Hackers and other malicious actors often target users, as they are the ones who access the organization’s digital assets. This makes them a potential entry point to infiltrate systems and gain unauthorized access to sensitive SaaS app data.
This is why it is crucial to deploy a user access management (UAM) tool to securely and effectively manage user access. In this blog, we’ll explore some well-known user access management tools designed to simplify the user access management process.
Before we explore the user access management platform, let's first understand why user access management tools are required and what benefits you can avail from them.
Why Do You Need User Access Management Tools?
User access management tools help your IT team simplify and automate user access management processes, such as granting, modifying, revoking access, and more. Further, it enables your team to manage and control who possesses access to all the organization's SaaS applications, data, critical systems, and networks. This helps adhere to security compliance regulatory standards and safeguard crucial data from cyber threats.
What Are the Key Benefits of User Access Management Tools?
By deploying an effective user access management platform, your team can attain the following benefits:
- Provides Proper Visibility: User access management tools offer your IT team complete visibility into who has access to what. This further helps in effectively managing and controlling user access and reduces the risk of data breaches and unauthorized access.
- Helps Adhere To Compliance Regulatory Standards: User access management systems help your IT team/GRC team meet internal policies, industry standards, and regulatory requirements. This helps organizations meet legal obligations and builds trust among stakeholders, showcasing the organization's commitment to safeguarding data.
- Enables To Efficiently Allocate Resources: UAM tools enable your IT team to grant employees access to resources that are necessary for them to perform their tasks. This promotes efficiency and resource optimization.
- Reduces SaaS Wastage: UAM tools offer a centralized platform for managing access across the organization. This centralization prevents resource wastage and helps control costs.
Now that you know what a user access management tool does and its benefits, let's dive deeper and discover some of the well-known advanced UAM software available in the market.
Here’re The Top 11 User Access Management Tools
Listed below are the 11 user access management tools that will help your IT team manage, control, and govern user access seamlessly.
1. Zluri
Zluri is an advanced SaaS management platform that enables your IT team to strike a balance between user ease and data security. It seamlessly connects users to applications, data, and devices/systems that are necessary for their work while ensuring that only the right individual gains access to the right apps with an appropriate level of permissions at the right time.
Furthermore, it automates and simplifies user access management processes such as provisioning, deprovisioning, access request management, and more. This not only helps in improving your IT efficiency but also significantly enhances the overall user experience by eliminating unnecessary wait times and bottlenecks.
Zluri is not restricted to this only. It further offers a wide range of functionalities that help your IT team seamlessly manage employee access in an organization:
- Zluri Enables Your IT Team To Accurately Assign Roles To Users Upon Onboarding
Previously, IT teams have relied on manual procedures to verify the identities of new users and then ultimately allocate them specific roles. Unfortunately, this approach was not only time-intensive but also susceptible to human errors, occasionally resulting in misalignment of user roles.
To prevent such situations, Zluri takes a proactive approach during the onboarding of new employees. It automatically links their profile with digital identity, which helps your IT team to easily cross-verify their identities and then assign them appropriate roles. Further, by doing so, your team can seamlessly grant new employees access and permissions necessary to perform their jobs.
- Manages User Access to SaaS Applications Effectively
Zluri integrates with your organization's HR system, ensuring your IT team has access to the most updated employee data. With the help of this integration, Zluri automatically retrieves and presents all employee information on a centralized dashboard.
This further helps your IT team to grant and modify access efficiently, ensuring employees have the right access to all the required apps from day one and get timely access upon their role change. By doing so, your team can improve employee experience and increase their productivity. Also, Zluri enables your IT team to revoke access when employees leave the organization, which helps prevent potential security breaches.
- Enables Your IT Team To Grant Users Access To Only What Is Essential
Zluri helps your IT team grant users access to apps, data, and other digital assets that are essential for their job. To maintain this access control, it helps your team implement different access control policies such as role-based access control (RBAC), the principle of least privilege access (PoPL), segregation of duties (SoD), and just-in-time access.
- By implementing role-based access control, Zluri enables your IT team to ensure the access rights align with the user's roles and responsibilities.
- By enforcingthe segregation of duty policy, Zluri enables your IT team to ensure no two individuals are responsible for completing one task.
- By enforcing the principle of least privilege, Zluri enables your IT team to ensure minimum access privileges/permissions should be granted to employees to avoid over-provisioning or granting excessive privileges.
- By implementing just-in-time access, Zluri securely enables your IT team to grant employees temporary conditional access or just-in-time access to required apps for a specific duration. This way, your team can reduce the attack surface caused by standing privileges.
- Zluri Regularly Monitors And Evaluates User Access
Zluri thoroughly documents who has access to what and keeps track of if anyone has more access than they require. If it finds any issues or violations, your IT team can promptly change the user's access permissions, ensuring only the right individual has the authorized level of access. This way, your IT team can reduce security breaches that may take place due to employees possessing excessive permissions.
It's not restricted to that only; further, Zluri also provides your IT team with real-time notifications on users attempting to access apps that are not authorized to access as per their role. This notification helps your team to take immediate action, like restricting or suspending user accounts if required, to maintain a secure access environment.

- Conducts Periodic Audits
Zluri conducts regular/periodic audits to ensure each user in the organization has the necessary level of access permissions to SaaS apps, data, and critical systems. If there is any misalignment/ mismanagement in their access rights, your IT team and reviewers can run deprovisioning playbooks or modify access playbooks. By doing so, your team can swiftly revoke access from users not necessary for their roles or modify the access.

Moreover, as per KuppingerCole’s analysis, Zluri’s automated access reviews reduce the time to audit readiness from months to weeks.
Furthermore, Zluri also documents the entire review process and generates audit logs and reports to show as proof/evidence to auditors that your IT team has enforced access control policy effectively without fail.
Furthermore, Zluri also documents the entire review process and generates audit logs and reports to show as proof/evidence to auditors that your IT team has enforced access control policy effectively without fail.

By doing so, you can meet stringent compliance regulatory standards such as GDPR and HIPAA, where data integrity is a crucial security requirement. This proactive approach aids in averting potential legal repercussions and financial penalties linked to non-compliance. Also, you can avoid getting into trouble and having to pay fines.
Now that you know the benefits offered by Zluri, why not book a demo and experience it firsthand? See how this game-changing solution can be a perfect fit for your IT team's needs.
Features
- Zluri conducts periodic access reviews to keep track of the access process. If any user activity violates the set access policies, Zluri instantly initiates auto-remediation actions, such as it runs a deprovisioning playbook to revoke access if users' access does not meet the access criteria or modify access with the reviewer's intervention.
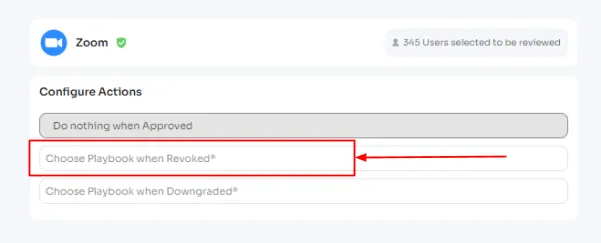
- Zluri offers your IT team with a centralized dashboard to monitor and analyze which user has access to which specific SaaS applications. This centralized visibility streamlines the access management process, eliminating the need to go through multiple screens back and forth to gather user and app data, saving your team's time and enhancing their efficiency
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
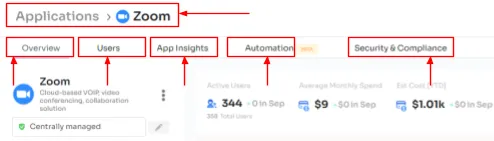
Customer Rating
- G2: 4.8/5
- Capterra: 4.9/5
2. Okta
Okta Workforce Identity Cloud, a notable user access management tool, offers a comprehensive solution to simplify and secure access for your workforce, allowing you to focus on strategic priorities such as cost reduction and enhancing customer service. By embracing an identity-first security approach, your team can protect your employees, safeguard your data, and accelerate your business in today's ever-changing work environment.
This solution empowers everyone within your organization, including employees, contractors, and more, enabling them to work effortlessly and securely from any device and location. With identity-powered security as the foundation of your business strategy, your team no longer needs to compromise between delivering an excellent user experience and ensuring the safety of your users.
Furthermore, it seamlessly integrates identity across your security stack with features like FastPass, Okta's Risk Engine, directory integrations, and workflows. By doing so, you can free up your technical teams from the daily tasks that often hinder productivity, allowing them to focus on more significant business initiatives.
Also, your team can attain efficiency and improve their productivity with features such as User Lifecycle Management, low and no-code automation via Okta Workflows, and a unified Identity access and governance solution. By centralizing and streamlining these processes, your team can enhance overall business performance.
Features
- Okta Workforce Identity Cloud enables access for everyone while ensuring that access is granted to the right individuals at the right time. This is achieved through secure, passwordless authentication methods and features like FastPass, device assurance, multi-factor authentication, and privileged access, providing a seamless user experience for your entire workforce from their first day to their last
- Okta improves security through its advanced verification process, which involves double- or triple-verifying the identification of employees before granting access. This stringent verification procedure significantly reduces the risk of cyberattacks and unauthorized access attempts, safeguarding your organization's digital assets and sensitive data
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
3. SailPoint IdentityIQ
SailPoint IdentityIQ, a notable user access management tool, empowers your workforce by providing secure and compliant access to essential resources, ensuring they can work effectively anytime, anywhere. Through SailPoint, your team can swiftly provision access based on the policies you define, granting employees immediate access to resources (apps, critical systems, and data) necessary for their roles.
Additionally, it ensures just enough access delivery, so when new users join or their roles change, access is automatically granted, updated, or revoked, ensuring the right level of access at all times. This proactive security protects cloud-stored apps and data from potential cyber threats.
Also, your team can improve efficiency through SailPoint's automation capabilities, facilitating quick access provisioning while adhering to established policies. This streamlines the process, allowing employees access to what they need while adhering to compliance regulatory standards and security requirements.
Features
- SailPoint's 24/7 self-service feature provides users the flexibility to do common IT tasks independently, such as password resets and access requests, reducing the workload on IT teams and enabling them to focus on other core areas
- Also, it enables your IT team to onboard and offboard temporary workers automatically. Meanwhile, preventing excessive permissions that could pose security risks and eliminating the need for manual processes
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
4. Oracle Identity Management

Oracle Identity Management, a notable user access management tool, enables your IT admins to efficiently oversee and manage the entire life cycle of user identities, offering adaptable solutions that cover identity governance, access management, and directory services. Also, it supports your IT team in strengthening security measures and streamlining compliance obligations.
Additionally, Oracle Identity Management is an integral part of the Oracle Fusion Middleware product suite. It promotes agility, facilitates well-informed decision-making, and mitigates costs and risks across diverse IT environments.
Furthermore, Oracle Identity Management is a fully integrated service that delivers all fundamental identity and access management functionalities via a multi-tenant Cloud platform called Oracle Identity Cloud Service.
Features
- Oracle identity management enables your IT team to easily edit and migrate user data from one place to another, and further, with just a few clicks, they can access all the data. This streamlined process eliminates manual intervention, significantly enhancing your team's productivity.
Customer Rating
- G2: 3.7/5
- Capterra: 4.4/5
5. Microsoft Entra ID
Microsoft Entra ID (formerly Azure Active Directory) enables your IT team to strengthen the organization's security posture with its comprehensive cloud identity and access management solution. This solution connects employees, customers, and partners to their essential applications, devices, and data.
Also, it helps your IT team to enhance user productivity by offering a quick and hassle-free sign-in experience across your multi-cloud environment. It reduces the time spent managing passwords, allowing your workforce to focus on more valuable tasks and boosting overall productivity.
- Furthermore, Microsoft Entra ID manages all your identities and their access in a single location. This centralized approach enhances visibility and control, simplifying employee access management and reducing the risk of unauthorized access.
- Additionally, Microsoft Entra ID’s automation feature helps to automatically detect and remediate identity-based risks swiftly. This proactive approach helps mitigate potential security threats before they escalate, strengthening your organization's security posture.
Features
- Microsoft Entra ID uses adaptive authentication and risk-based adaptive access policies to safeguard critical resources and data. This ensures that access is granted to authorized individuals while preventing potential threats
- It also provides your employees the freedom to manage their identities securely through user-friendly self-service access request portals, including features like My Apps, My Access, My Account, and My Groups. This reduces the administrative burden on IT teams and enhances user experience
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
6. CyberArk
CyberArk Workforce Identity, a notable user access management tool, is the solution that provides your workforce with secure access to essential business resources. With CyberArk Workforce Identity, your team can balance security and user ease by providing your workforce with the necessary tools while keeping security threats at bay.
Furthermore, to add a layer of protection, it includes multi-factor authentication for endpoints and verifies and authenticates devices and users.
Additionally, the integrated AI-powered analytics engine enables real-time monitoring of access requests, allowing your team to gain valuable insights and take proactive actions based on contextual information. Additionally, the solution provides the capability to record, audit, and protect end-user activity within web applications, further improving security and helping adhere to compliance requirements.
Features
- CyberArk provides secure access to on-premises applications without the need for VPNs, complex code changes, or additional infrastructure deployment, simplifying access for your employees while maintaining security standards
- Also, your team can safeguard and manage privileged accounts, credentials, and secrets with CyberArk's privileged access manager solution. This simplifies the process of securing critical assets from unauthorized users
Customer Rating
- G2: 4.4/5
7. PingIdentity
PingIdentity offers PingOne for Workforce, which is designed to centralize adaptive authentication, which helps enhance security and productivity for your employees. This solution connects users to applications on any device, whether they are working from home, in the office, or anywhere in between, simplifying access.
Adopting a Zero Trust security strategy is essential in today's landscape, and identity plays a pivotal role in verifying every employee and device before granting access. PingOne for Workforce provides authentication and authorization capabilities critical to achieving Zero Trust maturity. To keep pace with evolving IT requirements, Ping offers simple yet powerful orchestration capabilities, enabling your IT team to automate access management processes without needing to code.
This cloud-based solution offers identity intelligence, drag-and-drop workflows, passwordless sign-on, centralized authentication, and a unified admin portal, allowing your team to customize your identity and access management strategy to meet your business needs. With PingOne for Workforce, your team can enhance the experiences of your remote employees, ensuring seamless and secure access to resources they rely on.
Features
- Ping uses open standards to enhance its compatibility with various SaaS applications. This compatibility makes Ping an ideal platform for robust user authentication, enabling secure access across diverse software and services
- Also, it integrates with SSO (single-sign-on) and MFA (multi-factor authentication). This integration helps your employees access the organization's data and apps safely and securely without remembering multiple passwords or usernames
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
8. Jumpcloud
JumpCloud's One Identity platform enables your IT team to securely connect users to their devices, servers, networks, applications, and files, offering flexibility by seamlessly integrating with existing identity providers based on specific needs.
Furthermore, this platform enables your team to grant employees the required application access that suits their needs and job roles, which helps in increasing productivity. Also, it adheres to open standards like SAML, LDAP, RADIUS, and SCIM, enabling the connection and management of diverse cloud resources from a centralized source.
Additionally, JumpCloud also facilitates centralized identity management through native API-based integrations with a wide range of identity sources, including Google Workspace, Microsoft 365, and HRIS systems like BambooHR and Personio. This integration streamlines the provisioning of new user accounts and the management of existing ones, creating a central identity hub.
Furthermore, JumpCloud simplifies the mapping of identities and resources with one-click provisioning. Whether users are created directly within JumpCloud or imported from other sources, organizations can efficiently assign varying levels of access based on user group memberships.
To strengthen security, JumpCloud offers configurable features, such as conditional access policies, multi-factor authentication, and strong password management policies, ensuring the protection of managed identities and resources.
Features
- JumpCloud streamlines identity management through native API-based integrations with various identity sources, including Google Workspace, Microsoft 365, and HRIS systems like BambooHR and Personio. This integration streamlines the provisioning of new user accounts and the management of existing ones, creating a central identity hub
- Also, it enables your IT team to remove employees from multiple groups when they depart from the organization with a single click, which further saves your team's time and efforts
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
9. AuthO
AuthO, a notable user access management tool, enables your IT team to create a frictionless experience for users. With AuthO, your team can seamlessly migrate users from on-premises to cloud environments seamlessly. It offers multiple migration options that your team can transition/shift all users at once or gradually as they log in while ensuring zero disruption for your users.
Furthermore, Auth0 gives your team a user-friendly management interface that provides deep insights into your user's app preferences and requirements.
With Auth0, your team can focus on building exceptional user experiences while leaving the complexities of user management and migration in capable hands.
Features
- AuthO provides a secure user directory capable of scaling to accommodate hundreds of millions of users. So with the help of both basic and personalized user details, your IT team can create a unique user experience and smoothly integrate user information into your app
Customer Rating
- G2: 4.3/5
10. IBM
IBM Cloud App ID, also commonly known as the cloud directory, is an authentication and user management service provided by IBM Cloud. It allows developers to easily add authentication to their web and mobile applications without building an authentication system from scratch.
It also provides support for passwordless authentication using multi-factor authentication that adds an extra layer of security and helps employees to seamlessly access applications.
Additionally, IBM Cloud App ID has built-in security enhancements and self-service capabilities, including email verification and password reset functionality. And it's a versatile set of user interface (UI) components designed to enhance user registration, authentication, and password reset processes. These prebuilt UI widgets can seamlessly integrate into your application, providing a user-friendly experience.
Furthermore, App ID provides your IT team with the option to customize the UI to match your branding, ensuring a consistent and visually appealing look and feel.
Features
- IBM Cloud App ID goes beyond basic authentication by offering the user profiles feature. This functionality allows your IT team to store and manage user-specific information, such as user's app preferences. Using these accurate user insights, your team can create personalized app experiences for your users.
- It also offers a pre-built feature for email verification and password reset. This feature enables your IT team to configure the workflow according to their requirements. Such as allowing your users to use applications for a certain period before they authenticate/verify their email address.
Customer Rating
- G2: 4.1/5
- Capterra: 4.5/5
11. Keycloak
Keycloak, a notable user access management tool, is an open-source user access management solution that plays a pivotal role in simplifying the authentication/ verification of user identities while adding an essential layer of security to applications. By enforcing user verification before granting access, Keycloak significantly reduces the risk of potential security breaches stemming from the absence of a robust authentication system.
Furthermore, once users log in to Keycloak, they can access different applications seamlessly, eliminating the need to log in repeatedly. Similarly, Keycloak offers a single sign-out feature, allowing users to log out across all Keycloak-integrated applications by logging out from Keycloak.
Additionally, through its intuitive admin console, your IT admins can centrally manage various aspects of the Keycloak server. They can enable or disable specific features, configure identity brokering, and implement user federation. Additionally, administrators can create, manage, and fine-tune application settings, define granular authorization policies, and oversee user management, including permissions and sessions.
Apart from that, for end-users, Keycloak provides an account management console where they can take control of their own accounts and update their profiles or change passwords.
Features
- Keycloak provides a seamless and hassle-free way to enable identity brokering (creating trust between parties interested in using each other's online identities) and social login within your application. With this feature, your team can allow your users to log in using their preferred social network accounts without the need for any coding or modifications to your application
- Keycloak simplifies user management by offering built-in support for connecting to LDAP (lightweight directory access protocol) and active directory servers. Whether your users are stored in these established directories or other custom stores like relational databases, Keycloak provides the flexibility to integrate seamlessly
Customer Rating
- G2: 4.2/5









.svg)














