To effectively govern identities, you need to look beyond static identity attributes. You have to take contextual insights into account alongside. What are contextual risk insights? What role does it play in identity governance? In this article, we’ll discuss about it in detail.
Most access reviews still rely on static identity data: job titles, departments, and roles.
But that tells you only who the user is on paper, not how they're actually using their access.
And without that context, you end up:
- Keeping inactive users in your system.
- Leaving dormant or inactive accounts with elevated permissions staying active.
- Paying for licenses that no one is using.
- Submitting access review reports that are incomplete and unreliable for audits.
This is where contextual risk insights can make all the difference.
They add depth to identity data by showing how, when, and whether an access is being used, so you're no longer making decisions on assumptions.
In this article, you'll learn:
- What contextual risk insights actually look like
- How they help you make better and risk-aware governance decisions
Take Contextual Risk Insights Into Account For Better Identity Governance
What are Contextual risk insights? Contextual risk insights are basically the dynamic data points that reflect real-time user behavior/app usage patterns and identity-related risk indicators. They help your team gain clarity regarding ‘how’, ‘when’, and ‘where’ access is being used in a given moment or over time.
Which Data-Points Are Included In Contextual Risk Insights?
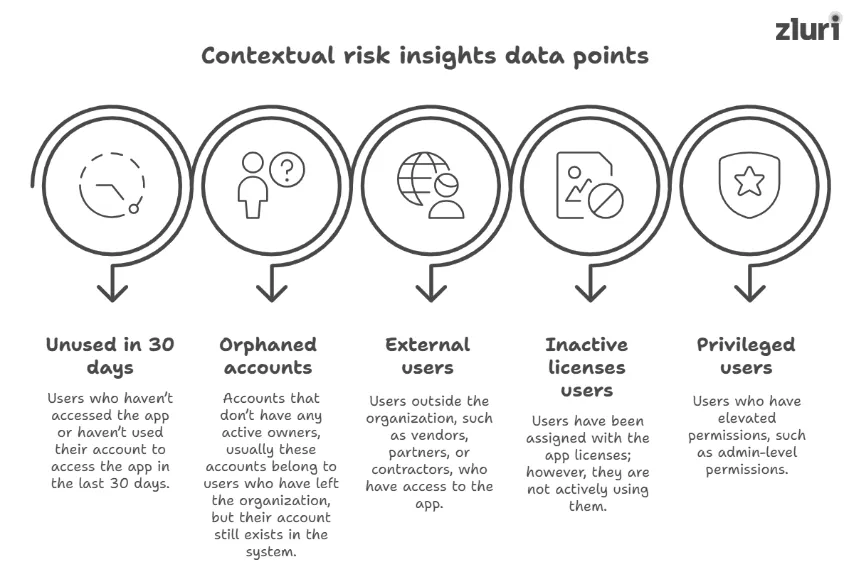
How Contextual Risk Insights Help Improve Access Decisions?
By taking contextual risk insights into account along with static data, your reviewers can make more informed access review decisions (whether to approve access, modify it, or revoke it).
Moreover, to make sure ‘the right user has access to the right applications at the right time’, it is important to understand the real-context behind the access - who’s using what, how often, and why.
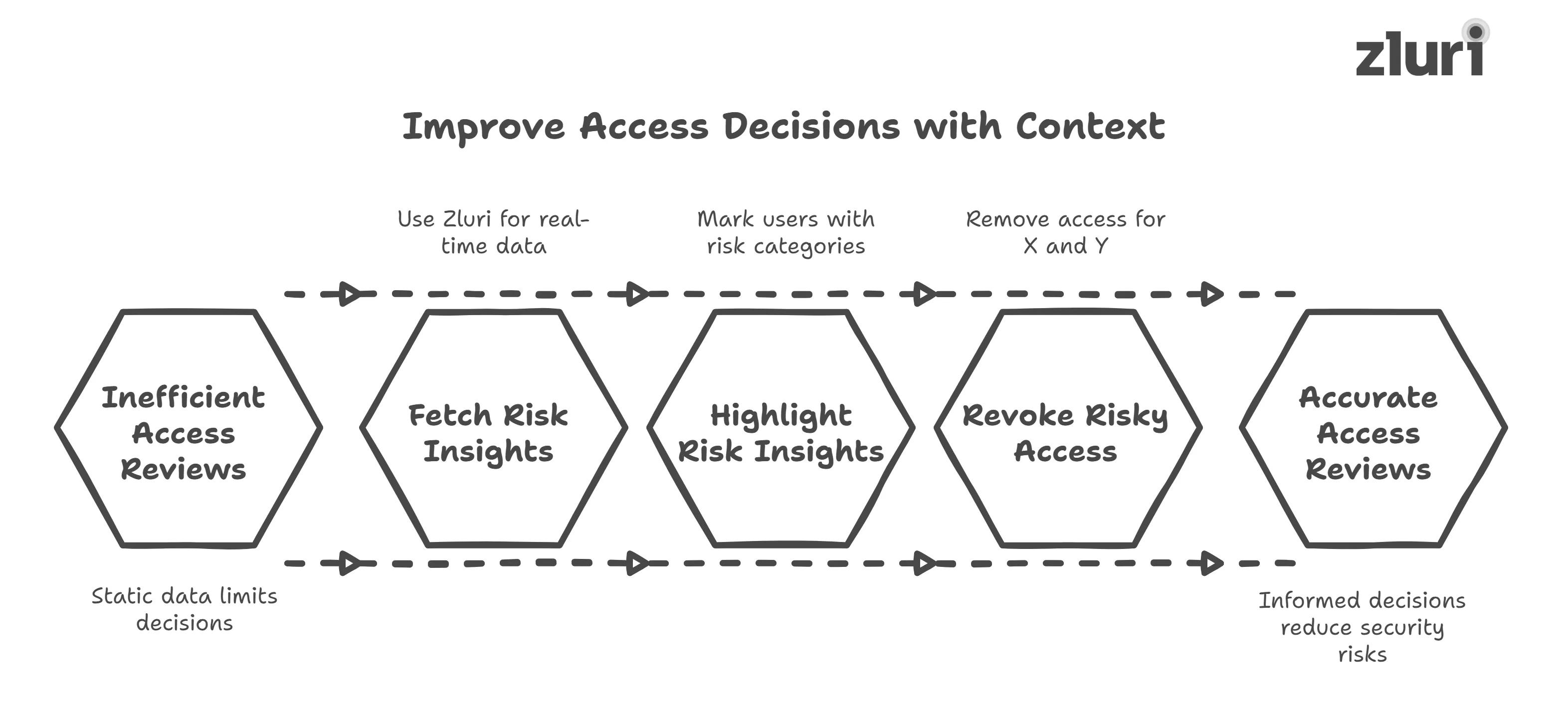
Let’s suppose, you have three external users – ‘X’, ‘Y’, and ‘Z’ – each with access to a SaaS application.
- User X hasn’t logged into the app in over 30 days.
- User Y has admin access to an app that’s not even relevant to their roles and responsibilities.
- User Z is using the right app appropriately.
Now, if you were only relying on static data like role or department to review the external users' access, you’d probably let all three keep their access.
However, when you consider contextual risk insights – you will view things differently, which will influence your access review decisions. Just like in this case.
Note: We’re using Zluri to fetch contextual risk insights because it's faster and delivers real-time, accurate, and complete data.
Zluri will highlight all the contextual risk insights in the review dashboard.

- It will mark ‘X’, ‘Y’, and ‘Z’ as external employees.
- It will put ‘X’ under unused in the 30 days contextual risk insights category.
- And it will put ‘Y’ under the privileged users category.
Now, since inactive users and external users with admin privileges shouldn’t retain app access, because they can introduce security risks. You, as a reviewer, can without any doubt revoke access for X and Y, and confidently allow Z to retain access since it’s justified and poses no risk.
Just like that, by performing a single review, you closed two potential access gaps and made your access review report more accurate, reliable, and audit-ready.
That’s not all, you can even use contextual risk insights for Joiner Leaver Mover Events. How? Here’s how.
Additional Use Cases Of Contextual Risk Insights
Below, we’ve given a few examples where you can use contextual data.
1. Joiner’s Event
Rather than granting new joiners application access solely based on their role and department, you add contextual conditions to grant more precise and relevant app access.
For example, you want to ensure that a new joiner in the marketing department receives basic-level access to marketing apps only if they are an intern and they are logging in from a specific laptop serial ID address - SN:202XXXX (example of contextual condition).
For that, you can specify the following in Zluri's onboarding automation rule workflow.
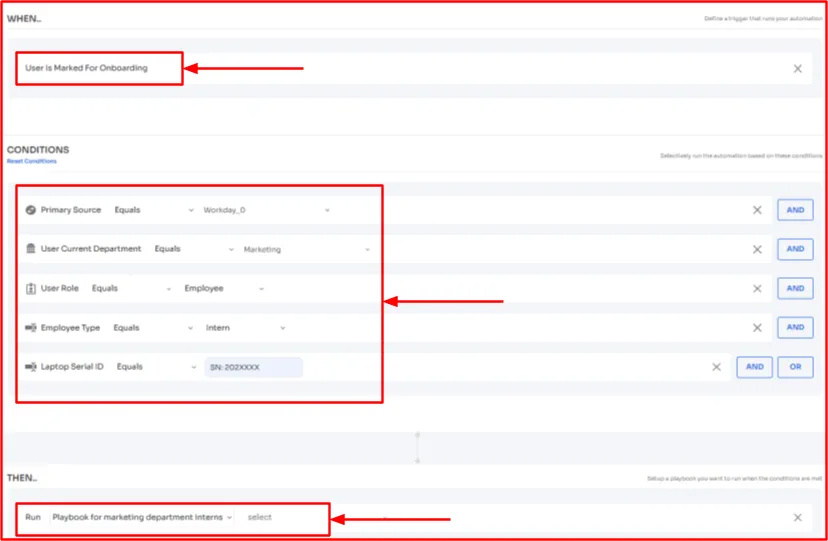
Once the static and contextual conditions are met, Zluri will automatically grant the marketing department new interns access to marketing tools.
2. Mover’s Event
Access permissions shouldn’t only be adjusted/modified when a user transitions to a new role or department. They should be updated when there is change in geographical location as well (as in the user move to a new region).
Moreover, as remote and hybrid work culture continues to grow – teams can no longer just rely on role and responsibilities to grant access; they have to consider where the user is operating as well (it’s equally important).
By taking such contextual conditions into account (geographical locations), your team can control how identities interact with your applications – no matter where they are currently working from. This way, you can prevent access from risky or untrusted locations.
- Let's say you want to ensure that users who have switched to the finance department can access financial applications only if they are working from approved regions such as India or the United States. If someone tries to access these apps from untrusted locations like Bangladesh or Myanmar, they shouldn’t be allowed to log in/access the financial applications.
So, for that, what you can do is specify the following in Zluri’s automation rule workflow.
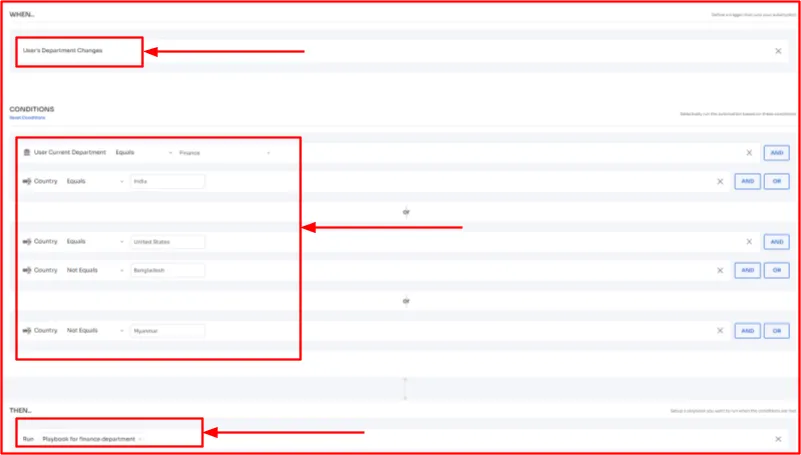
Once the conditions are satisfied, Zluri will automatically grant finance apps access to users who have recently moved to the finance department and are operating from approved regions.
3. Leaver’s Event
You shouldn’t only revoke access when a user leaves the organization. You should also take action when a user's status is marked as inactive – if they haven't logged into an application for an extended period. This way, you can prevent access from lingering.
- Let’s suppose, you want to ensure that users from the sales department who are on an extended leave, such as a sabbatical, have their access revoked for the duration of their absence.
So, for that, you can specify the following conditions in Zluri's offboarding automation workflow.
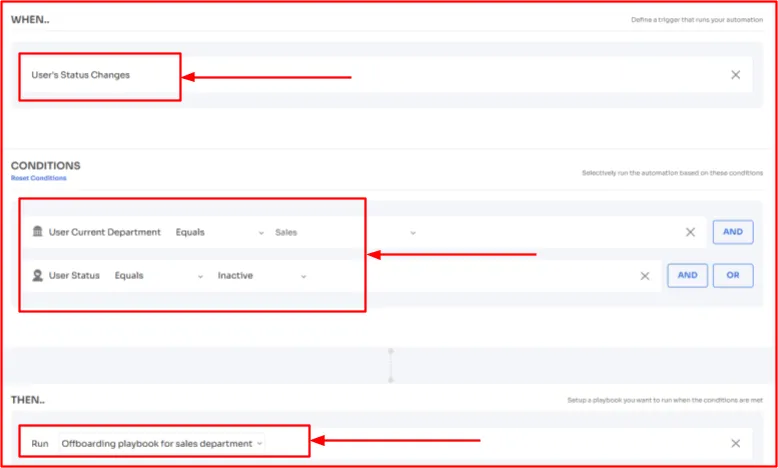
Once the conditions are met, Zluri will automatically revoke access to sales applications for inactive users in the sales department.
Pair Static Data with Context to Eliminate Access Gaps
In today’s dynamic and complex IT environment, relying solely on static data won’t be enough. To effectively govern identities and manage access, you need to pair it with contextual risk insights that reveal how access is being used, by whom, and from where.
By blending both static and contextual data, you get complete visibility (a whole picture) into your access environment. With this visibility, your team will be able to make more effective access decisions and will be able to prevent the creation of access gaps.








.svg)














