Welcome to the world of role modeling. Where constant role iteration is a way to streamline IT operations. Just like a dynamic puzzle, it involves introducing new roles, modifying existing ones, and retiring outdated ones. All while navigating varying levels of complexity.
Before diving into the details, let's start at the first crucial checkpoint of any project, i.e., finding goals and scope.
As an IT manager, a series of questions will arise when you start with your role modeling journey. What do we aim to achieve in terms of compliance, security, and efficiency? Which applications, identities, and contexts fall within the scope of our endeavor? These initial considerations set the foundation for a well-defined roadmap.
You will explore the depths of organizational objectives, uncovering the challenges and opportunities that lie ahead. Further, we'll learn about aligning with compliance, enhancing security, and improving operational efficiency.
Now, since you have a brief overview of what we will be discussing, let's move ahead and start with the basics first; What is a role so that you can grasp the concept more efficiently?
What Is Role?
Basically, a role is a collection of policies, entitlements, and job-related details that define what a person can do within an organization. Furthermore, roles are like predefined categories that group together similar types of employees based on their job titles or responsibilities.
Doing so makes it easier for your IT team to manage access rights because your employees with similar roles can be assigned the same set of permissions to perform their daily IT tasks. This could include grouping application-specific entitlements like LDAP, application privileges, or email.
Additionally, there are a few most common types of roles, which are listed below:
- Application roles that grant access to a specific app or system.
- Technical roles are for employees who need to execute administrative tasks.
- Business roles are the roles related to work responsibilities or one's position.
However, these may seem like straightforward categories for role assignment; designing roles can be challenging, maintaining them can be even harder, and removing them can be the most difficult. This is because roles are interconnected with various permissions and entitlements that are intricately woven throughout the organization.
Before we move forward and learn more about how to manage the roles, let's first get familiar with role modeling. By learning about role modeling, you will be able to understand the concept in a better way.
What Is Role Modeling In Identity Security?
Role modeling plays a crucial role in establishing best practices for your IT team, particularly in terms of maintaining identities in alignment with the principle of \"least privilege\" to carry out job responsibilities. When implemented effectively, a role-based approach enables your IT team to efficiently grant access granting and governance processes.
However, if the role model is not well-developed, it can significantly delay an Identity Governance & Administration (IGA) project. Therefore, well-defined and properly maintained identity management modeling programs are essential for your IT team's ability to oversee who is doing what and why. Additionally, automating the process of granting and revoking default access rights for new joiners, movers, and leavers can bring significant efficiency gains.
Create, Modify, and Decommissioning Role
Your IT team will come across different phases while managing your employee's role, from creating new roles, changing or updating existing roles, and eliminating outdated ones.
While creating new roles, IT teams are encouraged to utilize both mining and design approaches. Mining tools play a significant role in analyzing and establishing roles and privileges based on real-time production entitlement data. These tools help determine roles that align with the organizational hierarchy.
However, it's crucial to note that simply using a mining tool doesn't automatically complete the role-modeling process. It must be integrated with processes aligning with your organization's unique business needs. This includes considerations such as compliance measures and ensuring that specific entitlements are aligned with specific job functions.
Various factors come into play to gather the necessary data for role crafting, such as identity types, templates, and organizational attributes. This data-gathering process helps in shaping and defining the roles. Once the roles are created, they undergo validation by relevant stakeholders. Finally, the roles are listed, along with potential assignment policies.
By carefully designing and validating roles, your IT team can establish a robust foundation for effective role management. This ensures that the right access is granted to individuals based on their responsibilities and helps maintain a secure and compliant environment.
What Are The Challenges Faced While Managing Roles?
Managing roles comes with its fair share of challenges. Here are some of the common hurdles organizations face:
- Complexity in Large Organizations: As organizations grow in size, managing roles becomes more complex. With diverse job functions and departments, defining and maintaining roles can be challenging for IT teams.
- Time-consuming Role Assignment: Assigning roles to individuals or multiple employees can be time-consuming when done manually. IT teams often need to review employee profiles, verify roles, and then grant access to SaaS apps and data accordingly.
- Tedious Role Monitoring: Roles are not static; they change over time. IT teams must continuously monitor and update roles, reassigning and revoking access as necessary. This can be a tedious task, especially when managing roles for multiple employees, and it may lead to human errors and role mismanagement.
- Governance and Compliance Challenges: Ensuring role governance and compliance with industry regulations and internal policies can be demanding. IT teams need to establish proper controls, conduct regular audits, and enforce segregation of duties to mitigate risks associated with excessive access or privilege abuse.
Organizations can adopt automated solutions, like Zluri, to overcome these challenges, that streamline role management processes. Automation reduces manual effort, speeds up role assignment, and simplifies monitoring and compliance tasks. By leveraging Zluri's features, your IT teams can efficiently manage roles, minimize errors, and ensure governance and compliance requirements are met properly.
So let's learn in detail about what Zluri is and how it works.
How Zluri Seamlessly Manages User Access According To Their Role?
If your IT team struggles with efficiently managing roles and access, Zluri is the solution you've been looking for. What is Zluri? Well, Zluri is an intelligent platform that is designed to simplify the entire process of role-based access management.
With Zluri, your IT team can seamlessly assign, modify, and revoke the right access for individuals based on their roles. This means granting the appropriate permissions to the right people at the right time, without the hassle of manual work or mistakes.
It also offers exquisite capabilities to enhance your access management experience. From managing user lifecycles, and making onboarding and offboarding smooth, to handling access requests and certifications, it provides a comprehensive solution for your role-based access needs.
To fully understand how Zluri helps streamline role-based access management, let's dive into the details of its capabilities.
- Provides Access To The Required SaaS Apps On Day 1 As Per The Employee Role
When an employee newly joins the organization, they are assigned roles and responsibilities based on their profile; verifying each individual identity and then assigning access as per their role can be a tedious task as well as time-consuming when done manually.
So what Zluri does is it ties new employee(s) data with digital identity, making it easier for your IT team to verify and assign them role-based access to applications, preventing excessive access or over-provisioning.
Furthermore, it takes a step further by enabling your IT team to create an onboarding workflow that can be customized. By creating this onboarding workflow, your IT team can seamlessly grant multiple employees necessary access with just a few clicks, saving time and increasing efficiency.
Moreover, with Zluri, new employees gain immediate access to all the required apps and data relevant to their roles. This means they can hit the ground running and start working from day one without any delays or access-related obstacles.
How to create onboarding workflows in Zluri?
Your IT team can easily create an onboarding workflow by following the given below steps:
- Step 1: From Zluri's main interface, click on the workflow module and select the onboarding option from the drop-down list. Proceed by clicking on New Workflow.

- Step 2: Select the user for the onboarding box will appear; from there, select the employee(s) whom you want to onboard. Also, you can search for a particular employee in the search bar. Once done selecting the employee, click on continue.

- Note: you can even select multiple employees; this helps onboard multiple new employees in one go
- Step 3: With its intelligent feature, Zluri would suggest some apps under recommended apps based on the employee's department, role, and seniority. Choose any of those, then execute the required action for the selected applications.

- Step 4: To execute certain actions, you need to click on Edit Task and enter the required details. Your team can schedule the actions to execute the workflow on the day of onboarding. To save the actions, click on Save Task, and the actions will automatically be saved.
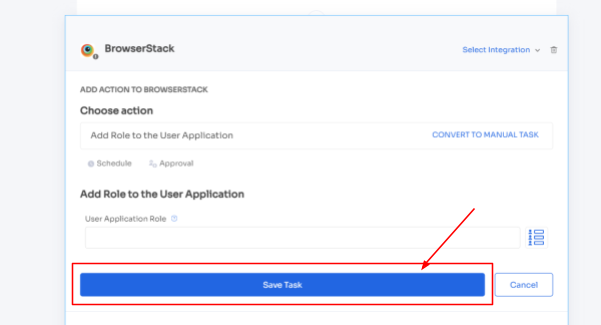
Also, your team can add your employees to channels or send an automated welcome greeting using Zluri's in-app suggestions. The actions can vary for different applications and are mentioned under recommended actions.

- Step 5: Finally, click on Save as Playbook to save the workflow. Then, you'll get a dialogue box with instructions to name the playbook. Add a name, proceed further by clicking on Save Playbook, and the onboarding workflow is ready.

Apart from that, Zluri offers automated playbooks (i.e. collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

Note- Apart from that, your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
- Seamlessly Modifyies Access Upon Role Change
Zluri is not restricted to that only; when employees undergo mid-lifecycle transition due to promotions, department changes, or geo-shift, they often require access to new applications. However, manually handling these access requests can take days, impacting productivity and jeopardizing the security of SaaS app data.
Zluri introduces a user-friendly self-service model known as the App Catalog & Access Request to streamline the approval process. The App Catalog & Access Request is a collection of pre-approved and verified SaaS applications managed by your IT admin. This empowers employees with the flexibility to choose the apps they need and gain access to them in no time.
All it takes for employees to initiate the process is submitting an access request. Zluri instantly notifies your IT admin, who can then verify the employee's identity and securely grant access with just a few clicks.
But how does your IT team stay updated on changes in employee roles? Zluri has a solution for that as well. Zluri automatically retrieves and displays updated employee data on a centralized dashboard by seamlessly integrating with your organization's HR system.
Now let’s see how your employees can raise an access request in EAS:
- Step 1: Your employees will receive an icon on the Zluri main interface's upper right corner; click on that, and a drop-down menu will appear; from there, click Switch to Employee View.

- Step 2: Overview dashboard will appear by default; now click on 'Request Access to an Application

- Step 3: Your employees will see a dialogue box where they need to enter the application name they require access to. Then, click on Continue.

- Step 4: Some applications will not be used in the organization. However, your employees can still request that application. Click on continue, and another dialogue box will appear, showing similar applications that are being used in the organization.

- If your employees want to opt for a similar application, they can simply click on the application or click on Ignore and Continue to proceed forward with your request.

- Step 5: Further, they have to fill in the required details like selecting the license plan, subscription duration, and description of why they need the application and attach supporting documents. Once filled, click on Confirm request.
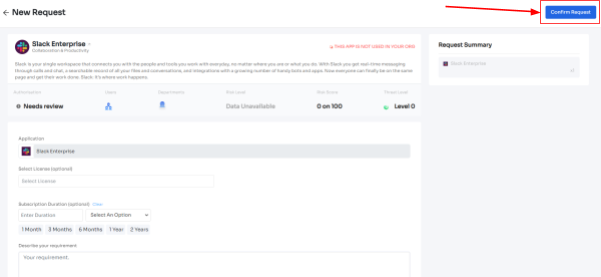
- Note: Additionally, if the request has been modified in any way or if one of the approvers suggests any substitutes for the application, your employee can check it in the \"Changelogs.\"

- And that's it. The app access request has been submitted.
- Revokes App Access When Employees Tenure Comes To An End
When employees depart from the organization due to resignation, termination, or sabbatical, it becomes crucial for your IT teams to ensure that their access to company SaaS app data is promptly revoked. However, manually managing this complicated process eats up your team’s productive time and can be prone to human errors.
So what Zluri does is it automates the deprovisioning process. Your IT teams can create and customize offboarding workflows that streamline the entire process. With just a few clicks, all access can be automatically revoked, and accounts can be suspended, leaving no room for lingering access with departing employees.
Further, by automating this deprovisioning process, your IT teams can effortlessly maintain the safety and security of your organization’s SaaS app data.
Now let’s see the steps to create an offboarding workflow:
- Step 1: From Zluri's main interface, click on the workflow module and select the offboarding option from the drop-down list. Proceed by clicking on New Workflow.
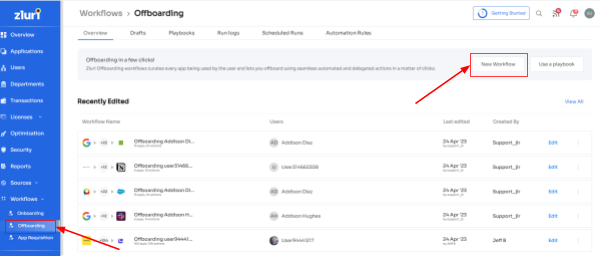
- Step 2: A popup labeled 'Select the user for offboarding' will appear. Select the employee(s) you want to offboard, or you can look for them in the 'search box. Click on continue after selecting the employee.

- Step 3: Your team will be able to view all the applications your employee can access. Now when you click on the app, Zluri will display some suggested actions under recommended actions. Select any of those or multiple actions, and then execute the required action for your chosen applications.
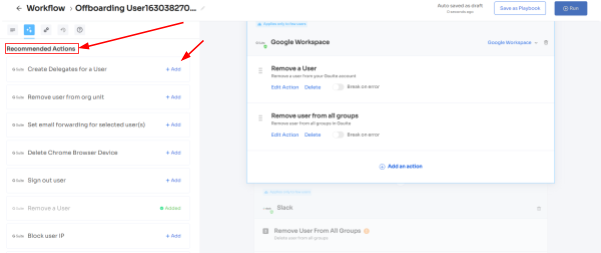
- Step 4: To add other actions, click Add an Action, fill in the required details, and proceed by clicking on Save Task; the actions will be saved.

- Step 5: Save the workflow by clicking Save as Playbook. A dialogue box will appear, instructing to name the playbook.
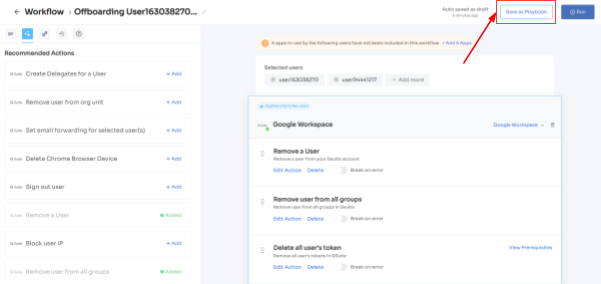
Add a name, click Save Playbook, and the offboarding workflow is ready.

Now how to monitor these access management processes effectively? With Zluri’s intuitive dashboard, your IT team can effortlessly track which employees have been granted access to specific applications, the level of permissions assigned, and recent access revocations. This centralized view enables quick and easy monitoring of access management activities, ensuring that the right level of access is maintained for each individual.
Zluri goes beyond basic monitoring capabilities. It also provides advanced detection of suspicious user activities. Zluri can identify unauthorized access attempts or unusual actions by analyzing user behavior and access patterns When such activities are detected, Zluri promptly alerts your IT team, empowering them to take immediate action to mitigate potential security risks.
By proactively identifying and responding to security incidents, your IT team can strengthen your organization's overall security posture and protect sensitive SaaS app data from potential breaches.
Govern Your User Access Seamlessly By Automating Access Certification
Now, we'll discuss an important aspect of access management: access reviewing. It's crucial to ensure that each user has the appropriate access to apps and data for security reasons. However, manually reviewing access can be time-consuming and require much effort.
So this is where Zluri comes in with its automated solutions. Zluri automates the entire access review process, gathering all the necessary user access data in one place. This makes the reviewing process much easier and more efficient for your team.
This was just an overview; Zluri is not only restricted to these few access review capabilities; it has more to offer, which is exclusive and sets it apart from the competitors. So, let’s explore them one by one.
- Unified Access Review
Zluri's unified access review feature helps your IT team easily see which users can access specific SaaS apps and data. Zluri gets this information from an access directory where all the user access data is stored in one central place.
Using this data, your IT team can check if users are admins or regular users and see which departments they belong to. This helps ensure users have the right access privileges based on their roles.
To keep everything running smoothly, Zluri's activity & alerts feature provides real-time updates on user activities and notifies IT teams about new logins. These insights help reviewers quickly and confidently make decisions during access reviews, ensuring the right people have the right access all the time.
- Automated Access Review
No more manual headaches with spreadsheets and JSONs! Zluri takes the hassle out of access reviews by automating the entire process. Just head to Zluri, create a certification, select the apps and users you want to review, and rest the reviewers will review and update you about the compilation via email.
So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let’s move ahead and see how it works.
- Once you gain access to contextual data through Zluri’s unified access feature, you can create access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take actions based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive) and more to make informed decisions during the review process such as whether the user can carry on with the existing access or need any modification.
With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
- Secure access orchestration/auto remediation
After completing the access review, the necessary changes will be implemented based on the actions set during certification creation. These actions, such as access modification or removal, are all part of a secure access orchestration process. This process ensures that access is managed securely and efficiently, protecting your organization's data and resources.
For example, when creating a new certification in Zluri, your team will encounter configuration actions to set up deprovisioning and modification playbooks. If the reviewers decline access permissions, the deprovisioning playbook will automatically run. The same goes for the modification playbook. In both cases, reviewers must provide reasons for declining or modifying access permissions.
It's important to note that these actions will happen automatically after the review is completed, which is why this process is called auto remediation.

Apart from that Zluri also offers integration features that are quite beneficial at the time of gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. By leveraging these integrations, it further enhances your access review process and strengthens the overall security posture of the organization.
For example, the top priority for the company is to review the Identity System and core applications, as they pose the highest risk. The Identity System, which stores crucial employee data, requires timely and thorough reviews to ensure security. So what Zluri does is it integrates with Salesforce, Okta, Azure, and others applications. Further, these integrations play a crucial role in gathering identity system and SaaS app data, providing valuable insights, and streamlining the review process.
Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as valuable documentation to share with auditors or keep as a reference for future reviews. And, audit trails act as roadmaps, showcasing the changes made during previous reviews.
For instance, if an employee's admin-level permissions were changed to user-level, it becomes essential to review and ensure that the access remains appropriate or if there were further changes back to admin. Understanding the reasons behind any upgrades is crucial for maintaining proper access control.
So Zluri automatically generates reports on such changes which further helps in the reviewing process.
So what are you waiting for? Book a demo now and check yourself how Zluri can be a game-changing solution for you.









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)