For IT managers, understanding the ever-evolving landscape of IAM is crucial. Identity and access management trends are reshaping IAM practices, introducing innovative solutions and, concurrently, new security challenges. In this article, we’ll explore IAM's latest trends and examine their contributions to minimizing security risks while fostering a secure access environment.
With the advancement of technology, hacking incidents, especially with passwords and networks, are on the rise, and nowadays, even strong passwords can be cracked in seconds. If data is not protected or stored on a secure server, then it's at risk of being accessed by unauthorized individuals. These breaches can further damage a company's reputation, financial losses and exposure to sensitive client information.
So, to mitigate these rising challenges, identity and access management come into play. It adds an extra layer of security to an organization's networks and helps keep track of employee activities, controls access to programs and apps to prevent unauthorized entry, and identifies suspicious patterns or errors.
However, there are also certain identity and access management trends that you need to be aware of in order to adapt and deal with this evolving digital environment. So, before we explore these trends in detail, let's first understand identity and access management and its importance.
What Is Identity And Access Management?
Identity and access management (IAM) is the process of managing, controlling, and securing digital identities and their access within an organization. Implementation of IAM involves procedures, guidelines, and advanced technological tools to manage digital identities and control/restrict access to systems and data.
The primary purpose of IAM systems is to thwart unauthorized access, prevent data breaches, and mitigate other security threats, all while ensuring that access to resources is limited to approved users. Furthermore, IAM also includes user authentication, authorization, and user management. In which:
- Authentication involves verifying a user's identity, typically through methods like usernames, passwords, multi-factor authentication, or biometrics.
- Authorization determines the specific resources or functionalities a user can access based on their identity and associated rights.
- User management involves overseeing sensitive user data, such as passwords, roles, and permissions, ensuring proper maintenance and security.
Moreover, the effective implementation of IAM is essential for maintaining the security of digital assets and achieving regulatory compliance. By tightly controlling and monitoring access, IAM contributes significantly to preventing unauthorized access, securing sensitive data, and aligning access privileges with organizational policies and regulatory requirements.
But why is the implementation of identity and access management crucial for organizations?
Importance Of Identity And Access Management
Safeguarding sensitive data and ensuring regulatory compliance have become paramount concerns for IT managers. As businesses embrace innovative solutions, the complexity of managing user access and protecting critical information has grown exponentially. To address these challenges, identity and access management plays a crucial role.
Beyond merely granting and revoking access, IAM has become a multifaceted asset that enables you to navigate the web of data security, regulatory compliance, insider threats, and operational efficiency.
To provide you with a better understanding, here’s how IAM plays an important role in modern cybersecurity
- Enhanced Data Security: IAM systems enable IT managers to control and monitor user access to critical systems and data. By implementing strong authentication methods, such as multi-factor authentication (MFA) and biometrics, IAM ensures that only authorized personnel can access sensitive information, mitigating the risk of unauthorized access or data breaches.
- Regulatory Compliance: Numerous regulations and standards, such as GDPR, HIPAA, and PCI DSS, mandate stringent data protection measures. IAM solutions assist IT managers in enforcing compliance by providing audit trails, access logs, and user activity monitoring. This documentation is crucial for demonstrating adherence to regulatory requirements during audits.
- Minimized Insider Threats: Insider threats, whether intentional or accidental, pose a significant risk to organizations. IAM tools allow IT managers to define user roles and permissions accurately. By implementing the principle of least privilege (PoLP), IAM ensures that employees have access only to the resources necessary for their specific roles, reducing the potential impact of insider threats.
- Scalability and Efficiency: IAM solutions streamline user provisioning and deprovisioning processes. IT managers can automate user onboarding and offboarding, ensuring that employees have access rights from day one and that access is promptly revoked upon employment termination. This automation not only enhances security but also improves operational efficiency.Now that you are familiar with what is identity and access management and why it’s important, let’s proceed further and explore different identity and access management trends 2024.
7 Identity And Access Management Trends In 2024
Below, we’ve uncovered the key trends in identity and access management for a secure, efficient, and technologically advanced future.
1. Zero-Trust Security Model
In the contemporary cybersecurity landscape, a notable identity and access management trend gaining prominence is the zero-trust security model. This approach operates on the core belief that no user or device can be inherently trusted, regardless of its location within or outside the network.
The essence of this model lies in its insistence on stringent authentication and authorization for every transaction. As businesses increasingly adopt hybrid work models, accommodating employees from diverse locations, the zero trust model has emerged as a vital safeguard. Its implementation involves deploying various tools that facilitate continuous authentication and authorization processes.
Embracing the zero trust paradigm equips organizations with robust security measures, ensuring resilience against the diverse cyber threats in our rapidly evolving digital landscape.
For example, employees frequently access sensitive corporate data from various locations using different devices in a company embracing a hybrid work model. Traditionally, such access might have been granted based on the employee's location (inside or outside the corporate network).
However, in the zero trust model, every access attempt, regardless of the user's location or device, is treated as potentially unauthorized.
2. Biometric Verification & Authentication
Biometric authentication and verification have swiftly emerged as a prominent cybersecurity identity and access management trend. This surge is primarily attributed to the heightened need for enhanced security measures in the face of evolving cyber threats.
Unlike traditional methods like passwords, biometric authentication utilizes unique biological or behavioral traits, such as fingerprints, facial features, or typing patterns, making it significantly more secure and challenging to replicate. Moreover, advancements in technology, including machine learning and artificial intelligence, have substantially improved the accuracy and reliability of biometric systems.
Additionally, the growing emphasis on regulatory compliance and the rising demand for seamless user experiences have propelled the widespread adoption of biometric methods. Industries ranging from finance to healthcare are swiftly integrating biometric authentication, marking a paradigm shift toward more secure and user-friendly authentication practices.
As you continue to prioritize data protection and user convenience, biometric verification and authentication are poised to remain a central focus in the evolving landscape of cybersecurity.
3. A Layered Approach To Security
Adopting a layered approach to security, incorporating multi-factor authentication (MFA) and single sign-on (SSO), represents an emerging trend in cybersecurity. In today's digital landscape, where cyber threats continue evolving in complexity and frequency, organizations recognize the need for comprehensive security strategies.
This identity and access management trend is emerging as you and your teams increasingly understand that relying solely on traditional security measures, such as passwords, is insufficient to protect against sophisticated attacks. By combining risk-based and behavioral-based adaptive access controls, this layered approach ensures that multiple factors are considered before granting access, adding an extra layer of defense.
MFA, which incorporates diverse authentication factors, and SSO, streamlining access across multiple platforms, are at the forefront of this trend. Businesses are embracing these advanced methods to fortify their security postures, reflecting an industry-wide shift towards more robust, multifaceted security solutions.
This trend signifies a proactive response to the growing challenges of cybersecurity, demonstrating a collective commitment to staying ahead of emerging threats and safeguarding sensitive information effectively.
4. Decentralized Digital Ecosystem
Decentralized Identity, also widely known as DID, is one of the emerging trends in identity and access management that uses blockchain technology to make a secure, self-sovereign identity framework/system. With DID, individuals can manage their identity data on their own and selectively share required information with trusted entities without depending on centralized authorities. Despite regulatory and technical obstacles, DID has the potential to revolutionize IAM by providing individuals with control over their personal information and lessening reliance on centralized authorities.
5. Entitlement Management
Entitlement management is a burgeoning identity and access management trend due to its evolution beyond the conventional principle of least privilege (POLP). While POLP has been a foundational concept, the emerging trend lies in its adaptation to the complexities of contemporary technology landscapes.
With the integration of machine and application identities, organizations are redefining access control strategies to counter evolving cybersecurity threats. Just-in-time access provisioning, a proactive approach ensuring precise privileges for specific durations, addresses the dynamic nature of modern roles, preventing privilege escalation and unauthorized access.
Additionally, the shift to cloud-based infrastructures necessitates reevaluating access rights, making entitlement management pivotal in synchronizing and securing these transitions. As organizations increasingly recognize the need for adaptable and nuanced access controls, entitlement management emerges as a crucial and evolving trend, reshaping how IAM is conceptualized and implemented in the face of rapidly advancing digital environments.
Consider a multinational corporation migrating its operations to the cloud. In this scenario, the traditional IAM approach might inadvertently grant extensive access rights to cloud resources, mirroring the on-premises setup. However, with entitlement management, the company can implement just-in-time access provisioning.
For instance, when a developer needs access to specific cloud resources for a limited time to complete a project, entitlement management ensures they receive precise privileges tailored to their task. This approach prevents unnecessary access, reducing the risk of security breaches.
6. Leveraging AI And Machine Learning
Integrating AI and machine learning into identity and access management processes marks an exciting and transformative trend in the cybersecurity landscape. This trend's momentum can be attributed to its unparalleled advantages, encompassing enhanced precision, remarkable speed, and unmatched scalability.
AI and ML are redefining how organizations protect their digital assets by automating vital tasks such as user provisioning, access certification, and real-time detection of behavioral anomalies.
What distinguishes this identity and access management trend is its capacity to respond to existing threats and anticipate future user behavior. This predictive ability empowers the implementation of personalized access controls custom-tailored to individual user behaviors, creating a proactive defense against potential security breaches.
Additionally, these sophisticated technologies empower organizations to manage identities efficiently, ensuring seamless operations and fortified security protocols. As AI and ML technologies evolve rapidly, they are poised to assume an even more central role in IAM. Their adaptive nature enables enterprises to anticipate and counter emerging threats, positioning them at the forefront of cybersecurity innovation.
By harnessing these advanced tools, you and your teams can keep up with evolving digital risks and proactively outpace them, strengthening defenses in an ever-shifting digital landscape.
7. Implementing Cloud-Based IAM Solutions
Cloud-based IAM solutions bring many advantages, revolutionizing how your teams manage identities and access. These benefits include enhanced security measures, streamlined user authentication, and real-time monitoring. By shifting to the cloud, businesses can ensure robust data protection, compliance adherence, and seamless user experiences, thereby gaining a competitive edge in the market.
Firstly, the increasing frequency and sophistication of cyber threats have compelled organizations to seek more robust and agile security measures. Cloud-based IAM offers advanced authentication protocols and real-time monitoring capabilities, providing a more secure environment for sensitive data.
Secondly, the rapid proliferation of cloud technologies has fundamentally transformed how businesses operate. Cloud platforms provide scalable, cost-effective solutions, making them highly appealing to organizations of all sizes. Cloud-based IAM aligns seamlessly with this trend, offering scalability and flexibility that traditional on-premise solutions struggle to match.
Additionally, the growing emphasis on remote work and mobile access has heightened the importance of IAM. Cloud-based solutions enable secure access control from anywhere, catering to the needs of modern, mobile-oriented workforces. Furthermore, the cloud facilitates more straightforward integration with other digital tools and services, enhancing overall efficiency and productivity.
Lastly, regulatory requirements around data protection and privacy have become increasingly stringent. Cloud-based IAM solutions often have robust compliance features, helping businesses adhere to these regulations effortlessly.
Why Is It Important To Stay Up-To-Date With Identity And Access Management Trends?
There are various reasons organizations should adopt and evolve with the latest identity and access management trends; some of the reasons are mentioned below:
1. To Ensure the Organization Stays Strong Against New Threats:
In order to stay ahead in maintaining proactive security measures, organizations need to stay up-to-date with new identity and access management trends. Moreover, by staying informed about the ever-evolving landscape of threats and vulnerabilities, an organization's IT teams can seamlessly anticipate and effectively address potential security breaches.
Also, staying up to date with the latest trends in identity and access management helps organizations strengthen their defense mechanism to safeguard their sensitive data against emerging cyber threats. This ensures the overall resilience of an organization's security posture.
2. To Keep Up With The Latest Technological Advancements:
Identity and access management trends are closely aligned with the emerging technological advancement in the field of cybersecurity. By embracing these trends, organizations can take advantage of advanced encryption techniques and cutting-edge access control technologies. This proactive adoption of innovative solutions strengthens an organization's security infrastructure, effectively addressing evolving cyber threats and maintaining a secure access environment.
3. To Improve the User Access Management Process
Identity and access management trends emphasize refining user management processes to optimize efficiency and enhance user experience. These trends often improve various aspects, including user onboarding, access provisioning, and account maintenance. The goal is to create a more productive and user-friendly environment within organizations. By streamlining these processes, IAM trends contribute to smoother operations, reducing the time and effort required for tasks related to user access.
A well-implemented IAM system enhances efficiency and mitigates the risk of errors. Improved user management ensures access privileges align with organizational policies, reducing the chances of unauthorized access or security lapses. This proactive approach benefits the organization internally and contributes to a positive user experience, fostering a secure and streamlined environment for both employees and IT teams.
4. To Implement Industry's Latest Security Best Practices
Identity and access management trends often align with industry best practices. When organizations incorporate these trends into their IAM strategies, they gain valuable insights from proven strategies and methodologies. By following these best practices, organizations enhance the overall effectiveness of their IAM implementations. This ensures a robust security framework and positions them to navigate the ever-evolving landscape of cybersecurity with a well-informed and proactive approach.
You need robust tools with robust IAM capabilities to navigate the complexities of the above identity and access management trends. Zluri's advanced IAM capabilities are designed to bolster security measures, streamline administrative tasks, and provide organizations with the upper hand in protecting their digital assets.
How Zluri Helps You Embrace The Identity And Access Management Trends?
Zluri stands at the forefront of cutting-edge cybersecurity solutions, offering advanced identity and access management capabilities that redefine digital security paradigms. Through its innovative IAM technology, Zluri empowers you to fortify your defenses, ensuring robust protection against unauthorized access and data breaches.
Digital threats constantly evolve; Zluri's IAM solution provides a comprehensive and sophisticated approach, safeguarding sensitive information, enhancing compliance, and promoting seamless user experiences. Explore how Zluri's IAM capabilities are shaping the future of cybersecurity, setting new standards to safeguard digital assets.
Advanced Identity Management Strategies With Zluri
Elevate your digital security with Zluri's cutting-edge identity management capabilities to ensure your organization's data remains secure in the face of evolving threats.
- Implementing Zero Trust Security Strategy
Within Zluri's domain, the rigorous implementation of the Zero Trust Security Strategy is paramount. Upholding principles like 'never trust, always verify' and 'assume breach,' Zluri orchestrates a meticulous verification process for users' digital identities.
This stringent authentication protocol ensures that access to critical resources such as applications, data, and systems is granted only after comprehensive identity verification, bolstering organizational security profoundly.
- Enforcing Principle Of Least-Privilege Access
Zluri fervently advocates for the principle of least-privilege access, a fundamental tenet in their access management approach. By meticulously assigning access permissions based on specific roles and responsibilities, Zluri significantly curtails the potential for security breaches.
This tailored approach eradicates over-provisioning, effectively minimizing vulnerable attack surfaces across the organizational digital landscape.
- Multi Factor Authentication for Enhanced Security:
Zluri's dedication to enhanced security manifests through multi-factor authentication methods that surpass conventional standards. Leveraging advanced techniques, including biometrics, possession validation, knowledge-based challenges, and location-specific verification, Zluri establishes a robust secondary user authentication layer.
These multi-factor authentication measures enhance security, providing a robust defense against unauthorized access attempts and potential cyber threats.
- Just-In-Time Access For Flexibility and Control:
In Zluri's innovative framework, just-in-time access provides unparalleled flexibility and control to organizations. Addressing scenarios demanding temporary privilege escalation, this approach grants time-limited access permissions tailored precisely to specific requirements.
Customization ensures that temporary access seamlessly integrates with overarching user access provisioning policies. Zluri's auto-remediation feature ensures prompt access revocation post the specified timeframe, effectively mitigating potential security risks associated with prolonged access periods.
- Role-Based Access Control For Streamlined User Management:
Zluri revolutionizes the complex terrain of role-based access control (RBAC) through automation and simplification. Empowering IT teams, Zluri enables them to define precise roles, establish granular access policies, and automate access adjustments seamlessly throughout the employee lifecycle.
This automated approach enhances organizational efficiency and guarantees secure and compliant user management practices, aligning seamlessly with industry regulations.
In adopting these advanced access management strategies, organizations partnering with Zluri embrace a future-proof security posture fortified against evolving cyber threats. Zluri's innovative solutions redefine access management, ensuring organizations thrive in the face of digital challenges.
Advanced Access Management With Zluri To Enhance Security And Efficiency
Empower your teams to tackle cybersecurity challenges proactively with Zluri to transform how you safeguard your digital assets.
- Automated Workflows For Efficient Access Management:
Zluri's automation capabilities are at the heart of its efficiency. By automating repetitive IT tasks like provisioning and deprovisioning, Zluri significantly reduces the margin for human error.
Customized onboarding and offboarding workflows, tailored to specific roles and responsibilities, ensure that new employees seamlessly integrate into the organization while departing employees undergo a secure departure process. These automated workflows guarantee a smooth transition, maintain data integrity, and enhance user experiences.
Also, as per Kuppingercole's research and analysis, Zluri’s automated onboarding/offboarding workflow saves IT teams hours of manual effort.

- Streamlined Access Certification Process:
Access certification is critical for ensuring that user access aligns precisely with their roles. Zluri simplifies this complex process through automation. IT teams can create certification workflows specifying reviewers and predefined actions (approval, modification, or rejection).
This automation expedites the certification process and guarantees accurate alignment of access permissions with users' responsibilities. It's a proactive measure to maintain a secure access environment, adhering to compliance standards and organizational policies.

- Embracing Passwordless Authentication:
Traditional password systems are susceptible to breaches. Zluri advocates for passwordless authentication, a modern approach to security. Users can choose from various methods, such as email-based, SMS-based, biometrics-based, or social login.
By eliminating reliance on easily compromised passwords, Zluri significantly enhances security. Users experience seamless yet highly secure authentication processes, reducing the risk of unauthorized access.
Embracing Modern Access Management With Zluri:
Zluri's data discovery engine offers deep insights into user access patterns. Organizations can make informed decisions to enhance governance and security strategies by understanding how users interact with applications and data.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Real-time activity alerts empower IT teams to respond promptly to suspicious activities, mitigating potential threats effectively. Furthermore, Zluri generates curated reports that offer actionable insights.
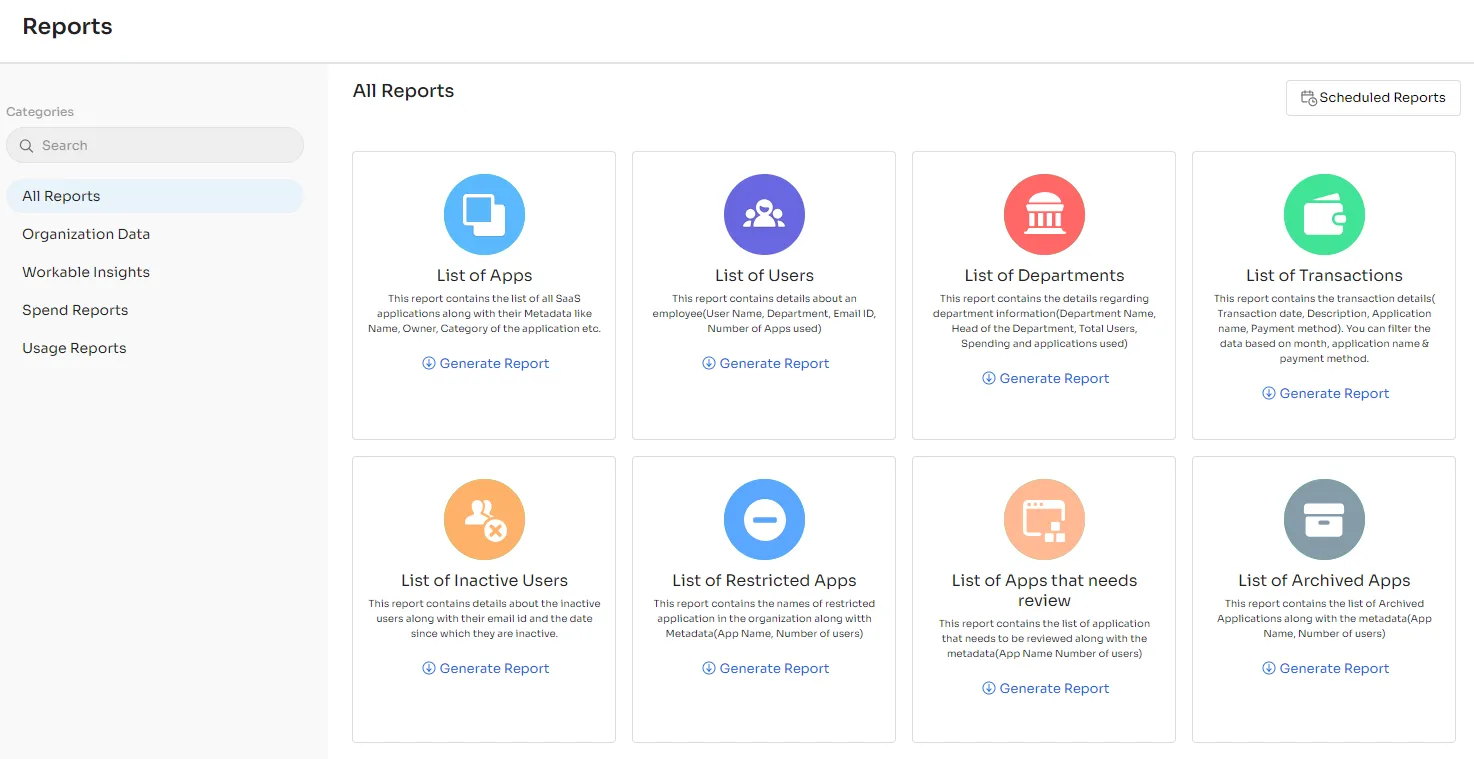
These reports enable proactive security measures, empowering organizations to stay one step ahead in the face of evolving cybersecurity challenges.
Zluri's advanced access management capabilities redefine how organizations approach security. By combining automation, streamlined certification processes, passwordless authentication, and granular insights, Zluri ensures enhanced security and a seamless user experience.
So what are you waiting for? Book a demo now and see for yourself.
FAQs
What Is The Future Of Identity And Access Management?
The future of IAM involves using adaptive and contextual methods to create experiences that are smooth, secure, and focused on the user. This signifies a shift towards methods that respond to individual needs and consider the specific context in which users interact with systems. By incorporating these adaptive and contextual strategies, the aim is to craft experiences that seamlessly cater to user requirements, ensuring both security and user-centricity.
What Factors Have Played A Pivotal Role In The Adoption Of An IAM Program?
Cybersecurity and operational efficiency are the two factors that influence organizations to adopt IAM programs. Cybersecurity is a top concern as organizations strive to safeguard their sensitive information and systems from malicious threats. IAM programs provide a robust defense by ensuring that only authorized individuals have access to critical resources, minimizing the risk of data breaches and unauthorized access. Operational efficiency is equally crucial for organizations aiming to streamline their day-to-day processes. IAM programs contribute to efficiency by simplifying the management of user access and permissions.
Which Sector Is Anticipated To Receive Significant Investment Focus In IAM From Organizations?
Organizations are allocating resources in their yearly budgets to enhance:
- Privileged access management
- Identity management and governance
- Multi-factor authentication programs









.svg)














