Still relying on legacy IGA to handle the needs of a hybrid/remote workforce, expanding SaaS ecosystem, and rising cyber threats? If yes, it’s time for a switch. Deploy next-gen IGA to manage today’s dynamic IT environments. Why is there a need to switch? In this article, we’ll discuss the legacy IGA gaps and how next-gen IGA helps close them.
Zilla’s 2025 state of IGA survey report reveals –
- Only 6% of organizations have a fully automated setup for managing their identity governance and administration process.
- 84% of the organizations rely entirely on manual methods
- The remaining 10% leverages legacy IGA and disparate solutions that partially automate the process and offer limited functionality.
This highlights that nearly the entire market (94% of the organizations) is operating with outdated approaches and solutions that are:
- Neither was built to address evolving cyberattacks
- Nor to manage dynamic IT environments (where the workforce is distributed and new apps are introduced now and then).
Manual approach consumes time, is highly prone to errors, and is labour-intensive. With increasing identities, apps, and compliance demands, this method not only delays operations but also opens the door to access assignment errors, audit failures, and security gaps.
And legacy IGA? They may automate a few sets of tasks, but they bring forth a different set of challenges.
What are they? Let’s find out.
The Hidden Gaps in Legacy IGA That Slow You Down
Below, we’ve listed some of the critical challenges of legacy IGA that you cannot afford to overlook.
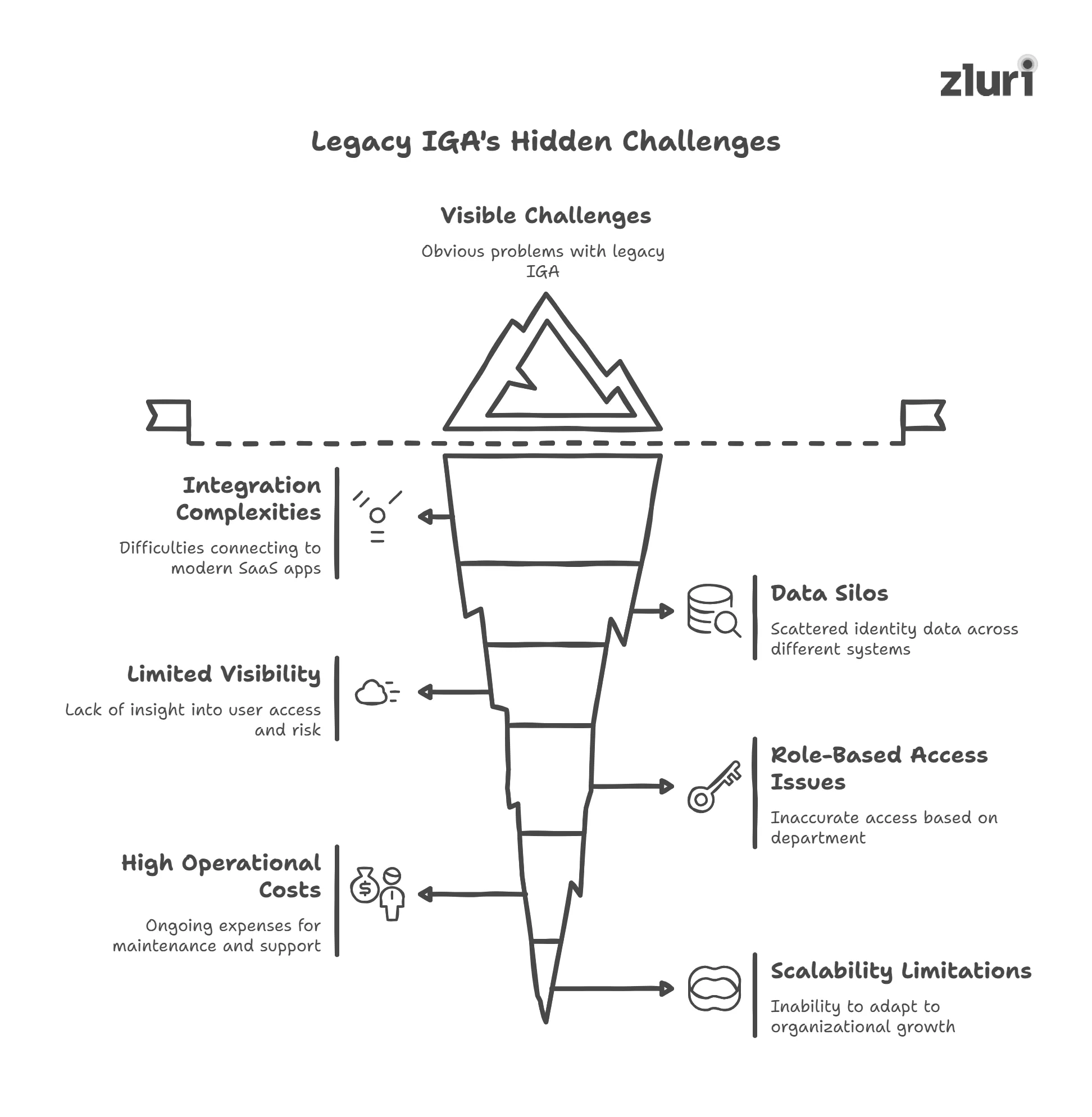
1. You Spend Weeks Just Integrating Basic Tools
Legacy IGA tools weren't built for the cloud era.
- They're rooted in an on-prem world, so the moment you try connecting modern SaaS apps, things start to fall apart.
- They rely on native connectors—great for stable, on-prem apps like Active Directory or SAP, but useless when it comes to cloud-based tools.
- SaaS apps work differently. They're API driven, change frequently, and follow dynamic authentication protocols. Legacy connectors just can't keep up.
That leaves you with two painful options:
- Build custom connectors for every app (which break every time the API changes)
- Or bring in middleware like iPaaS or identity brokers
Either way, you're stuck in a slow, complex setup. Even a basic integration can take months, sometimes up to a year, before it's fully functional.
2. It Can’t Tell When Two Accounts Belong To The Same Person
Most orgs today access several apps.
SSO for authentication, an access management platform for app access, and something for audits. Each stores its identity data differently, and in silos.
The result? Your identity data is scattered. And even if you integrate these tools into your legacy IGA, the platform doesn't unify the records.
Let's understand with an example:
- Your organization uses 3 IAM tools.
- A new user, John Dae, joins.
- One tool saves him as John.dae, another as John. D, and the third as J.Dae
Legacy IGA pulls data from all three systems, but shows three separate users on its dashboard. It can't match & merge them.
Why does this matter? You get duplicate records and inaccurate access visibility. Broken access reviews & compliance trails. Lastly, IT teams end up fixing the entire mess, manually.
When you're managing hundreds of apps and users, this manual revocation is a nightmare. You need identity data that's unified by default.
3. You Don’t Know Who Has Access Or Whether It’s Risky
Today's IT landscape is messy. You're managing:
- Full-time, remote, and contract users
- Service accounts, bots, and other non-human identities
- SaaS, on-prem, GenAI apps & Shadow IT
And with decentralization, users add apps without IT's approval. Visibility? Gone.
Legacy IGA won't help much:
- Uses outdated connectors or CSVs
- Can't reconcile duplicates
- Misses contractors, service accounts, and shadow apps
- Shows only who has access, not what they're doing with it
- No insights into risky or excessive permissions, rogue permissions, and orphaned accounts
So what happens?
.webp)
During access reviews, you're left guessing.
You chase app owners and managers to confirm basic information, like who this user is. Are they active? Is this access still needed?
By the time you figure it out, the risk has already been there for a long time.
4. Access Is Granted By Department, Not By Actual Role Or Risk
Legacy IGA solutions often rely on a group-based approach for access provisioning. Instead of analyzing who the identity is and which tools they need, legacy IGA simply groups users based on department and assigns access to the group.
- For example, it puts developers, network engineers, QA testers, and system admins – all in the “Engineer” group and then grants them (the group specifically) access to a broad set of tools.
The problem? Just because a user shares a department doesn’t mean they share responsibilities as well, so granting them access to a similar set of tools simply opens up security and compliance gaps. For example –
- A developer doesn’t need to have access to the network configuration tools.
- Similarly, a network engineer doesn’t need to have access to the CI/CD tools.
So, granting them unnecessary app access permissions will simply create potential access gaps. Attackers will exploit these gaps and move laterally across your systems undetected.
- Also, a developer can be an admin or a regular user. Granting them similar access permissions would violate the principle of least privilege.
5. You’re Paying Too Much To Keep It Running
Legacy IGA doesn't just cost more upfront; it keeps draining money over time.
Here's where the costs pile up:
- Integration headaches: Legacy IGA can't natively talk to modern SaaS apps. You will need middleware (like iPaaS), which comes with its own subscriptions and support costs.
- SSO tax: Some vendors charge extra just to connect through SSO.
- Specialized skillsets: These tools aren't built for regular IT teams. You will need certified experts or expensive training just to manage daily operations.
Is it homegrown? Add dev time, maintenance, security frameworks, and bug fixes forever.
6. It Doesn’t Scale With Your Organization's Growth
Legacy IGA works, until your org works.
It was designed for a simpler world: A fixed number of users, a static app stack, and an on-prem environment. But that's not how your workplace operates today.
Modern organizations are dynamic.
You're adding SaaS apps frequently, onboarding contractors, expanding to remote teams, and dealing with constant change. Legacy IGA wasn't built for this level of scale or flexibility.
So, what happens?
- Every time you need to support a new user type or app, you're stuck reconfiguring rigid workflows.
- Scaling to distributed teams or dynamic access scenarios becomes a manual, expensive project.
- Instead of enabling growth, your IGA becomes a bottleneck.
Now that we’ve discussed the challenges, let’s understand how next-gen IGA helps overcome them.
What Next-Gen IGA Fixes & Why It Works Better?
Below, we’ve outlined how next‑gen IGA overcomes the limitations of legacy systems. For clarity, we use Zluri as an example to show how such solutions perform and the impact they deliver.
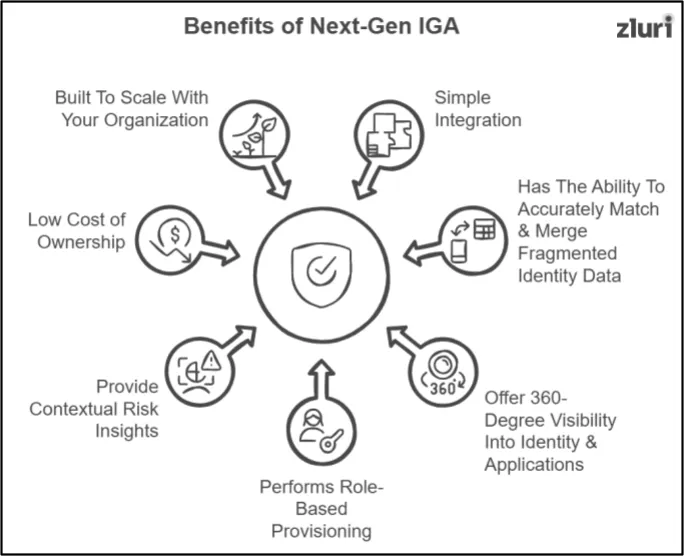
1. Connects To Your Apps In Minutes, Not Months
Next-gen IGA like Zluri is built for today’s cloud-first IT setup.
- It comes with a native iPaaS engine that allows you to seamlessly connect with over 300 modern SaaS apps – no coding and no middleware required.
- Apps that don’t have public APIs (like legacy on-prem apps) can use Zluri's custom builder SDKs, which your developers can use to code and create custom connectors.
As a result, you get quick time-to-value.
2. Automatically Match & Merge Fragmented Identity
No matter whether you have a disparate IGA model or a converged setup, Zluri provides a centralized view of identity data.
- It seamlessly integrates with all your IAM tools (SSO & MFA, LCM, ITSM, and more)
- Fetches the fragmented data from across systems.
- Then, it automatically matches and merges the fragmented identity records into a single, unified identity – creating one source of truth.
Unlike Legacy IGA, which treats one user, like John Doe, as multiple identities due to formatting differences across IAM tools. Zluri solves this by recognizing variations and unifying them into a single identity.
No more manually mapping identity data and getting confused with duplicate records.
3. Gives You A Complete, Real-Time View Of Access Across All Apps & Identity
Zluri uses 9 advanced discovery methods to identify –
- Every app present within your organization – whether it's a SaaS platform, on-premise tool, Gen-AI app, or even shadow IT that has slipped in.
- Every type of identity – including on-site and remote employees, contractors, freelancers, and non-human identities like service accounts.
With the help of this visibility, your team can effectively manage, control, govern, and secure your SaaS applications and identities.
4. Provisions Access Based On Role, Usage, And Risk – Not Just Departments
Unlike legacy IGA, Zluri allows you to grant access based on the user's specific role. This eliminates the risk of over-provisioning, thereby reducing the attack surface.
Also, by ensuring every identity strictly gets access that is relevant for their roles and responsibilities – nothing more, nothing less, Zluri helps meet PoLP.
How does it work?
It allows you to set up automation rules in onboarding workflows, where you can specify the conditions of role-based access control.
- Let’s say you want to ensure that every new hire in the market department automatically receives basic access to essential marketing tools the moment they are added to the primary source (like HRMS).
So, for that, you can define the following details in the automation workflow.
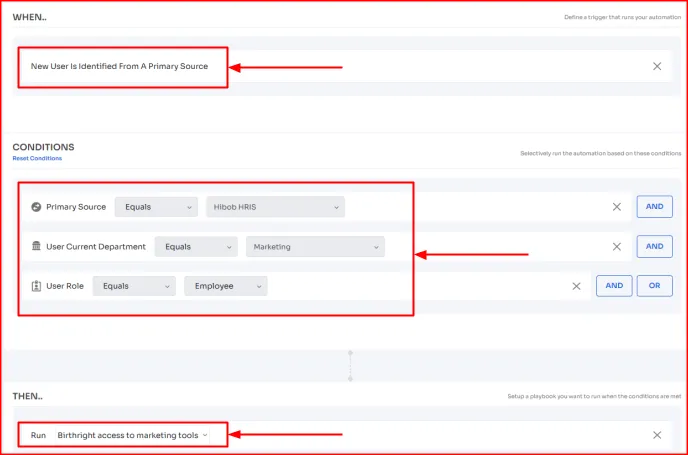
Once the conditions are satisfied, Zluri will automatically run the specified playbook and grant the required tool access to the users.
Note - However, if you wish to carry out group-based access provisioning, you can do that as well with Zluri. Instead of specifying role-based access control conditions, you can simply define group-based conditions.
5. Provide Contextual Risk Insights Before It Becomes A Problem
Zluri integrates with the apps (that are being reviewed) and fetches all the granular user details such as —
- What exact permissions are granted
- Whether any excessive/privileged permissions were given (like admin-level permissions),
- Employee status (inactive or active)
- Which users didn’t access the app in the last 30 days
- Orphaned accounts
With this rich identity context –
- Access reviewers no longer have to guess.
- They don’t need to chase down department heads or app owners for clarification on each user's role, employment status, or activity history.
All the relevant and contextual insights are provided within an easy-to-access centralized dashboard.
Result?
This helps accelerate the review process and enhances the reliability of access review reports.
6. Cuts Down Cost By Removing Manual Work & Infrastructure Overhead
Zluri is comparatively affordable.
- No need to purchase expensive middleware to connect with apps or pay SSO tax, as it has a native iPaaS engine that seamlessly connects with most SaaS apps, and it doesn’t charge extra for every integration.
- No need to hire costly teams of specialized engineers to operate it – even non-technical users can manage day-to-day tasks with its intuitive, no-code interface.
- Zluri is delivered as a fully managed IGA solution; there’s no need to worry about maintenance, patching (fixing bugs in software), or version upgrades.
7. Scales Effortlessly As Your Teams, Tools, & Users Grow
Modern IGA solutions like Zluri are dynamic by nature – designed to adapt to today’s evolving business environment.
Whether you are expanding your workforce, introducing new SaaS apps to your stack, or managing hybrid or remote teams, Zluri scales effectively to meet your needs.
That too, without any complex reconfigurations or costly upgrades.
Additional Benefits That Zluri Offers
- Provides App Recommendations: Within the onboarding workflows, Zluri suggests apps that are relevant for the user’s role, department, or designation.
- Provides Action Recommendations: Within the offboarding workflows, it suggests deprovisioning actions that can be performed within the apps.
- Allows You To Perform In-App Actions: It allows you to define specific in-app actions within the onboarding workflow. For example, within Slack, you can automate actions like sending a welcome message.
- Provides Approval Workflow: Within the approval workflow, you can create rules (configure conditions) to auto-approve and auto-reject access requests.
- Allows You To Set Up Multi-Layer Review: It allows you to set up multiple levels of reviewers – such as reporting managers, department heads, application owners, or even compliance officers – to review the same user's access in a tiered and sequential manner.
- Performs Close-Loop Remediation: It automatically remediates access anomalies by triggering deprovisioning or downgrade license playbooks.
- Allows You To Delegate Review: It allows you to delegate review tasks with ease. This feature is especially useful when the assigned reviewer is unavailable and the review needs to be completed on an urgent basis.
Switch To Next-Gen IGA To Close Legacy Loopholes Before It’s Too Late
Legacy IGA was built for the challenges of yesterday, not today’s reality. With new apps constantly being introduced to the stack, workforces frequently rotating, and compliance standards tightening, it simply can’t keep up.
And relying on outdated systems means leaving loopholes wide open – gaps that can quickly turn into costly breaches or compliance disasters. Don’t wait until your organization becomes the next headline.
Switch to Next-Gen IGA before the risks catch up with you.









.svg)














