You have secured your perimeter, added MFA, and adopted zero-trust principles — but somehow, identity remains the weakest link.
Why? Because most identity systems are built on the assumption that user context doesn’t change between logins. Once access is granted, it often stays regardless of how the user’s role, location, risk posture, or responsibilities evolve. And this outdated assumption is exactly what attackers exploit.
In today’s environment, where users shift roles, join new teams, use dozens of SaaS apps, or exit quietly without revocation, static access management creates invisible gaps. You might pass audits. But beneath the surface, you’re left with dormant access, excessive entitlements, and blind spots you can’t afford.
Security isn’t just about strong controls–it’s about timely and adaptive controls. And if your access decisions are based on who someone was last quarter instead of who they’re right now, they’re not managing risk — you’re just delaying it.
This is where continuous identity management comes in. It’s a shift in how you secure access across a constantly changing environment. In this article, you’ll learn why static approaches fall short, what “continuous” actually means in practice, and how teams are reimagining identity management to match the speed of their business.
The Flawed Foundation: Traditional IAM Assumed a Static World

If you trace how the identity systems function, you’ll see the same pattern:
- Access is provisioned when someone joins.
- Maybe it’s updated during an annual access review.
- And finally, it’s revoked when they leave (assuming the offboarding process catches everything).
On paper, this looks fine. In reality, it leaves you with months, sometimes years, of overexposed access.
Here’s why:
- Access piles up: Users accumulate access over time, but no one systematically removes what they no longer need.
- Reviews are infrequent: Quarterly or annual certifications give a snapshot, not an ongoing picture of risk.
- Organizational charts move faster than policies: Job changes, department shifts, and project-based roles occur instantly, but your IAM system often takes weeks or months to reflect these changes.
This static approach assumes your environment changes slowly and predictably. However, in a SaaS-first, hybrid, and contractor-heavy world, identity context changes daily. And every delay between a change in context and a change in access is an attack surface.
That’s why orphaned accounts, excessive privileges, and “access creep” aren’t outliers–they’re the inevitable outcome of a model that treats identity like a one-time setup, not a living asset.
The Modern Reality: Identity Context Shifts by the Minute
.png)
Your users aren’t static, and neither is their risk profile.
In a modern environment, access needs can change in hours, not months.
- SaaS adoption is rapid: New apps are onboarded by teams without the knowledge of IT teams, creating shadow access that can’t be tracked.
- Roles evolve instantly: An engineer might be promoted, a sales representative might move to a different region, or a contractor might switch projects mid-week.
- Hybrid work reshapes context: A user logging in from the office at 9 a.m. poses a different risk than the same user connecting from a personal device at 11 p.m. in another country.
The problem? Most identity systems react on a schedule, not in real time. By the time your quarterly review catches a risk, that risk may have already been exploited or have multiplied across multiple systems.
Attackers know this. They exploit the lag between context changes and access changes:
- A departing employee’s credentials remain valid for days after office hours.
- Privileges granted for a one-time project never get revoked.
- Service accounts with unused permissions stay untouched for months, waiting to be misused.
When change happens faster than your controls can adapt, you’re running with yesterday’s security model. And that doesn’t stop today’s threats.
What does Continuous Identity Management Actually Look Like?
Continuous identity management isn’t about running reviews more often; it’s about making identity governance event-driven, context-aware, and self-correcting.
Instead of relying on fixed schedules, access decisions are updated as soon as something changes that could impact risk. That means:
- Real-time identity signals: You’re not just looking at usernames and roles; you’re also factoring in device trust, location, login behavior, and app usage patterns.
- Event-based triggers: A role change, project reassignment, contractor’s contract ending, or even suspicious login activity can automatically kick off an access review or remediation workflow.
- Dynamic policy enforcement: Access policies update themselves in response to the current risk context. For example, a finance app might require additional verification if accessed from outside the corporate network.
- Automated remediation: If a user’s context changes, their access can be right-sized or revoked instantly, without waiting for a helpdesk ticket or quarterly certification cycle.
This approach transforms identity from a static record into a live, continuously validated trust layer. You’re no longer relying on people to spot outdated access; the system adjusts it proactively.
Key Pillars of Continuous Identity
Shifting to continuous identity management isn’t just about turning on a new tool; it’s about building a framework that ensures access stays aligned with real-time context.
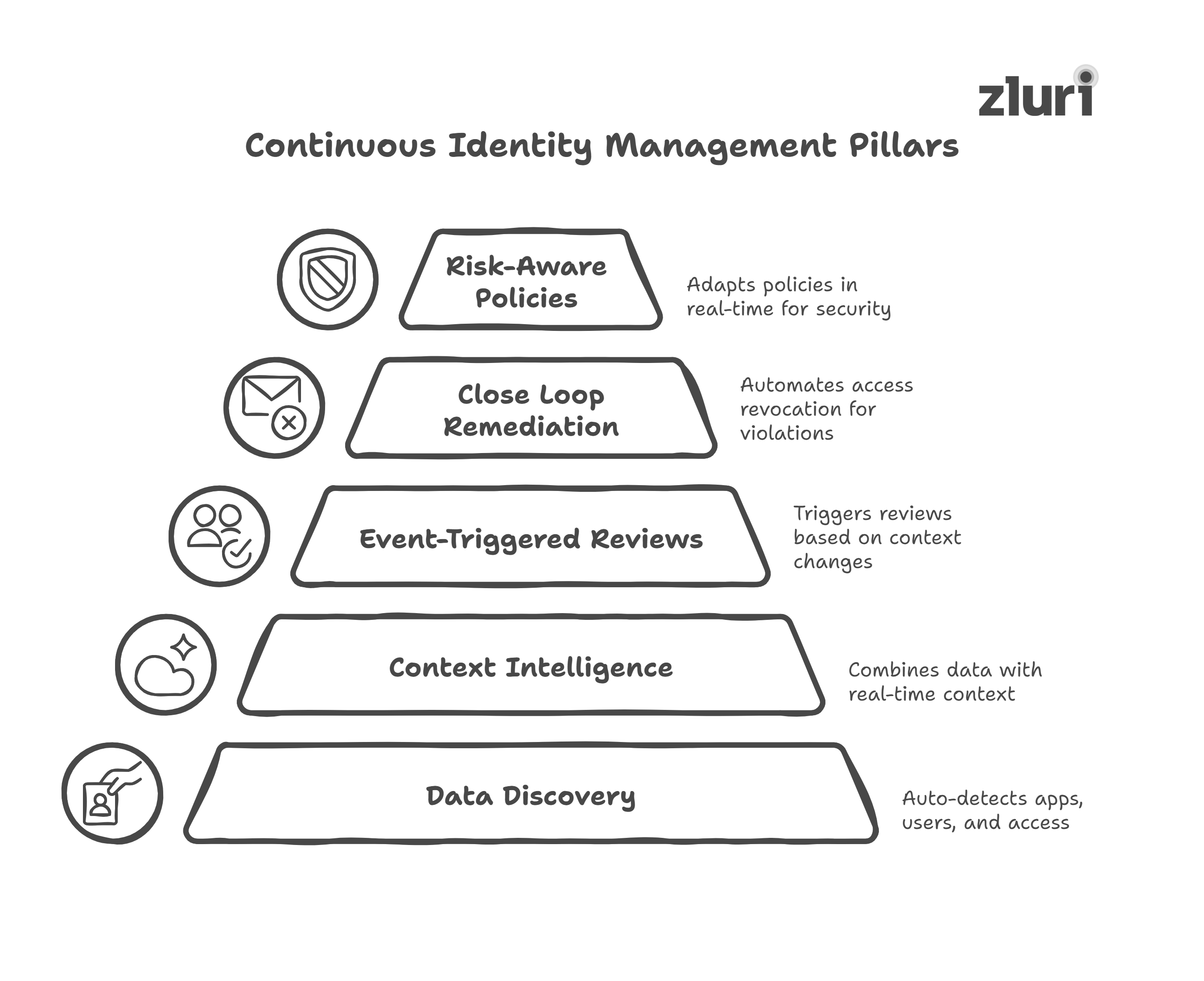
Here are the core pillars that make it work:
- Complete data discovery: Auto detects every app, user, & access
You can’t secure what you can’t see
- Auto-discover every app, user, role, and non-human identity across your environment.
- Identify shadow IT and unapproved integrations before they become security gaps.
- Maintain an always-updated inventory so your access decisions are based on today’s reality, not last year’s spreadsheet.
- Context access intelligence
Access should reflect the user's current identity.
- Combine identity data with HR, device, and behavioral context to understand actual risk.
- Detect when a user’s access no longer matches their job role or risk posture.
- Make decisions based on role, department, location, and current activity — not static profiles.
- Trigger reviews based on events (role or department change), not calendars
Move away from calendar-based reviews.
- Trigger reviews when context changes, not just at fixed intervals.
- Request justifications for sensitive access in real-time.
- Keep review fatigue low by surfacing only access that’s risky, unused, or outside policy.
- Close-loop remediation
Risk without action is still risk.
- Automate access revocation or right-sizing immediately after policy violations or changes in context.
- Eliminate the ticket queue bottleneck–issues are resolved in minutes, not weeks.
- Ensure no risk lingers between detection and action.
- Risk-aware access policies
Policies that adapt in real time strengthen security without slowing productivity.
- Apply adaptive controls, such as step-up authentication, based on the sensitivity of the resource and the current risk score.
- Auto-adjust permissions based on device trust, location, and active role.
- Reduce overprovisioning with access that expires unless actively renewed.
These pillars, together, form a self-correcting identity ecosystem — one that continuously aligns access with evolving business needs and risks. It’s proactive, not reactive. And in today’s environment, that’s the difference between staying ahead of threats or reacting to them after knowing.
Benefits: Why Continuous=More Secure & Efficient
Continuous identity management isn’t just a security upgrade; it’s a way to reduce risk and make operators seamless.

- Eliminates lateral movement opportunities: Access is corrected the moment roles or contexts change, leaving attackers with fewer paths to move undetected inside your environment.
- Reduces audit fatigue & review overhead: Reviewers focus only on risky, unused, or non-compliant access, instead of wading through thousands of low-value entries.
- Prevents access creep: Permissions don’t accumulate over time; unused or outdated access is automatically removed before it becomes a liability.
- Strengthens zero-trust posture: Trust decisions are continuously validated, making your zero-trust model actually live up to its name.
- Frees up IT teams: Automated remediation eliminates weeks of manual deprovisioning and ticket handling, letting teams focus on strategic initiatives instead of access cleanup.
With these gains, continuous identity management isn’t just about plugging security gaps; it’s about running a cleaner, faster, and more resilient identity program that scales with your business.
From Vision to Execution: Moving Towards Continuous IAM with Zluri
Even with strong governance policies, the reality is that most legacy IGA setups are slow, reactive, and ill-equipped for today’s SaaS-driven identity sprawl. Reviews take months, orphaned accounts slip through, and by the time risky access is flagged, it’s often too late. What’s needed is not just “another tool,” but an IGA platform that can operate as your real-time control center–continuous monitoring, flagging, and fixing access issues before they become breaches.
This is where Zluri’s identity-first IGA stands out. Unlike traditional solutions that focus only on static reviews, Zluri is built to:
- Continuously discover & monitor SaaS usage, so you always have an accurate, real-time context of who has access to what, including unsanctioned (shadow IT) apps.
- Automate access reviews with risk context–by prioritizing accounts with high-risk permissions or anomalous activity, you don’t just review faster; you review smarter.
- Enable closed-loop remediation – revoke or modify access directly from the review interface, eliminating the need for manual IT ticketing and reducing resolution time from weeks to minutes.
- Scale across cloud-first environments with over 300 direct SaaS integrations, Zluri avoids the connector gaps that slow down other platforms.
- Stay audit-ready by default with a complete, exportable history of access changes, reviews, and approvals, satisfying compliance frameworks such as SOX, ISO 27001, and HIPAA, without last-minute rushes.
With Zluri, you shift from periodic, compliance-driven revocations to continuous identity governance. That’s a major change–moving access control from being a defensive necessity to becoming an active enabler of security, productivity, and trust.
Security 2.0: What ‘Good Enough’ Looks Like Now
The era when identity could be treated as a static record is over. Attack surfaces now expand and contract in real time–and so must your governance.
The real shift isn’t just technological. Continuous identity management compels you to stop thinking in terms of “grant and forget” and start treating access as a crucial asset. That mindset change does more than protect against threats – it fundamentally changes how trust operates within your organization.
The organizations that will thrive aren’t the ones with the longest list of controls–they’re the ones with controls that function. If your identity governance can’t adapt as quickly as your environment changes, it’s not just outdated; it’s also part of the risk.
The future of identity isn’t a product you buy or a project you complete. It’s a capability you sustain. And the sooner you make that shit, the sooner you close the gap between “secure” on paper and secure in reality.









.svg)














