BetterCloud enables your IT teams to seamlessly manage and control SaaS application access & entitlements and security policies in your multi-SaaS environment.
Meanwhile, Okta focuses on ensuring secure connections between users and technology. It further allows your IT team to manage password and sign-on policies, role-based access to SaaS apps, MFA, integration with existing user directories, and more, adding an extra layer of security to verify your user's identity.
Nonetheless, it's essential for you, as an IT manager, to thoroughly assess the other unique capabilities offered by both tools before choosing the most suitable IGA solution for your IT team's needs.
To determine the most suitable tool between BetterCloud and Okta, it is essential to conduct an in-depth analysis of their capabilities and how they align with the specific requirements of your IT team. By doing so, you will be able to make an informed decision that best suits the needs of your IT team.
Suppose an organization requires an IGA tool with alerting, auditing, and reporting features, specifically targeting file/data security. So according to you, which tool will be more appropriate for this scenario, BetterCloud or Okta?
Well, BetterCloud allows your IT team to conduct file security audits by monitoring who has access to crucial data or file content and identifying potential violations of security standards. This further enables your team to enforce policies that protect against unauthorized access attempts and ensure compliance with data security regulations.
Okta will be well suited for organizations that primarily focus on managing user identities across different applications and simplifying access through single sign-on. It excels in centralizing user access and streamlining authentication processes for various applications through a unified platform.
However, this was just an overview of how functions can bring a difference in the decision-making process. Though, you cannot decide which tool to choose based solely on one functionality. You need to carefully consider each of their distinctive features to select the best one among the two.
So, let's move ahead and compare both tools based on different parameters to help you decide which IGA solution will best meet the requirements of your IT team.
BetterCloud Vs. Okta: Detailed Comparison To Choose The Best IGA Tool
Below are the parameters based on which we have closely compared the two IGA tools. By examining these parameters, you will be able to determine which tool offers the best functionalities to help your IT teams streamline the identity governance and administration process.
1. Identity Governance & Administration
Both BetterCloud and Okta offer access permissions and access certification capabilities to streamline identity governance. However, they have their own unique way of managing access. Let's see how they do it:
- BetterCloud allows your IT team to take control and manage access permissions, ensuring that only the appropriate level of access is granted to your employees. With BetterCloud, your IT team can gain complete visibility into which employee has access to which SaaS apps and data, what level of access permissions they possess, and more. Further, seamlessly adjusting roles and permissions across various SaaS applications within your organization enhances overall system safety and control.
This platform simplifies the process of addressing file/data security threats by implementing automated workflows that regulate access to sensitive data-containing files. It mitigates the risk of malicious or negligent user actions by consolidating the management of user access permissions for each SaaS application.
It doesn't stop here; BetterCloud allows your team to effortlessly implement a least privilege model, granting users access solely to the specific apps, files, and data they require and can modify employee access in bulk.
Moreover, it alerts your teams on unauthorized access attempts to maintain the safety and security of SaaS app data. Accordingly, your team can take preventive measures to mitigate the security risks.
Apart from that, BetterCloud manages roles and permissions by identifying and decommissioning unnecessary \"super admins,\" fine-tuning individual account privileges to align user permissions with their specific needs. Additionally, it provides limited and time-bound external user access, allowing for productivity while safeguarding the security of your sensitive SaaS app data. - Meanwhile, Okta Identity Governance enables your IT team to strengthen security measures, address modern security risks, and improve efficiency. A central aspect of Okta Identity Governance is its access governance solution, enabling your IT team to maintain strict control over access to SaaS apps and data. This ensures that the right employees have the right level of access to the necessary apps and data while minimizing unnecessary complications.
Furthermore, Okta's Workflows platform empowers your IT team to tailor complex identity governance requirements to their specific needs without the need for coding. Also, your IT team can customize and automate IT processes such as provisioning and deprovisioning, streamlining overall identity governance and access management processes effectively.
Apart from that, Okta simplifies compliance with automatic reports designed to meet auditor requirements. Additionally, it provides your IT team with a complete view of every user's access patterns, enabling them to identify potential security concerns proactively before they escalate into critical issues.
It is not restricted to that only; Okta offers a self-service access request feature that reduces frustration and empowers employees to raise access requests effortlessly. This user-friendly feature enhances productivity by minimizing the complexities associated with access requests.
2. Managing Access Seamlessly
- Automate the tedious, repetitive provisioning/deprovisioning process with BetterCloud
BetterCloud enables your IT team to eliminate repetitive provisioning and deprovisioning processes through automation. By leveraging BetterCloud, your IT team can enhance your employee productivity while ensuring the right level of access is granted based on their role, position, and department by integrating with HR systems like Workday and Bamboo HR.
How does BetterCloud achieve this? It empowers your IT team to automate and tailor onboarding workflows to meet your organization's specific requirements. It supports over 900+ actions, reducing the manual effort of granting access to the right employees and allowing your IT team to allocate more time to core IT activities.
Moreover, BetterCloud simplifies the offboarding process with its zero-touch approach, minimizing the steps involved in managing departing employees' access. Through robust automation, BetterCloud saves time and safeguards sensitive SaaS app data during employee departures by revoking all access and deactivating/suspending their accounts. This efficiency enhancement reduces the time required for employee deprovisioning from an average of 9 hours to less than 30 minutes.
In addition, BetterCloud allows your IT team to mitigate security risks by minimizing errors due to manual handling of IT processes. With support for 1000+ actions and a variety of best-practice templates, BetterCloud enables strategic scheduling of on-demand workflows. These workflows automatically revoke employee access to applications and groups and transfer files/data to other team members, ensuring a secure transition and adherence to IT governance practices. - Streamline the onboarding and offboarding process with Okta’s lifecycle management
With Okta’s lifecycle management, your IT team can seamlessly assign access based on employees’ roles, positions, or departments and promptly revoke all access upon employee departure. This streamlined approach ensures that employees can start working without delay after being hired, enhancing their overall working experience and boosting their productivity.
Furthermore, BetterCloud swiftly suspends user accounts and revokes access, enabling your team to reclaim/ re-assign software licenses. Also, It effectively safeguards SaaS app data by actively protecting against security breaches or unauthorized access.
Apart from that, BetterCloud seamlessly integrates with your HR system, streamlining the provisioning and deprovisioning processes. Additionally, your team can easily customize workflows using Okta workflows without the need for coding, allowing for flexibility and tailored automation.
With Okta's automation and integration capabilities, your team can efficiently grant access to the right applications to the right individuals and revoke access based on triggers from HR systems, IT resources such as AD and LDAP, and more. This comprehensive automation ensures efficient access management.
Moreover, Okta performs audits and generates reports that provide visibility into which employees can access specific applications and recent revocations of privileges. This centralized view allows your IT team to keep track of all employees and their account access in one convenient location.
3. Security & Compliance
- BetterCloud offers your IT team a complete view of your employees, groups/accounts, data, and access permissions. This visibility enables your team to closely monitor and detect any suspicious access activities carried out by employees.
Furthermore, it facilitates secure access management by implementing consistent policies across your organization. It streamlines workflows and ensures that employees are granted access based on their designated roles, promoting efficient and controlled access management practices.
BetterCloud goes beyond access management by actively monitoring potential violations of internal security standards. It enforces policies that protect against security breaches and ensures compliance with security regulations.
Additionally, with its centralized and granular security capabilities, your team can identify and address threats, effectively safeguarding the organization's SaaS app data. Through centralized content scanning, your IT team can gain greater visibility into potential risks and identify sensitive data such as personally identifiable information (PII) and financial information.
By leveraging powerful workflows, BetterCloud enables your team to establish and maintain consistent internal security policies. These workflows automatically remediate discovered security vulnerabilities, reducing risks without compromising employee productivity.
Moreover, BetterCloud provides detailed and centralized audit logs that never expire, facilitating quick and efficient internal compliance demonstrations. It allows you to efficiently implement least privilege controls, ensuring that employees have the appropriate access permissions from the outset.
- On the other hand, with Okta, your IT team can effectively safeguard your employees' accounts and protect SaaS app data from credential theft and fraud using its robust multi-factor authentication (MFA) solution. By implementing MFA, your team can strengthen security for both customer-facing and enterprise SaaS apps that house sensitive data, ensuring that only authorized individuals can access them.
To provide an additional layer of protection, Okta offers ThreatInsight, which automatically blocks suspicious IP addresses that have been involved in identity attacks on other organizations within Okta's customer base. This proactive approach, enhances your overall security and mitigates potential risks.
Okta also integrates external risk signals from various security vendors, granting your team enhanced visibility into potential threats. This integration empowers your team to strengthen authentication measures or block requests as needed without causing unnecessary disruptions to workflow.
Moreover, with Okta, your IT team can create contextual access policies that assess risk factors such as device, network, location, travel, IP, and other relevant contexts at each stage of the authentication process. This contextual approach adds an extra layer of security by evaluating multiple factors before granting access.
Furthermore, Okta ensures that your organization complies with the authentication assurance levels required by your industry, meeting the necessary security standards and regulations.
4. Policy Enforcement & Authentication Procedure
- BetterCloud provides protection against the unauthorized sharing of sensitive SaaS app data through automated and granular control mechanisms. It empowers your IT team to proactively identify and mitigate risks associated with data exposure.
With BetterCloud, your team can easily scan data using predefined and customized data types, enabling them to identify potential security breaches. The platform provides alerts for unwanted access and exposure, including sensitive information, such as security and passport numbers, credit card numbers, passwords, and non-compliant words and phrases.
BetterCloud enables proactive policy enforcement through automation to maintain a consistent data security policy. This protects data from improper exposure and prevents unauthorized file access. By leveraging automated workflows, the platform helps remediate threats by revoking file access and locking down files when sensitive data is accessible by unauthorized internal or external users. - Meanwhile, Okta aims to provide every employee with a seamless and secure authentication process by eliminating traditional password methods. How does it accomplish this? Okta introduces WebAuthn-based passwordless authentication, eliminating the need for passwords and significantly enhancing overall security. By adopting this method, your IT team can effectively safeguard your employees' identities against the risks associated with phishing attacks.
But it doesn't stop at security enhancements. Okta's WebAuthn also simplifies the authentication process. It leverages a single authentication method that serves as two factors, equivalent to multi-factor authentication (MFA). With this approach, employees authenticate once, eliminating the need for additional MFA steps. This streamlined process enhances the employee experience without compromising security.
Moreover, Okta offers versatility in authentication methods by allowing employees to verify themselves through SMS and email on various devices, including desktops, tablets, and mobile devices. This flexibility ensures convenience for employees while maintaining robust security measures.
After closely comparing BetterCloud and Okta, you may have understood which IGA tool aligns better with your IT team's requirements. However, you should not restrict yourself to just these two tools. The market offers a range of efficient IGA platforms, and one such alternative worth considering is Zluri. This platform provides exceptional functionalities to streamline the identity governance and administration process and presents itself as a viable alternative to BetterCloud and Okta
So, what exactly is Zluri, and what unique features does it bring to the table? Let's have a quick look.
Simplify Identity Governance and Administration with Zluri
Managing access permissions is not a one-time task; it's a recurring process that your IT team needs to do to maintain a secure and compliant environment for your employee identities and SaaS app data. However, juggling these responsibilities can be challenging for your IT team. So, if your team is facing such difficulties, Zluri is the ultimate modern IGA solution for you. Let’s see how it works and what all capabilities it has to offer.
1. Gaining Clear Insights into User Access with Zluri's Data Discovery Engine
Zluri stands out from its competitors in data discovery because it's primarily a SaaS management platform. This advantage makes Zluri highly effective in identifying SaaS app data and user access, giving your IT team complete visibility into user access data.
Zluri offers five discovery methods: SSO or IDP, finance systems, direct integrations, browser extensions (optional), and desktop agents (optional). With these methods, your IT team can easily identify which users have access to specific SaaS apps, their access rights, user status (active or inactive), and more.
Further, this valuable information helps your team manage user access efficiently and improves the overall security of SaaS app data.
Having access to such detailed knowledge enables your IT team to conduct access reviews effortlessly. The review process becomes more efficient, minimizing oversight risk and ensuring access privileges align with user roles and comply with regulatory requirements.

2. Simplify Access Management with Zluri's Automation Engine: From Onboarding to Offboarding
Managing employees' access starts as soon as they join the company. The IT team is responsible for ensuring the employees have the right access to required apps from day one. However, if the provisioning process is handled manually, there is a higher risk of errors, which can impact productivity and efficiency.
- Ensuring the Right Employees Have the Right Permissions Zluri streamlines access management during onboarding by linking user profiles to their digital identity. So that when your IT team verifies user identity for granting access, they can easily cross-check and access the user data from a centralized dashboard. This integration ensures precise assignment of access based on job roles.Moreover, Zluri goes beyond that by automating the entire provisioning process, granting new employees secure access with a few simple clicks. By automating the process, your team can ensure the right access is granted to the right employees with the right level of permissions to required SaaS apps and data. That further enhances employees' productivity by enabling them to start working from day one.You must be wondering how Zluri automates the provisioning process. Well, your IT team can create onboarding workflows. All they need to do is select users they want to grant access to or onboard and apps (you can even choose from recommended apps option), which all apps they want the users to access. Then, your team can take necessary actions easily by clicking \"add an action.\" Here, they can schedule the workflow and more.
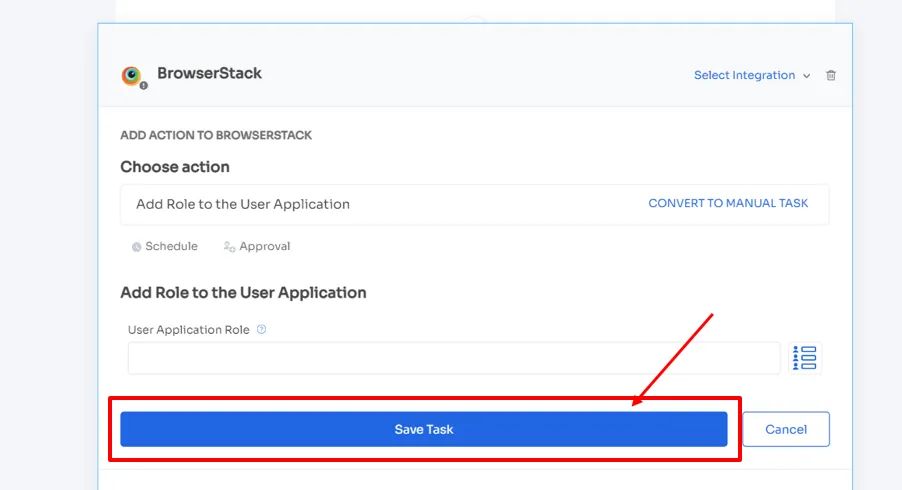
Zluri even provides in-app suggestions, allowing your team to add employees to different channels, groups, or projects or send automated welcome messages.
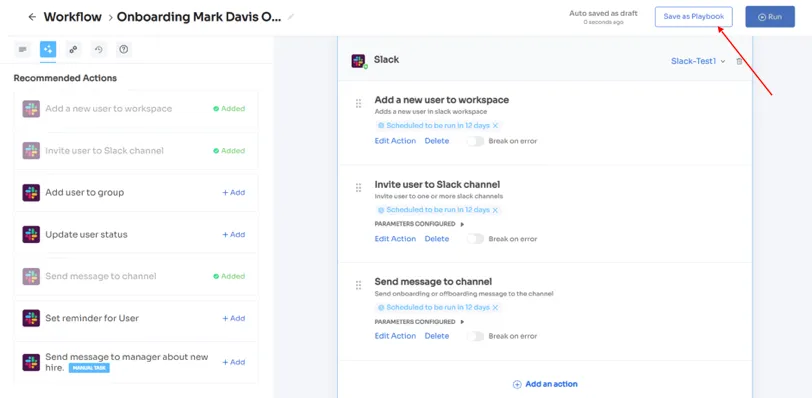
The actions can vary for different applications and are mentioned under recommended actions. Once all the actions are set, you can directly run the workflow or save it as a playbook for future use.
For added efficiency, Zluri offers automated playbooks (i.e., collections of recommended applications for automation) that can be customized for different roles, departments, and designations. This feature streamlines the onboarding of new employees, making it as easy as a few clicks to set up their access.

Note- Apart from that; your team can set automation actions, such as by triggering if and but conditions, they can grant Kissflow access to all the finance department employees.
- Ticketless Access ManagementNow, a crucial stage arises where the possibility of access mismanagement becomes a concern. As employees move to different roles or departments or need access to specific applications for specific tasks, their access needs change. Typically, they have to wait for days to get their app access requests approved, as the manual process involves multiple steps. However, Zluri addresses this issue by automating the time-consuming manual access request process, streamlining and expediting the approval process. Let's take a closer look at how it accomplishes this. In order to stay updated with the changes Zluri integrates with HRSM. With the help of this integration, Zluri automatically retrieves and displays updated employee data on a centralized dashboard. By leveraging this integration, your IT team can easily access and verify employee details without manual effort. This streamlined process ensures that access permissions align with current employee roles and responsibilities. Whether granting or revoking access, your team can efficiently manage user privileges based on the most up-to-date information available.

- It doesn't stop there, Zluri takes a step further to streamline the access request process by making it ticketless. It offers an Employee App Store (EAS), a self-serve model, a collection of applications pre-approved by your IT team. With this self-serve model, employees enjoy the flexibility of choosing any application from the app store and gaining quick access in no time.

- All they need to do is raise a request, and the IT team will verify and review their identity before providing access to the requested application. If approved, employees gain access right away. If access is declined, they receive prompt notifications along with reasons for the decision, any modifications made, or suggested alternatives for the application, all viewable in the \"Changelogs.\"
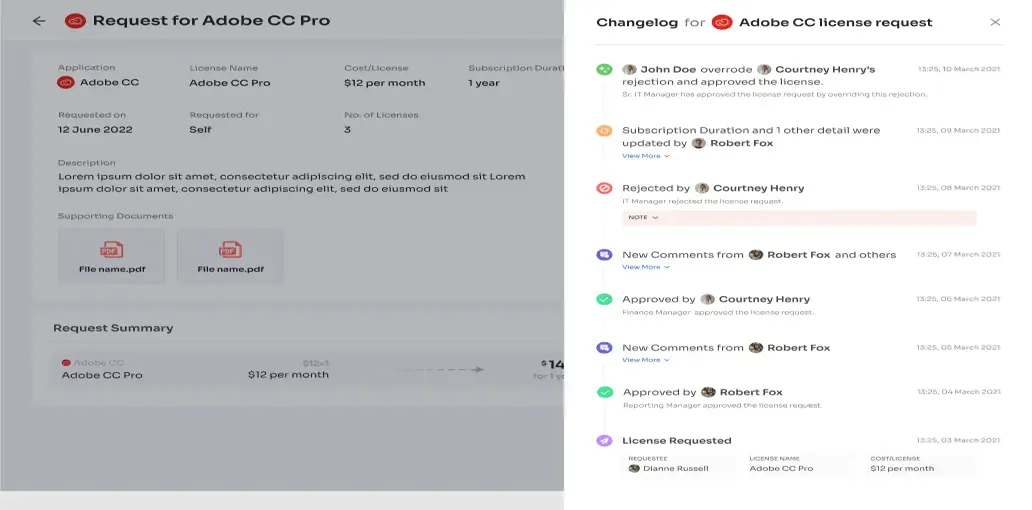
- Revoke Access When Not Required By The employees Revoking access from departing employees or those who no longer require certain application access is a critical task for IT teams. Even a single oversight in this process can potentially lead to security breaches, jeopardizing data security.Zluri recognizes this concern and provides a solution by automating the deprovisioning process. With just a few clicks, your IT team can effortlessly revoke required or all access from employees without missing any crucial steps. This automation ensures timely and thorough revocation, safeguarding SaaS app data from potential security breaches such as unauthorized attempts.Furthermore, to automate the process, your team can simply create an offboarding workflow. All they need to do is select the users from whom they want to revoke app access and then they will come across a list of recommended actions (such as signing out users, removing them from org units, and more).
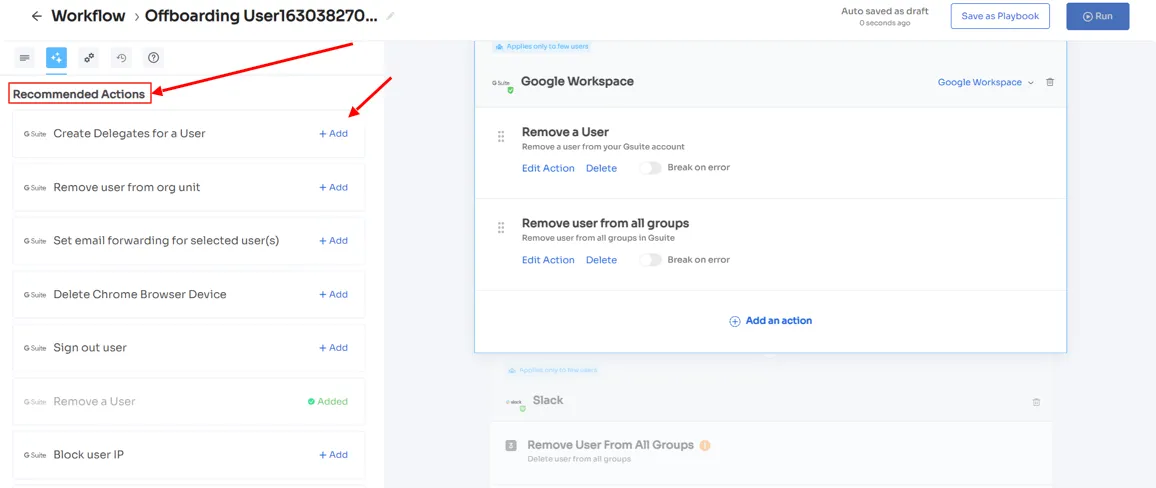
- Your team can choose one or multiple actions at once from the list, a point to note is that these actions will be executed post the deprovisioning process. Once all desired actions are added, your team can run the workflow instantly or save it as a playbook for future use.
3. Automate Access Review Process With Zluri’s Access Certification Feature
The next crucial step in access management is access reviewing, which ensures that every user has the appropriate level of access to apps and data, maintaining data security. However, manual access reviewing can be time-consuming and inefficient, requiring IT teams to gather user lists, user statuses, access patterns, and all the apps to which users have access.
For instance, a user had admin-level access to a specific application, but your IT team revoked those permissions two months ago because they no longer needed such high privileges. However, it's essential to periodically review this user's access to ensure it remains appropriate and that they haven't been granted admin-level permissions again without a valid reason. Manually managing this process would be time-consuming and inefficient.
To address this challenge, Zluri steps in with automated solutions. Zluri automates the entire access review process by collecting all user access-related data in one centralized location. This simplifies the reviewing process for your team or reviewers, removing any complexities and enhancing efficiency.
The capabilities we've discussed so far are just the beginning. Zluri has more exclusive features that set it apart from its competitors, so let’s explore them in detail.
- Unified Access Review
Zluri's unified access review feature empowers your IT team to easily determine which users have access to specific SaaS apps and data. How does Zluri accomplish this? It utilizes an access directory that centralizes all user access-related data in one place.
With the valuable insights provided by the access directory, such as user access permissions (admins, users, or others), the department the user belongs to, and more, your IT team can thoroughly assess users' access privileges and ensure they align with their designated roles.
Furthermore, Zluri's activity & alerts capabilities are crucial in keeping everything running smoothly. This feature offers real-time information on users' recent activities and notifies IT teams about new logins.
Armed with these insights, reviewers can quickly make decisions during access reviews, ensuring that the right individuals always have the appropriate access privileges.
- Automated Access Review No more manual headaches with spreadsheets and JSONs! Zluri takes the hassle out of access reviews by automating the entire process. Just head to Zluri, create a certification, select the apps and users you want to review, and rest the reviewers will review and update you about the compilation via email. So, by automating this process, you get 10 x better results than manual methods and save your IT team's efforts by 70%. Now let’s move ahead and see how it works.
- Once you gain access to contextual data through Zluri’s unified access feature, you can create access rules around these insights. For example, if someone is an admin on Salesforce, you can easily set up a review policy specifically tailored to that scenario.
- Next comes the schedule certification feature, where you can create certifications based on the gathered information. This allows you to take actions based on the insights you've gained. For instance, you can use data like last login, departments, user status (active or inactive), and more to make informed decisions during the review process, such as whether the user can carry on with the existing access or need any modification.As per KuppingerCole’s report, automated access reviews reduce the time to audit readiness from months to weeks.With Zluri's context-rich information, your team can confidently take actions that align with your access management policies. It's a smarter, more efficient way to ensure the right access for the right users, all while keeping your data secure. Zluri's automated access reviews and access rules are the key to simplifying your access governance process.
- Secure access orchestration/auto-remediation Once the access review is completed, changes will take place as per the set actions during certification creation, so all the actions such as access modification or removal are a part of secure access orchestration. This seamless process ensures that access is managed securely and efficiently, safeguarding your organization's valuable data and resources.For example, while creating a new certification in Zluri, your team will encounter the configuration action where they can create deprovisioning playbooks and modify playbooks. If the reviewers decline certain access permissions, the deprovisioning playbook will automatically execute, and the same goes for the modify playbook. Reviewers must also provide relevant reasons for declining or modifying access permissions.Point to note: These actions will take place automatically post the review, that's why this process is also known as the auto-remediation process.
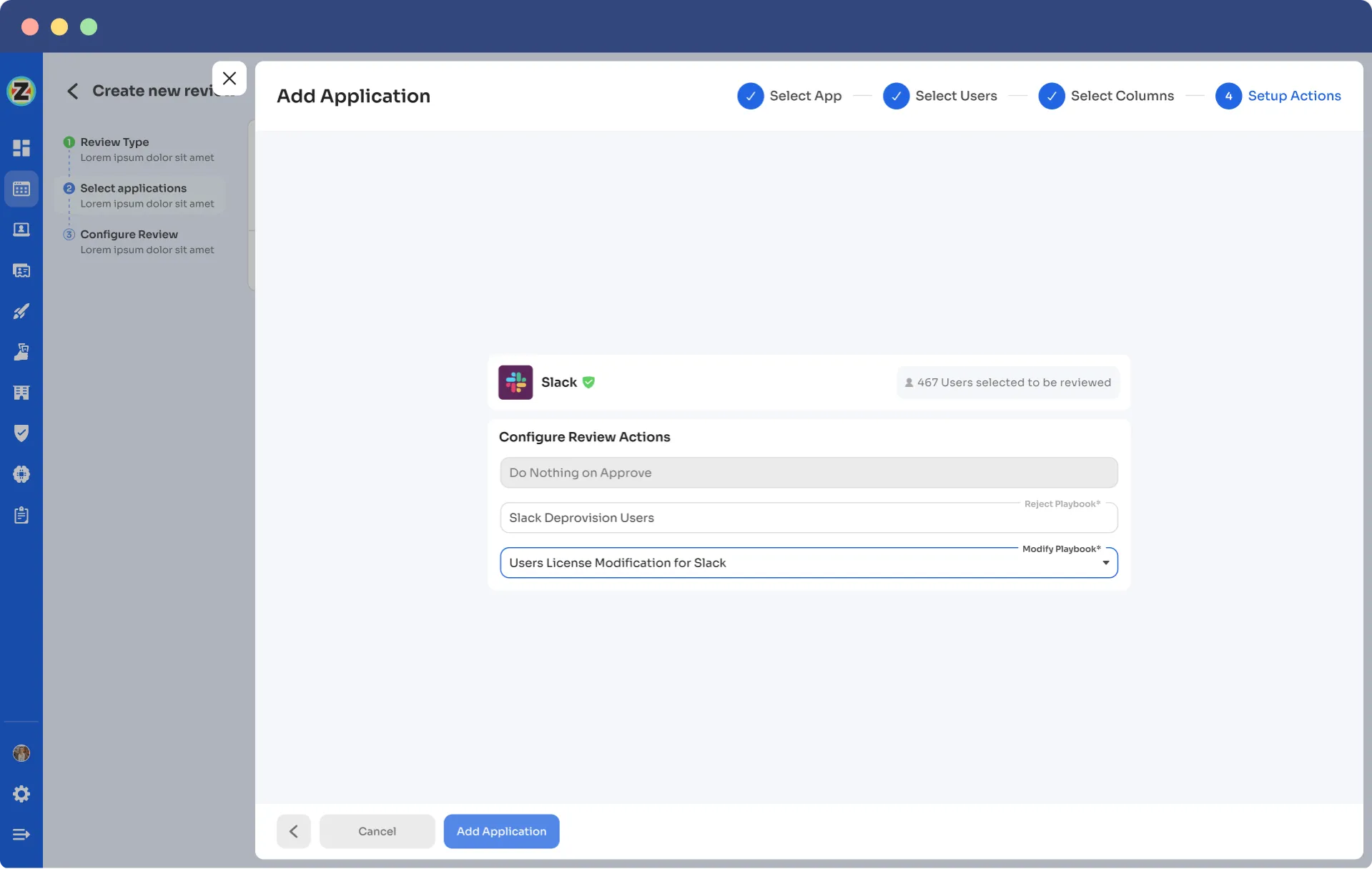
Apart from that Zluri also offers integration features that are quite beneficial at the time of gathering access data. Though Zluri already has data within its platform, but integration allows it to gather even more valuable insights. By leveraging these integrations, it further enhances your access review process and strengthens the overall security posture of the organization.For example, the top priority for the company is to review the Identity System and core applications, as they pose the highest risk. The Identity System, which stores crucial employee data, requires timely and thorough reviews to ensure security. So what Zluri does is it integrates with Salesforce, Okta, Azure, and other applications. Further, these integrations play a crucial role in gathering identity system and SaaS app data, providing valuable insights and streamlining the review process.Additionally, Zluri generates reports that are commonly associated with audit logs or audit trails. These audit reports serve as crucial documentation to share with auditors or keep as references for future reviews. The audit trails act as a roadmap, illustrating the changes made during previous reviews.For example, if an employee's admin-level permissions were changed to user-level, it becomes essential to review and ensure that the access remains appropriate or if there were further changes back to admin. Understanding the reasons behind any upgrades is critical for maintaining proper access control.
So Zluri automatically generates reports on such changes, which further helps in the reviewing process.
So why wait? Book a demo now and witness how Zluri enables your GRC team to streamline identity governance.









.svg)














