Cyber attackers often exploit weaknesses in an organization's security setup to compromise critical data. So, to prevent such attacks, it's crucial to identify and address these vulnerabilities beforehand. But how can that be done? The solution is vulnerability management. But what is vulnerability management? In this article, we'll explore this concept thoroughly.
Often, IT teams unknowingly overlook minute security flaws in systems, apps, devices, and networks. Unfortunately, these overlooked flaws become an opportunity for hackers to compromise an organization's security system.
Now, you may think conducting a risk assessment can do the work. But these vulnerabilities are so minute and unnoticeable that simply running an assessment won't be enough to completely detect them. Instead, one needs to have a proper process in place, such as vulnerability management. But what is vulnerability management?
What Is Vulnerability Management?
Vulnerability management is a continuous process of identifying, assessing, remediating, reporting, and monitoring security vulnerabilities (weaknesses) in SaaS apps, systems, and endpoints (any device that connects to a network). These vulnerabilities can be of different types, such as:
- Cloud Vulnerability
Cloud vulnerabilities refer to the weaknesses or flaws within cloud systems that can be exploited to compromise security or data integrity. These vulnerabilities arise from various factors, including improper firewall settings, substandard patching on the cloud server, or poorly configured servers.
- Application Vulnerability
These are known software bugs that can be used to break into a network's security. If the software isn't updated, it can create a gap that cyber attackers can exploit. Further, they can compromise network security and target the system's hardware and firmware.
- Configuration Errors
When network systems aren't set up correctly, they can become vulnerable to cyber-attacks. Simple issues, like keeping a system's default password or setting a network to public and unprotected, can provide easy access for attackers.
- Other Weaknesses
Vulnerabilities can still exist even if the software is updated and patched with no known errors. These might include not encrypting stored data or importing data from an insecure external source. Also, many companies prioritize security but often overlook the risk of their employees unintentionally introducing external threats.
Note: You can implement vulnerability management alongside other security strategies to effectively detect, prioritize, and address potential threats, which will help minimize the attack surface.
However, you also need to be aware of its key components to better understand vulnerability management. What are these core components?
Key Components Of Vulnerability Management

Listed below are the three key components of vulnerability management. Each component plays a particular role in identifying, assessing, and addressing vulnerabilities within a system.
1: Vulnerability Assessment
Vulnerability assessment is a process that looks for security weaknesses in systems like operating systems, software, and hardware. IT teams conduct these assessments and take preventive measures to address the identified vulnerabilities.
Note: Vulnerability assessment is repeated to check for vulnerabilities in the system and ensure its security is maintained over time.
2: Vulnerability Scanning
Vulnerability scanning checks internal and external assets to find potential weaknesses, whether on-premise, in the cloud, or a mix of both. This scanning provides information that helps your team to evaluate the security of devices connected to an organization's networks.
Furthermore, there are different types of vulnerability scans; you can choose any of them depending on your specific needs and requirements.
- External: Look for weaknesses from outside the organization's network.
- Internal: Assesses vulnerabilities within the organization's internal network.
- Authorized: Conducted with permission, targeting specific systems or networks.
- Comprehensive: Thoroughly scans all aspects of the system for vulnerabilities.
- Limited: Focuses on specific areas or aspects of the system.
3: Penetration Testing
Penetration testing, also called ethical hacking, is another important component of vulnerability management. Penetration testing is generally conducted manually (one can use penetration software as well) by a security expert to find and exploit specific vulnerabilities in a system.
Now that you are familiar with vulnerability management and its key components, let's review the stages of the vulnerability management lifecycle. With these insights, you will gain a better understanding of how this process works.
Vulnerability Management Lifecycle: 5 Key Phases
Vulnerability management is not a one-time task but an ongoing process that is repeated in cycles to ensure the ongoing security of an organization's systems and networks. It consists of 5 key stages in which IT teams need to perform different tasks:

Phase 1: Discover Vulnerabilities
This stage focuses on vulnerability assessment, which involves checking an organization's IT assets for known and potential vulnerabilities.
IT teams can use automated vulnerability scanner software to do this. Some scanners conduct regular, thorough network scans on a schedule, while others gather data directly from devices using installed agents. Additionally, security teams conduct occasional manual vulnerability assessments and find vulnerabilities that automated scanners may miss.
Phase 2: Categorization & Prioritization
Once vulnerabilities are found, they are sorted into different types, like device misconfigurations, sensitive data exposures, or encryption issues. Then, they're ranked based on their criticality. This helps estimate how severe each vulnerability is, how likely it is to be exploited, and the chances of an attack happening.
At this stage, the IT team can use threat intelligence sources such as the Common Vulnerability Scoring System (CVSS), which rates known vulnerabilities on a scale from 0 to 10.
Other popular sources include MITRE's list of Common Vulnerabilities and Exposures (CVEs) and NIST's National Vulnerability Database (NVD). These sources help determine how serious each vulnerability is and how urgently it needs to be addressed.
Phase 3: Resolution
Once vulnerabilities are ranked in order of importance, IT teams can address them in one of three ways:
- Remediation: This involves fully fixing a vulnerability so it can't be exploited anymore. For example, your team can install a patch to fix a software bug or eliminate/retire a vulnerable asset.
- Mitigation: This involves making a vulnerability harder to exploit and reducing the impact of exploitation without completely removing the vulnerability.
For instance, separating a vulnerable device from the rest of the network makes it more difficult for attackers to exploit it.
Note: Mitigation is often used when a patch or other form of remediation isn't available yet. - Acceptance: This means choosing to leave a vulnerability as it is without addressing it. This is often done when the vulnerability has low criticality scores, meaning the chances of it causing significant damage are less or nonexistent.
Phase 4: Reassessment
After addressing vulnerabilities, IT teams need to perform vulnerability assessments again to ensure that their mitigation or remediation actions successfully addressed the vulnerabilities, were effective, and did not introduce new vulnerabilities.
Phase 5: Reporting
IT teams can use vulnerability management platforms that offer dashboards for reporting key metrics such as mean time to respond (MTTR) and mean time to detect (MTTD). These reporting features will enable teams to set a standard for continuous vulnerability management efforts and track the effectiveness of the program over time.
But how is vulnerability management going to be beneficial for an organization? Let's find out.
Benefits Of Implementing Vulnerability Management
Here are some benefits of implementing vulnerability management within your organization:

1: Proactively Detects and Prevents Potential Threats & Vulnerabilities
Vulnerability management helps your team detect and address security issues before they turn into major cybersecurity problems. This can minimize data breaches and other incidents that could harm the organization's reputation and financial health.
2: Helps Meet Security Regulatory Compliance
Vulnerability management strengthens an organization's security by identifying and addressing weaknesses in its systems. This helps ensure that the organization meets the requirements set by security standards and regulations, which are created to protect critical data from unauthorized access or breaches.
3: Strengthens Security Posture
Vulnerability management involves conducting regular scans to identify weaknesses in systems. If any vulnerabilities are discovered during these scans or assessments, your team can swiftly address them. By implementing this proactive measure, you can strengthen your security posture and reduce the likelihood of attackers exploiting these weaknesses and gaining unauthorized access to systems.
4: Reduces Operational Disruption
Vulnerability management helps reduce the likelihood of cyber attacks that could disrupt operations or compromise data through regular scanning and patching. This allows organizations to minimize system downtime and protect their critical data.
Now that you are familiar with the benefits, you also need to understand that vulnerability management has certain challenges. What are these challenges?
Challenges In Vulnerability Management
Listed below are a few challenges that you may encounter during vulnerability management:
- Managing Numerous Vulnerabilities: Most large organizations extensively use SaaS applications, which also means there are many potential vulnerabilities to monitor, and not all of them pose the same level of risk.
Also, handling multiple vulnerabilities across numerous assets in a distributed network is challenging, especially if you lack the proper resources to track and mitigate them.
- Limited Time and Resources: Organizations often face constraints in terms of time and resources, making it difficult to effectively prioritize vulnerabilities. This limitation, coupled with a lack of expertise in vulnerability prioritization, can impact the vulnerability management process.
- Fragmented Toolset: Using multiple tools for vulnerability assessment and patch management can create confusion, as it becomes unclear which tools effectively handle vulnerabilities and which do not. This can lead to challenges in coordinating and streamlining the vulnerability management process.
- Overlooked Misconfigurations: Hackers can exploit overlooked misconfigurations to access networks, move laterally, and compromise other machines.
However, these challenges can be effectively managed if you focus on working with the right tools, like deploy, a centralized vulnerability management tool that handles both assessment and patch management processes, reducing confusion and enhancing efficiency. You can also follow best practices to ensure that you have effectively implemented vulnerability management.
But what are these best practices? Let's find out.
Vulnerability Management Best Practices
Below are some of the best practices that you can follow to ensure effective implementation of vulnerability management:
1: Define Your Objectives
The main goal of vulnerability management is to find and fix vulnerabilities before they can be exploited. However, it's also important to identify any secondary goals that can enhance the effectiveness of the process. These might include increasing the frequency of scans/risk assessments or reducing the time it takes to fix identified vulnerabilities.
2: Keep Track Of All Assets & Networks
Sometimes, old or forgotten pieces of hardware or software, which may have been deployed without the knowledge or oversight of the IT team, can be easy targets for attackers. Knowing everything that's part of your organization's tech setup is important to stay safe. By thoroughly checking and scanning for vulnerabilities on all devices and systems, you can spot and fix any weak spots before they cause trouble. This helps keep your organization's data and systems safe from cyber threats.
3: Create A Vulnerability Management Policy
Vulnerability management policy provides clear guidelines and procedures for identifying, assessing, and addressing vulnerabilities within an organization. By having a defined policy in place, organizations can ensure effectiveness in their approach to vulnerability management. Additionally, a well-designed policy helps prioritize remediation efforts based on the severity of vulnerabilities and reduces the likelihood of security breaches or incidents.
4: Define Roles Within Your Organization
For vulnerability management to work well, it's crucial to have all stakeholders involved and their roles clearly defined. Depending on the organization's structure, roles can be divided into monitors, resolvers, and authorizers.
- Monitors: Assess the severity and risk of vulnerabilities, document their findings, and alert the resolvers.
- Resolvers: Find and apply patches for known issues or create mitigation solutions when patches aren't available or convenient.
- Authorizers: Oversee system vulnerabilities and make strategic changes to address current and future threats.
5: Assess the Effectiveness of Your Vulnerability Management Program
Ongoing vulnerability management processes give a clear, up-to-date view of the organization's security status. Continuously assessing these processes helps identify what works well and what needs improvement. Remember, while the basic steps of vulnerability management are similar across organizations, it's important to customize the approach to fit your specific needs for better accuracy, clarity, and remediation.
After going through the vulnerability management stages and best practices, you may have realized that managing vulnerabilities is not that easy. However, these vulnerabilities can be effectively managed by using an effective platform like Zluri. What is Zluri? How does it work? Let's find out.
Zluri: Your All-In-One Solution To Effectively Manage Vulnerabilities
Zluri offers a SaaS management solution that streamlines vulnerability management by providing your team with tools to effectively identify, assess, and remediate security risks associated with your tech stack. How does it do that? What features does it offer?

- Discovers Applications
Without knowing what all applications are being used within the organization, tracking vulnerabilities associated with them becomes nearly impossible. However, with Zluri’s SMP, you gain complete visibility into your SaaS stack.
How? It offers discovery engine features that use different discovery methods to detect all the organization's applications. These methods include browser agents, IDPs & SSOs, desktop agents, direct integrations, active directories, HRMS platforms, MDM platforms, finance tools, and CASB platforms.
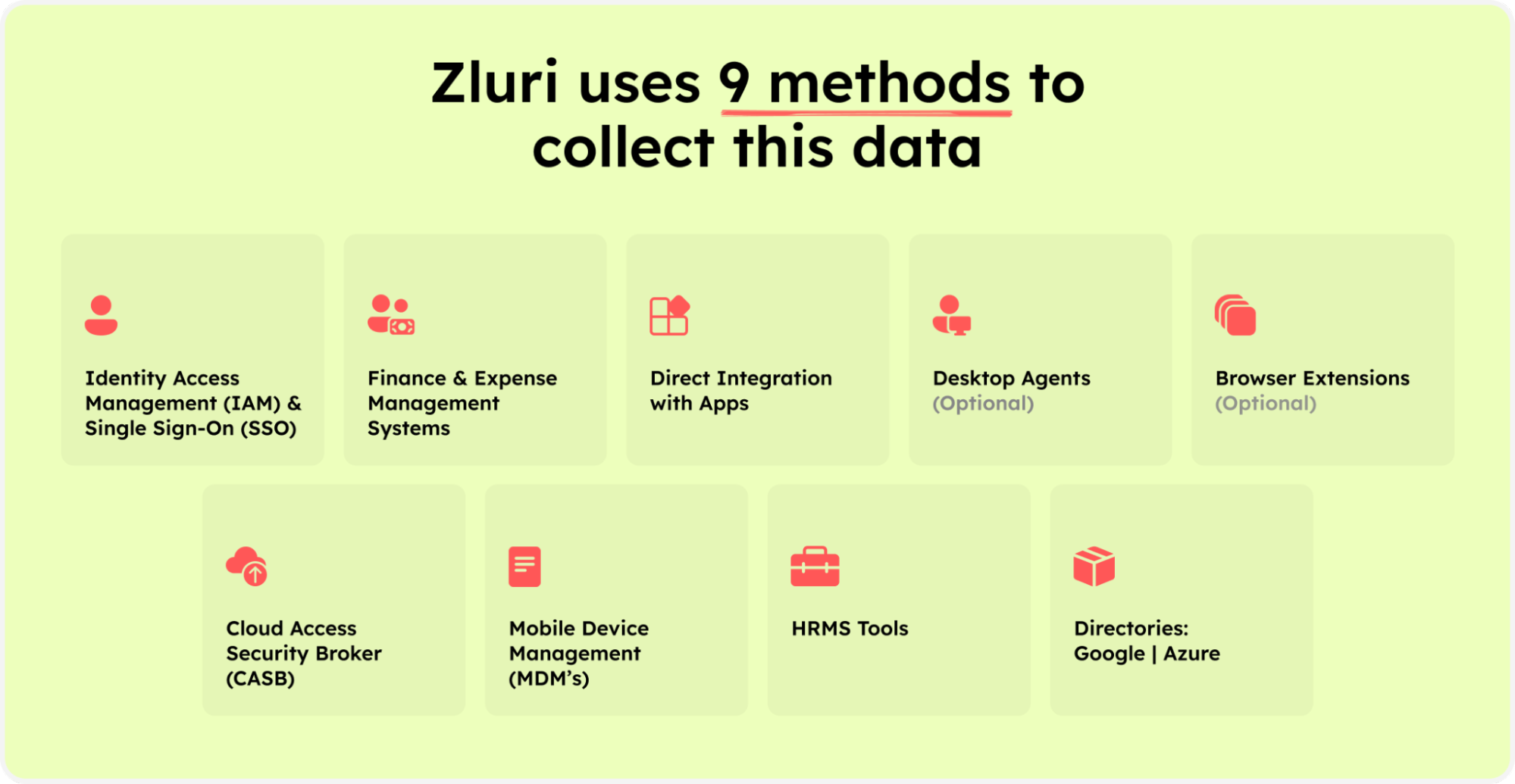
Zluri’s nine discovery methods
- Views Risk Score & Threat Score Associated With Each Application
Zluri SMP provides a centralized dashboard to view all the details of an app being used within the organization. However, you can check an application's security and compliance details for vulnerability management. These details include risk score, threat score, and compliance (the app complies with all regulatory standards).

That’s not all; it even categorizes apps with high-risk levels and threat scores under critical applications. This feature ensures that your team can give these apps the extra attention they need and closely monitor who is accessing them.

This is about identifying risky applications that can cause potential breaches. However, Zluri takes a step further to mitigate vulnerabilities by offering access management solutions.
- Mitigates Mismanagement Of Access
Zluri's access management solution ensures that only the right authorized users gain access to apps and data. How does it do that? It helps your team enforce various access controls like RBAC, JIT, PoLP, and SoD, just to make sure users have access that is required for their job and nothing beyond that. This approach effectively mitigates access gaps and enhances security.
- Continuously Monitors Access Rights
Zluri's access management helps your team continuously monitor employees' access rights. By doing so, they can easily detect if any employee is holding unauthorized or excessive access. Your team can then take preventative measures like restricting or revoking employees' access to prevent unauthorized access attempts.
To learn more about Zluri, book a demo now.
Protect Your Critical Assets From Exploits By Implementing Vulnerability Management
In conclusion, implementing a robust vulnerability management strategy is essential for any organization. This involves regular assessments, thorough scanning, and testing to detect and address potential security weaknesses. By doing so, you not only strengthen your security controls and meet regulatory requirements but also safeguard your organization's IT assets from potential exploits and minimize operational disruptions.
Furthermore, to ensure effective vulnerability management implementation, it is crucial to follow best practices. These include keeping track of all IT assets, defining objectives and roles, and continually reassessing the effectiveness of vulnerability programs. Additionally, leveraging effective tools like Zluri can significantly enhance your vulnerability management efforts.
FAQs
1. What Is A Vulnerability Management Program?
A vulnerability management program is a company's systematic approach to identifying, monitoring, and addressing vulnerabilities. This program outlines the processes, structure, and scope of vulnerability management, along with clearly defined roles and responsibilities for those managing the program and all employees within the organization.
2. What Is Exploits?
An exploit is a piece of code or software that hackers use to take advantage of vulnerabilities in computer systems, networks, or software applications. It allows them to gain unauthorized access, steal information, disrupt operations, or perform other malicious activities.
3. What Is The Difference Between Vulnerabilities, Threats, And Risks?
Vulnerabilities are weaknesses or flaws in systems, networks, or applications that attackers can exploit to compromise security. On the other hand, threats are potential events or incidents that can cause harm, such as cyberattacks or malicious activities. Risks occur from the combination of vulnerabilities and threats, reflecting the likelihood and impact of potential security breaches.







.png)

.svg)














