Okta and KeyCloak are two leading IAM solutions. If you're deciding between these tools for your IAM needs, keep reading to learn about their key features and find out which one might be the better fit for your organization.
Choosing the right identity and access management (IAM) solution can be challenging. If you pick the wrong one, it can lead to security vulnerabilities, wasted resources, and frustrated users.
Imagine dealing with constant security breaches, inefficient access controls, and frequent downtime because your IAM solution isn’t up to the mark. These issues can slow down your team, disrupt business operations, and compromise sensitive data. The frustration of resolving these problems can consume valuable time and energy that could be better spent on strategic initiatives.
In this article, we will compare Okta vs Keycloak to get a better understanding of their strengths and weaknesses. This will help you choose an IAM solution that enhances security, improves efficiency, and provides a smoother user experience.
But before conducting a thorough comparison of Okta vs Keycloak based on different parameters, it's essential to have a comprehensive understanding of the capabilities of both tools. Let's begin by taking a brief look at their overall functionality.
What is Okta?
Okta offers a comprehensive identity and access management solution with many advanced features. With its comprehensive set of features, Okta is a powerful tool for IT teams looking to streamline the user’s identity and access management workflows while maintaining high security.
The various standout feature of Okta includes:
- Okta provides Single Sign-On (SSO) functionality, allowing users to access multiple apps using a single login credential securely. Also, IT teams can leverage Okta's SSO to simplify access management by centrally managing access to all their applications through a single dashboard. This ensures that users have the appropriate level of access without compromising security, making it an indispensable tool for any organization.
- Moreover, Okta offers Multi-Factor Authentication (MFA) capabilities, which add an extra layer of security to the authentication process. By requiring users to provide additional information beyond their usernames and passwords, IT teams can ensure that only authorized users access their organization's data and applications, even if their login credentials are compromised.
- Further, Okta's Adaptive Multi-Factor Authentication (AMFA) takes MFA a step further by using machine learning to analyze user behavior and determine the appropriate level of authentication required. For instance, when a user attempts to access an application from a new location or device, AMFA may require additional authentication measures to ensure the user is who they claim to be. This feature benefits IT teams by providing an additional layer of security without causing undue inconvenience to users.
What is Keycloak?
Keycloak is an open-source IAM tool that helps IT teams manage application user authentication and authorization. It provides a centralized authentication server that can be used by multiple applications and services, making it easier to manage access control across various systems.
Here are some of the key features of Keycloak that make it an essential tool for IT teams:
- Single Sign-On (SSO): Keycloak provides a single sign-on solution that allows users to log in once and access multiple applications without needing to enter their credentials repeatedly. This saves time and reduces the risk of users forgetting their passwords or getting locked out of their accounts.
- Multi-Factor Authentication (MFA): Keycloak supports multi-factor authentication, which adds an extra layer of security to user accounts. This feature helps IT teams to protect their applications from unauthorized access and potential security breaches.
- User Federation: Keycloak supports user federation, which allows IT teams to connect their existing user directories (such as Active Directory or LDAP) to Keycloak. This feature makes managing user accounts and access control easier across multiple systems.
- Role-Based Access Control (RBAC): Keycloak provides a flexible and scalable RBAC system that allows IT teams to manage access control based on user roles. This feature simplifies access management and ensures users have access to the resources they need to do their jobs.
- Open Standards: Keycloak is built on open standards such as OAuth2 and OpenID Connect, making integrating a wide range of applications and services easy. This feature ensures that IT teams can use Keycloak with their existing systems without the need for complex customization.
After gaining a comprehensive understanding of the functionality of both tools, the next step is to evaluate and do Okta vs Keycloak comparison based on various parameters. Doing so lets you determine which tool best fits your organization's unique requirements.
Okta’s Workforce Identity vs Keycloak: Comparison based on 5 features
Let us explore the different aspects for Okta vs Keycloak comparison that can aid in creating a clear differentiation between the two IAM tools.
1. Single Sign-on
Single sign-on (SSO) is an essential feature that allows users to access multiple applications with a single set of login credentials. It simplifies the login process for end-users while enhancing the security posture of an organization.
For IT teams, implementing SSO can be a game-changer as it reduces the workload of managing multiple login credentials for each user. Moreover, IT teams can enforce security policies across all applications, ensuring that users comply with the organization's security standards.
- One solution that is widely used by IT teams to offer SSO to their organizations is Okta. Okta’s Workforce Identity provides SSO capabilities to a range of applications, including cloud, on-premise, and mobile. It enables IT teams to centralize user authentication, access control, and user management.
With Okta, IT teams can offer a seamless user experience, as users only need to remember a single set of credentials to access all applications. Moreover, Okta provides robust security features, such as multi-factor authentication, to ensure that only authorized users can access the applications.
Okta's SSO capabilities also help IT teams improve compliance and auditing, as they can track and manage user access to applications from a centralized console. - Keycloak is an open-source identity and access management platform that provides SSO capabilities to organizations. Keycloak enables IT teams to authenticate and authorize users across different applications, including web, mobile, and API.
It also supports various protocols such as OAuth2, OpenID Connect, and SAML, making it easy to integrate with different applications.
Moreover, Keycloak provides a comprehensive set of features, such as user federation, authentication, authorization, and identity brokering, enabling IT teams to manage users across the entire organization.
2. Okta’s Identity Governance vs Keycloak's Adapters
IT security is a critical concern for IT teams in organizations of all sizes. With the increasing number of cyber threats, it has become important to protect sensitive data from being compromised.
Organizations that fail to adequately protect their IT infrastructure can suffer devastating consequences, including lost revenue, damage to their reputation, and legal liability. For this reason, IT teams are required to quickly detect and respond to potential threats, ensuring their organization's IT systems are secure.
- One solution that has gained popularity among organizations is Okta’s Identity Governance. With Okta's identity governance feature, IT teams can manage access to their applications, data, and systems in a secure and efficient way.
Okta's identity governance enables IT teams to manage access and permissions from a central location. This means that administrators can easily manage user access across different applications and systems, without having to manually update permissions for each individual user. This can save IT teams a significant amount of time and reduce the risk of errors and security breaches. - On the other hand, Keycloak offers adapters to help IT admins manage access control and authentication. These adapters are actually libraries that make it easy to secure an organization’s applications and services with Keycloak.
One of the key differences between the tools is that with Okta’s identity governance, you can improve your security posture while mitigating security risks and increasing efficiency, while this is less possible with Keycloak’s adapters.
3. Lifecycle management capabilities
Lifecycle management of users is critical for IT teams to ensure that employees have the necessary access to resources while also safeguarding sensitive company data.
But how do Okta and Keycloak differ in terms of offering user provisioning and de-provisioning? Let's explore Okta vs Keycloak.
- Okta offers a lifecycle management feature that allows IT teams to swiftly provision and de-provision user accounts across multiple applications, including cloud-hosted ones. This capability enables IT teams to automatically create new user accounts in multiple applications, saving time and minimizing the risk of errors.
With Okta's user provisioning capabilities, new employees can be up and running quickly without IT having to create accounts in each application manually. Furthermore, Okta ensures that new user accounts are created with the appropriate access levels and permissions, reducing the possibility of data breaches.
Also, Okta's user de-provisioning capabilities allow IT teams to revoke access to applications when employees leave the company easily. By automatically de-provisioning user accounts, IT teams can guarantee that former employees can no longer access sensitive company data. - On the contrary, Keycloak does not provide lifecycle management capabilities. However, Keycloak offers a user federation that enables the connection of existing user directories, including Active Directory or LDAP, to Keycloak. As a result, managing user accounts and access control across multiple systems is made easier for IT teams, streamlining the entire user management process.
4. Integrations with other tools
Integrating apps with existing systems is crucial for IT teams, especially concerning user provisioning. This process involves creating, managing, and deactivating user accounts and application access.
By integrating apps with existing systems, IT teams can automate user provisioning and de-provisioning, which saves time and effort while enhancing security measures and reducing the risk of human error.
- Okta is one of the leading providers of IAM solutions that offer integrations to organizations to streamline user provisioning.
Okta's integrations enable IT teams to automate creating and deactivation of user accounts across multiple applications and systems. This makes managing user access and ensuring compliance easier for organizations.
Moreover, Okta's integrations also facilitate the adoption of a zero-trust security model by providing granular access controls and real-time visibility into user access. With these integrations, IT teams can enhance their security measures and ensure that only authorized users access sensitive information, minimizing the risk of data breaches. - On the contrary, Keycloak's integration capabilities support a range of authentication protocols, including OpenID Connect, OAuth 2.0, and SAML. This allows IT teams to easily integrate Keycloak with various applications, including web applications, mobile apps, and APIs.
It supports user federation protocols, including LDAP, Active Directory, and Kerberos. This allows IT teams to easily integrate Keycloak with their existing directory services and user management systems, making managing user identities and access across the organization easier.
5. Pricing and reviews
Okta offers a flexible pricing model that is based on the number of users and the required features. There are three pricing tiers available, each designed to cater to specific business needs:
- Okta Starter: This plan is ideal for small businesses and provides basic IAM features such as SSO, MFA, and Universal Directory. The pricing for this plan starts at $2 per user per month.
- Okta Advanced: This plan suits businesses with advanced IAM requirements and includes API access management and lifecycle management features. The pricing for this plan starts at $5 per user per month.
- Okta Enterprise: This plan is designed for large organizations with complex IAM needs and includes advanced MFA, adaptive authentication, and security reporting features. The pricing for this plan is customized based on the organization's specific requirements.
Okta's pricing model allows organizations to choose the plan that suits their unique needs and budget. By offering different pricing tiers, Okta ensures that businesses of all sizes can benefit from their ULM and IAM solutions.
Okta has the plan to help them manage their users and secure their digital assets, whether a business is just starting or already an established enterprise.
In contrast, Keycloak is a free, open-source platform that can be downloaded and used for free by any organization. However, for organizations that require additional features, support, or hosting services, Keycloak offers several paid options for which prices are available based on the organization's requirements.
Customer ratings of Okta
- G2: 4.5/5
- Capterra: 4.7/5
Customer ratings of Keycloak
- G2: 4.2/5
Once you've learned the difference between Okta and Keycloak, you may better understand which tool is optimal for your IT teams to enhance identity and access management. However, there's another tool, Zluri, that you can consider for your growing enterprise.
Zluri - The Efficient Tool for Your Organization
So, what is Zluri, and how does it work? Here's a quick brief.
Managing provisioning and deprovisionning can be a daunting task for organizations, with various challenges to overcome. However, Zluri is here to simplify and streamline the process, ensuring that companies can manage their access control in a secure and efficient manner.
As a leading provider of SaaS management platform and user lifecycle management platform, Zluri provides a comprehensive access management solution that is highly scalable and incorporates cutting-edge security features such as multi-factor authentication, encryption, and audit trails.
With these features, IT admins can rest assured that the organization’s data is protected, and access to sensitive information is tightly controlled.
Zluri's platform offers automation capabilities for many manual tasks related to identity and access management, such as provisioning and de-provisioning. This frees up IT admins to focus on more important tasks, resulting in increased productivity and efficiency for the organization.
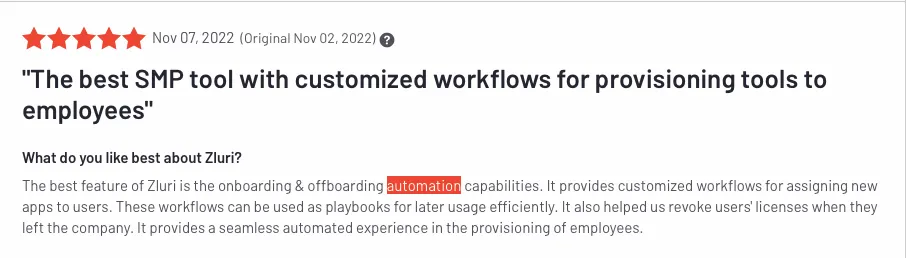
In addition, Zluri's powerful analytics and reporting capabilities allow IT admins to gain valuable insights into user behavior, enabling them to make informed decisions that improve security even further.
With Zluri, IT admins can enhance their identity and access management, improve security and productivity, and drive their business forward.
Schedule a demo with Zluri today to learn more about their identity and access management capabilities and how they can help your business achieve its goals.







.png)

.svg)














