As organizations scale, managing user access becomes increasingly fragmented and difficult to control. Permissions can become inconsistent, leading to security gaps, as users may retain access long after their roles change or depart. Group based access control is the solution to this concern. Read on to learn more about it.
Studies show that 63% of organizations struggle with managing access permissions across their workforce, causing confusion and compliance risks. With growing security demands and stricter compliance standards, adopting a structured access control model like group based access control is no longer optional—it’s a necessity for modern businesses.
In this blog, we’ll explore group based access control, its key benefits, the challenges organizations face when implementing it, and best practices for successful adoption.
What is a Group Based Access Control?
Group based access control (GBAC) is a security model in which users are granted permissions based on their group membership rather than individually. This approach simplifies access management by organizing users into logical groups—such as departments, roles, or teams—and granting permissions based on the resources each group requires.
Instead of configuring individual permissions, group based access control allows access to be managed at the group level, which reduces administrative workload, minimizes human error, and ensures the right people have the right access.
Consider your company with three departments: HR, Finance, and IT, each needing access to different systems:
- HR requires access to user records and payroll systems.
- Finance needs access to financial software and budgeting tools.
- IT needs admin access to network systems and security tools.
Without GBAC, manually assigning permissions to each user is not only time-consuming but also prone to mistakes. For instance, a Finance user might accidentally get HR access, or an IT team member could be granted unnecessary access to payroll systems.
With GBAC, you create user groups- HR, Finance, and IT- and assign the appropriate permissions to each. When users move between departments, you simply update their group membership, automatically adjusting their access rights.
Implementing group based access control boosts security and streamlines processes, saving time for IT teams.
Key Components of Group Based Access Control
Let's explore the key components of group based access control.
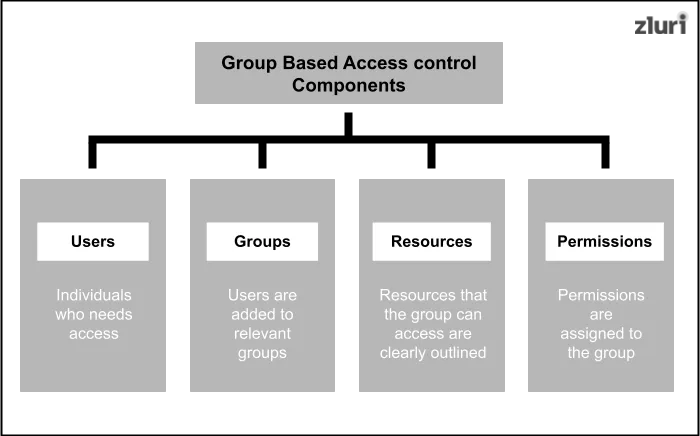
1. Users: Users are the individuals who need access to the systems or data. Each user is assigned to one or more groups, and their access permissions depend on the groups they belong to. For example, an IT manager might be a part of both the "IT team" and "Admin team" groups, inheriting permissions from each.
2. Groups: Groups are collections of users with similar roles or needs. Permissions are granted at the group level to streamline management and reduce errors. For instance, the "Finance team" group can access financial reports, while the "Support Team" group can manage ticketing systems.
3. Resources: Resources include systems, files, or data users need to access. Groups are linked to these resources to define who can read, write, or edit them. For instance, only the "HR team" group may access user records, ensuring data privacy.
4. Permissions: Permissions define actions users can perform on a resource, such as "read," "write," or "execute." Assigning permissions at the group level ensures consistency and simplifies updates. For instance, a group may have "read-only" access to reports, preventing unauthorized modifications.
Benefits of Implementing Group Based Access Control
Group based access control offers several advantages for managing permissions in modern organizations. It not only simplifies user management but also strengthens security and supports scalability. Let's look at the key benefits:
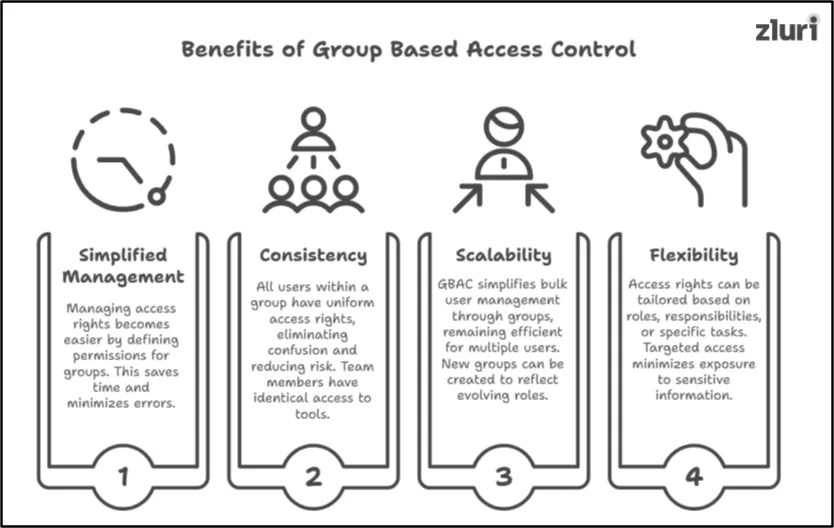
1. Simplified Management
Managing access rights becomes easier with GBAC. Instead of assigning permissions to each user individually, you define permissions for groups. For instance, when onboarding a new user, you simply add them to an appropriate group. If someone switches roles, moving them to a new group updates their access seamlessly. This streamlined approach saves time and minimizes errors.
2. Consistency
Group based access control ensures that all users within a group have uniform access rights. This standardization eliminates confusion, reduces the risk of unauthorized access, and promotes accountability. For example, team members in the Marketing group will have identical access to tools and systems, creating a consistent and secure workflow.
3. Scalability
As your organization grows, managing access for an expanding workforce can be challenging. GBAC simplifies this by allowing bulk user management through groups. The process remains efficient whether adding, removing, or updating access for multiple users. Additionally, you can easily create new groups to reflect evolving roles or teams, ensuring scalability for businesses of any size.
4. Flexibility
With group based access control, you can tailor access rights based on roles, responsibilities, or specific tasks. For example, the HR group can access users' records, while the Finance group views financial data. This targeted access minimizes exposure to sensitive information and ensures users only access what they need, enhancing both security and efficiency.
Also Read: To learn more about managing role-based access, check out this guide on Role-Based Access Control
Challenges of Implementing Group Based Access Control
While group based access control offers significant benefits, implementing it comes with challenges that organizations must address. Let's explore these:
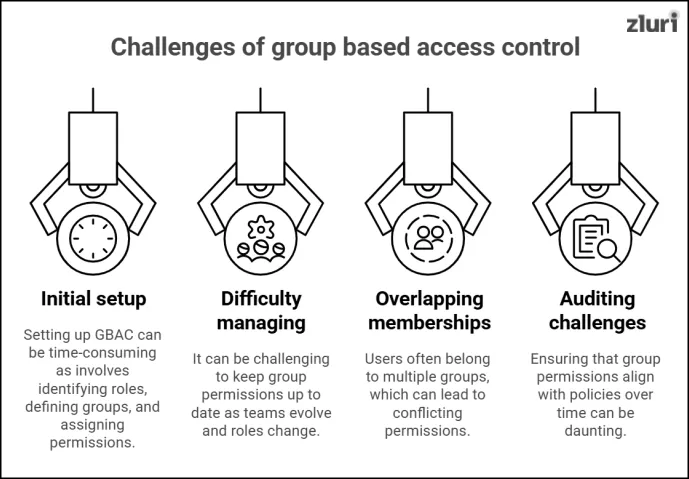
1. Initial setup complexity
Setting up group based access control can be time-consuming. It involves identifying roles, defining groups, and assigning permissions. This process requires careful planning to avoid errors leading to incorrect access rights. For instance, if permissions are misconfigured during setup, it might disrupt workflows or expose sensitive data, compromising security.
2. Difficulty in managing groups
It can be challenging to keep group permissions up to date as teams evolve and roles change. Outdated settings may persist without regular reviews, leading to security gaps or unnecessary restrictions. For example, a former project group may still retain access to resources long after the project ends, creating potential vulnerabilities.
Also Read: Understand the importance of reviewing access rights regular with this user access review guide
3. Overlapping group memberships
Users often belong to multiple groups, which can lead to conflicting permissions. For instance, a manager in both the "Finance" and "HR" groups might have overlapping or contradictory access rights. Resolving these conflicts requires a clear hierarchy or priority system for permissions, which can be complex to implement effectively.
4. Auditing challenges
Ensuring that group permissions align with policies over time can be daunting. Periodic audits are essential but can become complicated as permissions drift from the original setup due to evolving roles or system changes. This increases the risk of non-compliance, making demonstrating adherence to regulatory standards more difficult.
Best Practices for Implementing Group Based Access Control
Once you’re aware of the challenges, let’s explore the best practices for implementing group based access control to overcome them.
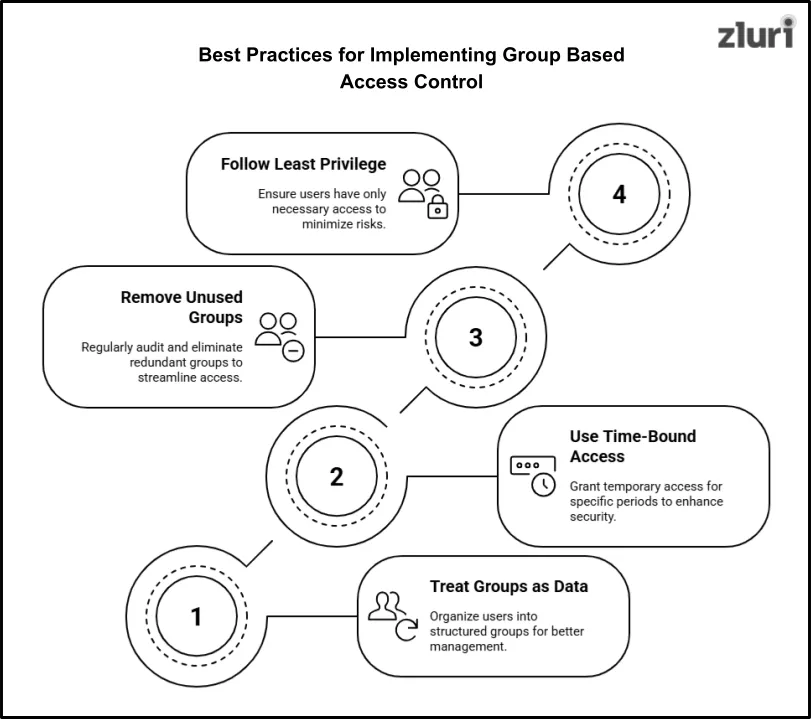
1. Treat Groups as a Data Structure
Think of groups as more than just buckets for organizing users—they're like building blocks in your access control system. When you treat users as structured data models, managing permissions becomes less chaotic and a lot more predictable.
Start by giving each user a clear purpose. For example, instead of dumping all finance users into one big "Finance" group, you could create smaller, more specific groups like "Finance_Viewers" for read-only access and "Finance_ADmins" for full control. This way, permissions are tightly aligned with actual roles, and there's no confusion about who can do what.
Now, let's discuss naming your groups. Imagine you're looking at a list of group names—would you know what each one does? If not, it's time to introduce some naming conventions. Names like "HR_Records_ReadOnly" or "IT_Support_Admin" instantly tell you the group's purpose. It might seem like a small detail, but it saves time, avoids errors, and makes audit seamless.
Also, be picky about who gets added to each group. Set rules upfront about membership—like only the HR team can access user records—and stick to them.
A quick tip: Avoid creating groups just to solve quick, one-off access issues. Temporary fixes can pile up fast and lead to a tangled mess of groups that nobody can manage properly.
Another bonus? When groups are treated as structured data, compliance checks become much easier. Auditors love systems that are well-organized, and so will you when it's time to prove that permissions are under control. Tools like AD or Okta can even help automate some of this structure, so you don't have to track everything manually.
The bottom line is that structured groups keep your access control system clean, scalable, and aligned with our organization's goals. Plus, this group based access control best practice saves you from headaches when users change roles or when audit season rolls around.
2. Use Time-Bound Access
Not everyone needs permanent access to every resource- and that’s where time-bound access comes in. Instead of granting permissions indefinitely, you assign access for a specific period. Once that time is up, the access automatically expires. It’s like giving someone a guest pass that works only for the duration of their visit.
This approach is especially useful for temporary projects, contractors, or users working on short-term assignments. For example, if a consultant is hired to review financial data for a month, you can add them to a group with the required permissions and set an expiration draw. Once the project ends, their access is revoked automatically—there is no need to remember them manually.
Also Read: Explore these 4 ways of revoking user access
Time-bound access also comes in handy during role transitions. Say a user is temporarily filling in for a manager on leave. You can grant elevated access just for the duration of the manager’s absence and let it roll back to standard permissions afterward. This reduces the risk of unnecessary access lingering after temporary tasks are completed.
Also Read: How to control access & streamline mid-lifecycle changes for individual apps
Many identity and access management (IAM) tools, like Okta and Azure AD, let you automate time-based permissions to make this process even smoother. You can set start and end dates right when you create a group or assign access. Alerts can also notify you before permissions expire, giving you the chance to review and renew access if needed.
The best part? Time-bound access minimizes security risks and simplifies audits. Instead of sifting through piles of permissions to figure out who still has access, you’ll know that expired permissions have already been cleaned up.
By limiting access to only when needed, you strike the perfect balance between security and flexibility—keeping your systems safe without slowing down productivity.
3. Identify and Remove Unused or Redundant Groups
Over time, your group based access control system can become cluttered with unused or redundant groups. It’s like having a closet full of clothes you never wear—taking up space and making it harder to find what you actually need. That’s why regularly identifying and removing unnecessary groups is a crucial best practice.
First, take a good look at your groups. Some might have been created for short-term projects or temporary teams, but after time, those groups might no longer serve a purpose. A simple audit can help you identify groups that are no longer in use. For example, a group for a marketing campaign that wrapped up months ago or a team that no longer exists should be cleared out.
But it’s not just about removing inactive groups—redundancy can sneak in, too. Maybe you’ve ended up with two different groups with the same members and permissions. This can happen when roles evolve or when groups are created without proper documentation. In these cases, you’ll want to consolidate groups to eliminate unnecessary duplication.
The benefits of this practice are clear:
- Security: Fewer groups mean fewer potential access points, making it easier to ensure that only the right people have access to sensitive data.
- Efficiency: It’s much simpler to manage a leaner, cleaner group of groups, which helps you stay organized and responsive to changes.
- Compliance: Regularly cleaning up your groups makes it easier to pass audits and stay compliant with security standards, as you’ll have a well-maintained access control system.
Automating this process can save you time and effort. Tools like Okta and AD can help you track group usage and set reminders for periodic reviews. Some IAM solutions even flag redundant groups automatically so you can easily identify them and take action.
In short, following this group based access control best practice, i.e., by removing unused or redundant groups, you streamline your access control system, reduce security risks, and make your overall management much more efficient. It’s a small task with big rewards in terms of simplicity and control.
4. Follow the Principle of Least Privilege
The principle of least privilege is one of the cornerstones of a secure access control system, and it’s simple to grasp: give users only the access they absolutely need to do their jobs—and nothing more. Think of it like giving someone a key to just the room they need to access rather than handling them the entire building’s keyring.
This approach minimizes the risk of accidental or intentional misuse of sensitive data. For example, if someone in the IT department only needs to read logs for troubleshooting, they shouldn’t have to write admin permissions on those logs. By strictly limiting permissions, you reduce the potential for human error and the impact of any potential breaches.
A practical way to implement the PoLP is through RBAC or Attribute Based Access Control (ABAC). With RBAC, you assign users to groups based on their roles and responsibilities, making it easy to ensure that they only get the permissions required for their specific tasks. With ABAC, you can take a more fine-tuned approach by setting permissions based on user attributes (e.g., job title, department, location).
Additionally, regularly review permissions to ensure that users still need the access they have. Users often shift roles or move departments, and over time, you might find that someone has accumulated excessive access rights. Regular reviews and automated access controls can help you keep track of this and previous “permission creep.”
Implementing the PoLP also means granting temporary elevated permissions when necessary. For example, if a team member temporarily needs access to a specific system to perform a task, you can grant them access for just the duration of that task and remove it once it’s completed.
By following this principle, you’re creating a safer environment where users have just the access they need, reducing risks and improving overall security. Plus, it makes audits and compliance checks easier because it’s clear who has access to what and for what purpose.
To implement group based access control efficiently, always grant the minimum level of access needed. Avoid giving extra permissions, even for temporary tasks. Moreover, regularly review permissions to ensure they remain relevant.
Following this best practice—least privilege—will reduce the chances of accidental misuse or insider threats. It will also protect your organization’s sensitive data and critical systems. This practice also aligns with compliance standards, making audits easier to handle.
Optimize Security & Streamline Access Management with Group Based Access Control
Group based access control is more than just a way to manage permissions—it’s a step towards better security, streamlined operations, and consistent access policies. Yes, setting it up takes effort, and keeping it updated can feel daunting, but the benefits far outweigh the challenges.
With tools like Zluri, you can simplify the entire process. Its access management solution automates group assignments, manages changes effortlessly, and ensures your organization stays secure and compliant. It’s about building a system that works for you today and grows with you tomorrow.






.svg)














