SCIM and SAML, both protocols are pivotal in managing identities and facilitating secure access within organizations. This article discusses these differences, helping you optimize your identity and access management strategies.
Managing user identities and access efficiently is a constant challenge for IT managers. The complexities involved in ensuring secure and seamless access to various systems can often feel overwhelming. This might lead to errors and consumes valuable time that could be spent on more strategic tasks.
Therefore, choosing the right protocol between SCIM (System for Cross-domain Identity Management) and SAML (Security Assertion Markup Language) is essential. By understanding the key differences between SCIM and SAML, you can make an informed decision that enhances both security and efficiency.
This article will break down the core aspects of SCIM and SAML, helping you identify the best fit for your organization’s needs.
But seeing the SCIM vs SAML comparison, let’s learn more about them.
What is SCIM?
SCIM, short for \"System for Cross-domain Identity Management,\" is an open standard protocol for automating user identity management tasks across various domains and systems. Its core purpose is simplifying the intricate task of overseeing user identities and access privileges across various applications, platforms, and services.
This protocol facilitates seamless automation within organizations. Through SCIM, entities can:
- Efficiently handle user provisioning and deprovisioning
- Synchronize user data between disparate systems
- Optimize the overall identity management process.
Essentially, SCIM streamlines the complexities inherent in maintaining and synchronizing user identities across multiple platforms, ensuring smooth operations and improved organization security protocols.
Benefits of SCIM
- Automated IT Operations: SCIM streamlines the arduous IT tasks associated with provisioning and maintaining accounts across diverse systems. It orchestrates the synchronization of accounts, groups, permissions, and entitlements directly from an organization's database, ensuring every unique system is promptly updated and accessible to employees.
- Effortless Management of Cloud-Based App Identities: As organizations increasingly adopt cloud-based applications and services, SCIM serves as a pivotal solution for seamlessly managing identities across these platforms. It provides a streamlined approach to handling user identities in the cloud ecosystem.
- Simplified Deployment: Implementing SCIM is straightforward. Integration involves deploying RESTful SCIM APIs for the utilized applications. These APIs facilitate essential calls for provisioning:
- Retrieving users based on the \"User Name\" filter
- User creation
- Retrieval and update of users by ID
- Group management (creation, update, deletion)
- Enhanced Security and Compliance: SCIM aids in maintaining secure access controls and compliance standards by ensuring accurate and up-to-date user provisioning and deprovisioning across systems. This helps organizations adhere to security protocols and regulatory requirements more effectively.
What is SAML?
SAML, or Security Assertion Markup Language, is a standardized protocol that facilitates the secure authentication and authorization data exchange. It primarily operates between a service provider (SP) and an identity provider (IdP).
The primary objective of SAML is to enable a streamlined process for Single Sign-On (SSO), easing user access to various applications and services across an organization.
At its core, SAML works through assertions—data statements that convey authenticated user information and their corresponding authorization levels.
These assertions are transmitted between the IdP and SP, enabling the granting of access to requested resources within the system. This framework ensures a secure, efficient, and standardized approach to managing user authentication and access control across multiple organizational platforms.
Benefits of SAML
- Single Sign-On (SSO): SAML-enabled SSO, allowing users to access multiple applications and services with a single set of credentials. This streamlines the login process and enhances user convenience while reducing password fatigue.
- Enhanced Security: SAML improves security by facilitating the exchange of authentication and authorization data through assertions. It minimizes the exposure of user credentials to multiple service providers, reducing the risk of unauthorized access and credential theft.
- Decoupling Directories: SAML operates without the need to synchronize and maintain user data across directories. This loose coupling allows for efficient authentication and authorization processes without the overhead of constant data synchronization between different systems.
- Cost Efficiency for Service Providers: Service providers benefit significantly from SAML as they are relieved of managing user account information across multiple services. The identity provider assumes this role, reducing operational costs associated with maintaining user data redundantly.
The Distinction Between SCIM vs SAML
Here are the key differentiating factors for SCIM vs SAML comparison:
1. Purpose
SCIM, the System for Cross-domain Identity Management, addresses the challenge of managing user identities scattered across diverse cloud-based applications and services. It aims to streamline the complexities tied to handling user information within interconnected systems.
As a protocol, SCIM automates and simplifies the laborious tasks associated with user identity management. It empowers your organization to govern user data efficiently by automating the processes of user addition, modification, or removal across multiple systems and platforms.
For example, suppose a new employee joins a company. SCIM ensures their information - such as user profiles, access permissions, or role assignments - is automatically synchronized across various applications used within the organization. If that employee's role changes or they leave the company, SCIM facilitates automatic updates or removals across all linked platforms, ensuring consistent and efficient user data management.
On the other hand, SAML, or Security Assertion Markup Language, helps in authentication and authorization within single sign-on frameworks, particularly in web-based applications. It is the conduit for securely validating and granting access to users across different platforms.
Its primary role is coordinating the secure exchange of authentication and authorization information between entities: identity providers (IdPs) responsible for user verification and service providers (SPs) furnishing access to various applications or services.
For instance, when users log into an application using SAML, they are authenticated by the identity provider (IdP) and gain access to various other connected applications without needing multiple logins. This streamlines the user experience across different platforms.
2. Functionality & Usage
Let's break down how each protocol functions and how SCIM vs SAML differ in usage.
How SCIM Works:
SCIM serves a different purpose than SAML. SCIM is designed to manage user identities across various applications and services automatically. It standardizes user information exchanges to simplify the provisioning and management of user accounts. Here's how it typically operates:
- An IT administrator sets up user identities in a central system (which acts as the identity provider).
- SCIM automatically pushes these user identity details to various third-party applications and services.
- When changes are made to a user's profile (like a job role update or termination), SCIM ensures these updates are automatically reflected across all connected services.
This automatic syncing saves significant time and reduces the potential for errors compared to manually updating user details in multiple systems.
How SAML works:
SAML is a standard protocol used to enable secure, single sign-on (SSO) for enterprise applications. SAML exchanges authentication and authorization data between an identity provider (IdP) and a service provider (SP).
Here's a simplified explanation of the process:
- When users attempt to access a service provider's application, they are redirected to an identity provider for authentication.
- The user logs in using their credentials stored at the identity provider.
- Upon successful authentication, the identity provider generates a SAML assertion (a package of information confirming the user's identity and permissions).
- The SAML assertion is sent back to the service provider through the user's browser.
- The service provider validates the SAML assertion and, if it checks out, grants the user access to the application.
This method removes the need for multiple passwords and logins, simplifying access management across different systems, enhancing security, and improving user experience.
While both SAML and SCIM deal with identity management, they serve different functions. SAML primarily focuses on authentication and secure single sign-on, ensuring that users are who they claim to be and have appropriate access rights. In contrast, SCIM is concerned with identity provisioning and management — it ensures that the correct user account information is created, updated, and removed as necessary across various systems.
3. Cloud Infrastructure
Managing access and identity verification efficiently is crucial for security and operational efficiency in cloud infrastructure and SaaS. Two key technologies that play pivotal roles in these areas are SAML and SCIM. Both serve important yet distinct functions in managing identity and access in cloud environments.
- SAML is primarily used for authentication processes. It allows users to log in to multiple software applications with one set of credentials (Single Sign-On—SSO). Once users authenticate themselves with their primary credentials, they can access all linked applications without needing to log in separately to each one.
For example, an IT manager might use their organization's SSO enabled by SAML to access various SaaS applications like email, CRM, and HR systems without signing into each one individually. - On the other hand, SCIM is designed to manage user identities across various systems. It focuses on automating the user lifecycle management—creation, updates, and deletion of user accounts—across multiple SaaS applications. SCIM provides a standardized way to sync identity data like user attributes and roles across different systems, reducing the manual effort needed to manage user accounts in each application separately.
For instance, when a new employee joins the company, SCIM can help automatically set up their accounts across all operational applications, such as email services, project management tools, and employee benefits portals.
Using SAML and SCIM together in a cloud infrastructure offers a comprehensive approach to identity and access management, streamlining user experience and administrative workflows. This integration enhances security by minimizing identity redundancy and errors. It also improves operational efficiency by reducing the time and resources spent on manual user management tasks.
4. Security Standards
When comparing security standards, SCIM and SAML each offer distinct functionalities within identity management.
- SCIM operates as an open-standard protocol for swift and secure identity management, enabling robust authentication across diverse applications.
Its framework relies on leveraging HTTP headers and standardized request bodies to transmit data, boasting key attributes such as user-friendly operations, rapid deployment, scalability, and seamless integration with multiple applications. - On the other hand, SAML specializes in facilitating authentication and authorization data exchange between involved parties. Its core strength lies in the secure encoding of identity data, which allows it to create streamlined single sign-on experiences.
Notably adaptable, SAML effortlessly integrates with a variety of applications. Its defining features include prioritizing secure data encryption and offering a reliable single sign-on mechanism.
For instance, consider a large corporation employing SCIM to swiftly manage user identities across its internal systems and cloud-based applications. Simultaneously, they employ SAML to enable employees to access these platforms seamlessly with a single login, ensuring secure access across diverse platforms. This blend of SCIM for identity management and SAML for authentication showcases their synergy in bolstering security and streamlining organizations' operations.
5. Data Safety
SCIM focuses on managing user identities across various domains or applications. It enables swift actions such as user addition and deletion, efficient password management, and facilitates seamless data import and export processes. This protocol empowers administrators with the tools needed for streamlined identity management, ensuring a more organized and responsive system for user identity maintenance.
On the other hand, SAML plays a significant role in bolstering data security by enabling single sign-on (SSO) capabilities across multiple applications. Its primary function is simplifying login processes, offering users a unified and secure access experience across various platforms. By minimizing the need for multiple logins and centralizing authentication, SAML significantly enhances data security by reducing potential vulnerabilities associated with multiple login points.
The key difference between SCIM and SAML regarding data safety lies in their specific focuses: SCIM streamlines the administrative aspects of identity management, while SAML simplifies user access across multiple applications. Together, they contribute to a more robust and comprehensive approach to data safety and user identity management within an organization.
SCIM vs SAML Differentiation Table
Here's a table highlighting the distinctions of SCIM vs SAML across various aspects:
Each protocol serves distinct functions within identity and access management, offering specialized functionalities that cater to different aspects of secure authentication, user provisioning, and centralized identity governance.
Integrating SCIM and SAML can enhance overall data safety and streamline identity management processes within an organization by leveraging their respective strengths in managing user identities and ensuring secure access experiences.
While SCIM and SAML serve specific purposes within identity and access management, an access management platform acts as a comprehensive solution that integrates various protocols, including SCIM and SAML, to address diverse identity-related challenges centrally. One such solution is Zluri.
How Zluri Helps You Manage App Access Efficiently?
Zluri simplifies the complex task of access management by offering a robust access management solution. Firstly, Zluri provides API-based integrations that allow your team to seamlessly connect with a wide array of applications, both SCIM and non-SCIM apps.
By leveraging the integration capability, you can automate the provisioning process, saving time and reducing the potential for human error. Let’s see how.
- Zero Touch Provisioning and Secure Deprovisioning
Zluri’s zero-touch provisioning feature streamlines the onboarding process for new users. Once set up, the system automatically assigns and configures the necessary applications and permissions based on predefined rules, making the entire process effortless and error-free.
Conversely, secure deprovisioning ensures that when employees leave the company or switch roles, their access to sensitive information and applications is promptly and safely revoked, mitigating any risk of data breaches.
- Extensive Access Control Beyond SCIM
While SCIM provides a standard for automating the exchange of user identity information between IT systems, Zluri goes a step further. It ensures that you can grant or revoke access for SCIM-compliant apps and those that do not support SCIM. This broad capability ensures y
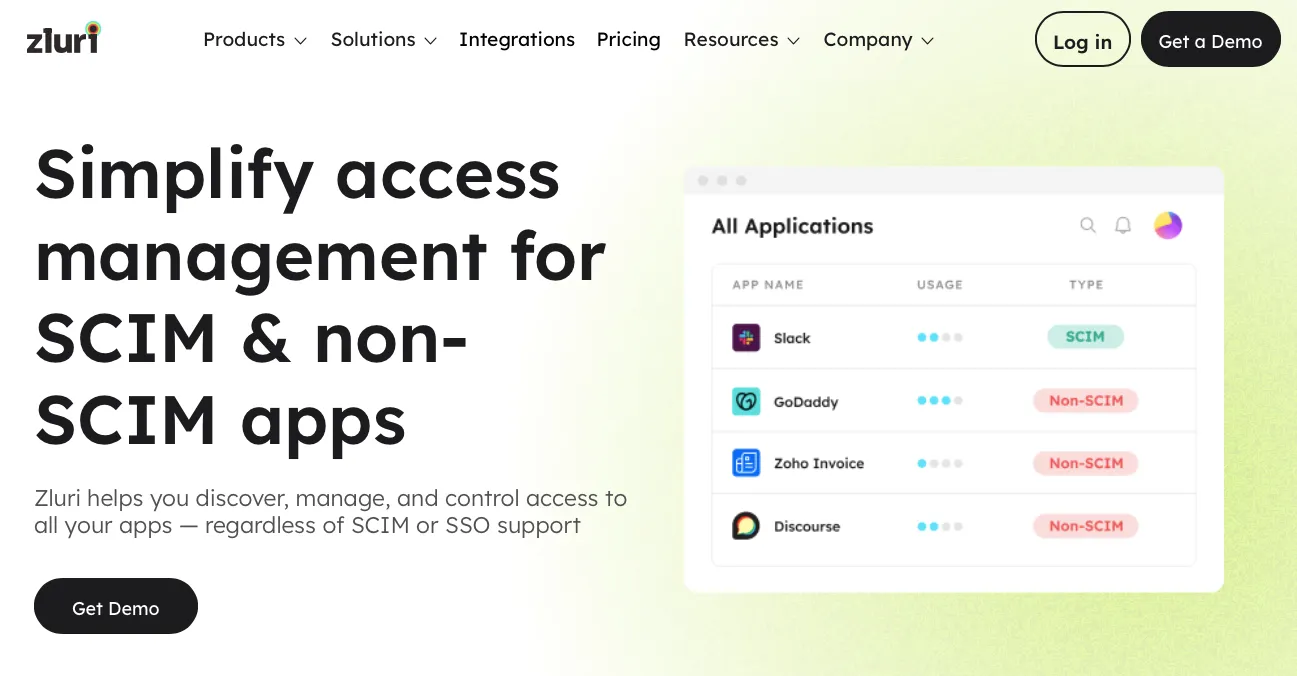
ou can manage access rights across all your software tools, maintaining security and compliance without additional overhead.
- Automated Provisioning with Policies and Workflows
Zluri goes beyond basic access management by offering automated user provisioning through customizable policies and workflows. You can define specific rules and conditions for access provisioning, allowing Zluri to automate the entire process based on predefined criteria. This automation streamlines operations, reduces administrative overhead, and ensures compliance with organizational policies.
- Privileged Access Management
Managing privileged access is crucial in safeguarding your company’s critical systems and data. Zluri offers robust solutions to control and monitor privileged accounts. This helps prevent unauthorized access and ensures all actions performed with elevated rights are logged and auditable. By efficiently managing these sensitive permissions, Zluri helps reinforce your organization’s security framework.
Book a demo today!
Frequently Asked Questions (FAQs)
Is SCIM the same as SSO?
SCIM and SSO are distinct yet complementary technologies designed to streamline identity and access management in different ways. SCIM primarily focuses on automating the provisioning and management of user identities across various applications, ensuring that user data is consistent and up-to-date.
On the other hand, SSO simplifies the user experience by enabling individuals to access multiple applications with a single set of credentials, enhancing both security and convenience. Together, SCIM enhances the effectiveness of SSO by ensuring that user identity information is accurately synchronized across all platforms, thereby supporting a seamless authentication process.
Is SCIM an authentication?
The System for Cross-domain Identity Management (SCIM) is a protocol suite designed to automate data provisioning across various applications. It leverages JSON, REST, and various authentication methods to streamline user data management, ensuring seamless integration and maintenance of user identities across multiple platforms.









.svg)














