Data breaches are inevitable. For IT managers responsible for safeguarding sensitive information, it's not a question of if, but when. The consequences affect your organization's reputation, security, finances, and operations. Thus, this article will walk you through the common causes of data breaches.
Human error, such as weak passwords and falling for phishing scams, often leads to data breaches. This can expose confidential data, causing severe financial and reputational damage.
One major challenge is the lack of awareness and training among employees. With the integration of cloud services, mobile devices, and third-party applications, the attack surface expands, making it easier for cybercriminals to find vulnerabilities.
The solution lies in implementing robust security measures, providing regular employee training, and staying updated with the latest cybersecurity practices can help prevent data breaches.
Now, we will discuss the major causes of data breaches and how to mitigate these risks effectively.
The Major Causes of Data Breaches
Understanding data breaches and its major causes is crucial for implementing effective strategies to safeguard sensitive information.
Human-centric factors
Let’s delve into the human-related factors contributing to data breaches and actionable insights for prevention and mitigation.
1. Social Engineering and phishing attacks
Social engineering and phishing attacks are the top causes of security breaches due to their exploitation of human psychology. These attacks manipulate people into revealing sensitive information or compromising security.
They thrive on trust, using emotions and authority to trick individuals. Phishing emails mimic trusted sources, duping victims into sharing data. These attacks occur via various channels, boosting their success chances. Impersonation of authoritative figures lends credibility.
What makes them impactful is their focus on human behavior over technical skills. Even cautious people can fall victim to these well-crafted schemes. Detection is tough because attackers play on psychological vulnerabilities, often bypassing traditional security tools.
A single human error can lead to significant breaches. Thus, emphasizing security education is crucial. As tactics evolve, regular training is vital to recognize evolving threats. While user awareness is pivotal, no defense is absolute. A comprehensive strategy, integrating technology and education, is essential to minimize risks from these manipulative cyber threats.
2. Weak Authentication Practices
Weak authentication practices are pivotal in security breaches, providing an open doorway for unauthorized access to accounts and systems. This vulnerability arises primarily from poorly managed passwords and the lack of multi-factor authentication (MFA).
Password vulnerabilities and reuse are common pitfalls that attackers exploit. Weak passwords, such as \"password123,\" are easily cracked using automated tools that systematically test various combinations. Furthermore, the reuse of passwords across multiple accounts amplifies the risk. If one account is compromised, an attacker gains a potential entry point to other accounts, potentially leading to breaches.
To fortify security, multi-factor authentication (MFA) is a key strategy. MFA introduces an additional layer of verification beyond the traditional password. This commonly involves something the user knows (password) and something they have (a smartphone or security token). Even if an attacker can acquire a password, they would still require the second authentication factor, which is far more challenging.
The implications of employing weak authentication mechanisms, however, are profound. The aftermath of data breaches exposes sensitive information, leading to financial loss, identity theft, and damage to reputation. Breached accounts can also be exploited for malicious purposes, while organizations may face legal consequences for non-compliance.
3. Insider threats
Insider threats involve authorized individuals deliberately misusing their access to an organization's systems for personal gain or harm. Unlike accidental errors, these actions are intentional and can result in significant breaches. The complexity of insider threats lies in several factors.
Insiders enjoy trusted access, making their activities harder to detect than external attackers. Their familiarity with systems and protocols allows them to navigate under the radar, increasing the challenge of identifying their actions.
Motivations behind insider threats often revolve around financial gain. Authorized users exploit their access to pilfer valuable data, intellectual property, or sensitive information for personal profit or advantage. This sets them apart from external hackers who may have different motivations.
The difficulty in detecting insider threats arises from their ability to mimic legitimate activities. Their insider knowledge enables them to circumvent security measures and avoid arousing suspicion. Often, these threats are unearthed during forensic examination after the individual has left the organization, further complicating prevention.
Insider threats are indeed complex and challenging to prevent entirely, but a proactive and comprehensive approach to security can significantly mitigate the risks they pose to an organization's data and operations.
Technical factors
Let’s delve into the tech-related factors contributing to data breaches.
1. Malware and Ransomware
Malware is malicious software that stands as a formidable adversary in cybersecurity. It embodies a wide array of software designed with malicious intent to breach, exploit, or gain unauthorized access to computer systems and data. Its diverse forms include viruses, worms, Trojans, spyware, adware, and particularly pernicious ransomware.
These malicious entities infiltrate systems through vulnerabilities within applications or operating systems. Their success often hinges on exploiting unpatched software or outdated security measures. Attackers use tactics to introduce malware, such as phishing emails, infected attachments, compromised websites, and manipulative social engineering ploys.
Within this landscape, one particularly menacing manifestation of malware is ransomware. This specific variant takes cyber attacks to a dire level by encrypting victims' crucial files, accompanied by a demand for a ransom payment in exchange for the decryption key.
Moreover, the repercussions are profound: your entire organization can be brought to a standstill, grappling with financial losses, tarnished reputations, and legal ramifications. However, even if you choose to pay the ransom, there’s no guarantee that you will regain access to your data or be safe from future attacks.
2. Unpatched Software and System Weaknesses
Unpatched software and system weaknesses are prime catalysts for security breaches. Every software has vulnerabilities that hackers can exploit. Vendors release patches to mend these vulnerabilities, but the problem arises when users delay or ignore updates.
Attackers actively search for unpatched vulnerabilities to breach systems, gaining unauthorized access and causing data breaches. This delay gives hackers a window to target vulnerable systems.
Attackers are quick to reverse-engineer patches, crafting attacks for unpatched systems. To counter these risks, prompt patching is vital. Regularly updating software reduces vulnerability exposure and lessens the chance of breaches. Implementing security practices, like least privilege access and intrusion detection, further bolsters defenses.
While vulnerabilities are inherent, the key lies in swiftly applying patches and maintaining proactive security measures to thwart potential breaches stemming from unpatched software and system weaknesses.
Identity governance and administration (IGA) serves as a critical defense against the major causes of data breaches by orchestrating the management and protection of user identities, access rights, and permissions within an organization's IT infrastructure.
IGA solutions are pivotal in establishing controlled access to critical resources, monitoring user activities, implementing security policies, and maintaining adherence to regulatory compliance benchmarks. One such solution is Zluri. Let’s explore how Zluri’s capabilities help prevent data breaches and enhance security.
Ensuring Data Breach Prevention with Zluri's IGA Excellence
Zluri's advanced identity governance and administration (IGA) platform is a game-changer in keeping your organization's data safe. It simplifies access management by following the principle of least privilege, reducing complexities that could slow down productivity.
Zluri's intelligent automation lets your IT team effortlessly handle user access, ensuring the right people have the right permissions and stopping unauthorized access attempts.
The platform's easy-to-use interface takes the stress out of managing access, freeing up your team to focus on essential tasks. Zluri's IGA also takes data security seriously. It allows secure access management from anywhere, catering to flexible work needs. Even as your team accesses data remotely, the platform ensures that sensitive information remains confidential and intact.
Role of Zluri's data engine in preventing data breach
The role of Zluri's data engine in preventing data breaches is nothing short of transformative for IT managers like yourself, aiming to bolster productivity while maintaining an airtight security posture. Zluri's advanced data engine is the cornerstone of its IGA solution, fundamentally enhancing your organization's defense mechanisms against the ever-looming threat of data breaches.
This data engine capitalizes on a diverse array of nine discovery methods, strategically encompassing MDMs, IDPs & SSO, direct integration with apps, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extension (optional).
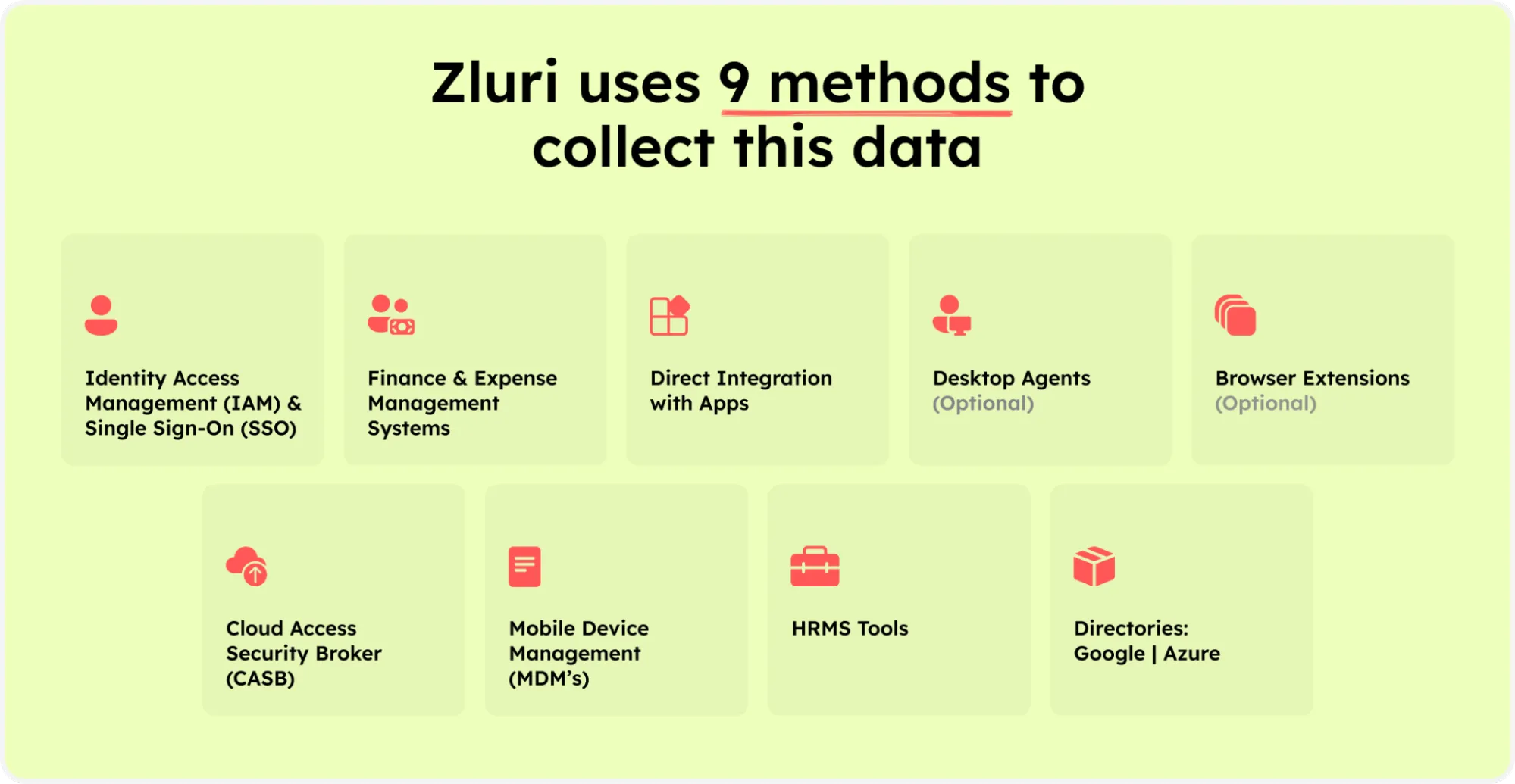
Zluri’s nine discovery methods
Through these methods, Zluri facilitates a smooth analysis of crucial SaaS apps and user data, enabling you to discern application access, track active users, manage permissions, and even identify critical organizational users.
Zluri's data engine goes beyond analysis – it drives automated efficiency. This means your team is freed from laborious tasks as the platform autonomously identifies managed, unmanaged, and shadow IT apps. This proactive approach saves precious time and resources and leads to a meticulously organized SaaS app landscape. Consequently, your team can redirect focus toward strategic endeavors that drive the organization forward.
However, the heart of Zluri's data engine lies in simplifying access management. By adopting a user-friendly approach, Zluri ensures that proper permissions are granted to the right employees for their service accounts. This streamlines the access control process, empowering your IT team to establish and uphold a secure access environment that aligns seamlessly with your organization's security policies and compliance regulations resulting in reduced data breaches.
Role of Zluri’s automation engine in data breach prevention
Effective data breach prevention goes beyond merely allocating or withdrawing permissions; it demands a finely tuned and dynamic user lifecycle management approach. Zluri's automation engine emerges as a game-changer, seamlessly orchestrating the entire user journey from onboarding to offboarding and every stage in between.
Moreover, as per Kuppingercole's report, Zluri's automation engine bolsters efficiency by reducing any human-related measures or any manual intervention. Traditional user access management methods often involve time-consuming manual updates to access rights, leaving room for errors and delays. Zluri's IGA streamlines this process by automatically synchronizing user profiles with their current responsibilities.
This enhances security and frees up valuable IT resources to focus on strategic initiatives rather than routine access management tasks.
Enhancing Data Security Through Streamlined User Access Provisioning:
Zluri's platform offers a seamless experience by automating user access provisioning. This automation minimizes the involvement of the IT team in repetitive tasks, allowing them to focus on more strategic initiatives. With Zluri, your teams can effortlessly manage and control access rights, reducing the chances of granting unauthorized access and minimizing potential vulnerabilities.
One of Zluri's key strengths lies in its intuitive interface, which empowers IT teams to easily create and customize onboarding workflows. This means that new employees can be granted access quickly and efficiently while ensuring that the level of access is tailored to their specific job entitlements, roles, positions, and departments. This tailored approach ensures that each employee has access to precisely what they need for their roles, minimizing the risk of unauthorized data exposure.
The user-friendly interface provided by Zluri further simplifies the process of designing workflows. IT teams can configure access privileges based on predefined job roles and responsibilities using just a few clicks. This intuitive approach eliminates the complexities of manually designing workflows and reduces the chances of mistakes that can lead to data breaches.
With Zluri's powerful workflow capabilities, you can expect increased efficiency, enhanced employee productivity, and heightened security for both users and SaaS app data.
By incorporating Zluri's innovative solution into the operations, your teams can significantly reduce the potential for data breaches caused by improper access provisioning. The streamlined process ensures that every step of user onboarding aligns with security best practices, reducing the risk of both insider threats and external attacks.
With Zluri, data security becomes a proactive endeavor rather than a reactive one, allowing your teams to safeguard sensitive information and maintain the trust of their customers and partners.
Enhancing Data Security Through Streamlined User Access Deprovisioning:
Zluri's intelligent platform offers an efficient and streamlined approach to user access deprovisioning. The platform's automation capabilities drastically reduce the time and effort required to revoke access across various channels. This not only ensures a smoother transition during employee departures but also significantly minimizes the window of potential data breach that arises during these transitions.
One of Zluri's standout features is its ability to automatically revoke access to all devices, applications, and systems. This proactive approach serves as a robust safeguard against unauthorized entry to sensitive data after an employee's departure. By promptly removing access permissions, Zluri helps prevent potential data breaches that can occur due to lingering permissions.
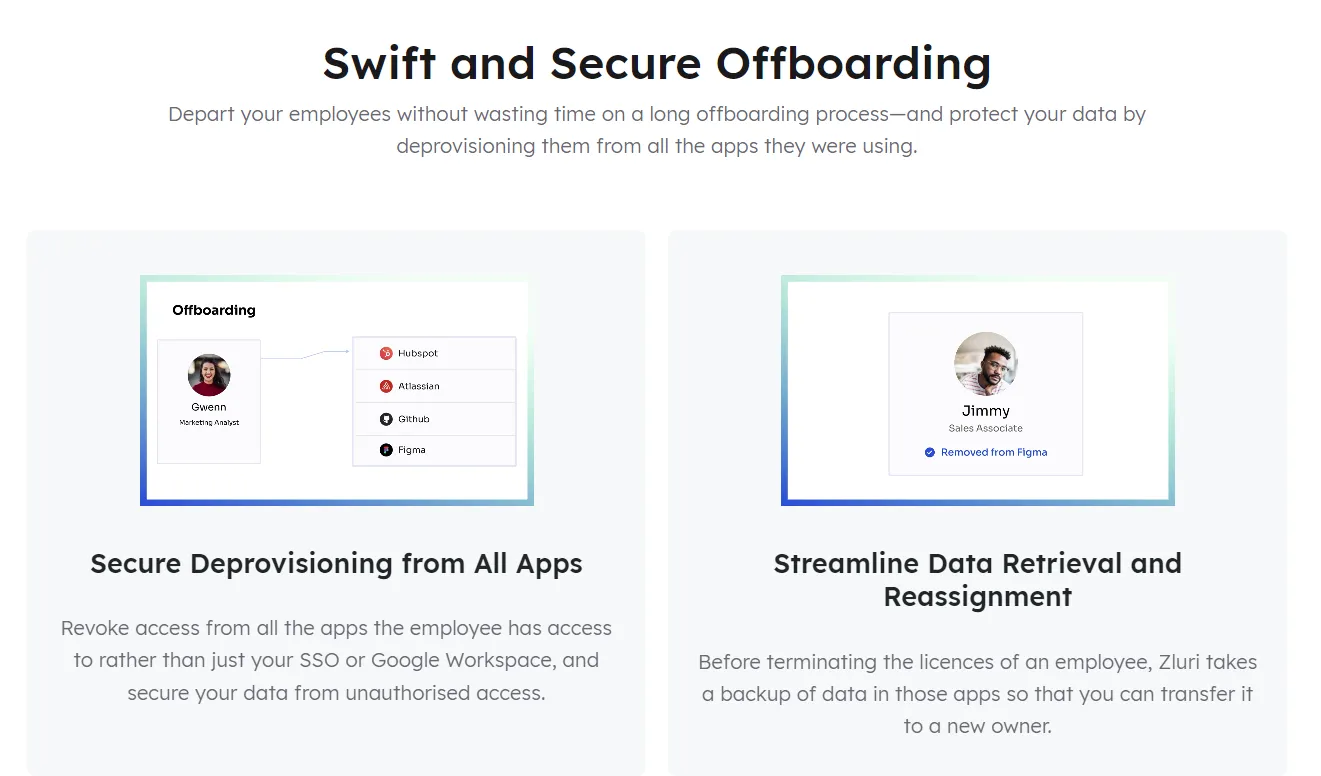
Zluri's offboarding solution goes beyond access revocation by addressing the crucial aspect of data protection. During the offboarding process, the platform takes charge of backing up essential data and transferring it to a new owner or the appropriate team within the organization. This preventive measure ensures that critical information doesn't get lost or fall into the wrong hands, maintaining data integrity and compliance.
Zluri simplifies the revocation of licenses and blocking SSO access for departed employees. By doing so, the platform eliminates the risk of ex-employees continuing to use organization applications, reducing the potential for security breaches.
Zluri's approach to offboarding offers consistency and security in handling employee departures. The platform ensures that all necessary steps are taken to prevent data breaches and unauthorized access, irrespective of the circumstances of the departure. This level of thoroughness instills confidence in organizations, allowing them to address employee offboarding with ease and peace of mind.
Prevent Data Breaches with Zluri's Automation Playbooks
Zluri's automation playbooks empower your team to automate manual and repetitive tasks, saving precious time and drastically reducing the likelihood of human errors. This results in smoother workflows and more accurate access control, fortifying your organization's security posture.
One of the key areas where the automation playbook shines is in expediting user provisioning and deprovisioning processes. The feature ensures that the right individuals have timely access to the necessary resources, and that access is promptly revoked when no longer necessary.

This enhances overall operational efficiency and security by mitigating the chances of dormant accounts and lingering access points that can become potential vulnerabilities or breaches.
Ensuring data security with Zluri's self-serve model
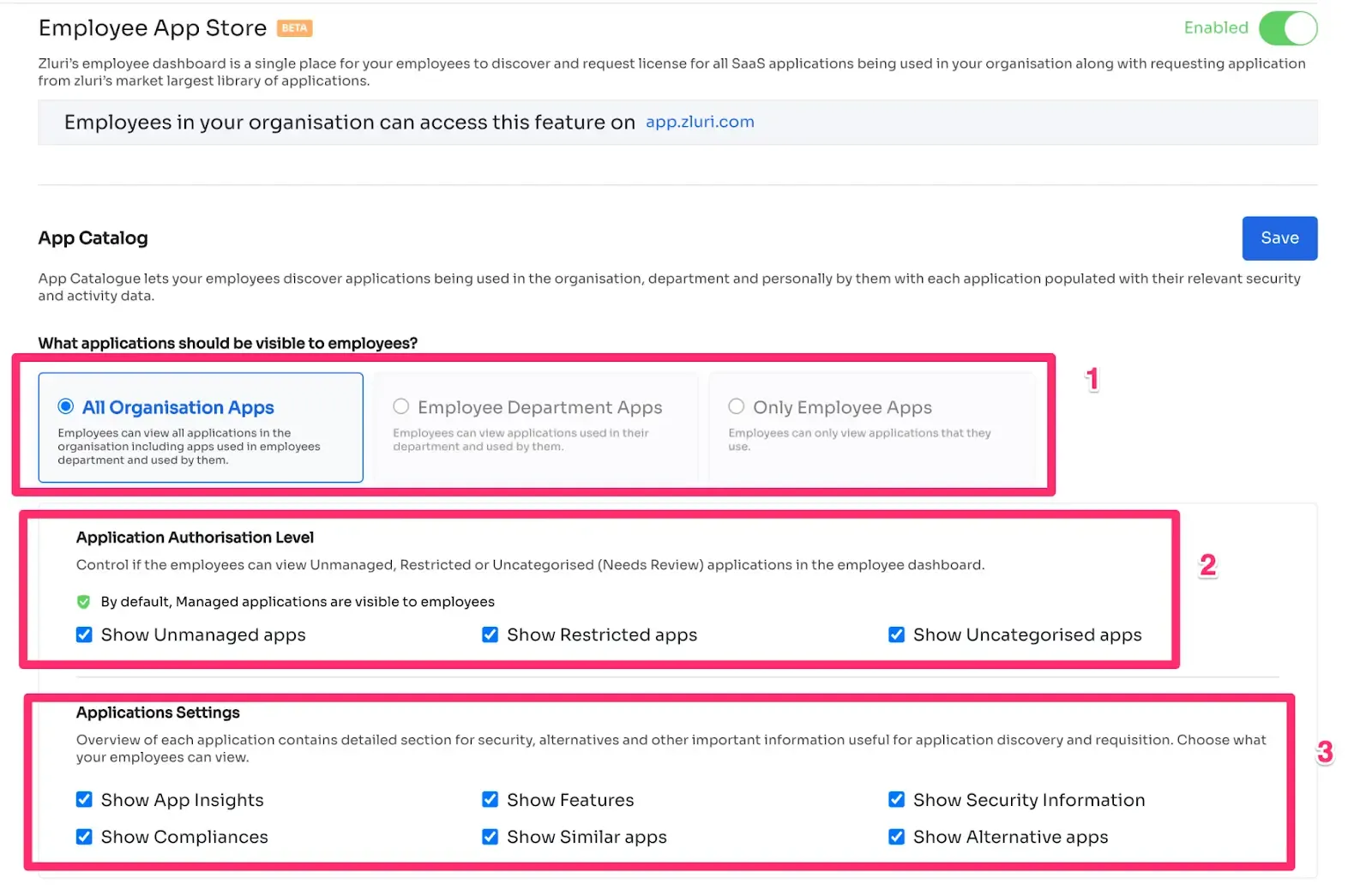
Managing access requests, particularly during employee transitions, is a complex task that requires meticulous attention to detail to prevent data breaches. Zluri's innovative self-serve model, the employee app store (EAS), offers a solution that streamlines access request management, minimizing the risk of unauthorized data exposure while ensuring employees have the appropriate permissions for their roles.

Zluri's EAS eliminates the need for manual access request processes. This self-serve model allows teams and approvers to seamlessly review and approve access requests based on the specific job responsibilities of each employee. By tailoring access according to job roles, unnecessary privileges are avoided, reducing the risk of data breaches due to over-authorization.
Zluri empowers you with robust control over access privileges, maintaining the confidentiality of sensitive information. With the EAS, your teams can prevent unauthorized access to critical data by defining precise boundaries for each employee's access. This technology ensures that only authorized personnel can access specific tools and resources, bolstering data security.
The EAS operates on a multi-tiered approval system, involving app owners, reporting managers, and IT administrators. This hierarchical approach allows higher authorities to override decisions made by lower-level admins or managers, facilitating swift action when necessary. This dynamic approval system ensures a balance between granting access and maintaining security.
Transparency is a cornerstone of Zluri's IGA solution. Approvers can include detailed comments when rejecting an access request, ensuring employees comprehend each decision's rationale. Zluri's intelligent solutions also enable approvers to modify specific requests, ensuring access aligns precisely with organizational requirements.
Keeping stakeholders informed is crucial in access management. Zluri's IGA solutions offer a comprehensive \"changelog\" feature that tracks updates, including approvals, rejections, and changes in license duration or tier. This feature facilitates transparency by documenting every change, creating an audit trail that aids in compliance efforts.
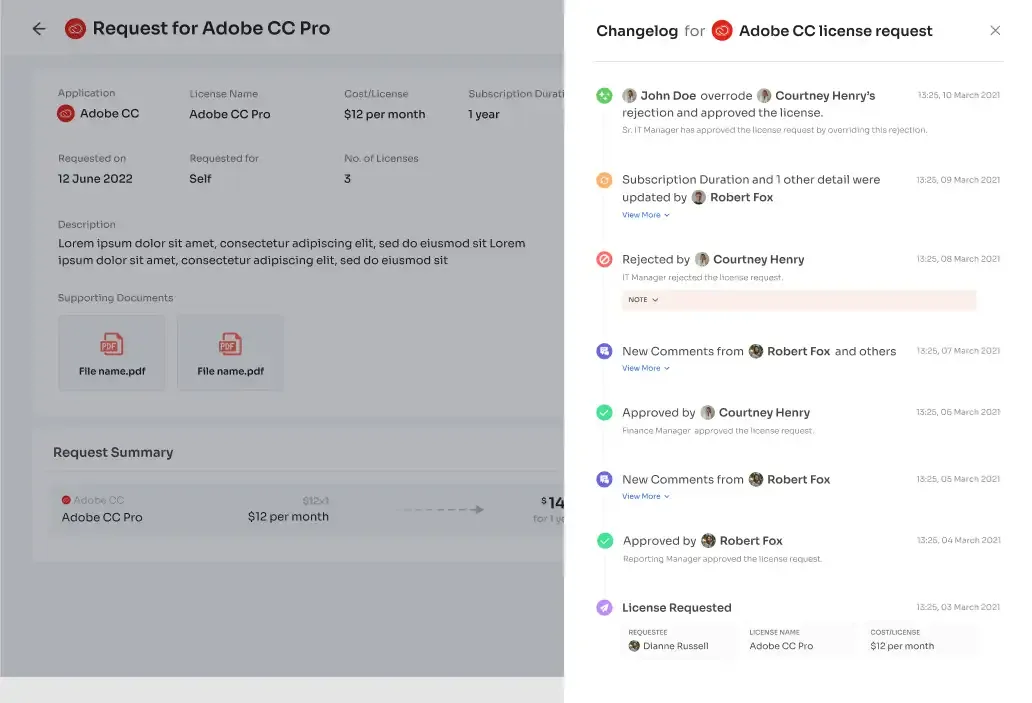
Zluri's EAS encourages a collaborative approach to access management. The changelog captures comments added by any admin, promoting informed decision-making and knowledge sharing among team members. This collaborative environment ensures that access decisions are well-informed and aligned with your organizational goals.
Strengthening data security & ensuring compliance through Zluri's access review process
Through a meticulous transformation of conventional practices, Zluri's IGA solution is pivotal in fortifying data security measures. Unlike the previous time-consuming and labor-intensive access review methods, Zluri's innovative approach focuses on automating and expediting access reviews.
By liberating your admins from manual intricacies, Zluri allows them to prioritize core responsibilities for fostering business expansion while enhancing security protocols concurrently.
The essence of Zluri's accomplishment lies in its comprehensive strategy. By offering a centralized platform that seamlessly integrates all SaaS systems and applications operating within your organizational framework, Zluri empowers your IT team with a holistic view. This holistic perspective facilitates efficient management of user access review across the entire SaaS landscape, mitigating the risk of unauthorized entry points and thus contributing to the prevention of potential data breaches.
Data Breach Prevention through Unified Access: Gain a 360-Degree View of Digital Identities
Zluri's IGA solution emerges as a robust defense against data breaches, equipping your teams to safeguard sensitive information. By offering an integrated perspective on access privileges and user behaviors, Zluri enables a proactive approach to prevent data breaches and fortify your organization's security posture.
Zluri's IGA solution revolutionizes access management by consolidating user access data from diverse sources into a centralized platform. This eliminates the need to manage multiple directories and disconnected identity repositories, ensuring that admins have a holistic view of user access across the organization.
- Centralized access repository: Imagine a large organization with multiple departments and systems. Admins must navigate various directories and databases without a centralized access repository to determine user access rights. This complexity can lead to oversight, where a user might have access to sensitive data they shouldn't.
Zluri's solution centralizes this information, allowing administrators to review and update access privileges from one platform easily. This prevents scenarios where employees have unintended access to confidential information, reducing the risk of data breaches. - Empowered access control: Consider an employee who changes organizational roles. Their old access permissions might only be revoked with proper access control, giving them unnecessary access to systems and data.
Zluri's unified access approach empowers admins to identify such cases and adjust access rights accordingly promptly. This prevents situations where ex-employees or employees in different roles retain access that malicious factors could exploit to breach sensitive information. - Real-time insights and proactive alerts: Picture a scenario where an employee's account is compromised, and an unauthorized person starts accessing sensitive files. Without real-time monitoring, this activity could go unnoticed for an extended period, increasing the potential damage.
Zluri's IGA solution continuously monitors user activities and triggers immediate alerts for suspicious behavior. This early warning system allows admins to take swift action, such as locking accounts or revoking access, to prevent further unauthorized access and minimize the impact of a potential breach.
Data breach prevention requires a multi-layered approach, and Zluri's IGA solution plays a pivotal role by providing essential capabilities needed to manage access effectively, detect anomalies, and respond swiftly to potential threats. With Zluri's advanced access review process, your teams can significantly reduce the likelihood of data breaches and strengthen your organization’s overall cybersecurity posture.
Data Breach Prevention through Automated Framework: Unleashing the Power of Automation
Zluri's advanced automated access review framework plays a pivotal role in fortifying your organization's defenses and mitigating the risk of data breaches. By leveraging the power of automation, Zluri's solution establishes an impenetrable shield around sensitive information, ensuring that only authorized individuals have access and significantly reducing the likelihood of unauthorized breaches.
- Strategic access control: Consider a scenario where an employee with legitimate access inadvertently shares their login credentials. This error could go unnoticed without Zluri's access review framework, potentially granting unauthorized individuals access to critical systems.
However, Zluri's automated access reviews continually evaluate user access against predefined criteria. In this case, the platform detects the unusual access pattern, triggers an alert, and restricts access, preventing a potential data breach. - Continuous certification vigilance: Zluri's automated reviews are orchestrated at regular intervals, ensuring that access permissions remain up-to-date in accordance with evolving security standards. By simplifying and automating the certification process, potential security gaps caused by outdated access rights are swiftly eliminated. This proactive stance significantly reduces the window of vulnerability, making it much more challenging for cybercriminals to exploit weaknesses and breach your system.
Consider a situation where an employee departs the company – Zluri's system promptly identifies the change in employment status, revokes access, and prevents unauthorized data exposure. - Swift Remediation: With automated remediation actions, Zluri enables your IT team to proactively address potential risks before they escalate. By automating these corrective measures, the platform empowers your teams to respond swiftly to security threats, minimizing the potential impact of breaches.
This rapid response prevents breaches and ensures that any attempted breaches are met with immediate resistance, safeguarding your data from compromise.
For instance, consider a company operating in the healthcare and finance sectors, subject to HIPAA and SOX regulations. Through automated access reviews, Zluri ensures that access permissions adhere to both sets of rules, reducing the risk of compliance violations and potential data breaches.
Zluri establishes a robust defense against data breaches by integrating these comprehensive features. With strategic access control, continuous certification oversight, and swift remediation, your organization is equipped to counter the dynamic threats posed by cybercriminals, ultimately safeguarding sensitive data and preserving your reputation.
Wondering how to automate user access reviews? Zluri’s comprehensive ‘access certification’ module has got you covered:
- Step 1: To automate access reviews, access Zluri's main interface and navigate to the \"Access certification\" module. Within the module, select the option to create a ‘new certification.’
- Step 2: Assign a name to the certification and designate an owner who will oversee the automated access reviews.
- Step 3: Choose the preferred method of reviewing user access by exploring the options: Application, Users, and Groups.
- Step 4: Opt for the \"Application\" review method if desired and add the relevant application(s) to be audited for users' access.
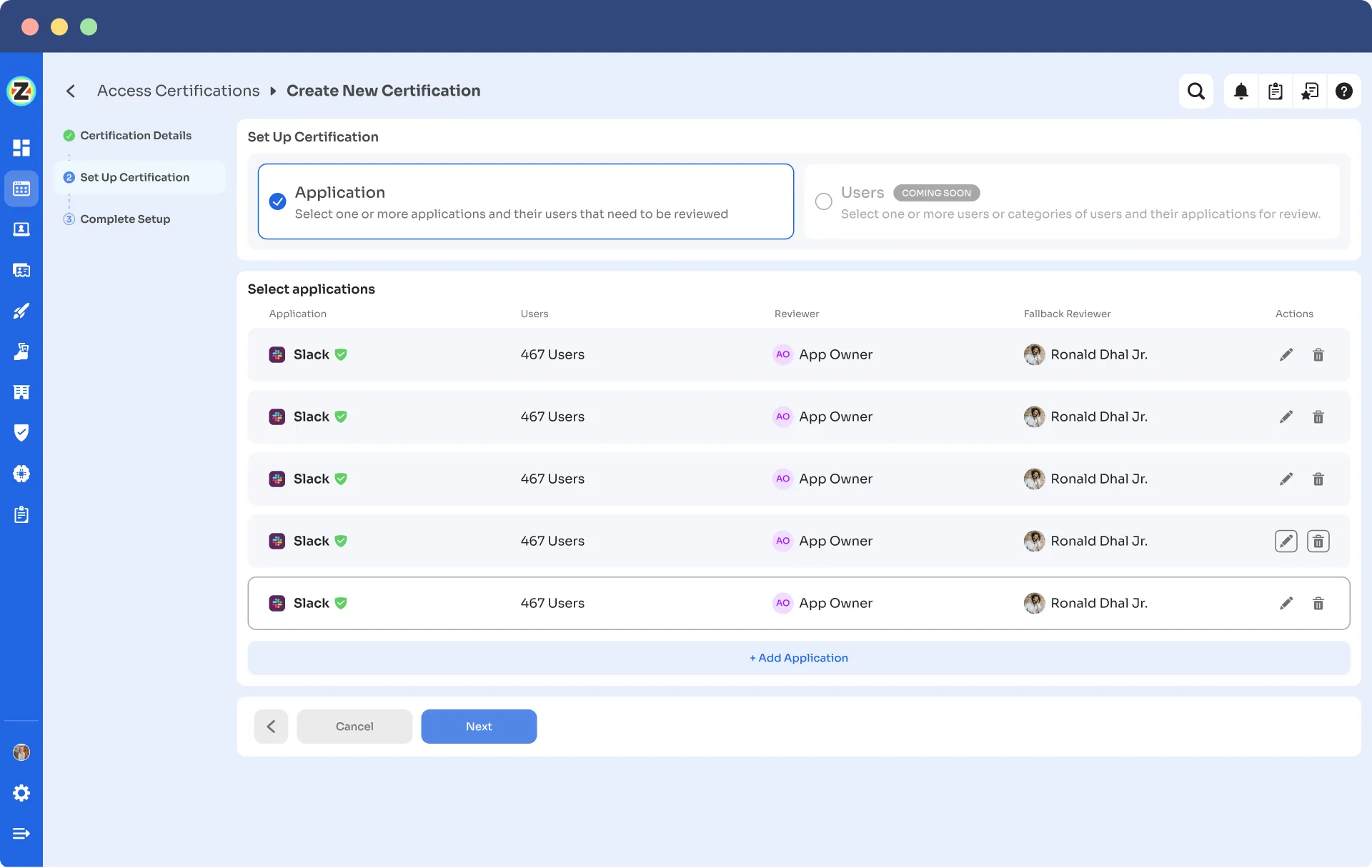
- Step 5: Select a primary reviewer and a fallback reviewer from the dropdown menu for the automated access reviews.
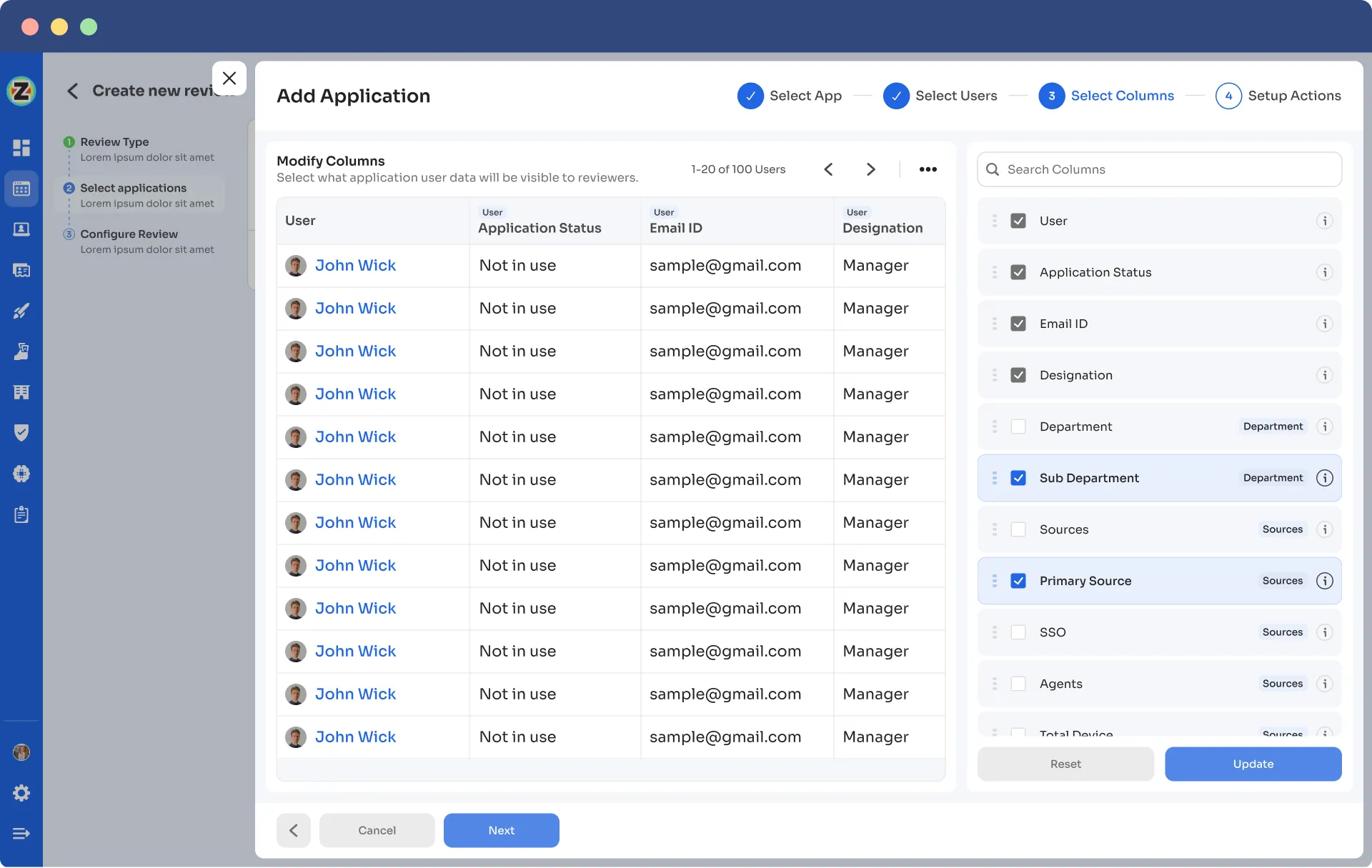
- Step 6: Select the users to be included in the automated access reviews process and apply data filtering to refine the user selection based on certification requirements.
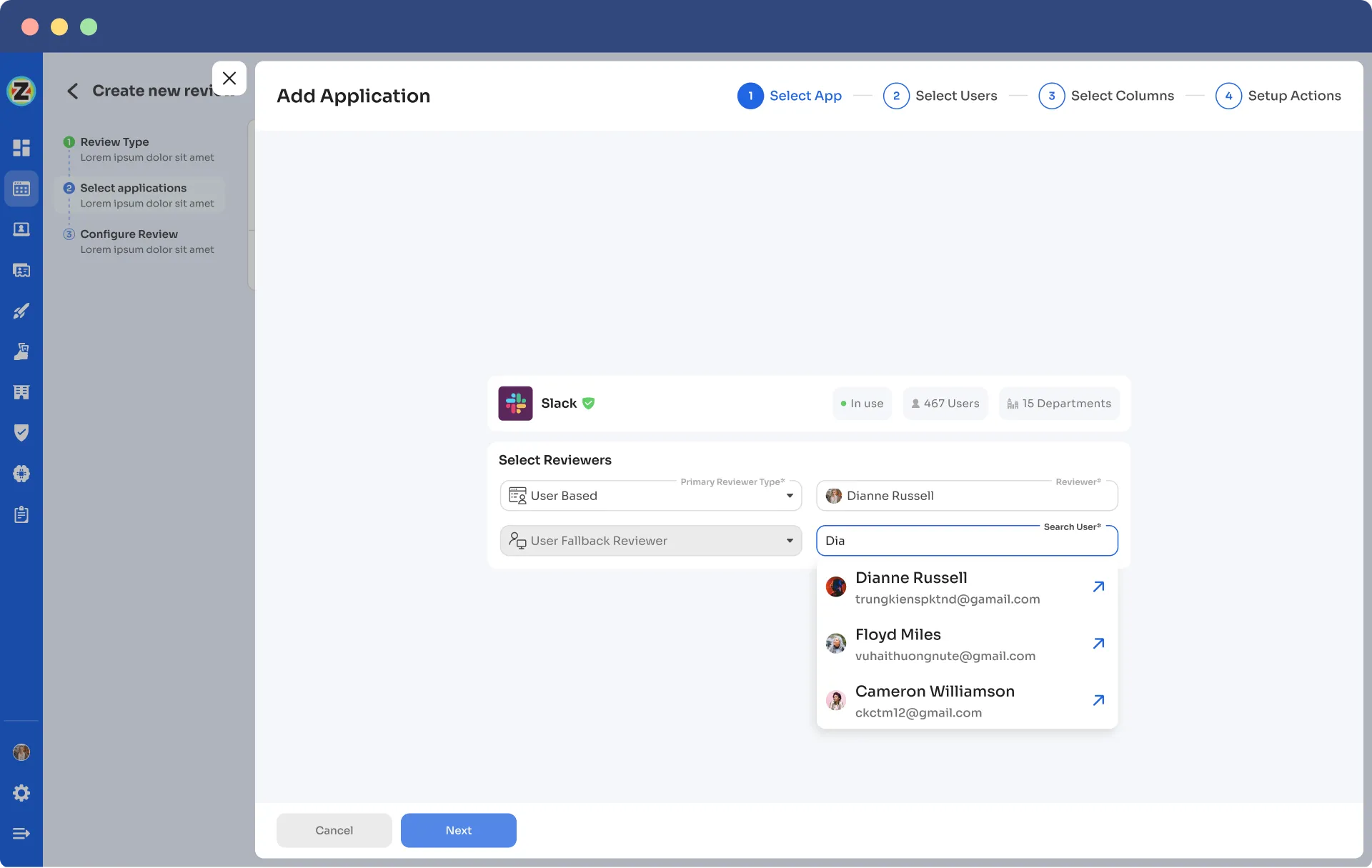
- Step 7: Proceed to the next step and configure the actions to be performed during the automated access reviews, choosing from the provided dropdown list of actions.
Note: If there are multiple applications to be included in the same certification, repeat the process of adding applications as needed.
- Step 8: Specify the start and end dates for the automated access certification process, ensuring they align with recurring or scheduled certifications.
- Step 9: Save the configuration as a template for future use by clicking on the \"Save Template\" option.
- Step 10: Monitor the progress and updates of the automated access review process for the specific certification by regularly checking the \"Review Stage\" section.Incorporating Zluri's cutting-edge IGA solution can lead to a substantial improvement in data security and regulatory compliance. By introducing a centralized access platform and implementing automated review mechanisms, Zluri revolutionizes how user access is managed. The solution's robust features are designed to bolster your organization's defenses, reduce the risk of data breaches, and ensure efficient control over user access privileges. With the potential to expedite reviews by a factor of 10 and reduce effort by 70%, Zluri's IGA solution optimizes access management workflows, allowing your team to prioritize growth and innovation.Zluri's IGA solution streamlines access provisioning and provides comprehensive visibility and control, enabling proactive measures in user access review. By leveraging its powerful insights, your organization can stay ahead of potential security threats, enhancing overall data protection and compliance efforts.By embracing this innovative solution, you can confidently navigate the complex landscape of cybersecurity and regulatory expectations, ultimately ensuring a safer and more secure digital environment. Book a demo today!







.png)

.svg)














