Segregation of duties (SoD) involves dividing tasks among different individuals to prevent conflicts of interest and minimize the risk of errors or fraud. SoD policies outline guidelines for task assignment, while procedures specify how to implement these guidelines. By adhering to SoD policies and procedures, organizations enhance internal controls and reduce the likelihood of unauthorized actions or mistakes.
For instance, think of a policy as a general rule or guideline, like \"no departing employee should retain access to any SaaS applications, data, or systems.\" Basically, what's done here is your organization has set a rule for what needs to be done.
Now, think of a procedure as a detailed instruction manual that explains exactly how to follow the policy. It tells you step by step what actions to take, like \"how your IT team can securely deprovision departing employees,\" which includes removing the employee from all groups, channels, and projects and revoking all access without missing out on any critical steps.
Similarly, when it comes to the Segregation of duties policy, and procedure, they work together but have distinct roles. So, in this article, we'll learn how your IT team can create an SoD policy for your organization and how your IT team can streamline it by following SoD procedures.
What is a Segregation of Duties Policy?
The Segregation of Duties policy is a crucial component that you need to grasp to ensure robust security and compliance within your organization. This policy revolves around the fundamental principle of dividing tasks and responsibilities among different individuals to prevent conflicts of interest and potential fraud.
Simply put, segregation of duties aims to distribute key functions among multiple team members, ensuring that no single person has complete control over a critical process. This not only helps in safeguarding sensitive data but also acts as a deterrent against internal threats and unintentional errors that may arise in the course of business operations.
Consider a scenario where an organization's finance department is responsible for both initiating payments and reconciling bank statements. Without a Segregation of Duties policy in place, a single employee could manipulate financial records to cover up fraudulent activities, such as embezzlement or unauthorized transactions.
By implementing SoD, you can designate separate individuals for these tasks. One employee initiates payments, while another is responsible for reconciling bank statements. This division of duties acts as a checks-and-balances system, reducing the risk associated with financial misconduct and enhancing the integrity of financial processes.
Why Is There A Need To Enforce SoD Policy?
The separation of duties policy is one of the organization's most effective internal control strategies. Its primary purpose is to prevent conflicts of interest and minimize errors during the access management process.
Basically, this SoD policy revolves around the fundamental principle - no single employee/user should hold all the power and sole responsibility for specific IT tasks. This SoD control or internal control further helps ensure impartial decision-making by assigning different employees to manage different aspects of a task (like authorization, recording, and custody of assets should be performed by different employees).
To provide a clear understanding, here's a real-time example: the IT team responsible for granting, modifying, and revoking employees' access to apps, data, and systems should not also be in charge of reviewing that access. Instead, a separate team should be assigned to manage the access review. This separation ensures that there's no room for biased decisions or data manipulation during the review process.
Now let's proceed and see how your IT team can create and customize the SoD policy according to your organization's workflow.
How Your IT Team Can Create SoD Policy For Your Organizations
Below are the steps your IT team needs to follow to create a segregation of duties policy that caters to your organization's operational requirements.
Step 1: Create An SoD Policy With Resolution Instructions
Consider adding resolution instructions in the \"Resolve\" field when creating your separation of duty policy. Your IT team can even embed HTML links in these instructions to provide additional information or guidance to users when reviewing an SoD policy violation. While this step is optional, it helps users understand how to resolve violations without waiting for further instructions.
Step 2: Define SoD Conditions, User Conditions, and Account Conditions
A SoD policy relies on defining conditions that specify which combinations of permissions and roles users are prohibited from holding.
Your IT team can configure expressions for user and account conditions to specify the applicability of the segregation of duties policy. For instance, your IT team can define the policy's conditions for specific users or unmapped accounts (like users in certain locations or accounts with particular categories). Similarly, your IT team can implement conditions to exclude specific users or unmapped accounts from the SoD policy.
Further, after creating the SoD policy, your IT team can test a user's permissions and roles against these conditions to determine if they violate the policy.
Note- A violation only occurs if the user's permissions and roles violate every condition specified in the SoD policy.
Additionally, the SoD policy works for unmapped accounts with no associated users, as they may have permissions assigned to them. These accounts are also subject to SoD policy checks like users.
Thus, your IT team needs to verify if an account's permissions match the conditions specified in the policy.
Note: A violation for the account only arises if its permissions don't meet every condition outlined in the segregation of duties policy.
By following these steps, your IT team can create a Segregation of Duties policy that will help your team effectively manage access control and promote a secure and compliant access environment within your organization.
Furthermore, to manage the SoD policy seamlessly, your IT team needs to follow effective SoD procedures. So let's find out about the separation of duties procedure, why there is a need for the SoD procedure, and what steps are involved in it.
What is Segregation of Duties Procedure?
One essential practice that plays a pivotal role in enhancing security is the implementation of Segregation of Duties (SoD) procedures. SoD is a systematic approach that divides tasks and responsibilities among different individuals to prevent conflicts of interest and unauthorized access, thus bolstering the overall security posture of an organization.
To illustrate, let's consider an example within a cloud-based financial management system. Traditionally, a single user might have complete control over financial transactions, from initiating payments to final approvals. However, this concentrated authority creates a potential risk, as a single compromised account could lead to financial mismanagement or fraud.
With the Segregation of Duties, these tasks are distributed among multiple individuals or roles. For instance, the user who initiates a payment is distinct from the one who approves it, introducing a layered security approach. This way, even if one account is compromised, the potential damage is limited as the malicious actor would need access to multiple accounts to carry out a fraudulent transaction.
Why Does Your IT Team Need To Follow SoD Procedures?
SoD procedure comprises a structured set of specific steps that your IT team needs to follow to carefully navigate successful implementation and maintain separation of duties policy within your organization. Further, these steps are important for:
- Ensuring data security- One of the primary objectives of the SoD procedure is to safeguard your organization's data. By following these steps involved in the SoD procedure, your IT team can create a robust security framework where access to sensitive information is controlled, reducing the chances of data breaches and unauthorized access.
- Minimizing risks of access mismanagement- Access mismanagement can pose significant risks to an organization. Errors or intentional misuse of privileges can lead to security vulnerabilities and operational disruptions. The SoD procedure acts as a preventive measure to minimize these risks by structuring access control.
- Maintaining compliance. Compliance with industry regulations and standards is paramount. Many regulatory bodies require organizations to have effective access control mechanisms in place. Following the SoD procedure ensures that your organization complies with these requirements and avoids potential legal and financial consequences.
Let's move further and explore the steps involved in the SoD procedure in detail.
6 Steps Included In SoD Procedure
Below are the steps your IT team needs to follow to streamline the segregation of duties in your organization.
Step 1: Define Policies & Processes
Deploy an effective identity governance tool that will help your IT team implement segregation of duties and consistently enforce policies across multiple applications.
Step 2: Create A Centralized Dashboard
To monitor separate duties effectively, your IT team needs to have a unified dashboard displaying access and authentication activities across all enterprise applications. This enables tracking user activities, even when users have access to multiple applications.
Step 3: Manage Privileged Access By Putting Restrictions
Implement the concept of providing temporary, elevated access to users based on time constraints or specific role-related conditions. Remove this access when it's no longer necessary or when it may lead to an SoD conflict.
Step 4: Create Structured Access Request Workflows
Access should never be granted haphazardly but should always follow predefined workflows. Identity governance tools streamline these workflows, ensuring only authorized users gain access to authorized SaaS apps, data, and systems that align with their roles and responsibilities. Also, advanced IGA solutions help your IT team to document the entire process so that during the audit, your IT team shows all the standards are met and no SoD policy is violated.
Step 5: Implement Role-Based Access Provisioning
As a general practice, refrain from granting access directly to individual users. Instead, assign individuals to roles and automate access provisioning based on their assigned roles. This automation helps prevent delays in access provisioning that can negatively impact productivity.
Step 6: Promote Collaboration Between IT & HR Departments
These two departments can jointly define roles and approvals. This collaboration will help your IT team ensure that access permissions closely align with the job descriptions and the specific skill sets of individual employees.
Now that you are aware of the SoD policy implementation, the next step is to find a suitable tool to enforce these policies. While numerous options are available in the market, one standout solution is Zluri.
Opt For Zluri To Implement SoD Policy & Procedure
Zluri is a modern access management platform designed to help your IT team seamlessly enforce segregation of duties (SoD) and prevent potential security breaches. How does it do that? Here's a quick read-through.
Identify Who Has Access To What With Zluri’s Data Discovery Engine
Zluri's IGA solution is at the forefront of redefining SoD policy management, introducing a paradigm shift in how organizations maintain a robust separation of duties while harnessing the full potential of their SaaS applications and user landscape.
Central to this transformation is Zluri's cutting-edge discovery engine, which seamlessly integrates nine discovery methods – MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional). These methodologies synergize harmoniously to equip your IT team with effortless access to invaluable data insights.
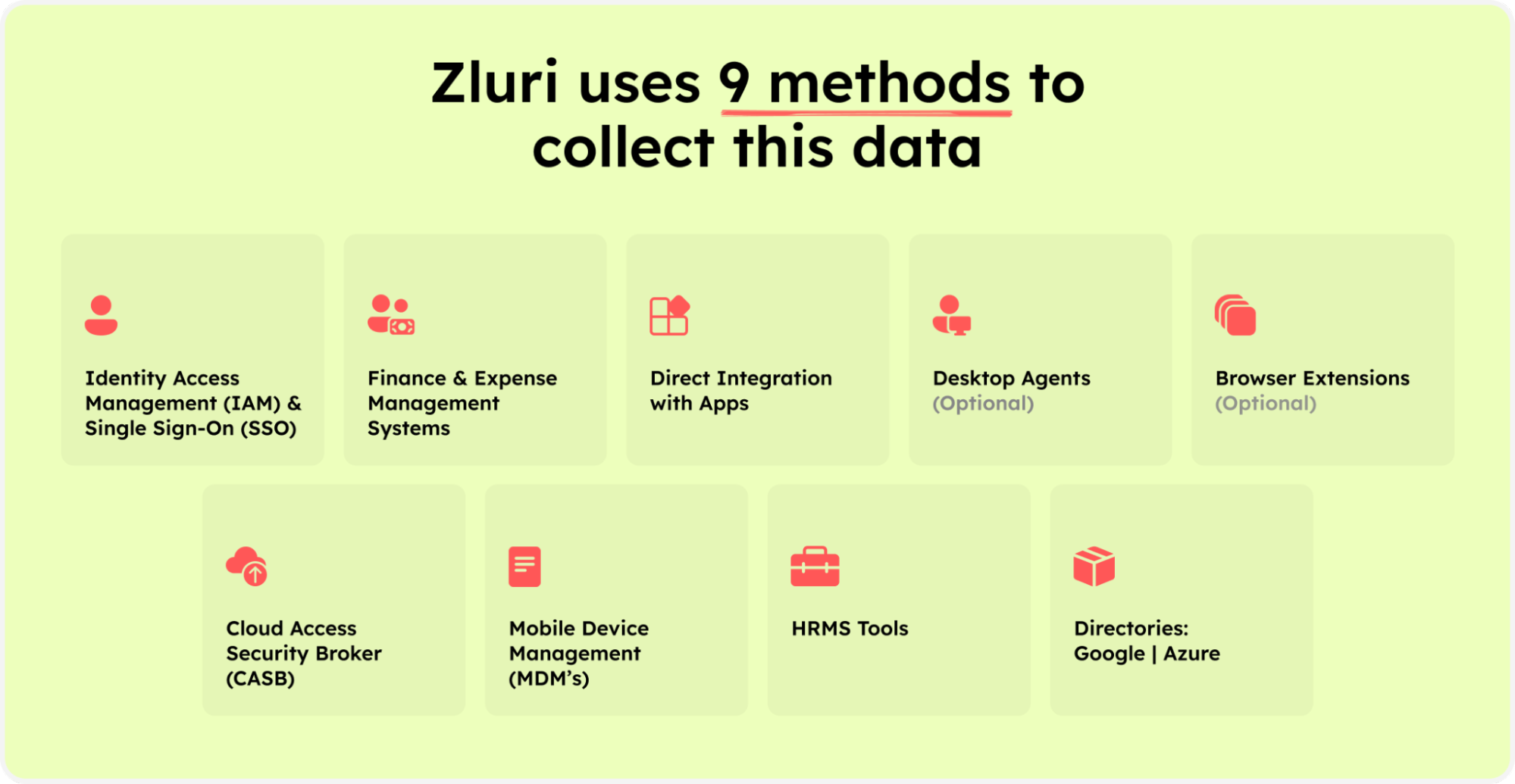
Zluri’s nine discovery methods
A strategic embrace of SoD principles
Incorporating the principles of separation of duties, Zluri elevates its commitment to the next level. By meticulously segregating data access and analysis roles, the platform sets new benchmarks in security enhancement. This meticulous approach ensures that individuals authorized for data access remain distinct from those entrusted with its in-depth analysis and interpretation.
This strategic division significantly reduces the risk of unauthorized tampering, safeguarding the integrity of your insights and strengthening compliance endeavors.
Set SoD Policies During Provisioning & Mid-lifecycle Transition With Zluri’s Automation Engine
Zluri’s automation engine enables your IT team to enforce Segregation of Duties policies seamlessly.
- Streamlined Onboarding Process:
- Zluri automatically links your employees' profiles with their digital identities from the organization’s HRMS upon onboarding.
- Facilitates identity verification before assigning roles and granting access to SaaS applications and data.
- Your IT team can create customized onboarding workflows with in-app suggestion features.

- Assigns roles, adds employees to groups/projects, and customizes access permissions effortlessly without coding.
- Role-Based Access Control (RBAC):
- Zluri’s RBAC capability ensures designated roles for specific tasks to prevent role conflicts and reduce the risk of over-permission.
- Minimizes conflicts of interest by granting only necessary permissions for respective tasks.
- Mitigating Operational Disruptions:
- Illustrative scenario: Addressing inefficiencies in the IT department's resolution process.
- Implementation of SoD policy during onboarding via Zluri's workflow creation.
- Assigning distinct roles to employees to segregate duties and ensure accountability.
- Enhanced Accountability and Error Detection:
- Separation of duties reduces biases and fraudulent activities.
- Enables effective error detection and issue resolution by clearly defining responsibilities.
- Mid-Lifecycle Transition Management:
- Zluri notifies IT teams about changes in roles, departments, or positions.
- Enables modification of role and access permissions post-verification, preventing excessive privileges.
- Introduces Zluri’s Employee App Store (EAS) for streamlined access request management.
- Empowers IT teams to control access permissions aligned with employees' job roles and responsibilities.
- Enhances user experience by determining app visibility for each user dynamically.
- Seamless Offboarding Workflows:
- Zluri automates the offboarding process, streamlining the tasks associated with revoking access and permissions for departing employees.
- Zluri's offboarding process plays a crucial role in supporting segregation of duties policies and procedures for IT managers by automating access revocation, implementing role-based access controls, providing centralized visibility, and facilitating documentation.
Ensure SoD Policy Conditions Are Met By Reviewing User Access With Zluri’s Access Certification Capabilities
Managing access reviews manually can be time-consuming and prone to inaccuracies, posing challenges for businesses striving to maintain compliance with Segregation of Duties (SoD) policies. Zluri offers a comprehensive solution to streamline the access review process, ensuring efficiency and accuracy.

Unified Access Review Feature: Zluri's unified user acccess review solution empowers your IT team to efficiently assess user access across multiple applications. By centralizing access-related data in Zluri's access directory, organizations gain valuable insights into employee access privileges, enabling them to identify potential violations of SoD policies.
Thorough Examination of Access Privileges: With Zluri, your IT team can conduct thorough examinations of user access privileges, ensuring alignment with employees' roles and responsibilities. By leveraging insights such as user roles and departments, organizations can mitigate the risk of unauthorized access and maintain compliance with SoD policies.
Real-time Activity Monitoring and Alerts: Zluri's activity and alert feature provides real-time updates on users' access activities, empowering your IT team to promptly address any deviations from established access policies. This proactive approach ensures smooth operations and facilitates informed decision-making during access reviews.
Automated Access Certification Process: Zluri simplifies the access certification process by offering automation capabilities. Through Zluri's intuitive interface, organizations can create certifications, select relevant apps and users for review, and rely on automated verification to ensure compliance with access policies. Reports are seamlessly generated and distributed to reviewers, optimizing efficiency and transparency.
Impartial Review Process: Zluri ensures an impartial review process by preventing reviewers from being involved in user role management, thereby mitigating the risk of biased decisions. This safeguards the integrity of the access review process and promotes fairness in evaluating access privileges.
Enhanced Compliance and Risk Management: By leveraging Zluri's contextual insights, organizations can enforce SoD policies based on industry regulations and internal best practices. The platform enables proactive identification of potential access violations and facilitates corrective actions to maintain compliance with regulatory requirements.
Scheduled Certifications and Auto-Remediation: Zluri's schedule certification feature enables organizations to create certifications based on real-time data, empowering teams to take timely actions to address access-related risks. In the event of policy deviations, Zluri initiates auto-remediation actions, such as access revocation or modification, ensuring adherence to established policies.
Comprehensive Reporting and Analytics: Zluri offers detailed reports and analytics on user access patterns, violations, and associated risks, enabling organizations to proactively identify and mitigate potential SoD violations. This data-driven approach facilitates informed decision-making and strengthens overall compliance efforts.
Now that you've learned how Zluri helps your IT team implement the SoD policy and procedure. So why wait any longer? Book a demo now and witness yourself how Zluri seamlessly controls, manages, and governs user access by ensuring that users have the right access aligned with their roles and responsibilities, preventing a conflict of interest.
FAQs
What is a segregation of duties example?
In the scenario of a corporate acquisition, when one business assimilates another, the integration process extends to the ERP system. It becomes imperative for members of the finance and IT teams to secure access rights within the newly acquired ERP system. Furthermore, ensuring the continuity of their existing access privileges within the parent company's ERP system is essential.
What is the separation of duties protocol?
Duty segregation ensures that the individual who initiates an action is distinct from the one responsible for its approval. This measure effectively minimizes the potential for conflicts of interest or regulatory noncompliance, mitigating the risk of legal repercussions in any given situation.
What are SoD Matrices?
The SoD Matrix plays a pivotal role in establishing clear definitions for accounting responsibilities, roles, and risks. In the past, creating the SoD matrix involved:
- Manual efforts.
- Utilizing pen and paper.
- Relying on human reviews of permissions associated with each role.
Today, sophisticated software solutions automate this process, streamlining and enhancing the efficiency of SoD management.
What are SoD conflicts?
Potential SoD conflicts arise when a specific role within an organization possesses the power to impact financial activities or the financial reporting process by executing various tasks within a financial workflow.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)