific requirements, you can implement one method or even combine both to create a more threat-resilient security setup—the decision is entirely in your hands!
Note: Below, we’re not going to dive into the specifics of what needs to be incorporated into a CBAC policy because every organization has a unique structure and distinct security requirements. Due to these differences, the approach to defining and implementing the policy will vary. Therefore, we've left it up to you to decide what should be included in your policies!
Now you may ask — ‘How exactly can an application help enforce context based access control?’
To demonstrate how apps help enforce controls, below, we’ve taken Zluri’s access management solution as an example and explained how it helps implement access controls like CBAC in detail.
Zluri offers an access management solution that helps seamlessly implement context based access control with just a few clicks. Here’s how it works: Zluri’s access management provides an automation workflow in which your IT team can outline the rules of context based access control. Based on the defined rules, it automatically enforces them across your organization’s apps, systems, and users.
Suppose, your organization is based in India, and you want to ensure that only users (users that are working for your organization) located in India can access your apps. So, what you can do is – specify these context-driven triggers/rules in Zluri’s automated workflow as below:
Once the configuration is completed, whenever users request app access, Zluri’s access management will automatically check their context—their geographic location (user’s IP address/geolocation)—against the rules you’ve defined.
If the conditions are met, that means if the user who is requesting app access is based in India and not Bangladesh, then access will instantly be granted. If the user doesn’t meet the conditions, Zluri’s access management solution will automatically deny access by default.
This way, you can ensure that only authorized users—those meeting your predefined contextual rules—can access your critical applications, systems, and databases.
Note: While creating onboarding workflows, Zluri’s access management also offers contextual app recommendations. This feature auto-suggests what apps can be suitable for your new hires by evaluating your user’s profile (role, designation, or position), making it easier to grant users access to relevant apps.
Take Control Over Who Can Access What Within Your Organization With Context Based Access Control
Context based access control strictly follows the zero-trust security model, i.e., never trust, always verify. That’s why it leaves no room for assumption. It thoroughly verifies the context of each access request (request raised by users)—be it the user’s location, the device they are using, or the time of the request—before granting the final approval (access is granted only when conditions are met). In short, it does not trust any individual by default!
In fact, it treats every request with utmost caution and care, ensuring your systems and applications remain unbreakable at all times. By implementing CBAC, you as an organization can gain complete control over who can access what and under what circumstances. So, if you want this level of security and control, don’t wait—implement context based access control today!
Frequently Asked Questions (FAQs)
1. What Is The Difference Between Context Based Access Control & Attribute Based Access Control?
Context based access control focuses on evaluating contextual parameters like a user's geolocation, the device type they use, their IP address, and other factors before granting them access to requested applications. Meanwhile, ABAC evaluates predefined attributes like a user's role, department, seniority, and unique ID before granting them access to apps and systems.
2. Can CBAC Be Used For Both On-Premise And Cloud Environments?
Yes! CBAC works effectively in any environment – on-premise, cloud, or hybrid environment.
3. Can I use CBAC to control seasonal contractors'/freelancers' access?
Yes, you can! CBAC enforces time-based access control that allows you to seamlessly manage seasonal contractors/freelancers' access. It basically grants seasonal workers a restricted time window—as in, 2-3 months (you can customize the duration)—to access the applications they need to perform their tasks. Once this time frame expires, access will automatically be revoked, which will further help keep your data secure from unauthorized access attempts.








.svg)














