SSO and MFA are just the starting point–not the complete picture.
You have rolled out SSO across your apps. MFA is enabled for every user. From the outside, your identity setup looks solid: centralized and secure.
But here’s the thing: authentication isn’t the same as governance. MFA confirms the user is legitimate. SSO makes access easier to manage.
What neither does is question whether that user should still have access or if they ever needed it in the first place. This is where many identity platforms fall short.
- Contractors often retain administrative rights long after their engagement has ended.
- Employees who have switched departments but retain their entitlements from their previous role.
- Shadow SaaS apps in use by users: unmonitored, unconnected to your SSO, and completely invisible to IT.
You’re not alone. We have seen mature IT teams miss these gaps, not because they lack controls, but because MFA and SSO weren’t built to handle access governance.
That’s where identity governance steps in. It brings the visibility, oversight, and lifecycle controls that your current tools can’t. And without it, you’re making access decisions without full context, just with stronger passwords.
The Illusion of Security: Where MFA & SSO Fall Short
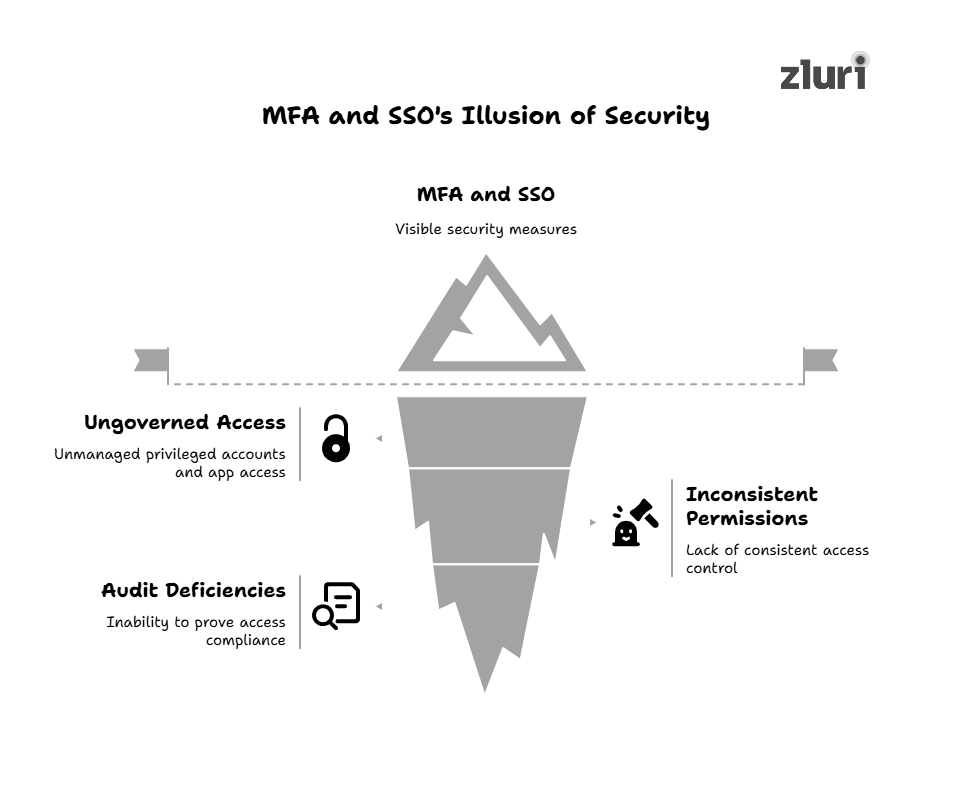
There’s no doubt MFA and SSO have transformed how you secure identity. MFA reduces credential-based attacks. SSO reduces password fatigue, centralizes login, and enhances access control across systems.
If you have deployed both, you have taken two critical steps in building a secure identity foundation.
But here’s the thing: they weren’t built to govern access.
MFA validates who’s logging in. SSO manages how they get in. Neither answers questions like:
- Should this user still have access to this app?
- Have their privileges changed with their role?
- Who owns that access, and when was it last reviewed?
That’s where real gaps start to show.
We have seen IT teams assume that centralized authentication means centralized control, until they audit access logs and realize how much is still unmanaged. For instance:
- Privileged accounts were left untouched for years because no one had mapped ownership or regularly reviewed access.
- Business-critical apps where SSO is technically connected, but users continue logging in through direct URLs, bypassing controls.
- Vendor teams accessing internal systems through shared credentials, with no way to track individual activity or enforce time-bound access.
Even in environments with mature Identity Providers (IdPs), these gaps persist because multi-factor authentication (MFA) and single sign-on (SSO) weren’t built to govern what happens after login.
And it’s not just about revoking access. Without governance, there’s no consistent way to ensure the right user has the right level of access at the right time. And that you can prove when needed, whether for compliance or audits.
That’s exactly where identity governance becomes essential. It doesn’t replace your existing setup. It completes it by adding lifecycle awareness, policy enforcement, and continuous oversight to access.
Where SSO and MFA Stop, Governance Takes Over
If SSO and MFA help you lock the front door, identity governance ensures that everyone inside is where they’re supposed to be and not wandering into rooms they shouldn’t be in.
Governance gives you what authentication alone can’t: visibility, context, and control across the entire access lifecycle.
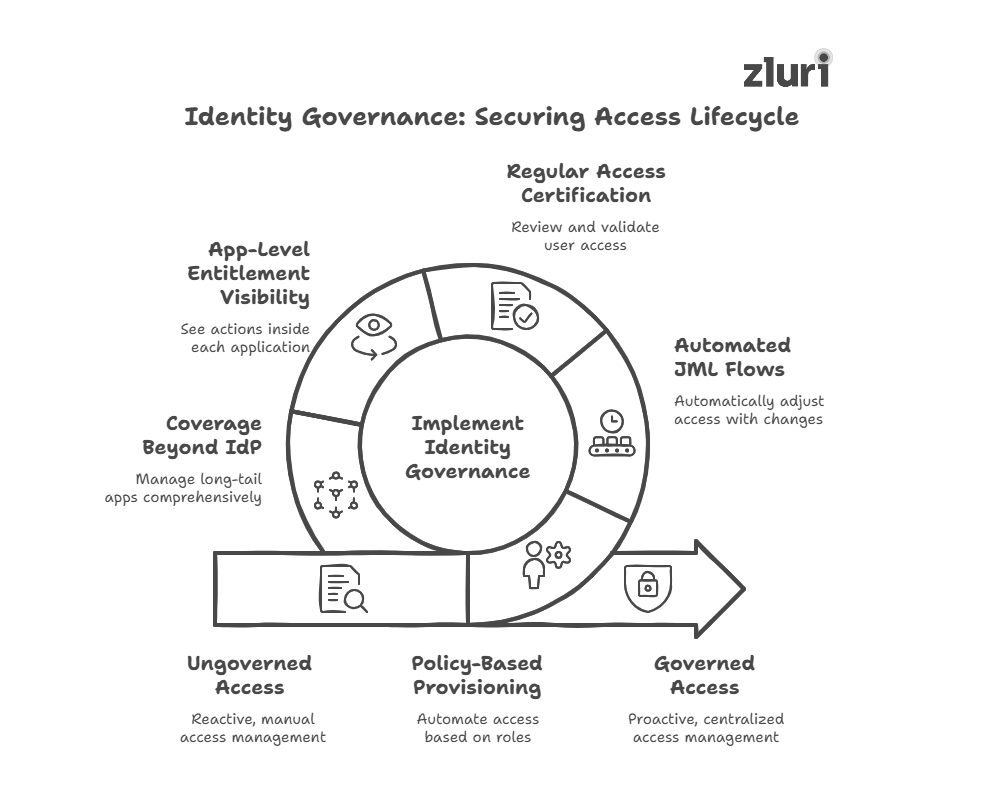
Here’s what that looks like in practice:
- Policy-based provisioning: Instead of ad-hoc requests, users receive the right set of apps and permissions automatically based on their role, department, or seniority. You define the rules once, and governance enforces them consistently.
- Automated (joiner-mover-leaver) flows: As users join, switch roles, or leave, access is automatically adjusted or revoked. No more relying on tickets or hoping someone remembers to clean up access.
- Regular access certification: App owners or managers review who has access to what and certify whether it’s still valid. This closes the loop on excess privileges, providing a provable audit trail.
- Visibility into app-level entitlements: Governance tools don’t show you who has access to which apps; they show what they can do inside those apps. That includes sensitive actions, hidden roles, and combinations you won’t see from the SSO console.
- Coverage beyond your IdP: Many cloud apps, especially in SaaS-heavy environments, operate outside your identity provider. Governance helps you discover and manage these long-tail apps, including those that teams adopted without IT’s approval.
The result? You get a security model that doesn’t just block unauthorized access, but continuously validates and governs authorized access with built-in accountability at every step.
Without governance, you’re stuck playing catch-up, reacting to incidents, manually reviewing access logs, or rushing to prepare for audits.
With it, you stay ahead: clean and centralized access, less mess, and complete control.
Key Use Cases Where Identity Governance Becomes Essential
By the time most organizations think about governance, it’s usually because something has already gone wrong: an audit finding, a permissions-related incident, or a wake-up call during a merger.
If you have seen these scenarios firsthand, you will know exactly why IGA matters. If not, here’s where the cracks usually start to show.
.png)
1. Mergers, acquisitions & organizational restructuring
During M&A activity or even internal reorganizations, identity chaos is almost guaranteed:
- Duplicate users across systems
- Access granted based on previous roles that no longer exist
- And a backlog of provisioning and revocation tickets that no team can keep up with
We have seen organizations take 6-12 months just to untangle cross-entity access, which delays integration efforts and exposes critical systems in the process. With governance, you can automate access realignment based on new business structures and reduce the risk of inherited access.
2. Contractor and vendor access
Temporary users often become long-term liabilities.
We have seen contractor accounts remain active well beyond their engagement, not due to negligence, but because no one was responsible for the deprovisioning process.
Governance solves this by:
- Enforcing time-bound access
- Auto-revoking permissions when contracts end
- Providing clear ownership over third-party identities
For regulated industries, this level of control often becomes a compliance requirement, not just a security best practice.
3. Shadow IT and SaaS sprawl
It’s rare to find a team that hasn’t signed up for tools outside the approved stack. Whether it’s design, sales, or marketing, SaaS apps are often adopted before IT even becomes aware of them.
The result?
- Accounts that never go through your SSO
- Admin roles assigned outside policy
- Zero visibility into usage or data exposure
Governance brings these apps into the light, allowing you to apply policies, monitor entitlements, and shut down what doesn’t belong. This is especially critical in SaaS-heavy environments where IT teams don’t directly control app onboarding.
4. Privileged access and SoD conflicts
Even in well-structured organizations, roles slowly accumulate access over time.
That’s how a junior finance analyst ends up with approval rights, or how an engineer ends up deploying to production and reviewing their changes.
Without governance:
- You don’t know that such unwanted combinations exist
- You can’t detect privilege creep
- You can’t prove to auditors that SoD policies are enforced
Governance lets you flag conflicts early, route access to the right reviewers, and reduce reliance on manual controls.
These aren’t theoretical risks; they’re operational realities. If you have ever struggled to answer, “Who has access to this system and why?” – that’s your signal that governance is missing.
And the longer these gaps go unaddressed, the harder they become to unwind.
IGA + SSO + MFA: Building a Complete Identity-First Stack
If you already have MFA and SSO in place, you have solved two big parts of the access equation.
- MFA protects against credential theft by verifying identity.
- SSO simplifies and centralizes user access to systems.
However, if you stop there, you’re still leaving a major gap open: who has access to what, and whether that access remains valid.
That’s where identity governance fits in–not as an add-on, but as the control layer that ties everything together.
.png)
Here’s how the three work together:
- MFA ensures the person logging in is who they claim to be.
- SSO provides a single portal for accessing multiple apps, reducing password sprawl and enabling centralized access control.
- IGA governs whether they should have access in the first place, how long they should retain it, and who is accountable for approving or reviewing it.
Why does governance need to lead?
In theory, you can roll out MFA and SSO across every system. But in reality:
- Not every app supports SSO
- Not all teams follow the same onboarding process
- Access requests still happen outside defined channels, through tickers, emails, or informal Slack pings.
That’s why IGA isn’t just a finishing touch; it needs to anchor your identity strategy:
- It enforces access policies at scale
- It closes the loop with automated provisioning and deprovisioning
- It gives you a continuous, auditable record of access decisions across apps, users, and teams
Think of it this way:
- MFA locks the doors.
- SSO manages the keys.
- Identity governance decides who should even be allowed in, what they can do, and when they should leave.
Without governance, you’re only securing the front end of the identity journey.
With it, you’re securing the complete lifecycle from onboarding to offboarding, from one-time access to ongoing accountability.
Closing Your Governance Gaps Starts with Visibility & Zluri Gives You That on Day 1
MFA validates identity. SSO streamlines login. But what happens next? Who gets access, for how long, and under what conditions? This is where most stacks fall short. That's exactly the blind spot Zluri fills.
Zluri brings governance into the picture by providing you with the tools to continuously monitor, control, and recover access, even in sprawling SaaS environments where traditional IAM controls often stop at the front door.
Here's how it helps:
1. Discover all applications, including what SSO misses
SSO only shows you what it’s connected to. But in most SaaS-heavy environments, there’s a long tail of apps that never go through it. Think of tools adopted by individual teams or contractors that fly under the radar.
Zluri solves this with its discovery engine and 9 discovery methods, i.e., SSO & IdP, browser extensions, desktop agent, HRMS, finance systems, CASBs, MDMs, which map your app landscape, including:
- Shadow IT tools
- Unmanaged apps
- External or niche platforms not covered by SSO
- Non-human identities
Even if an app doesn’t support standard integrations, Zluri can still connect to it using webhooks. It allows you to track and govern access even in hard-to-reach corners of your stack.
Everything, from app usage to user entitlements, is pulled into one clean dashboard, so you don’t have to rely on spreadsheets or ping department heads for visibility.
2. Build access policies around roles, not just requests
Zluri lets you create automation rules to grant the right access when specific conditions are met, like department, role, or location, without waiting on IT tickets.
For example, when a new hire from the Marketing team appears in your HR systems:
- Zluri detects the new user
- Matches them to their department
- And automatically provisions only the tools they need, based on a predefined playbook.
For that, you can outline the following details in the automation rule workflow:
Once triggered and conditions are satisfied, Zluri will automatically grant the marketing department employees access to the specified tools (the ones that are specified in the marketing department playbook).
You can also enforce:
- Role-based controls (e.g., only team leads get admin permissions)
- Contextual access rules (e.g., block access from restricted regions)
Access becomes predictable, consistent, and policy-driven from the very beginning.
3. Automate joiner-mover-leaver workflows across the lifecycle
Zluri automates the entire user lifecycle, onboarding, transitions, and exits, so you’re not stuck reacting manually at every stage.
- Provisioning: Choose from multiple methods - SSO group, direct API, Jira triggers, or custom workflows.
- Role transitions: Automatically revoke old access and provision new tools when users switch departments or roles.
- Deprovisioning: With one click, revoke access, transfer ownership of data, remove users from shared channels, and even set up email forwarding.
Zluri also provides contextual app recommendations during onboarding, so IT doesn’t have to guess which apps are relevant. Just review the suggestions, run the workflow, and Zluri handles the rest, with no follow-ups needed.
Even better, you can define in-app actions (such as assigning a user to a specific Slack channel or role in Okta) directly within the workflow. No post-provisioning cleanup required.
4. Run access reviews that improve security
Zluri transforms access reviews from a routine task into a meaningful security layer. Here’s how:
- Multi-level reviews
You can create up to five levels of reviewers, each with fallback options in case someone is unavailable. If one reviewer misses something, the next level can still catch it. This layered approach reduces the risk of misaligned access going unnoticed.
- Context and risk insights
Zluri brings risk context directly into the review interface:
- How many orphaned accounts are there
- How many external users (freelancers, contractors, or non-traditional workers) are there
- How many privileged users (such as users that hold admin-level permissions) are there
- How many inactive licensed users are there
- How many accounts have been inactive for the last 30 days
Instead of approving blindly, reviewers get clear signals about where to take action, all in one place.
- Built-in remediation
Once access is reviewed, Zluri doesn’t just log the result; it takes action. You can trigger automated workflows based on decisions.
- Revoke access
- Downgrade permissions
- Adjust license tiers
For repeat issues, reviewers can also use bulk actions, selecting all similar anomalies (such as multiple inactive accounts) and submitting a single decision and comment for the entire group.
Zluri completes the picture.
MFA protects credentials. SSO streamlines entry.
But without governance, you’re still missing answers to key questions:
- Who has access?
- Should they still have it?
- What can they do with it?
- Can you prove that, at any time?
Zluri gives you that missing layer. It ties access to policies, automates every lifecycle event, and provides your IT and security teams with true visibility and control over every identity, whether human or not.
To know more about how Zluri helps you move beyond authentication, schedule a demo with Zluri.
Don’t Mistake Authentication for Governance
.png)
You have put the right building blocks in place: SSO and MFA. But if governance is still an afterthought, you’re only solving part of the access problem.
Authentication tells you who someone is.
Governance tells you whether they belong there, what they can do, and when it’s time to step out.
And that’s the part too many teams overlook, until access reviews become unmanageable, audits uncover privilege creep, or an incident traces back to a forgotten identity.
Identity governance isn’t a “nice to have” layered on top of SSO. It’s the system that makes access secure, sustainable, and accountable – every step of the way.
If you’re serious about controlling access risk, start where it matters most: with visibility, lifecycle control, and policy-driven decisions that scale with your environment.
Because in the end, securing the login is just the beginning. Governance is the process of maintaining security long after the user gains access.









.svg)














