Google Drive is a lifesaver when it comes to storing and sharing files. Yet, amid great convenience, a slight sense of concern arises: "Are my files safe? Is Google Drive secure?" It's totally understandable to have these concerns.
However, just by taking a few simple steps to boost your Google Drive security, you can rest easy knowing that your files are safe and secured.
So, let's dive in and ensure you're making the most out of Google Drive's powerful features while keeping your data secure.
Google Drive is a widely used and secure cloud storage application that enables users to store a wide range of data, including documents, recordings, videos, photos, and more. Its popularity is largely due to the integration of G-Suite, which allows users to manage and perform their daily tasks directly within the application.
Furthermore, the accessibility of Google Drive is a significant advantage, as users can access their files from any device with an internet connection, regardless of their location. This flexibility greatly enhances productivity and convenience, making it a go-to choice for teams and organizations alike.
In addition to storage, Google Drive offers many collaborative tools that foster teamwork and efficient communication. These include Gmail for email, Google Docs for document editing and collaboration, Google Slides for presentations, Google Sheets for spreadsheets, and Google Hangouts for video conferencing. These integrated tools simplify collaboration, streamline workflows, and make it easier for teams to work together, whether in the same office or across the globe. Google Drive's comprehensive suite of features makes it an amazing platform for IT teams and users seeking to boost productivity and enhance collaboration.
However, despite these benefits and features, Google Drive security presents certain challenges.
Challenges Associated with Google Drive Security
While Google Drive is a highly secure platform with advanced built-in security features, businesses may still face several challenges when it comes to ensuring the safety and privacy of their data.
- One of the main challenges is external sharing, as users may accidentally expose sensitive information when sharing files or folders with individuals outside of their organization.
- Additionally, insider threats can pose a risk, as well-meaning employees may unintentionally share confidential documents with the wrong people, or a disgruntled employee may intentionally leak sensitive data.
- Further, third-party apps can also be a potential security risk, as Google Drive has an open API that allows third-party apps to integrate with the platform. Some apps may not be secure or can access more data than necessary.
- Account compromise is also a concern, as Google Drive accounts can be hacked through phishing attacks or weak passwords.
To address these challenges and safeguard your Google Drive, businesses must implement additional security measures to minimize the risk of data breaches and unauthorized access to sensitive information on Google Drive.
Why Should You Prioritize Your Google Drive Security?
Securing your Google Drive account is crucial for protecting your business-sensitive data. Here are some reasons why securing your Google Drive account is essential:
- Prevent unauthorized access: By securing your Google Drive account, you can prevent unauthorized access to your data by hackers or other malicious actors. This is particularly important if you store sensitive information on your Google Drive, such as financial data, personal documents, or confidential work files.
- Protect against data breaches: Google Drive is a popular cloud storage platform and is, therefore, a target for cybercriminals seeking to steal sensitive information. Securing your account with strong passwords and other security measures can help protect your data from data breaches and cyber-attacks.
- Safeguard against accidental data loss: Accidents happen, and sometimes we accidentally delete or lose important files. By securing your Google Drive account, you can help safeguard against accidental data loss by creating backups of important files and setting up recovery options.
Now that we have discussed the potential challenges and the significance of safeguarding your Google Drive account, let's dive into some of the most effective best practices you can implement to bolster its security.
7 Best Practices To Improve Your Google Drive Security
Below are the 7 best practices that can help improve the security of your Google Drive account and keep your potential data safe.
1. Stay on Top of Shared Documents with Regular Reviews
Regularly reviewing shared documents on Google Drive is crucial for ensuring the security and confidentiality of your data. When you share a document, you grant access to another person or group who may view, edit, or even delete the file. If you don't regularly review the list of people who have access to your documents, you run the risk of unauthorized access or accidental sharing of sensitive information.
Regularly reviewing shared documents can help you identify any unnecessary or outdated access permissions and remove them promptly, minimizing the risk of data breaches and unauthorized access.
Moreover, if you're sharing documents with colleagues or collaborators, in that case, it's important to keep track of who has access to what, especially when team members leave or change roles within the organization. Hence, it is recommended to remove shared permissions from anyone who no longer needs them.
It helps you control user access and ensures that only the right people can access the right information at the right time.
However, identifying all the files you've shared on Google Drive can be challenging, as the platform doesn't provide a comprehensive list of outgoing shared files. The advanced search feature doesn't include a filter for this purpose, and the "Shared with me" section only displays incoming shared files. Therefore, the only way to determine who can access a file or folder is to open its sharing menu and review the list of shared users.
2. Use Endpoint Management In G-suite
Endpoint management in G Suite is essential for several reasons.
- Like it enables admins to enforce security policies for all endpoints that have access to Google Drive.
- You can manage which laptops, desktops, and other endpoint devices have access to the data belonging to your company and obtain information regarding those endpoints.
- You can restrict access to Google Drive to only authorized devices, ensuring that sensitive data is not accessed on unauthorized devices. This helps to prevent data breaches and ensures that data is accessed only by authorized personnel.
- It allows admins to monitor and manage devices that access Google Drive. This means you can remotely wipe data from a lost or stolen device or revoke access to a device if an employee leaves the organization. This helps to protect sensitive data and prevent unauthorized access.
- Further, endpoint management enables admins to deploy and manage applications on endpoints that access Google Drive. This allows them to ensure that all necessary applications are installed on endpoints and that they are up-to-date.Lastly, this helps to improve productivity and reduce the risk of Google Drive security vulnerabilities.
3. Follow data encryption before transfer
Data encryption is one of the major security steps that you can follow. It is the process of converting plain text or data into an unreadable format that can only be read with a decryption key. Encryption protects sensitive information from unauthorized access, interception, or theft.
Encryption ensures that even if someone gains access to your data, they cannot read or use it without the encryption key. This helps protect against unauthorized access to your sensitive information.
Encrypting your data before transfer adds an extra layer of privacy, as only the intended recipient with the encryption key can access and decrypt the data. It's a best practice to ensure the security and privacy of your sensitive information.
Although Google encrypts the data stored on its servers, you can further increase the security and privacy of your data by encrypting it on your own systems before sending it to Google Drive. This can be done using third-party solutions such as Boxcryptor or Cryptomator.
4. Adopt a 2-factor authentication method
Two-factor authentication (2FA) is an effective security strategy that adds an extra layer of protection to your Google Drive account. 2FA adds a layer of security beyond just a password, making it more difficult for hackers to access your account.
Even if your password is compromised through a data breach or other means, 2FA can prevent hackers from accessing your account since they would also need access to the secondary factor (such as a code generated by an app or sent to your phone) to log in. Even if you unknowingly provide your password to a hacker, they would still need the secondary factor to access your account.
Therefore, using two-factor authentication in Google Drive protects against password breaches and phishing attacks and complies with security best practices.
By taking just a few extra seconds to enter the code each time they log in, users can help ensure the security of their accounts and prevent unauthorized access to their sensitive information.
5. Conduct Audits of Linked Apps on Google Drive
Auditing linked apps in Google Drive helps you identify which third-party applications can access your Google Drive data. This allows you to ensure that only authorized apps are accessing your data. It allows you to identify potential vulnerabilities in your security setup and address them before hackers can exploit them. This can help prevent data breaches and protect your sensitive information.
To ensure the security of your account, it's important to verify that you still trust and use all the apps you have linked to Google Drive. To do this, click the settings cog at the top-right corner of the Drive window, then navigate to settings > manage apps. You'll find a list of apps connected to your Google Drive account here.
You can use the "Use by default" option to select an app to open compatible files from your Drive. For example, you can open JPEGs in a photo editor. You may also see deleted apps using "hidden app data." If you wish to remove an active app, click "Options" and select "Disconnect from Drive". You can choose "Delete hidden app data" from the "Options" menu to remove any leftover files for inactive apps.
6. Data classification
Data classification is critical for improving Google Drive security since it helps identify and prioritize the data based on its sensitivity and potential impact on the organization. By categorizing the data, IT teams can apply appropriate security controls to protect it from unauthorized access, modification, or disclosure.
By applying different levels of protection to different types of data, you can ensure that your organization's most sensitive information is safeguarded.
For example, sensitive or confidential data such as financial records, personal identifiable information (PII), or trade secrets should be classified as high-risk and stored in secure folders with restricted access permissions.
On the other hand, non-sensitive data such as marketing materials or public reports can be classified as low-risk and stored in folders with less strict access permissions.
7. Backup your data
Data backup is essential for improving Google Drive security because it provides a reliable copy of your data in case of accidental or intentional loss, damage, or corruption. With regular backups, you can recover your data quickly and minimize the impact of any data loss incidents, such as hardware failure, malware attacks, or human error.
Furthermore, backups can help you maintain data integrity and ensure you can access and use your data when needed. In case of any data corruption or deletion, you can restore the data from the backup and avoid potential data loss.
By backing up your data regularly, you can reduce the risk of data loss or damage, improve data availability and integrity, and enhance your overall data security posture. Google Drive provides several backup options, such as Google Drive Backup and Sync, which can help you automate and simplify the backup process.
While we've just covered some essential best practices for enhancing your Google Drive security, it's important to also address the broader context of SaaS security. Fortunately, we have a solution to bolster your SaaS security as well
Simplify Your SaaS Security With “Zluri”
Effectively managing SaaS data security poses a significant challenge for IT teams. However, a well-handled approach to SaaS security can offer organizations substantial benefits by safeguarding their sensitive data from potential cyber-attacks and data breaches. Consequently, organizations relying on SaaS applications should proactively implement measures to fortify both their data and reputation.
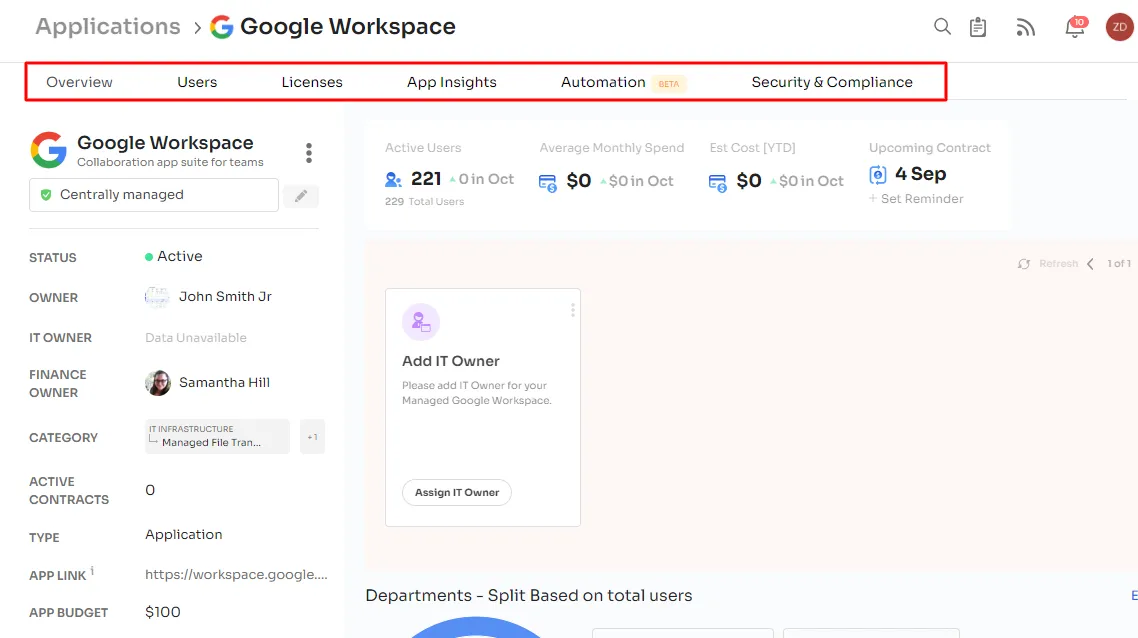
Zluri, a leading SaaS management platform, presents a comprehensive SaaS security solution. It offers a clear overview of the organization's SaaS landscape, providing IT teams with detailed insights regarding SaaS app’s security and compliance. Moreover, Zluri facilitates a seamless user lifecycle management process, encompassing smooth onboarding, efficient mid-lifecycle adjustments, and streamlined offboarding procedures.
Here are few ways in which Zluri help you in SaaS app security assessment:
- Comprehensive Assessment: Zluri conducts a thorough evaluation of applications, meticulously seeking out potential security risks.
- Multi-faceted Evaluation: The assessment encompasses critical aspects like architecture, configuration, data flow, and vulnerability scans.
- Intuitive Dashboard: Zluri provides an easy-to-use dashboard post-assessment, custom-tailored for critical apps and users.
- Rich Information Representation: The dashboard distills findings into an accessible format, offering unmatched insights into security and compliance.
- Event Tracking to Data Insights: Covers a wide spectrum, from event tracking to shared data, enhancing security measures comprehensively.
- Meticulous Logging: Maintains detailed, auditable logs of significant activities, ensuring continuous awareness and control over security posture.
- Risk Identification and Scoring: Identifies risks and assigns a risk score to each SaaS application, aiding IT admins in prioritizing security efforts.
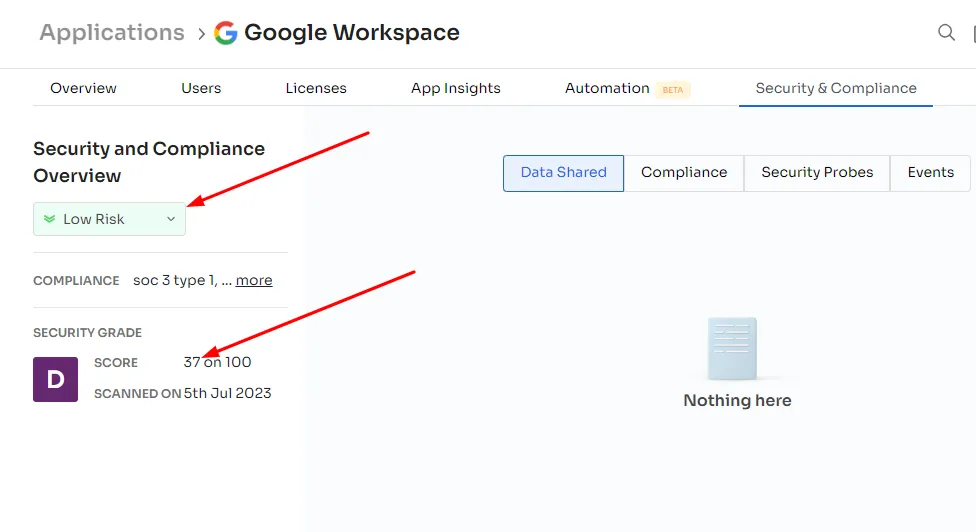
Are you wondering on what basis Zluri assigns a risk score to every SaaS app?
Zluri employs a four-factor risk scoring system for SaaS apps to assist IT admins in understanding potential risks.
1. Events (Recent Security Breaches):
Zluri continuously monitors security breaches related to SaaS apps. It displays data from internet sources under the events tab, including event dates and security impact assessments. This data influences the app's overall risk score.
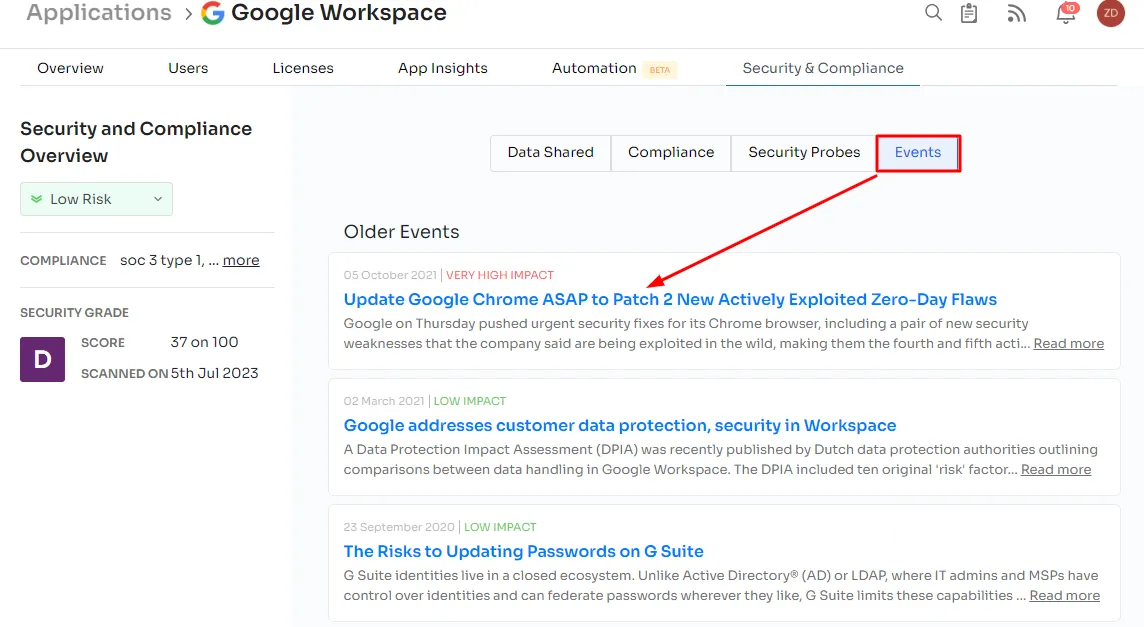
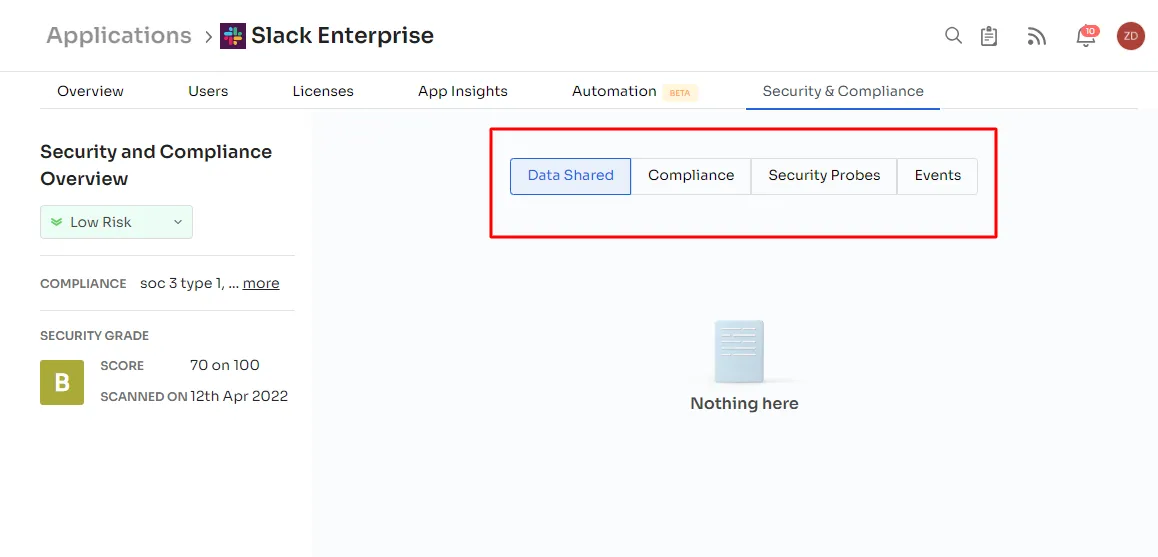
2. Data Shared:
Zluri evaluates user access levels and shared data to assess the threat level of an app. Higher access levels and critical data actions lead to a higher threat level. For e.g., an app with delete access to Google Drive data is considered riskier than one with read-only access to Google Mail.

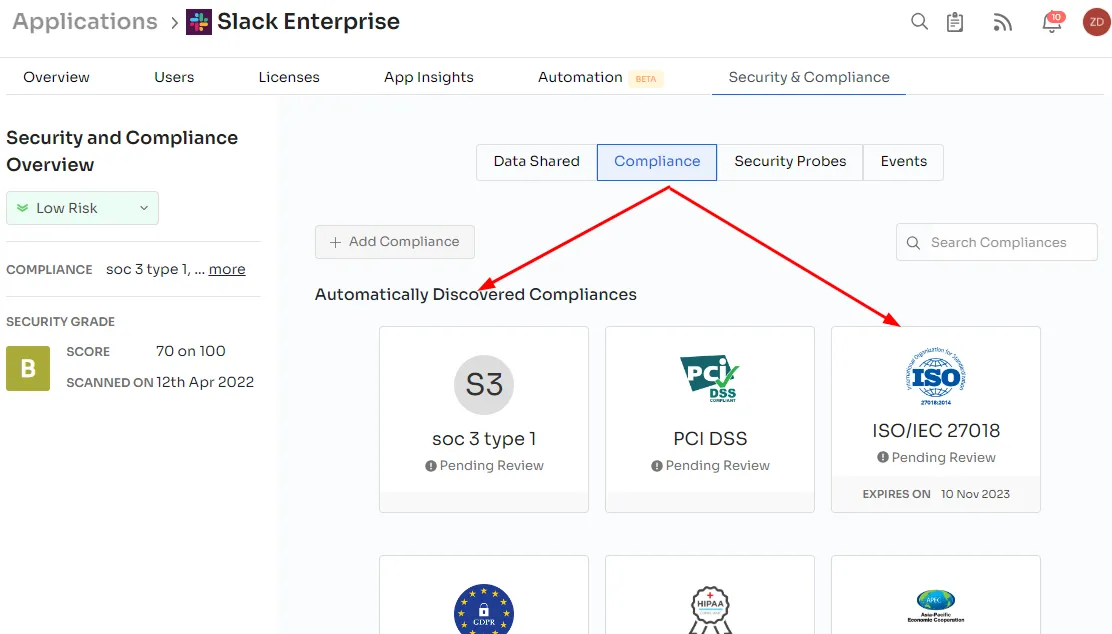
3. Compliance:
Zluri considers compliance with various standards and regulations when calculating the risk score. Apps adhering to more compliances are deemed more secure.For example, Slack complies with major global standards, making it more secure.
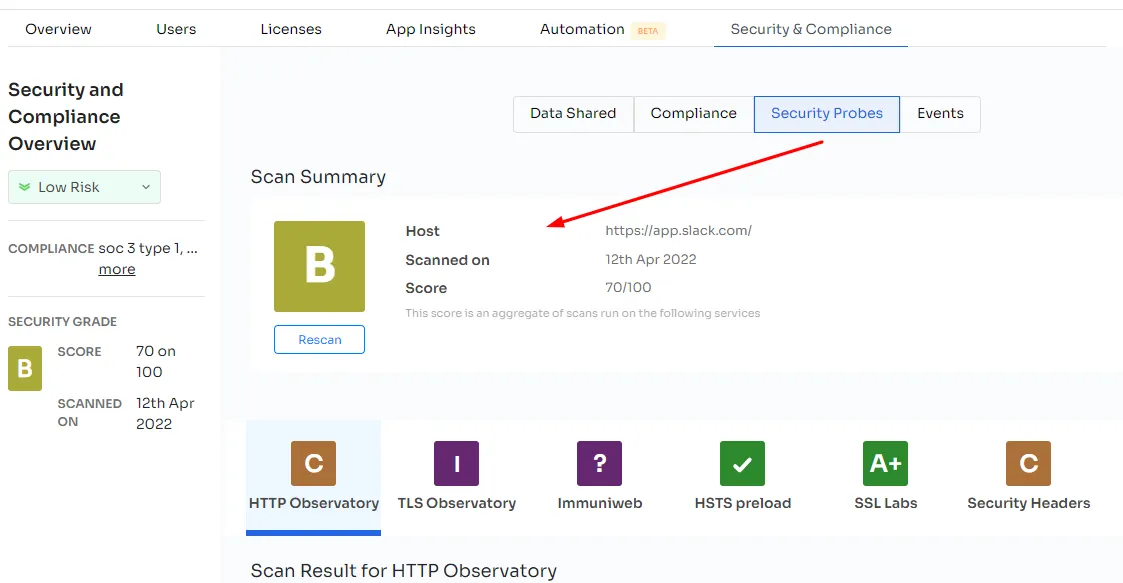
4. Security Probes:
Zluri gathers security data by scanning third-party websites like ssllabs, Immuniweb, and imirhil. It calculates a weighted average of security grades from A to F and displays results on the dashboard. Real-time scanning is available by clicking the Rescan button.
Zluri assigns security score ratings from 1 to 5 based on these factors. Ratings of 1 and 2 indicate low risk, 3 signifies medium risk, and 4 or 5 denote severe risk.
Moreover, Zluri uses secure encryption algorithms to encrypt and safeguard all sensitive data. The platform provides a detailed and trackable record of key activities, enabling you to monitor your app's security effectively. All data is stored in an encrypted state and backed up for a duration of 60 days. Data collected, including SaaS-app usage metrics, is retained indefinitely unless a removal request is submitted.
Want to know more??









.svg)



.svg)
.svg)
.svg)
.svg)

.svg)

.svg)

.svg)
















.webp)







.webp)
.webp)





.webp)