As an IT manager, you understand the crucial role of identity and access management in securing access to apps and systems. Serving as a digital fortress, IAM guarantees that only authorized users can access your systems and data. To achieve this, selecting the appropriate identity and access management tools is imperative for your organization's cybersecurity.
Organizations that prioritize security without compromising user experience actively pursue reliable and user-friendly identity and access management (IAM) tools to attain their goals. These tools streamline tasks like user provisioning and access control, enhancing overall security and facilitating smooth onboarding and offboarding processes.
The post explores some of the best identity and access management tools, with the goal of aiding IT teams in securing data and ensuring a seamless experience for users.
What are Identity and Access Management Tools?
IAM (Identity and Access Management) is a pivotal component in ensuring the security of digital environments by managing and controlling access to resources. IAM tools are designed to ensure secure and efficient management of user identities and their access to various systems, applications, and resources within an organization.
Operating throughout the entire user lifecycle, IAM tools commence with authentication, where users verify their identity through diverse methods like passwords, biometrics, or multi-factor authentication. Once authenticated, these tools meticulously govern user authorization, precisely dictating access to resources based on roles and permissions. Further, automated onboarding and offboarding processes streamline account provisioning and de-provisioning as employees join or depart.
In short, IAM tools orchestrate authentication, authorization, and user lifecycle management to safeguard digital assets, optimize access control, and elevate cybersecurity within an organization.
Core Capabilities of Identity and Access Management Tools
Identity and access management (IAM) tools are essential to fortifying digital security. From seamless authentication to centralized access control, these core features ensure secure and efficient management of digital identities and permissions.
- Authentication Excellence
IAM tools deliver robust authentication mechanisms to verify the identity of users accessing systems, applications, and data. This encompasses a range of authentication factors, including passwords, biometrics, smart cards, and multi-factor authentication (MFA), ensuring a secure and reliable access control process.
- Streamlined Single Sign-On (SSO) Advancement
IAM platforms revolutionize application access by empowering users to sign in with a single set of credentials. SSO facilitates seamless one-click access across all applications and services, prioritizing user convenience and eliminating the complexities associated with managing multiple accounts and passwords.
- Multi-Factor Authentication (MFA) Mastery
IAM tools further elevate security measures by mandating users present two or more authentication methods. MFA introduces an additional layer of protection beyond traditional username/password, incorporating evidence from categories such as something you know, have, and are—this includes biometrics, SMS codes, or physical tokens, bolstering overall authentication robustness.
- Directory Prowess
IAM tools excel in securing and efficiently managing identity and profile data at scale. Serving as a versatile and secure database, IAM directories store customer, employee, and partner identities. This ensures the protection of sensitive data, including passwords and personally identifiable information (PII), while accommodating unstructured data and facilitating seamless access to applications.
- Web/API Access Centralization
IAM tools specialize in access security and centralize and enforce secure access management for applications and APIs. These tools authorize authenticated users by leveraging identity attributes and contextual data, granting access only to relevant apps, resources, and APIs. This approach enhances overall security through the centralized management of policies based on user and device context.
Now, let's explore how these fundamental capabilities contribute to valuable benefits.
Key Benefits Of Employing IAM Tools
Identity and Access Management tools provide a spectrum of key benefits, enhancing overall security and operational efficiency within organizations:
- Enhanced Security: IAM solutions bolster cybersecurity by ensuring that only authorized users have access to sensitive resources. Its features such as multi-factor authentication, robust authorization controls, and continuous monitoring contribute to a more resilient digital security framework.
- Regulatory Compliance: IAM platforms help organizations adhere to regulatory requirements by enforcing access policies, tracking user activities, and maintaining audit trails. This ensures compliance with industry-specific regulations and data protection laws.
- Streamlined User Onboarding and Offboarding: Further, these tools automate the process of user provisioning and deprovisioning, simplifying user onboarding for new employees and enhancing security during offboarding. This improves operational efficiency and reduces the risk of unauthorized access.
- Single Sign-On (SSO) Convenience: Its SSO functionality reduces the burden on users by allowing them to access multiple applications with a single set of credentials. This not only enhances user convenience but also minimizes the likelihood of weak password practices.
- Centralized Access Management: IAM platforms facilitates centralized access management by providing a unified platform for managing access to various resources. This centralized control allows organizations to enforce consistent security policies and quickly respond to changes in user roles or permissions.
- Improved Productivity: By streamlining authentication processes and minimizing password-related challenges, IAM tools contribute to increased user productivity. Users can seamlessly access the resources they need without unnecessary authentication hurdles.
- Reduced Security Risks: IAM tools help organizations adopt the principle of least privilege, ensuring that users only have access to the resources necessary for their roles. This minimizes the potential impact of security breaches and reduces the attack surface.
- Enhanced User Experience: Through features like SSO and user self-service portals, IAM tools contribute to a positive user experience. Users can access resources effortlessly, reset passwords, and manage their profiles independently, reducing dependency on IT support.
- Audit and Reporting Capabilities: IAM tools provide robust audit trails and reporting functionalities, allowing organizations to monitor user activities, track changes, and generate compliance reports. This helps in identifying and addressing security incidents promptly.
- Scalability and Flexibility: Lastly, IAM solutions are designed to scale with the growth of an organization. They offer flexibility in managing diverse user identities, accommodating changes in user roles, and adapting to evolving security requirements.
Also Read: To know more about IAM, you can go through IAM challenges, IAM framework, IAM Best Practices.
IAM tools are instrumental in strengthening the security posture, guaranteeing regulatory compliance, and streamlining user access management, ultimately contributing to the overall resilience and efficiency of an organization's digital ecosystem.
13 Best Identity and Access Management Tools
In an era where safeguarding digital assets is paramount, identity and access management solutions stand out for their robust features, regulatory compliance, and ability to fortify organizations' digital defenses. This section explores the wide range of identity and access management tools suitable for your organization.
1. Zluri
Zluri presents a unified access management platform that manages and monitors access rights throughout your organization. IT teams can effortlessly assign, modify, or revoke access to applications and resources through a singular, user-friendly dashboard. This centralized approach gives your team unparalleled control over users accessing critical systems and sensitive data.
Integrating seamlessly with identity providers, HRMS, SCIM and non-SCIM apps, and your ITSM tools, Zluri seamlessly embeds itself into your tech ecosystem. Once integrated, it unveils complete access details across your organization, identifying all internal and external users along with their application access and entitlements or access levels. Note: It is backed by Kuppingercole's research and analysis report, that Zluri provides accurate and up-to-date data about which applications users have access to, and what level of access they have.
In fact, Zluri has been named in the Gartner® Report: Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation. Download now!
Gartner, Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation, Rebecca Archambault, 8 October 2025
Gartner is a trademark of Gartner, Inc. and/or its affiliates.
Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.
Key Features
- Zero-Touch Provisioning

Zluri revolutionizes the onboarding experience by offering zero-touch provisioning. It offers seamless onboarding automation without replacing your Single Sign-On (SSO) provider. It integrates with your identity provider, HRMS, SSO, and tech stack, ensuring efficient onboarding. For instance, when a new employee is marked for onboarding in HRMS, Zluri automatically provisions access to the required applications.
Unlike existing SSO or LCM tools, Zluri provides flexibility in setting onboarding conditions and rules. For example, you can delay access until the employee's actual joining date. This capability enhances employee experience and saves time for IT teams.
Further, Zluri offers user-friendly onboarding triggers based on specific conditions, such as user data from SSO. You can define actions such as approval routing or access requests, streamlining the process with automation rules and notifications.
Also Read: To know more about provisioning, you can read User Provisioning, User Provisioning Best Practices, User Provisioning Workflows.

It also allows easy customization of playbooks for different onboarding scenarios or roles. You can effortlessly create, edit, and duplicate playbooks, gain insights into run statuses and configure automation rules for a seamless process.
This advanced feature makes granting new users access to necessary applications and resources seamless with minimal or no manual intervention.
- Secure User Offboarding
Thanks to Zluri's secure user offboarding feature, security remains paramount, even during user departures. It simplifies employee offboarding by automating user deprovisioning.

Unlike traditional methods that lack complete visibility, Zluri automatically identifies all apps accessed by the departing employee. With pre-populated playbooks, you can seamlessly transfer data, set up email forwarding, and revoke access.
Additionally, Zluri allows for customized offboarding policies triggered by user status changes in SSO, ensuring efficient and secure offboarding workflows.
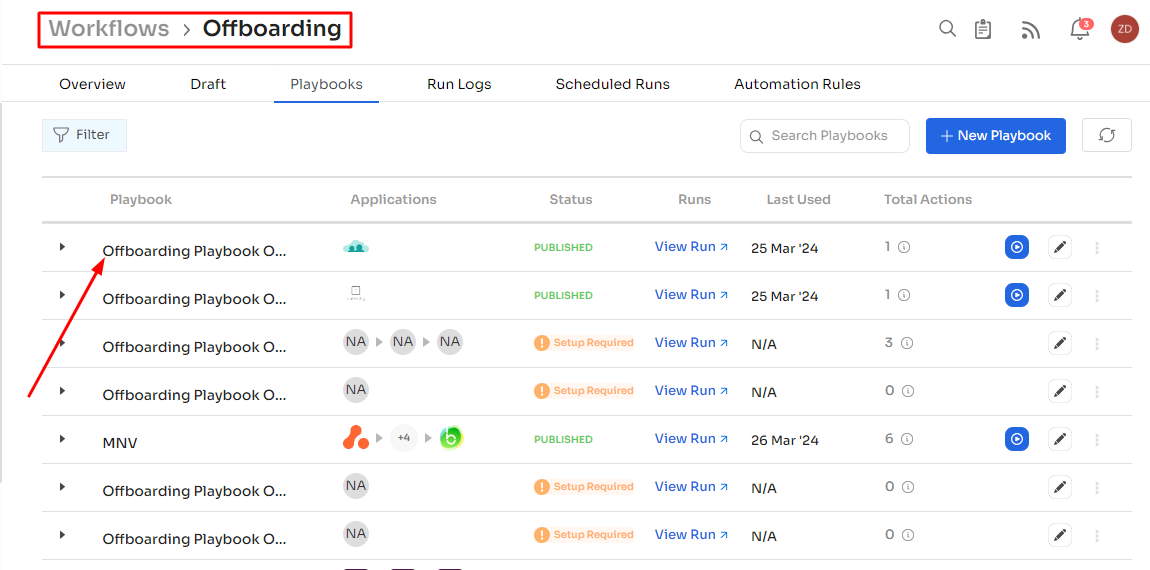
Another option is to set up different offboarding policies; for instance, you can trigger Zluri to run an offboarding playbook and deprovision user access automatically when the user status is marked as inactive in SSO. No manual selection is needed—Zluri fetches the data and runs the playbook as soon as the user is marked inactive.
By minimizing the risk of unauthorized access and potential security breaches, Zluri ensures a smooth and secure transition during user offboarding.
- Facilitate Automated Access Requests

Zluri simplifies access request management by automating the entire process. The platform provides an Employee App Catalog with pre-approved tools selected by IT teams. Employees can select tools based on their preferences and needs from this catalog. Further, it offers features like automated license assignment, customizable approval policies, and the ability to override stalled requests, enhancing productivity and compliance.
Also, users can easily request access to specific applications not available in the catalog directly through the platform. The automated workflow efficiently processes these requests, reducing delays and enhancing overall user productivity by ensuring timely access to necessary resources.
Also Read: To know more about Zluri’s access request, go through Self-service access requests.
- Manage Access Beyond SCIM

Zluri manages access comprehensively beyond SCIM (System for Cross-domain Identity Management).
Managing access for applications without SCIM connectors can be challenging for IT teams and app admins. Traditional tools rely on the SCIM protocol, making manual provisioning cumbersome and prone to errors. Zluri overcomes this by offering direct API integration with apps, enabling automated provisioning for non-SCIM apps.
The platform helps you discover, manage, and control access to all your apps — regardless of SCIM or SSO support.
Easily connect with 300+ apps using API connectors and automate user provisioning with robust actions, surpassing SCIM's limitations. This ensures enhanced control, visibility, and security across the organization's entire access landscape.
Also Read: To know the role of SCIM in managing access, you can go through SCIM provisioning.
Want to try Zluri? Book a personalized demo today!
Customer ratings
- G2: 4.8/5
- Capterra: 4.9/5
2. Okta Workforce Identity

Okta is a leading identity and access management (IAM) solution provider that over 14000 global brands use to secure digital interactions with employees and customers. It keeps all applications in one place and allows access quickly with a single sign-on without maintaining different passwords for every application. Okta enables users to access any application from any device, anytime and anywhere.
Okta offers an intuitive and user-friendly interface that simplifies the management of user identities and access control. You can easily configure policies, view reports, and monitor security from a centralized dashboard, making your job more efficient and effective.
Key Features
- Single Sign-On (SSO): With Okta’s robust SSO capability, your employees can access multiple applications with just one set of credentials. This boosts productivity and enhances security by reducing the risk of password-related vulnerabilities and identify anomalous behavior.
- Multi-Factor Authentication (MFA): Okta's MFA adds an extra layer of protection by requiring users to provide multiple verification forms before granting access, reducing the risk of unauthorized breaches.
- User Lifecycle Management: Okta simplifies this process by automating user provisioning and de-provisioning. When an employee joins or leaves your organization, Okta ensures that resource access is adjusted accordingly, reducing administrative overhead and security risks.
- Adaptive Authentication: Okta's adaptive authentication takes security to the next level by continuously monitoring user behavior. It assesses risk factors and adjusts authentication requirements accordingly. For example, if a user logs in from an unfamiliar location or device, Okta may prompt for additional verification to ensure the security of your system.
- Compliance and Reporting: Okta provides robust reporting and compliance features, helping you maintain a clear overview of user activities and security. With detailed audit logs and compliance reports, you can easily demonstrate your organization's adherence to regulatory requirements and security best practices.
Customer Rating
- G2: 4.4/5
- Capterra: 4.7/5
3. CyberArk Workforce Identity

CyberArk Workforce Identity offers identity and access management (IAM) software that protects your organization from modern cyber-attacks and helps users get the right resources easily. It is simple to use and easily integrates with other tools.
With CyberArk, users can access any application with just one click and a single set of credentials. So users don't have to worry about different passwords for different applications.
Key Features
- Privileged Access Management (PAM): CyberArk's identity and access management platform is anchored by its cutting-edge privileged access management capabilities. It empowers you to control, monitor, and secure access to privileged accounts, reducing the risk of unauthorized access and data breaches.
- Password Vaulting: CyberArk offers a secure password vault where sensitive credentials are stored in an encrypted format. This eliminates the common practice of storing passwords in spreadsheets or sticky notes, reducing the risk of password-related security incidents.
- Multi-Factor Authentication (MFA): Enhance user authentication with MFA, a key feature in CyberArk's IAM solution. MFA adds an additional security by requiring users to provide multiple verification forms before accessing critical systems or data.
- Session Recording and Monitoring: CyberArk provides comprehensive session recording and monitoring capabilities. This potential capability allows you to monitor privileged accounts and user activities in real-time, enabling quick detection and response to suspicious behavior.
- Least Privilege Access: Implementing the principle of least privilege ensures that users only have access to the resources necessary for their roles. CyberArk's IAM solution allows you to define granular access controls, reducing the attack surface and enhancing identity security.
- Privilege Elevation: With CyberArk's privilege elevation features, you can enable users to temporarily elevate their privileges for specific tasks without revealing sensitive credentials. This \"just-in-time\" access minimizes exposure and mitigates the risk associated with long-term elevated privileges.
Customer Rating
- G2- 4.4/5
- Capterra- 4.3/5
4. OneLogin
OneLogin empowers your team to improve your employees' experience by giving them access to all applications with a single set of credentials. It has more than 6000 direct integrations with several applications including on-premises applications. OneLogin makes onboarding and onboarding users very easy and efficient by allowing them to give or revoke access in a single click.
OneLogin provides comprehensive security reporting and auditing features. You can monitor user activities, track login attempts, and generate detailed reports to gain valuable insights into your organization's security posture. This helps you identify potential threats and ensure compliance with industry regulations.
Key Features
- Streamlined Access Control: OneLogin offers single sign-on (SSO) functionality, allowing your employees to access multiple applications with a single set of credentials. This potential capability boosts productivity and reduces the risk of password-related security breaches.
- Robust Multi-Factor Authentication (MFA): OneLogin recognizes this and offers robust MFA options. With MFA, you can rest easy knowing that only authorized individuals gain access.
- Effortless User Provisioning and Deprovisioning: OneLogin's identity and access management platform simplifies this process by automating user provisioning and deprovisioning. When a new employee joins your company, OneLogin ensures they have access to the right tools from day one. And when an employee leaves, their access is promptly revoked, minimizing security risks.
- Unified Directory Services: OneLogin integrates seamlessly with your existing directory services, such as Active Directory or LDAP, ensuring consistency in user profiles and permissions. This integration simplifies management and minimizes the risk of errors.
Customer Rating
- G2: 4.3/5
- Capterra: 4.7/5
5. Microsoft Entra ID

Formerly known as Azure Active Directory, Microsoft Entra ID emerges as a cutting-edge, cloud-based solution meticulously crafted to enhance the security of your access environment. This platform achieves its objective through the implementation of robust authentication measures and adaptive access policies rooted in comprehensive risk assessment, all while prioritizing a seamless and user-friendly experience.
The platform not only enhances user productivity but also reduces the complexities associated with password management, ultimately contributing to an elevated level of operational efficiency.
Key features
- Integrated Application Safeguarding: Microsoft Entra ID seamlessly incorporates integration tools within its framework, empowering the development of applications dedicated to safeguarding sensitive data and employee identities. This integrated approach ensures a comprehensive security stance, solidifying your organization's commitment to protecting valuable information in the ever-evolving digital landscape.
- Centralized User Identity and Access Control: Azure Active Directory, now known as Microsoft Entra ID, empowers your IT team to oversee and control all user identities and application access. This centralized management hub, available in the cloud or on-premises, enhances visibility and control over your organization's users and their access actions.
- Enhanced Visibility and Management: The centralization provided by Azure AD contributes to improved visibility and management of your organization's users and their access activities. This consolidated approach ensures that your IT team can efficiently oversee and regulate user identities and application access from a unified platform.
- Transparent Data Encryption: Microsoft Entra ID incorporates transparent data encryption features, allowing your IT team to secure vital data through encryption. This capability empowers your organization to protect information stored on servers, preventing unauthorized or external users from gaining access to sensitive data.
- Fortified Security Posture: By adopting a holistic approach to security, Microsoft Entra ID reinforces your organization's security posture. This comprehensive strategy is designed to adapt to the dynamic digital landscape, ensuring that your valuable information remains protected against potential threats and unauthorized access.
Customer Rating
- G2: 4.5/5
- Capterra: 4.8/5
6. SailPoint

SailPoint offers identity and access management (IAM) software that empowers your team to centralize access for all applications and data from one single dashboard. It automates compliance and delivers audit-ready reports. SailPoint sends alerts for any sort of abnormalities in user behaviors to ensure that organizations' data are secure.
Key Features
- Identity Governance: SailPoint empowers you with comprehensive identity governance capabilities. It allows you to define and manage user identities across your hybrid environment, ensuring that the right people access the right resources. This potential capability simplifies user lifecycle management, from onboarding to role changes and offboarding, while ensuring compliance with industry regulations.
- Access Management: SailPoint provides advanced access management tools that help your team establish fine-grained controls over user privileges. You can define and enforce access policies, reduce the risk of unauthorized access to apps, and minimize the attack surface.
- Single Sign-On (SSO): Simplify the user experience and improve productivity with SailPoint's SSO feature. This not only enhances security but also reduces the burden on IT support.
- Password Management: With this capability, you can implement self-service password reset options, reducing support ticket volumes and enhancing user satisfaction.
- Risk-Based Authentication: SailPoint helps you implement risk-based authentication, allowing you to assess the level of risk associated with each access attempt.
Customer Rating
- G2: 4.4/5
- Capterra: 4.2/5
7. RSA SecurID

RSA SecurID is an enterprise-grade intelligent identity and access management (IAM) platform that comes with flexible deployment options. RSA is a subsidiary of Dell EMC. RSA SecurID offers all the necessary features that are essential for larger organizations, such as SSO, identity governance, and identity and lifecycle management.
For employees, RSA SecurID enables them to access different applications with a single set of credentials to enhance their experience and reduce the load of managing multiple credentials.
Key Features
- Multi-Factor Authentication (MFA): RSA SecurID offers MFA that ensures only authorized personnel gain access, adding an extra layer of security. This robust authentication method mitigates the risk of unauthorized access, reducing potential breaches.
- Risk-Based Authentication: Adapting to the dynamic nature of security threats, RSA SecurID incorporates risk-based authentication. This potential capability evaluates user behavior and context to determine if an access attempt is high or low risk.
- Seamless Integration: The tool integrates seamlessly into your existing IAM infrastructure, making the transition smooth and cost-effective.
- Self-Service Portal: RSA SecurID offers a user-friendly self-service portal that empowers your employees to manage their authentication methods and reset passwords independently. This potential capability not only reduces your IT team's workload but also enhances the user experience by putting control back in the hands of the end-users.
- Compliance and Reporting: It provides robust reporting tools for audits and compliance assessments. Detailed logs and real-time monitoring help you maintain a tight grip on your organization's security posture.
Customer Rating
- G2: 4.4/5
- Capterra: 4.6/5
8. Ping Identity
Ping Identity empowers your team to provide a convenient employee experience while accessing different applications. It eliminates the hurdle of keeping different credentials for accessing various applications. With Ping Identity, employees can access any application with a single credential from a centralized dashboard.
Ping Identity seamlessly integrates with popular cloud platforms. This ensures consistent identity management and access control across your entire IT ecosystem, whether on-premises or in the cloud.
Key Features
- Single Sign-On (SSO) Simplified: Ping Identity streamlines user access by offering SSO capability. Your team can now access various applications and services with a single set of credentials, enhancing both security and user experience.
- Multi-Factor Authentication (MFA): Ping Identity combats this with multi-factor authentication, adding an extra layer of protection that significantly reduces the risk of unauthorized access.
- Adaptive Authentication: Ping Identity's adaptive authentication takes this into account. This potential capability evaluates the context of each login, considering factors such as location, device, and behavior to assign risk levels.
- Federated Identity: Ping Identity allows seamless and secure access to resources across different domains and platforms. This robust capability simplifies collaboration and ensures data integrity while maintaining robust security measures.
- User Lifecycle Management: Ping Identity simplifies this process by automating user provisioning and de-provisioning. When employees join or leave the organization, their access rights are updated accordingly, reducing the risk of unauthorized access.
- API Security: Ping Identity extends its security features to APIs, safeguarding the connections between applications and data sources. This ensures your APIs are protected against threats and adhere to industry standards.
Customer Rating
- G2: 4.4/5
- Capterra: 4.8/5
9. Symantec
Symantec by Broadcom offers an enterprise-focused intelligent identity and access management platform. IAM is part of its identity security suite, which includes the SaaS-based VIP and advanced authentication solutions. It also performs risk analysis and detects location-based anomalies in different accounts to prevent threats.
Symantec's IAM solution seamlessly integrates with various cloud services, ensuring your organization's identity and access management strategy can adapt to evolving technology trends. It offers scalability to accommodate your growing business needs, making it a future-proof choice.
Key Features
- Single Sign-On (SSO) for Seamless Access: Symantec's IAM software simplifies the user experience by providing a Single Sign-On (SSO) capability. It boosts convenience and strengthens security by reducing the risk of password-related vulnerabilities and identify anomalous behavior.
- Multi-Factor Authentication (MFA): Security is paramount, and Symantec's IAM solution offers Multi-Factor Authentication (MFA) to fortify your organization's defense against unauthorized access. This additional security significantly reduces the risk of unauthorized access.
- Role-Based Access Control (RBAC): With Symantec's IAM software, you gain granular control over user permissions and access rights. This potential capability ensures that users only have access to the resources necessary for their tasks, minimizing the risk of data breaches and insider threats.
- User Lifecycle Management: Symantec simplifies managing user accounts and their access lifecycle by automating user provisioning and deprovisioning. This robust capability ensures that their access privileges are updated or revoked promptly. This not only improves security but also enhances operational efficiency.
- Audit and Compliance Reporting: Symantec's IAM software has robust auditing and reporting capabilities. This feature is invaluable for meeting compliance requirements and demonstrating regulatory adherence to auditors, helping your organization avoid potential fines and penalties.
Customer Rating
- G2: 3.4/5
- Capterra: 4.7/5
10. ForgeRock Identity Platform

ForgeRock Identity Platform is an intelligent identity and access management platform with advanced cloud infrastructure and artificial intelligence to make it easy for your team to manage, secure, and govern all user identities across your organization.
The tool ensures that solely authorized users gain access to your organization’s resources, serving as a shield against potential threats or data breaches. Moreover, it enhances operational efficiency through the automation of account creation and removal, as well as streamlining many other tasks to eliminate the need for manual intervention and human error.
Key Features
- Single Sign-On (SSO): ForgeRock simplifies user access by offering an SSO capability. No more password fatigue or the risk of weak passwords – ForgeRock enhances security while streamlining user experience.
- Multi-Factor Authentication (MFA): ForgeRock incorporates MFA, adding an extra layer of security by requiring users to provide multiple forms of authentication, such as a fingerprint, token, or SMS code, making unauthorized access nearly impossible.
- User Self-Service Portal: ForgeRock provides a user-friendly portal where employees can reset passwords, manage their profiles, and request access to resources. This reduces your IT team's workload and improves overall efficiency.
- Adaptive Authentication: ForgeRock's adaptive authentication engine uses advanced analytics to assess risk and dynamically adjust security measures accordingly. This robust capability can detect suspicious behavior, such as login attempts from unusual locations or devices, and respond with additional security checks as needed.
- Identity Lifecycle Management: ForgeRock offers a robust capability for provisioning and deprovisioning user accounts, ensuring employees have the right access at the right time, improving compliance, and reducing security risks.
- IoT and API Security: As the Internet of Things (IoT) and APIs become integral to modern business operations, ForgeRock extends its IAM capabilities to cover these areas, ensuring secure interactions between devices and applications.
Customer Rating
- G2: 4.4/5
- Capterra: 5/5
11. IBM Cloud

IBM identity and access management (IAM) empowers your team to manage the complete lifecycle of users' identities and digital interactions. Its cloud IAM incorporates AI, big data, and deep analytics to automate various identity management tasks, such as changing user access and identifying anomalies in user behavior.
IBM Cloud easily integrates with popular cloud platforms, allowing you to extend security measures to cloud-based applications and resources, making it an ideal choice. Further, whether you're a small business or a large enterprise, you can rely on its high availability and scalability to accommodate growth.
Key Features
- Single Sign-On (SSO) for Simplified Access Management: One of the standout features of IBM IAM is its Single Sign-On capability. This simplifies the login process and enhances security by reducing the risk of password-related breaches.
- Comprehensive User Lifecycle Management: IBM Cloud offers a centralized management platform to manage the entire lifecycle of user identities. This ensures that the right individuals have the right level of access at all times as per your access requirements, improving efficiency and security.
- Multi-Factor Authentication (MFA) for Enhanced Security: IBM Cloud incorporates multi-factor authentication (MFA) options, such as biometrics, one-time passwords, and smart cards. This additional security fortifies your organization against unauthorized access attempts.
- Role-Based Access Control (RBAC): You can implement RBAC policies easily with the IBM cloud. Assign roles to users and grant them appropriate permissions, ensuring they can perform their tasks without unnecessary access to sensitive data.
- Federated Identity Management: IBM Cloud supports federated identity management as its robust capability enables seamless integration with external identity providers. This means your partners can securely access your resources without needing separate credentials.
- Self-Service Portal: Empower your users with a self-service portal where they can reset passwords, update personal information, and request access permissions. This reduces the burden on your IT team along with human error and enhances user satisfaction.
Customer Rating
- G2: 3.8/5
- Capterra: 5/5
12. Oracle Identity Management
Oracle Identity Management emerges as a robust solution designed to simplify identity and access management (IAM) for your IT team. Boasting an array of user-friendly features and cutting-edge identity security measures, Oracle Identity can be an ideal choice to elevate your identity management strategies.
The Oracle Identity software seamlessly integrates with a multitude of applications, encompassing popular SaaS offerings, critical HR systems, and tailor-made applications. This seamless integration process simplifies your provisioning and deprovisioning of user accounts, ensuring that access rights remain consistently up-to-date.
Key Features
- Single Sign-On (SSO): Oracle Identity offers a seamless SSO experience for users. Your team can benefit from simplified password management and reduced helpdesk ticket volumes, resulting in cost savings and increased productivity.
- Multi-Factor Authentication (MFA): It provides robust multi-factor authentication options, allowing your team to bolster access control with factors like biometrics, smart cards, and one-time passwords. This ensures that only authorized personnel gain access to sensitive data.
- Role-Based Access Control (RBAC): Oracle Identity software supports RBAC, a fundamental aspect of effective identity management. Your team can easily assign and manage user roles, granting access rights according to job responsibilities.
- Self-Service User Portal: Oracle Identity incorporates a self-service user portal, empowering employees to manage their accounts, reset passwords, and request access to resources without IT intervention. This feature not only boosts user satisfaction but also reduces the administrative burden on your IT team.
- Cloud and On-Premises Deployment: Oracle Identity can be deployed both in the cloud and on-premises, allowing you to choose the deployment model that best aligns with your organization's needs and preferences.
Customer Ratings
- G2: 3.7/5
- Capterra: 4.6/5
13. Duo Security
Duo Security stands as a cloud-hosted security suite that ensures the protection of access to all applications for users and devices, regardless of their location worldwide. The platform equips you with policies and controls, enabling the blocking of access based on endpoints or user risk. This is executed in conjunction with detailed insights into users' devices, enhancing your organization's security posture.
Duo Security ensures a standardized sign-in experience for users, facilitating centralized access to both on-premises and cloud-based applications. With its user-friendly design and powerful security features, Duo Security is a reliable solution for organizations seeking effective access management in today's dynamic digital landscape.
Key Features
- Cloud-Based Access Protection: Duo Security operates as a cloud-hosted security suite, safeguarding access to all applications for users and devices worldwide. This cloud-centric approach ensures flexibility and scalability in securing access in diverse environments.
- Simplified User Experience: Designed for simplicity in both usage and implementation, Duo Security provides a user-friendly experience. The intuitive interface facilitates ease of use for both administrators and end-users, contributing to a seamless and efficient security management process.
- Total Visibility and Endpoint Control: Offering total visibility and control over endpoints, Duo Security empowers organizations to monitor and manage access comprehensively. This enhances the ability to enforce security policies and respond effectively to potential threats.
- Passwordless Authentication: Duo Security introduces strong authentication mechanisms that eliminate the need for passwords. This innovative feature not only enhances security but also simplifies the login experience for users, contributing to a frictionless authentication process.
- Multi-Factor Authentication (MFA) Leadership: Positioned as a market leader in multi-factor authentication, Duo Security ensures an extra layer of protection for users and devices. This advanced security measure significantly enhances the resilience of access controls against various security risks.
- Policy-Based Access Control: Duo Security provides robust policies and controls, allowing organizations to block access based on specific endpoints or user risk. This policy-based approach enhances security by tailoring access permissions to align with organizational requirements.
Customer Ratings
- G2- 4.5/5
- Capterra- 4.7/5
Elevate Your Security Measures with Identity and Access Management Tools
This guide provides an overview of the top 13 identity and access Management tools. However, making the right choice for an IAM platform requires a comprehensive assessment of factors like cost, complexity, scalability, integration capabilities, automation features, and reporting capabilities. These considerations offer a holistic understanding and should serve as guiding factors throughout your decision-making process.
A strategic approach involves crafting a customized list of feature requirements tailored to your organization's specific needs. This organized list assists in pinpointing IAM solutions that align best with your unique requirements and priorities, streamlining the selection process.
Ultimately, the decision is yours regarding which platforms to further explore. A meticulous evaluation based on your defined criteria will lead you to the most suitable IAM tool for your organization's needs in the dynamic landscape of identity and access management.
Frequently Asked Questions (FAQs)
1. Is IAM a guarantee of security?
IAM significantly enhances security by minimizing dependence on multiple passwords and centralizing authentication. However, a robust security posture also requires additional measures, such as encryption and stringent access controls, to safeguard the system and protect sensitive data effectively.
2. What challenges may arise with IAM implementation?
Challenges in IAM implementation include addressing interoperability issues between diverse identity systems, managing potential trust and privacy concerns between organizations, and ensuring consistent security standards across participating entities. Adherence to proper protocols and standards is essential to mitigate these challenges.
3. How does IAM differ from Single Sign-On (SSO)?
IAM serves as a comprehensive concept, facilitating authentication and authorization across multiple domains or organizations. On the other hand, Single Sign-On (SSO) is a specific implementation of IAM, enabling users to access multiple applications with a single set of credentials, but typically within a single organization.
4. What role does IAM play in regulatory compliance?
IAM plays a crucial role in regulatory compliance by enforcing access controls, monitoring user activities, and maintaining detailed audit trails. Aligning with industry-specific regulations and data protection laws, IAM tools contribute significantly to ensuring organizations meet compliance requirements.
5. How can IAM enhance user productivity?
IAM boosts user productivity through features like Single Sign-On (SSO) and user-friendly self-service portals. Users gain seamless access to resources, reducing the complexity of managing multiple passwords. Moreover, streamlined onboarding and offboarding processes contribute to an overall more efficient user experience.







.png)

.svg)














