Still relying on legacy IAM solutions to prevent sophisticated identity-centric attacks? If so, you might be inadvertently creating access gaps that malicious actors can exploit. But how? What’s the problem with legacy IAM solutions?
Attackers today aren’t breaking in; they’re logging in.
Phishing, credential stuffing, session hijacking, and even Kerberoasting are all designed to do one thing: steal identity-related information, such as usernames, passwords, access tokens, and session cookies. Once inside, attackers move laterally, escape privileges, and operate undetected, all while your legacy IAM platform thinks everything's fine.
This isn’t hypothetical. A 2025 Forbes Technology report shows that 87% of breaches now stem from identity-based attacks.
And yet, most legacy IAM solutions are still built to protect a network perimeter that no longer exists. In today's cloud-first, SaaS-driven world, identity is the new perimeter, and if your defenses don't center around it, you're leaving gaps attackers can easily exploit.
Legacy IAM tools don't authenticate based on static credentials, and fail to prevent unauthorized access when those credentials are stolen.
If your identity strategy still leans on legacy IAM, you're not protecting your perimeter; you're exposing it.
Let's break down exactly where legacy IAM fails, and what you need instead.
Why Legacy IAM Fails Against Identity-Based Threats?
The legacy IAM platform may help manage access, but it wasn’t built to prevent today’s identity-first attacks. Here’s where it falls short, and why those gaps matter to you.
.png)
1. Doesn’t Provide Complete Visibility Into Who Is Accessing What
Legacy IAM was built for a simpler time, when most users were full-time, on-prem employees accessing a handful of IT-managed systems.
- Identities were limited in number and relatively static.
- Users rarely changed roles, worked remotely, or accessed apps outside the perimeter.
- So, it was easy for traditional IAM tools to track access..
Today, that’s no longer the case.
- Identities have multiplied and become diverse, including contractors, third-party vendors, service accounts, bots, and APIs.
- They’re also highly dynamic, often changing roles, operating remotely, or logging in from unmanaged devices.
Legacy IAM platforms can’t keep up.
- It lacks the context to monitor access across user types, devices, and environments.
- Non-standard identities often go unmanaged, leaving blind spots that attackers can exploit.
You can’t protect what you can’t see – and that’s the core failure here.
Without clear visibility, identity management becomes guesswork. And in cybersecurity, guesswork is a risk.
2. Authenticates, But Doesn’t Authorize
Legacy IAM solutions stop at step 1: authentication – validating whether a user’s credentials (like a username and password) are correct.
But it doesn’t handle authorization – deciding what the authenticated user is allowed to access or do once logged in. That’s a critical gap.
Here’s why it is risky:
- If an attacker steals valid credentials (via phishing, credential stuffing, etc.), legacy IAM systems grant access without performing any further checks.
- It doesn’t assess user behavior, risk signals, or anomalies —such as location mismatch, typing speed, or device fingerprint.
- No step to question: “Should this user be doing this?”
As a result, attackers can move laterally, browsing systems, accessing sensitive data, and escalating privileges — all while appearing legitimate.
Authentication without authorization is like letting someone into your building without asking why they’re there.
3. Cannot Unify Fragmented Identity Data
Organizations often use siloed IAM tools (such as SSO, MFA, and PAM) from different vendors, each storing user data in its own format. These tools don’t sync, making it hard to build a single source of truth.
Can’t we just integrate them?
Technically, yes—via iPaaS or custom connectors. But legacy IAM systems can only fetch, not reconcile identity records.
Example:
- The SSO system stores the user as Olivia. wilde
- PAM system stores the same user as Olivia.w
Legacy IAM pulls both, but treats them as different users, resulting in duplicate records.
Why is it a problem?
- IT manages duplicate identities as separate people.
- Olivia ends up with overprovisioned access.
- Upon exit, only one identity may be deactivated, leaving a stale access point vulnerable to attack.
Without proper unification, fragmented identity data increases security risks and access mismanagement.
4. Violates Least Privilege by Overprovisioning
Most legacy IAM solutions assign access based on static groups rather than individual roles. That means users often get far more access than they need, putting your organization at risk.
What legacy IAM does?
- Use a group-based provisioning method, assigning access based on departments (e.g., Finance).
- Everyone in the group – interns, analysts, and managers - gets the same set of apps and permissions.
- Ignores role-specific needs and risk levels.
Why is that a problem?
- Overprovisioning has become the norm. Users get access to tools they don’t need or shouldn’t use.
For example, A finance intern might access tools meant for analysts or even gain admin permissions.
- Violates the principle of least privilege. Not all users require the same level of access or permission.
- Creates security gaps and non-compliance risks, attackers can exploit excess access.
What should you do instead?
- Move away from static groups to context-aware provisioning.
- Adopt a modern IGA platform that:
- Maps access to job responsibilities
- Considers risk, context, and sensitivity of permissions
- Prevents excessive access from the start
Leverage Next-Gen IGA Solution To Address Identity Attacks
Below, we’ve discussed how a next-gen solution helps manage identities and secure your IT environment against potential cyberattacks.
.png)
Note: We’re using Zluri's next-gen IGA as an example to help you better understand how next-gen IGA platforms work in real-time and the value they deliver.
1. Offers Complete Visibility Into Who Has Access To What
Zluri leverages 9 advanced discovery methods to deliver comprehensive visibility into:
- Visibility into every identity across your organization, be it on-site or remote employees, contractors, freelancers, or even non-human identities like service accounts.
- Additionally, it uncovers which applications they interact with – whether it’s SaaS apps, on-premise tools, GenAI-powered apps, or even shadow IT.
It then provides all identity-related information in one easy-to-access centralized dashboard.
Furthermore, with the help of this visibility, your team can effectively manage, control, govern, and secure your identities.
2. Authenticates Identities As Well As Authorizes Them
Zluri first verifies the identity of a user who is attempting to log in or access an app. It does this by establishing and maintaining a trust relationship with the identity provider (IdP).
- Whenever a user attempts to log in, Zluri shares the user’s data with the IdP.
- The IdP then checks whether the user’s data matches the data stored in directories.
- If the details match, IdP sends an authentication token, confirming the user is legitimate. Once this token is received, Zluri proceeds to the authorization stage.
It determines what actions the user is authorized to perform within the app based on pre-defined rules/controls. Then, it finally grants the user access to the app.
Let’s say a new IT admin logs into the HRMS app; you want them to get admin-level access immediately after authentication. With Zluri, you can configure automation rules to handle this scenario without manual intervention. Here’s how:
Simply specify the following rules within the automation rule workflow –
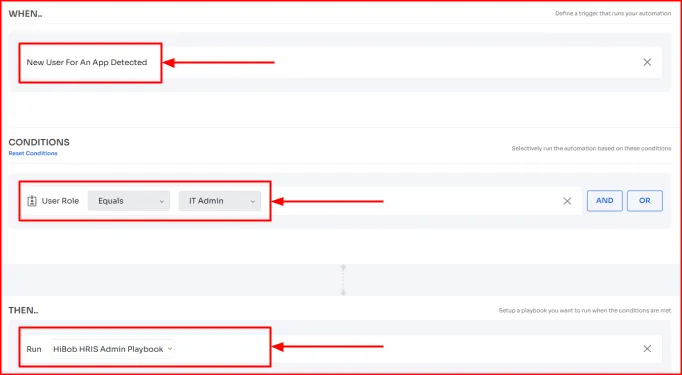
Once these conditions are met, Zluri auto-assign the user admin access to the HRMS app. This helps ensure that only the right individuals get the right level of access to the apps and sensitive data, which further helps reduce the attack surface and prevents violation of PoLP.
Take a look at this blog to gain better clarity: Authentication Vs Authorization: 5 Key Differences
3. Unifies Fragmented Identity Data
Regardless of whether your setup is disparate or converged. Zluri provides a unified, centralized view of identity data. It does that by –
- Integrating with your (IAM) tools – be it SSO & MFA, PAM, LCM, ITSM, or others and automatically pulls the fragmented identity data from scattered systems.
- Then, intelligently matching and merging different identity records that actually belong to the same person and creating a single, unified view (often called a "single source of truth").
All of this identity data is then presented in a single dashboard, making it much easier for IT teams to use it to manage, govern, and secure identities — without confusion.
This way, users like Olivia don't receive excessive app permissions, and when they leave, every access point is revoked – eliminating stale accounts and reducing security risks.
Rethink Your Strategy To Fight Against Evolving Identity-Centric Attacks
Identity-centric attacks are rising day by day; you never know – any moment, your organization can be the next target.
So, do not just sit back and debate what if the legacy IAM might hold up, or stress over whether the next-gen IGA solution will be the right choice. Every moment spent hesitating gives attackers more time to find a way in. It’s time to act!
Strengthen your defenses, modernize your identity security, and stay one step ahead – before your organization becomes the next headline.









.svg)














